Introduction
Why show running-config does not give valid output on a lower privilege level
More Information
The issue faced is due to the design of the IOS. We can lower down the privilege levels of all the configuration and exec mode commands.
However, the show run or write terminal will only display the configuration of all of the commands that the current user is able to modify. In other words, all the commands at or below the user's current privilege level.
The show run/write terminal command should not display commands above the user's current privilege level because of security considerations.
To overcome such limitations, and provide more flexibility Cisco modified the industry standard TACACS and made it TACACS+.
You can use this to provide users access at your terms by authenticating the users from a TACACS+ server (like ACS).
Summary
Show run will not display a full output if its set below privilege level 15.
Solution
Assign privilege 15 but restrict access using command sets.
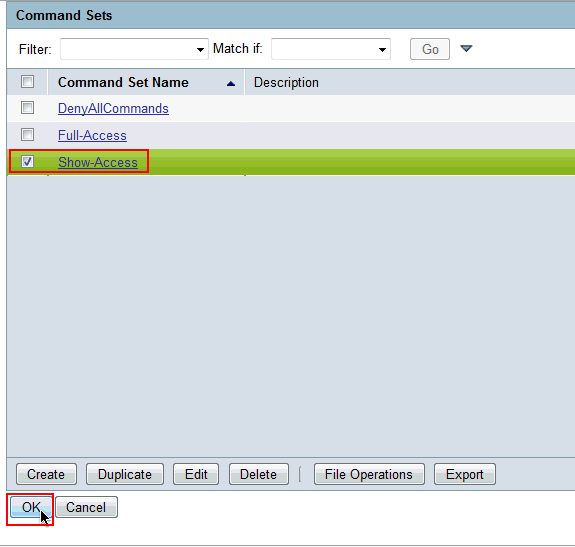
In the Shell Command Authorization Set area of the Shared Profile Components window, configure these settings:
- In the Name field, enter ReadOnlyAccess as the name of the command authorization set.
- In the Description field, enter a description for the command authorization set.
- Click the Deny radio button.
- Enter the show command in the field above the Add Command button, and then click Add Command.
- Check the Permit Unmatched Args check box, and click Submit.
Reusable Named Command Authorization Sets—Without directly citing any user or user group, you can create a named set of command authorizations. You can define several command authorization sets that delineate different access profiles. For example:
A Help desk command authorization set could permit access to high-level browsing commands, such as show run, and deny any configuration commands.
Related Information