- Cisco Community
- Technology and Support
- Service Providers
- Service Providers Knowledge Base
- ASR9000/XR: Troubleshooting packet drops and understanding NP drop counters
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 03-04-2011 08:06 AM
Introduction
In this article we'll discuss how to troubleshoot packet loss in the asr9000 and specifically understanding the NP drop counters, what they mean and what you can do to mitigate them.
This document will be an ongoing effort to improve troubleshooting for the asr9000, so if after reading this article things are still not clear, please do comment on the article and I'll have details added in case my current descriptions are not explanatory enough.
Core Issue
Before we are going to dive into the packet troubleshooting on the asr9000 it is important to undertand a bit of the architecture of the system.
Packets are received by the mac/phy, forwarded to the NPU who is processing the features, the NPU hands it over to the bridge who in turn delivers
the packets to the FIA (Fabric Interfacing Asic) upon which it is sent over the fabric (residing physically on the RSP) and handed over to the egress
Linecard who follows the FIA->bridge->NP-MAC path then.
The NP processes packets for both ingress and egress direction.
The Bridge is just a memory interface converter and is non blocking, unless you have QOS back pressure, there is generally no reason
for the Bridge to drop packets. This article will not focus on the bridge and FIA drop counters as they are generally not common.
Both NP, Bridge, FIA and Fabric are all priority aware and have separate queues for High and Low priority traffic as well as Unicast and Multicast. So when you look at the bridge you see UC/MC (unicast/mcast) as well as LP/HP queues.
A different article will focus on that.
Resolution
Here a graphical overview of how the individual asics are interconnecting with the different commands that point to the actual
asic of where we are viewing statistics from.
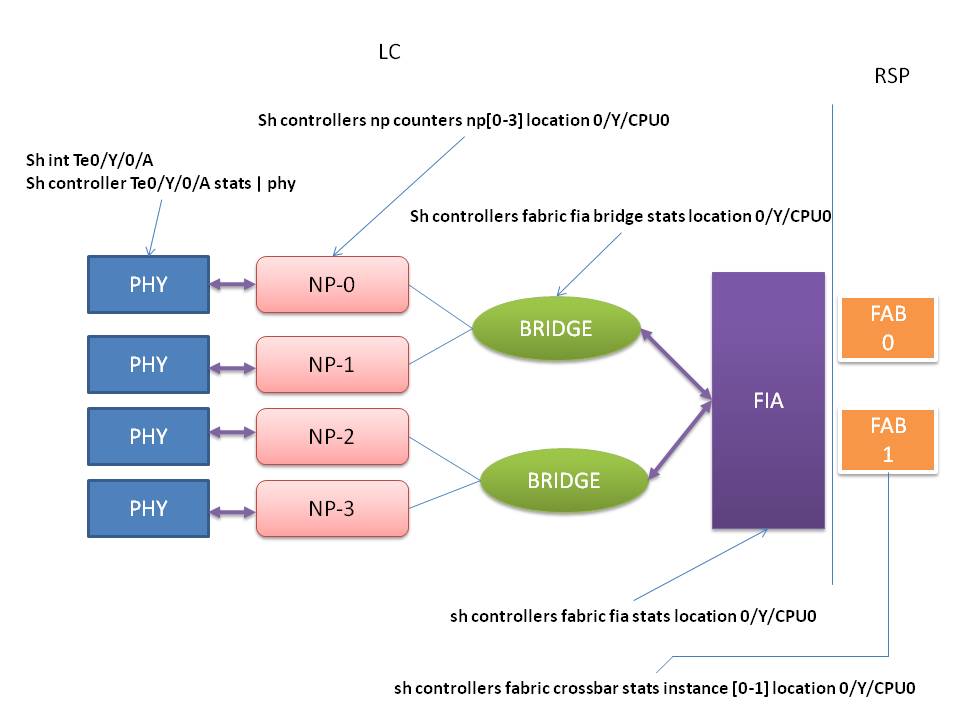
In this picture Y is the slot where the linecard is inserted on and A identifies the individual interface.
The first place to verify drops is the interface. The regular show interface command is well known.
Drops reported on the interface are an aggregate of phyiscal layer drops as well as (certain!!) drops that were experienced in the NP.
When printing the show controller np counters command, you may not know which interface identifier connects to which, therefore use
the "show controller np ports all location 0/Y/CPU0" to find out which interface maps to which NP.
RP/0/RSP1/CPU0:A9K-BOTTOM#sh controllers np ports all loc 0/7/CPU0
Fri Mar 4 12:09:41.132 EST
Node: 0/7/CPU0:
----------------------------------------------------------------
NP Bridge Fia Ports
-- ------ --- ---------------------------------------------------
0 0 0 TenGigE0/7/0/3
1 0 0 TenGigE0/7/0/2
2 1 0 TenGigE0/7/0/1
3 1 0 TenGigE0/7/0/0
In case you have an oversubscribed linecard, 2 TenGig interfaces can be connected to the same NP.
For 80G linecards such as the A9K-8T, you'll see 8 NP's listed.
For the 40 port 1GE, you'll see 10 1-Gig interfaces connecting to an NP, note that this is not oversubscription.
With that info you can now view the controller statistics and some information as to what the controller is doing.
Note that not all counters in this command constitute a problem! They are regular traffic counters also.
There is a simple rate mechanism that keeps the shadow counts from the previous command invokation.
Upon the next time the command is run delta's are taken and divided over the elapsed time to provide some rate counts.
It is important for more accurate rate counts instantly that you run this command twice the first time with a 2/3 second interval.
The output may look similar to this:
RP/0/RSP1/CPU0:A9K-BOTTOM#show controller np count np1 loc 0/7/CPU0
Node: 0/7/CPU0:
----------------------------------------------------------------
Show global stats counters for NP1, revision v3
Read 30 non-zero NP counters:
Offset Counter FrameValue Rate (pps)
-------------------------------------------------------------------------------
22 PARSE_ENET_RECEIVE_CNT 51047 1
23 PARSE_FABRIC_RECEIVE_CNT 35826 0
30 MODIFY_ENET_TRANSMIT_CNT 36677 0
31 PARSE_INGRESS_DROP_CNT 1 0
34 RESOLVE_EGRESS_DROP_CNT 628 0
40 PARSE_INGRESS_PUNT_CNT 3015 0
41 PARSE_EGRESS_PUNT_CNT 222 0
....
What all these mnemonics mean is listed out in this table below:
1. Common Global Counters
| Counter Name | Counter Description |
| IPV4_SANITY_ADDR_CHK_FAILURES | Ingress IPV4 address martian check failure 127.0.0.0/8 224.0.0.0/8, not 224.0.0.0/4 (225.0.0.0/8 and 239.0.0.0/8 don't increment error count) When source address is below, ASR9K forward the packet without any error. 0.0.0.0/8 10.0.0.0/8 128.0.0.0/16 169.254.0.0/16 172.16.0.0/12 191.255.0.0/16 192.0.0.0/24 223.255.255.0/24 240.0.0.0/4 |
| DROP_IPV4_LENGTH_ERROR | Ingress IPV4 header length invalid or frame length incompatible with fragment length |
| DROP_IPV4_CHECKSUM_ERROR | Ingress IPV4 checksum invalid |
| IPV6_SANITY_ADDR_CHK_FAILURES | Ingress IPV6 frame source or destination address invalid |
| DROP_IPV6_LENGTH_ERROR | Ingress IPV6 frame length invalid |
| MPLS_TTL_ERROR | Ingress MPLS frame outer label TTL is 0 |
| MPLS_EXCEEDS_MTU | MPLS TTL exceeded – punt frame to host |
| DROP_IPV4_NOT_ENABLED | Ingress IPV4 frame and IPV4 not enabled in L3 ingress intf struct |
| DROP_IPV4_NEXT_HOP_DOWN | Drop bit set in rx adjacency (ingress) or tx adjacency (egress) and ICMP punt disabled in intf struct (ingress/egress) for the interface – drop bit in non-recursive adjacency or adjacency result |
| IPV4_PLU_DROP_PKT | Drop bit set in leaf or non-recursive adjacency lookup miss (ingress/egress) and ICMP punt disabled in intf struct (ingress/egress) for the interface. |
| IPV4_RP_DEST_DROP | IPV4 RP drop bit set in non-recursive adjacency or adjacency result and ICMP punt disabled in intf struct (ingress/egress) for the interface |
| IPV4_NULL_RTE_DROP_PKT | No IPV4 route (ingress/egress) and ICMP punt disabled in intf struct (ingress/egress) for the interface – null route set in leaf or recursive adjacency |
| DROP_IPV6_NOT_ENABLED | Ingress IPV6 frame and IPV6 not enabled in L3 ingress intf struct |
| DROP_IPV6_NEXT_HOP_DOWN | Drop bit set in rx adjacency (ingress) or tx adjacency (egress) and ICMP punt disabled in intf struct (ingress/egress) for the interface – drop bit in non-recursive adjacency or adjacency result |
| DROP_IPV6_PLU | Drop bit set in leaf or non-recursive adjacency lookup miss (ingress/egress) and ICMP punt disabled in intf struct (ingress/egress) for the interface. |
| IPV6_RP_DEST_DROP | RP drop bit set in non-recursive adjacency or adjacency result and ICMP punt disabled in intf struct (ingress/egress) for the interface |
| IPV6_NULL_RTE_DROP_PKT | No IPV6 route (ingress/egress) and ICMP punt disabled in intf struct (ingress/egress) for the interface – null route set in leaf or recursive adjacency |
| MPLS_NOT_ENABLED_DROP | Ingress MPLS frame and MPLs not enabled in L3 ingress intf struct |
| MPLS_PLU_NO_MATCH | Ingress MPLS frame and outer label lookup miss and not a VCCV frame associated with a pseudo-wire |
| MPLS_PLU_DROP_PKT | Ingress MPLS frame and label lookup results return a NULL route, or have no forwarding control bits set, OR one of the following: 1) Next hop down – Drop bit set in rx adjacency (ingress) or tx adjacency (egress) and ICMP punt disabled in intf struct (ingress/egress) for the interface – drop bit in non-recursive adjacency or adjacency result 2) Leaf drop - Drop bit set in leaf or non-recursive adjacency lookup miss (ingress/egress) and ICMP punt disabled in intf struct (ingress/egress) for the interface. 3) RP drop - RP drop bit set in non-recursive adjacency or adjacency result and ICMP punt disabled in intf struct (ingress/egress) for the interface 4) No route - No route (ingress/egress) and ICMP punt disabled in intf struct (ingress/egress) for the interface – null route set in leaf or recursive adjacency 5) Punt bit set in leaf results or recursive adjacency results – egress mpls punt not supported |
| MPLS_UNSUPP_PLU_LABEL_TYPE | Ingress MPLS frame outer label is 15 or less and not a router alert or null tag. |
| DEAGG_PKT_NON_IPV4 | Ingress MPLS frame outer label lookup control bits are L3VPN deagg. And the payload is not IPV4. |
2. NP debug and drop counters
- Bulk Forwarding Counts
- Inject/Punt type counts
- Main Drop counts
- QOS/ACL drop counts
| Counter Name | Counter Description |
| PARSE_ENET_RECEIVE_CNT | Total frames received from Ethernet on an ingress NP |
| PARSE_FABRIC_RECEIVE_CNT | Total frames received by an egress NP from the fabric – Note that this currently includes loopback frames |
| MODIFY_FABRIC_TRANSMIT_CNT | Total frames sent to fabric by an ingress NP |
| MODIFY_ENET_TRANSMIT_CNT | Total frames sent to Ethernet by an egress NP |
| PARSE_LOOPBACK_RECEIVE_CNT | Total loopback frames received by an NP – Note that these are egress loopback frames only and do not include ingress loopback frames such as Interflex |
| PARSE_INTERFLEX_RECEIVE_CNT | Total frames received by an NP from the interflex loopback port – these are ingress loopback frames |
| MODIFY_FRAMES_PADDED_CNT | Total number of frames sent to fabric that were undersized and required padding to 60 bytes. |
| MODIFY_RX_SPAN_CNT | Ingress frames sent to fabric on a SPAN link – these frames are replicated |
| MODIFY_TX_SPAN_CNT | Egress frames sent to Ethernet on a SPAN link – these frames are replicated |
| MODIFY_LC_PUNT_CNT | Total frames punted to LC host (all punts are handled by the modify engine) |
| MODIFY_RP_PUNT_CNT | Total frames punted to RP host (all punts are handled by the modify engine) |
| MODIFY_PUNT_DROP_CNT | Total punt packets dropped by ingress modify engine due to punt policing, OR due to punt reason lookup fail. |
| MODIFY_LC_PUNT_EXCD_CNT | Punt frames to LC dropped due to punt policing |
| MODIFY_RP_PUNT_EXCD_CNT | Punt frames to RP dropped due to punt policing |
| PARSE_INGRESS_DROP_CNT | Total packets dropped by ingress NP in the parse engine |
| PARSE_EGRESS_DROP_CNT | Total packets dropped by egress NP in the parse engine |
| RESOLVE_INGRESS_DROP_CNT | Total packets dropped by ingress NP in the resolve engine |
| RESOLVE_EGRESS_DROP_CNT | Total packets dropped by egress NP in the resolve engine |
| MODIFY_INGRESS_DROP_CNT | Total packets dropped by ingress NP in the modify engine |
| MODIFY_EGRESS_DROP_CNT | Total packets dropped by ingress NP in the modify engine |
| PARSE_INGRESS_PUNT_CNT | Total packets flagged for punting by the ingress NP in the parse engine |
| PARSE_EGRESS_PUNT_CNT | Total packets flagged for punting by the egress NP in the parse engine |
| RESOLVE_INGRESS_L3_PUNT_CNT | Total Layer3 packets flagged for punting by an ingress NP in the resolve engine due to lookup results or other cases such as ICMP unreachable |
| RESOLVE_INGRESS_IFIB_PUNT_CNT | Total Layer3 packets flagged for punting due to an ingress IFIB lookup match |
| RESOLVE_INGRESS_L2_PUNT_CNT | Total Layer2 packets flagged for punting by the egress NP in the resolve engine due to cases such as IGMP/DHCP snooping or punting of ingress L2 protocol such as LAG or MSTP or CFM |
| RESOLVE_EGRESS_L3_PUNT_CNT | Total Layer3 packets flagged for punting by an ingress NP in the resolve engine due to lookup results or other cases such as ICMP unreachable |
| RESOLVE_EGRESS_L2_PUNT_CNT | Total Layer2 packets flagged for punting by the egress NP in the resolve engine due to cases such as IGMP/DHCP snooping or punting of ingress L2 protocol such as MSTP or CFM |
| PARSE_LC_INJECT_TO_FAB_CNT | Frames injected from LC host that are intended to go directly to fabric to an egress LC without modification or protocol handling (inject header is stripped by microcode) |
| PARSE_LC_INJECT_TO_PORT_CNT | Frames injected from LC host that are intened to go directly to an Ethernet port without modification or protocol handling (inject header is stripped by microcode) |
| PARSE_FAB_INJECT_IPV4_CNT | Total number of IPV4 inject frames received by the egress NP from the fabric (sent from RP) |
| PARSE_FAB_INJECT_PRTE_CNT | Total number of layer 3 preroute inject frames received by the egress NP from the fabric (sent from RP) |
| PARSE_FAB_INJECT_UNKN_CNT | Total number of unknown inject frames received by the egress NP from the fabric (sent from RP). These are punted to the LC host. |
| PARSE_FAB_INJECT_SNOOP_CNT | Total number of IGMP/DHCP snoop inject frames received by the egress NP from the fabric (sent from RP). For DHCP, these are always re-injects from the RP. For IGMP, these can be re-injects or originated injects from the RP. |
| PARSE_FAB_INJECT_MPLS_CNT | Total number of mpls inject frames received by the egress NP from the fabric (sent from RP). |
| PARSE_FAB_INJECT_IPV6_CNT | Total number of IPV6 inject frames received by the egress NP from the fabric (sent from RP) |
| INJECT_EGR_PARSE_PRRT_NEXT_HOP | Inject preroute frames received from the fabric that are next hop type. |
| INJECT_EGR_PARSE_PRRT_PIT | Inject preroute frames received from the fabric that are PIT type . |
| L3_EGR_RSV_PRRT_PUNT_TO_LC_CPU | Inject preroute frames that have a PIT table lookup miss. These are punted to the LC host. |
| L2_INJECT_ING_PARSE_INWARD | Total number of ingress CFM injects received from the LC host that are intended to be sent to the fabric. These can either be bridged or pre-routed to a specific NP. |
| CFM_L2_ING_PARSE_BRIDGED | Total number of ingress CFM injects received from the LC host that are intended to be bridged and sent to the fabric. The bridge lookups are done for these inject frames resulting in unicast or flood traffic. |
| L2_INJECT_ING_PARSE_PREROUTE | Total number of ingress CFM injects received from the LC host that are intended to be pre-routed to a specific output port on an egress NP. bridged and sent to the fabric. The bridge lookups are not done for these inject frames. |
| L2_INJECT_ING_PARSE_EGRESS | Total number of ingress CFM injects received from the LC host that are intended to be sent to a specific output port on an egress NP. |
| INJ_UNKNOWN_TYPE_DROP | Unknown ingress inject received from the LC host – these are dropped. |
| STATS_STATIC_PARSE_INTR_AGE_CNT | Total Number of Parse Interrupt frames associated with learned MAC address aging. |
| STATS_STATIC_PARSE_INTR_STATS_CNT | Total Number of Parse Interrupt frames associated with statistics gathering. |
| PARSE_VIDMON_FLOW_AGING_SCAN_CNT | Total Number of Parse Interrupt frames associated with video monitoring flow scanning. |
| UNSUPPORTED_INTERRUPT_FRAME | Unsupported interrupt frame type received on NP. Supported types are for aging and statistics only. |
| RESOLVE_BAD_EGR_PRS_RSV_MSG_DROP_CNT | Invalid parse engine to resolve engine message received for an ingress frame – this is likely a software implementation error. |
| RESOLVE_BAD_ING_PRS_RSV_MSG_DROP_CNT | Invalid parse engine to resolve engine message received for an egress frame – this is likely a software implementation error. |
| EGR_UNKNOWN_PAK_TYPE | A frame received from the fabric by an egress NP has an unknown NPH header type – these are dropped. This is likely a software implementation error. |
| EGR_LB_UNKNOWN_PAK_TYPE | A frame received from the egress loopback queue by an egress NP has an unknown NPH header type – these are dropped. This is likely a software implementation error. |
| XAUI_TRAINING_PKT_DISCARD | These are diag packets sent to the egress NP at startup from the fabric FPGA. These are ignored and dropped by software. |
| PRS_DEBUGTRACE_EVENT | This counter increments whenever a preconfigured debug trace event matches on an ingress or egress frame. Currently the debug trace is only configurable for all drop events. |
| IN_INTF STRUCT_TCAM_MISS | Ingress frame with a pre-parse TCAM lookup miss – these are dropped. This is likely due to a TCAM setup problem. |
| IN_INTF STRUCT_NO_ENTRY | Ingress frame with a pre-parse TCAM index that is invalid – these are dropped. This is likely due to a TCAM setup problem |
| IN_INTF STRUCT_DOWN | Ingress frame with a intf struct entry with down status – these are dropped, with the exeception of ingress LACP frames on a subinterface. |
| OUT_INTF STRUCT_INTF STRUCT_DOWN | Egress Layer3 frame with an egress INTF STRUCT that has line status down, and ICMP punt is disabled in the intf struct. |
| IN_L2_INTF STRUCT_DROP | Ingress Layer2 frame on a subinterface with the L2 intf struct drop bit set. |
| ING_VLAN_FILTER_DISCARD | A vlan tagged packet has a intf struct index that does points to a default layer3 intf struct – these are dropped. Only untagged pkts can be setup on a default layer3 intf struct. |
| IN_FAST_DISC | A ingress frame was dropped due to the early discard feature. This can occur at high ingress traffic rate based on the configuration. |
| UNKNOWN_L2_ON_L3_DISCARD | Unknown Layer2 frame (non-IPV4/V6/MPLS) on a Layer3 interface. These are dropped. Known layer2 protocols are punted on a layer3 interface such as ARP/LACP/CDP/ISIS/etc. |
| L3_NOT_MYMAC | A layer3 unicast IPV4/IPV6 frame does not have the destination mac address of the router, or any mac address defined in the VRRP table. These are dropped. |
| IPV4_UNICAST_RPF_DROP_PKT | With RPF enabled, an ingress IPV4 frame has a source IP address that is not permitted, or not permitted on the ingress interface – these are dropped. |
| RESOLVE_L3_ING_PUNT_IFIB_DROP | Ingress frame has TTL of 0, or discard BFD frame if BFD not enabled |
| MPLS_VPN_SEC_CHECK_FAIL | An ingress MPLS does not have the proper VPN security code, and IPV4 is not using the global routing table. |
| MPLS_EGR_PLU_NO_MATCH | MPLS frame outer label lookup on egress NP does not match – these are dropped. |
| MPLS_EGR_PLU_DROP_PKT | MPLS frame outer label lookup on egress NP has a result with the drop bit set. |
| RESOLVE_EGR_LAG_NOT_LOCAL_DROP_CNT | An egress frame hash to a bundle interface has a bundle member that is not local to the NP – these are dropped. This can be due to a bad hash, or a bad bundle member index. It can also occur normally for floods or multicast – non-local members are dropped for each copy that is a bundle output. |
| RESOLVE_L3_ING_ERROR_DROP_CNT | L3 ingress protocol handling in the resolve engine falls through to an invalid case – these are dropped. This would occur due to a software implementation error. |
| RESOLVE_L3_EGR_ERROR_DROP_CNT | L3 egress protocol handling in the resolve engine falls through to an invalid case – these are dropped. This would occur due to a software implementation error. |
| ING_QOS_INVALID_FORMAT | An ingress packet has a QOS format value in the ingress intf struct that is not valid. Only checked if QOS is enabled in the ingress intf struct. Valid formats are 20/3/2/1/0. |
| RESOLVE_L3_ING_ACL_DENY_DROP_CNT | Total number of ingress Layer3 frames dropped due to an ACL deny policy. |
| RESOLVE_L3_EGR_ACL_DENY_DROP_CNT | Total number of egress Layer3 frames dropped due to an ACL deny policy. |
| RESOLVE_L2_ING_ACL_DENY_DROP_CNT | Total number of ingress Layer2 frames dropped due to an ACL deny policy. |
| RESOLVE_L2_EGR_ACL_DENY_DROP_CNT | Total number of egress Layer2 frames dropped due to an ACL deny policy. |
| RESOLVE_L2L3_QOS_C_DROP_CNT | Total number of ingress/egress frames dropped to a child policing policy. |
| RESOLVE_L2L3_QOS_P_DROP_CNT | Total number of ingress/egress frames dropped to a parent policing policy. |
Layer3 Multicast related counts
These include:
- IP mcast forwarding counts
- Video Monitoring counts
- Multicast Fast Reroute counts
| Counter Name | Counter Description |
| IPV4_MCAST_NOT_ENABLED | Ingress IPV4 frames dropped due to ipv4 multicast not enabled. The ipv4 multicast enable check may be ignored for non-routable IGMP frames. Also, the ipv4 multicast enable check does not apply to well known multicast frames. |
| IPV6_MCAST_UNSUPPORTED_DROP | Ingress IPV6 multicast frame and IPV6 multicast not supported in the current release |
| RESOLVE_IPM4_ING_RTE_DROP_CNT | Ingress IPV4 multicast frame route lookup fails with no match. |
| RESOLVE_IPM4_EGR_RTE_DROP_CNT | Egress IPV4 multicast frame route lookup fails with no match. |
| RESOLVE_IPM4_NO_OLIST_DROP_CNT | Egress IPV4 multicast frame has zero olist members – no copies are sent to output ports. |
| RESOLVE_IPM4_OLIST_DROP_CNT | Egress IPV4 multicast frame has olist drop bit set (no copies are sent to output ports), OR egress IPV4 multicast frame olist lookup fails. Olist lookup failure could be due to a bad copy number, or a missing entry for that copy. |
| RESOLVE_IPM4_FILTER_DROP_CNT | Egress IPV4 multicast frame copy is reflection filtered – copies to the original source port are dropped. |
| RESOLVE_IPM4_TTL_DROP_CNT | Egress IPV4 multicast frame copy fails TTL check. The frame TTL is beyond the programmed threshold. |
| MODIFY_RPF_FAIL_DROP_CNT | Ingress IPV4 multicast frames dropped due to reverse-path-forwarding check failed (to prevent looping or duplicated packets); these multicast frames came in from wrong interface. |
| RESOLVE_VIDMON_FLOWS_DELETED_BY_AGING | Inactive Video Monitoring flows deleted by hardware aging mechanism. |
| RESOLVE_VIDMON_CLASS_FLOW_LIMIT_REACHED | Indicates that the Video Monitoring Maximum flows per class limit reached. |
| RESOLVE_VIDMON_FLOW_START_INTRVL_RESET | Video Monitoring flow start interval reset to current Real Time Clock Tick (instead of updating with actual next packet arrival time) because the flow has been inactive for more than 3 interval timeouts. |
| VIDMON_PUNT_FAILED_NO_TXBUF_CNT | Punt frames dropped by Video Monitoring due to no buffer |
| PARSE_MOFRR_WATCHDOG_INTR_RCVD | L3 Multicast Fast Reroute Watchdog interrupts received by nP. The count is summation of both Activity and Loss interrupt counts. |
| PARSE_MOFRR_SWITCH_MSG_RCVD_FROM_FAB | Number of L3 Multicast Fast Reroute Switch (Flood) messages received by nP from Fabric. |
| RESOLVE_MOFRR_HRT_LKUP_FAIL_DROP | Number of watchdog interrupts are dropped because of an error in MoFRR Hash Table lookup. This counter indicates that the watchdog interrupt (Activity or Loss) is received but micro code failed to process further because of MoFRR Hash look up failed. This counter indicates an error. |
| RESOLVE_MOFRR_WDT_INVALID_RESULTS_DROP_CNT | Number of watchdog interrupts are dropped because of an error in Watch Dog counter hash table lookup. This counter indicates that the watchdog interrupt (Activity or Loss) is received but micro code failed to process further because of lookup failed. This counter indicates an error. |
| RESOLVE_MOFRR_SWITCH_MSG_HRT_LKUP_FAIL_DROP | Number of MoFRR switch messages are dropped because of an error with MoFRR Hash Table lookup failure. This counter indicates that the switch message is received from fabric but micro code failed to process further because of MoFRR Hash look up failed. This counter indicates an error and could be traffic disruptive. |
| RESOLVE_MOFRR_SWITCH_MSG_SEQNUM_MISMATCH_DROP | Number of MoFRR switch messages are dropped because of sequence number mismatch. This counter indicates that the switch message is received from fabric but micro code failed to process further the sequence number received from ingress LC does not match with sequence number for same route on egress LC. This counter indicates a programming error, race condition or hash result corruption in micro code etc. This is not a usual thing and could be traffic disruptive. |
| RESOLVE_MOFRR_HASH_UPDATE_CNT | Number of times MoFRR active flag is updated in MoFRR hash table. This counter indicates the switch message is processed successfully, i.e. RDT/Hash/Direct table lookups are successful and MoFRR Active flag is updated in MoFRR hash table. |
| RESOLVE_MOFRR_SWITCH_MSG_INGNORED | Total numbers of MoFRR switch (flood) messages are filtered without being punted to LC CPU. This counter indicates switch message is processed successfully (i.e. lookups successful and MoFRR flag is updated in hardware hash table), but the message is not punted to LC CPU either because the RPF Id is not primary or RPF Id is not local to the nP. Note that this counter is informative and does not necessarily mean an error. |
| RESOLVE_MOFRR_SWITCH_MSG_TO_FAB | Number of MoFRR switch (flood) messages generated by nP as a result of Loss Activity interrupts. This counter indicates that the Loss Activity interrupt is processed successfully by ingress LC and MoFRR switch message is flooded to all LCs towards fabric. |
| RESOLVE_MOFRR_EGR_RPF_FAIL_DROP | IP Multicast MoFRR enabled packets dropped at egress LC because of RPF check failure. |
Layer 2 protocol Debug Counters
These include: · VPLS counts · VPWS counts · DHCP/IGMP snooping counts · CFM protocol counts · VPLS Learning/Aging related counts
| Counter Name | Counter Description |
| IN_L2_BLOCKED | Ingress L2 frames dropped and not forwarded due to ingress interface in spanning tree blocked state. |
| OUT_L2_BLOCKED | Egress L2 frames dropped and not forwarded due to egress interface in spanning tree blocked state. |
| IN_DOT1Q_VTP_FILTERED | Ingress VTP frames dropped due to dot1q filtering enabled. |
| IN_DOT1Q_DROP | Ingress 802.1q frames dropped due to dot1q filtering enabled. |
| IN_DOT1AD_DROP | Ingress 802.1ad frames dropped due to dot1ad filtering enabled. |
| ING_SLOW_PROTO_UNKNOWN_SUBTYPE | Ingress slow protocol frame on an L3 interface that is not recognized (not LACP/EFM/SYNCE). |
| IN_ROUTER_GUARD_DROP | Ingress Layer2 IGMP or PIM dropped due to Router Guard with IGMP snooping enabled. |
| IN_DHCP_UNTRUSTED_DROP | Ingress DHCP frame dropped due to the untrusted DHCP bit set in the ingress L2 intf struct. |
| RESOLVE_L2_DHCP_SNOOP_UNTRUSTED_DROP_CNT | Egress DHCP frame dropped due to the untrusted DHCP bit set in the egress L2 intf struct. |
| ING_DHCP_PW_DROP | Ingress DHCP frame from AC that is destined for a PW and is eligible for snooping due to the DHCP snoop enabled bit set in the L2 ingress INTF STRUCT. This is dropped on ingress due to an L2 unicast to PW. DHCP snooping not supported for AC to PW frames. |
| EGR_DHCP_PW_DROP | Ingress DHCP frame from AC that is destined for a PW and is eligible for snooping due to the DHCP snoop enabled bit set in the L2 ingress INTF STRUCT. This is dropped on egress due to an L2 flood with a PW member. DHCP snooping not supported for AC to PW frames. |
| L2VPN_DEAGG_NON_VPWS_VPLS_DROP | Invalid setting for L2VPN deaggregation set in Label UFIB lookup result for ingress MPLS frame. This is most likely due to a programming error in the Label UFIB entry. |
| XID_ZERO_DISCARD | Ingress VPWS XC to AC frame has a zero destination XID stored in the L2 ingress INTF STRUCT – zero XID index is invalid. |
| XC2AC_NOMATCH_DROP | Egress VPWS XC to AC frame XID lookup fails. This is caused by an invalid XID index or missing XID entry. |
| L2UNIC_NOMATCH_DROP | Egress VPLS AC to AC frame XID lookup fails. This is caused by an invalid XID index or missing XID entry. This can also occur on an IGMP snoop originated inject to an AC/PW/Bundle with invalid XID in the inject feature header. |
| L2FLOOD_NOMATCH_DROP | Egress VPLS flood copy lookup in the flood member table fails. This could be caused by an invalid copy number or missing entry in the flood member table for that copy. |
| L2FLOOD_SRCDST_DROP | Egress VPLS flood copy is reflection filtered – copies to the original source port are dropped. |
| L2FLOOD_INACTIVE_MEMBER_DROP | Egress VPLS flood copy lookup in the flood member table returns an entry that’s not active (active bit in result is cleared). |
| L2FLOOD_EGR_XID_NO_MATCH | Egress VPLS flood copy XID lookup fails – XID stored in the OLIST result is invalid or entry is missing. This can occur if the copy is intended to go over a PW and the PW is down. |
| EGR_AC_PW_MISMATCH | Egress VPWS XC to AC XID lookup returns a PW type. For VPWS, PW entry is always on ingress. Note that for VPLS AC to AC, a PW type XID is allows in order to support IGMP injects to a PW. |
| RESOLVE_VPWS_LAG_BIT_DROP_CNT | An ingress VPWS XC to Bundle frame with a LAG table lookup fail. This is due to programming error where the LAG table pointer is invalid or no LAG table entry. |
| RESOLVE_L2_SXID_MISS_DROP_CNT | An ingress VPLS frame with a source XID lookup fail. This can be due to an invalid source XID programmed in the L2 ingress intf struct, or a missing source XID entry. |
| RESOLVE_VPLS_SPLIT_HORIZON_DROP_CNT | An ingress or egress VPLS that is dropped due to a split horizon group mismatch. Note that the split horizon group check is skipped for zero split horizon group indexes. |
| RESOLVE_VPLS_REFLECTION_FILTER_DROP_CNT | An ingress unicast VPLS frame that has a source XID that matches its destination XID. These are dropped since it cannot be sent back to the source port. |
| RESOLVE_VPLS_MAC_FILTER_DROP_CNT | An ingress VPLS frame has a source or destination MAC with the filter bit set in the L2FIB result – these are dropped. |
| RESOLVE_VPLS_ING_BD_STR_MISS_DROP_CNT | An ingress VPLS frame that is dropped due to a bridge domain lookup fail. |
| RESOLVE_VPLS_EGR_BD_STR_MISS_DROP_CNT | An egress VPLS flood frame or mac notify frame that is dropped due to a BD structure lookup miss. |
| RESOLVE_VPLS_FLOOD_BLOCK_DROP_CNT | An Ingress VPLS frame that is dropped due to its associated flood block bit being set: Unknown Unicast or Multicast. |
| RESOLVE_VPLS_STORM_DROP_CNT | An ingress VPLS frame that is dropped due to rate exceed for its associated flood storm control – Unknown Unicast or Multicast or Broadcast. |
| RESOLVE_VPLS_EGR_FLD_NO_MEMBERS_DROP_CNT | Egress L2 flood frame has zero members – no copies are sent to output ports. |
| RESOLVE_L2_EGR_INTF STRUCT_MISS_DROP_CNT | An egress VPLS unicast or flood copy frame to an AC or Bundle that is dropped to an egress L2 INTF STRUCT lookup miss. This is due to an invalid INTF STRUCT index in the XID or a missing egress L2 INTF STRUCT entry. This can also occur with L2 multicast forwarded frames or L2 multicast inject frames. |
| RESOLVE_L2_EGR_PW_INTF STRUCT_MISS_DROP_CNT | An egress VPLS unicast or flood copy frame to a PW that is dropped to an egress L2 INTF STRUCT lookup miss. This is due to an invalid INTF STRUCT index in the XID or a missing egress L2 INTF STRUCT entry. This can also occur if the PW is down. . This can also occur with L2 multicast forwarded frames or L2 multicast inject frames to a PW. |
| RESOLVE_VPWS_L2VPN_LDI_MISS_DROP_CNT | An ingress VPWS or VPLS unicast frame to a PW with an L2VPN LDI table lookup fail. This can be due to an invalid L2VPN LDI index in the XID, or a missing entry in the L2VPN LDI table. |
| RESOLVE_VPWS_RP_DROP_CNT | An ingress VPWS or VPLS unicast frame to a PW with the RP drop bit or RP dest. bit set in the NON-RECURSIVE ADJACENCY or RX-ADJ lookup results. Punts are not supported for an L2 PW adjacency. |
| RESOLVE_VPWS_NULL_ROUTE_DROP_CNT | An ingress VPWS or VPLS unicast frame to a PW with the Null Route bit or IFIB punt bit set in the Leaf lookup or RECURSIVE ADJACENCY lookup results. Punts are not supported for an L2 PW adjacency. |
| RESOLVE_VPWS_LEAF_DROP_CNT | An ingress VPWS or VPLS unicast frame to a PW with the Drop bit or Punt bit set in the Leaf lookup or RECURSIVE ADJACENCY lookup results. Punts are not supported for an L2 PW adjacency. |
| RESOLVE_VPLS_EGR_NULL_RTE_DROP_CNT | An egress VPLS flood frame copy to a PW with the Null Route bit set in the Leaf lookup or RECURSIVE ADJACENCY lookup results. Also includes IGMP snoop injects to a PW. Due to a software problem, this may also get incremented due to a BD structure lookup miss on egress flood. |
| RESOLVE_VPLS_EGR_LEAF_IFIB_DROP_CNT | An egress VPLS flood frame copy to a PW with the IFIB punt bit set in the Leaf lookup or RECURSIVE ADJACENCY lookup results. Punts are not supported for an L2 PW adjacency. Also includes IGMP snoop injects to a PW. |
| RESOLVE_VPLS_EGR_LEAF_PUNT_DROP_CNT | An egress VPLS flood frame copy to a PW with the Drop bit or Punt bit or Next Hop Down bit set in the Leaf lookup or RECURSIVE ADJACENCY or NON-RECURSIVE ADJACENCY lookup results. Punts are not supported for an L2 PW adjacency. Also includes IGMP snoop injects to a PW. |
| RESOLVE_VPLS_EGR_TE_LABEL_DROP_CNT | An egress VPLS flood frame copy to a PW with the Drop bit or Punt bit or Incomplete Adjacency bit set in the Tx adjacency or Backup Adjacency or NH Adjacency lookup results. Punts are not supported for an L2 PW adjacency. Also includes IGMP snoop injects to a PW. |
| RESOLVE_VPLS_EGR_PW_FLOOD_MTU_DROP_CNT | An egress VPLS flood frame copy to a PW that fails L3 MTU check. Punts are not supported for an L2 PW adjacency with MTU fail. Also includes IGMP snoop injects to a PW. |
| RESOLVE_VPLS_EGR_PW_FLOOD_INTF STRUCT_DOWN_DROP_CNT | An egress VPLS flood frame copy to a PW with egress INTF STRUCT in down state. Punts are not supported for an L2 PW adjacency with line status down. Also includes IGMP snoop injects to a PW. |
| RESOLVE_VPLS_EGR_PW_FLOOD_NO_NRLDI_DROP_CNT | An egress VPLS flood frame copy to a PW with and NON-RECURSIVE ADJACENCY lookup miss. Also includes IGMP snoop injects to a PW. |
| RESOLVE_INGRESS_LEARN_CNT | Total number of VPLS Source MAC learns on an ingress frame – learned locals. |
| PARSE_FAB_MACN_W_FLD_RECEIVE_CNT | Count of all frames received from fabric on egress LC with NPH L2 flood type and mac notify included (mac notify for ingress SA learn included with L2 flood) |
| PARSE_FAB_MACN_RECEIVE_CNT | Count of all frames received from fabric on egress LC with NPH mac notify flood type (mac notify for ingress SA learn). This includes: 1) forward mac notifies (from ingress LC) 2) reverse mac notifies (from egress LC in response to flood 3) mac deletes (due to a mac move or port flush) |
| PARSE_FAB_DEST_MACN_RECEIVE_CNT | Count of all mac notify frames received from fabric on egress LC that are reverse mac notify type |
| PARSE_FAB_MAC_DELETE_RECEIVE_CNT | Count of all mac notify frames received from fabric on egress LC that are mac delete type |
| RESOLVE_LEARN_FROM_NOTIFY_CNT | Total number of VPLS Source MAC learns from mac notify received. |
| RESOLVE_VPLS_MAC_MOVE_CNT | Total number of source MAC moves detected as a result of an ingress learn local or mac notify receive learn. |
| RESOLVE_BD_FLUSH_DELETE_CNT | Total number of learned entries deleted due to a Bridge Domain Flush |
| RESOLVE_INGRESS_SMAC_MISS_CNT | Total number of ingress frames with source MACs that did have a learned entry. These source MACs will be relearned if learned limits have not been exceeded, learning is enabled, and the address is unicast. |
| RESOLVE_VPLS_MCAST_SRC_MAC_DROP_CNT | Total number of ingress frames with source MACs that were not unicast. These frames are invalid and are are dropped. Non-unicast source macs cannot be learned. |
| RESOLVE_HALF_AGE_RELEARN_CNT | Total mac address from ingress frames that were relearned due to exceeding the half age period. These entries are refreshed to update the age timeout. |
| STATS_STATIC_PARSE_PORTFLUSH_CNT | Egress VPLS frame that has been detected as port flushed. Not valid if port based mac accounting is disabled. The frame will be dropped and mac delete indication sent to the bridge domain. |
| RESOLVE_PORT_FLUSH_DROP_CNT | Egress unicast frames dropped because the destination port has been flushed. For each a Mac Delete frame is sent to the bridge domain to remove the destination address. |
| RESOLVE_PORT_FLUSH_DELETE_CNT | Count of learned MACs deleted due to their source port being flushed. Does not include MACs deleted due to MAC Delete message. |
| RESOLVE_PORT_FLUSH_AGE_OUT_CNT | VPLS MAC entries that have been port flushed as detected by the MAC aging scan. These frames are dropped. Also can occur if the frame XID lookup fails and the XID is global or learned local – XID has been removed. |
| RESOLVE_VPLS_LEARN_LIMIT_ACTION_DROP_CNT | Ingress VPLS Frames dropped to learned limit exceeded – port based or bridge domain based learn limits – these frames are dropped. |
| RESOLVE_VPLS_STATIC_MAC_MOVE_DROP_CNT | A static MAC entry that are deleted due to a MAC move detected – these should never move. |
| RESOLVE_MAC_NOTIFY_CTRL_DROP_CNT | Total number of processed mac notify frames – forward or reverse mac notify – dropped after processing. |
| RESOLVE_MAC_DELETE_CTRL_DROP_CNT | Total number of processed mac delete frames – forward or reverse mac notify – dropped after processing. |
| RESOLVE_AGE_NOMAC_DROP_CNT | MAC scan aging message dropped due to an L2FIB lookup fail for the scanned mac entry. |
| RESOLVE_AGE_MAC_STATIC_DROP_CNT | MAC scan aging message dropped due to static MAC address for the scanned mac entry. |
| EGR_VLANOPS_DROP | Egress L2 frame without the proper number of vlans to do egress VLAN ops – the frame from the fabric needs at least one vlan to do a pop operation or replace operation. |
| EGR_PREFILTER_VLAN_DROP | Egress L2 frame that fails EFP pre-filter check – only valid if EFP filtering enabled – attached VLAN mismatch. |
| RESOLVE_EFP_FILTER_TCAM_MISS_DROP | Egress L2 frame that fails EFP filter TCAM – only valid if EFP filtering enabled – likely due to a TCAM missing entry due to a programming error. |
| RESOLVE_EFP_FILTER_MISS_MATCH_DROP | Egress L2 frame that fails EFP filter check – only valid if EFP filtering enabled – attached VLAN mismatch. |
| CFM_ING_PUNT | Ingress CFM frame punt count. |
| CFM_EGR_PUNT | Egress CFM frame punt count. |
| CFM_EGR_PARSE | Total egress Layer2 CFM frames processed by the NP – including egress CFM inject and egress CFM forwarded frames. |
| INJ_NO_XID_MATCH_DROP | Ingress CFM frame injects with an XID lookup fail – source XID for bridged injects, and dest. XID for pre-route injects – invalid XID index or missing entry. |
| EGR_CFM_XID_NOMATCH | Egress CFM frame inject with a dest. XID lookup fail – invalid XID index or missing entry. |
| EGR_CFM_PW_DROP | Egress CFM frame injected to a PW – not supported. |
| PARSE_INGRESS_L3_CFM_DROP_CNT | Ingress CFM frame on a layer 3 interface dropped due to CFM not enabled. |
| RESOLVE_VPLS_MC_ING_RTE_DROP_CNT | Ingress L2 multicast frame route lookup fails with no match. |
| RESOLVE_VPLS_MC_EGR_RTE_DROP_CNT | Egress L2 multicast frame route lookup fails with no match. |
| RESOLVE_VPLS_MC_NO_OLIST_DROP_CNT | Egress L2 multicast frame has zero olist members – no copies are sent to output ports. |
| EGR_L2MC_OLIST_NOMATCH | Egress L2 multicast frame has olist drop bit set (no copies are sent to output ports), OR egress L2 multicast frame olist lookup fails. Olist lookup failure could be due to a bad copy number, or a missing entry for that copy. |
| EGR_L2MC_SRCDST | Egress L2 multicast frame copy is reflection filtered – copies to the original source port are dropped. |
| EGR_L2MC_XID_NOMATCH | Egress L2 multicast frame copy XID lookup fails – XID stored in the OLIST result is invalid or entry is missing. This can occur if the copy is intended to go over a PW and the PW is down. |
| RESOLVE_L2_PROT_BYTE_ERROR_DROP_CNT | Invalid L2 protocol action set – this is an internal software programming error on an ingress or egress L2 frame if incremented. |
| RESOLVE_VPLS_ING_ERR_DROP_CNT | An ingress VPLS frame has an invalid processing type. This is likely an internal error in software. |
| RESOLVE_VPLS_EGR_STRUCT_MISS_DROP_CNT | Egress VPLS frame protocol handling falls through to an invalid case. This is likely a software implementation error. |
3. Punt Reason Counters
For each punt reason, there are 2 counters. The total number of frames attempted to be punted by microcode is the sum of these 2 counters.
- Actual punted
- Punt drops due to policing
If the punt reason lookup fails, then software will drop the packet with MODIFY_PUNT_DROP_CNT increment. A layer3 interface is either a router gateway or a default interface for untagged frames (or both).
| Counter Name | Counter Description |
| PUNT_INVALID PUNT_INVALID_DROP | Invalid Punt Reason – this should not occur. |
| PUNT_ALL PUNT_ALL_EXCD | Punt All Set – not implemented by software. |
| CDP CDP_EXCD | Punt Ingress CDP protocol frames – layer3 interface only. |
| ARP ARP_EXCD | Punt Ingress ARP protocol frames – layer3 interface only. |
| RARP RARP_EXCD | Punt Ingress Reverse ARP protocol frames – layer3 interface only. |
| CGMP CGMP_EXCD | Punt Ingress CGMP protocol frames – layer3 interface only. |
| LOOP LOOP_EXCD | Punt Ingress ELOOP protocol frames – layer3 interface only. |
| CFM_OTHER CFM_OTHER_EXCD | Ingress NP Punt or Egress NP Punt of CFM other packets (link trace or perf. mon.). Ingress punts can occur on a Layer2 or Layer3 interface Egress punts occur on a Layer2 interface only. |
| CFM_CC CFM_CC_EXCD | Ingress NP Punt or Egress NP Punt of CFM CC packets (continuity check). Ingress punts can occur on a Layer2 or Layer3 interface Egress punts occur on a Layer2 interface only. |
| DHCP_SNOOP_REQ DHCP_SNOOP_REQ_EXCD | Ingress Punt of DHCP snoop request frames – layer2 interface only and DHCP snooping enabled. |
| DHCP_SNOOP_REPLY DHCP_SNOOP_REPLY_EXCD | Ingress Punt of DHCP snoop reply frames – layer2 interface only and DHCP snooping enabled. |
| MSTP MSTP_EXCD | Ingress NP Punt or Egress NP Punt of MSTP frames. For Layer2 VPLS or Layer3, punt is on ingress frames only. For Layer3 VPWS, punt is on egress frames only. |
| MSTP_PB MSTP_PB_EXCD | Ingress NP Punt or Egress NP Punt of MSTP Provider Bridge frames. For Layer2 VPLS or Layer3, punt is on ingress frames only. For Layer3 VPWS, punt is on egress frames only. |
| IGMP_SNOOP IGMP_SNOOP_EXCD | Ingress punt of snooped IGMP or PIM frames – layer2 interface only and IGMP snooping enabled. |
| EFM EFM_EXCD | Ingress Punt of EFM Protocol frames – layer3 interface only. |
| IPv4_OPTIONS IPv4_OPTIONS_EXCD | Ingress Punt of IP frames with options – layer3 interface only – IPV4, IPV6. |
| IPV4_PLU_PUNT (IPV4_FIB_PUNT) IPV4_PLU_PUNT_EXCD | Ingress or Egress punt of IPV4 frames with punt flag set in Leaf results or RECURSIVE ADJACENCY results – layer3 interface only. |
| IPV4MC_DO_ALL IPV4MC_DO_ALL_EXCD | Ingress punt of IPV4 Mcast frames due to punt only set for route, OR Egress punt of IPV4 Mcast frames due to punt and forward bit set for mcast group member – layer3 interface only. IPV4 Mcast punts not support for egress route. |
| IPV4MC_DO_ALL_BUT_FWD IPV4MC_DO_ALL_BUT_FWD_EXCD | Ingress punt and forward of IPV4 Mcast frames due to punt only set for route, OR Egress punt and forward of IPV4 Mcast frames due to punt and forward bit set for mcast group member – layer3 interface only. IPV4 Mcast punts not support for egress route. This can also occur as a result of the RPF source interface check. |
| PUNT_NO_MATCH (PUNT_FOR_ICMP) PUNT_NO_MATCH_EXCD | An Ingress or Egress IPV4/IPV6 unicast frame punt due to ICMP Unreachable (i.e., next hop down). |
| IPV4_TTL_ERROR (TTL_EXCEEDED) IPV4_TTL_ERROR_EXCD | An Ingress IPV4 frame with a TTL of 1 is punted (TTL of 0 is dropped). |
| IPV4_DF_SET_FRAG_NEEDED_PUNT IPV4_DF_SET_FRAG_NEEDED_PUNT_EXCD | An egress IPV4 or MPLS frame with MTU exceeded is punted. |
| RP_PUNT RP_PUNT_EXCD | An ingress IPV4 or MPLS has the RP punt bit set in the NON-RECURSIVE ADJACENCY or RX adjacency. |
| PUNT_IFIB PUNT_IFIB_EXCD | An ingress IPV4 ucast or IPV6 frame has an IFIB lookup match resulting in an IFIB punt. |
| PUNT_ADJ PUNT_ADJ_EXCD | An ingress IPV4 ucast or MPLS frame has the adjacency punt bit set in the NON-RECURSIVE ADJACENCY or RX adjacency. An egress IPV4 ucast or MPLS frame has the adjacency punt bit set in the NON-RECURSIVE ADJACENCY or TX adjacency. |
| PUNT_UNKNOWN_IFIB PUNT_UNKNOWN_IFIB_EXCD | An ingress IPV4 ucast frame has the IFIB bit set in the LEAF or RECURSIVE ADJACENCY and the IFIB lookup does not get a match, OR an ingress MPLS frame has the IFIB bit set in the LEAF or RECURSIVE ADJACENCY. |
| PUNT_ACL_DENY PUNT_ACL_DENY_EXCD | Ingress or Egress frame has a deny action set in the ACL policy and ACL punt (instead of drop) is enabled. |
| PUNT_ACL_LOG PUNT_ACL_LOG_EXCD | Ingress or Egress frame has an ACL policy match and ACL logging is enabled. Layer3 frames only. |
| PUNT_ACL_LOG_L2 PUNT_ACL_LOG_L2_EXCD | Ingress or Egress frame has an ACL policy match and ACL logging is enabled. Layer2 frames only. |
| IPV6_LINK_LOCAL IPV6_LINK_LOCAL_EXCD | Ingress IPV6 frames received that are link local packets – these are punted – layer3 interface only. |
| IPV6_HOP_BY_HOP IPV6_HOP_BY_HOP_EXCD | Ingress IPV6 frames received that are hop by hop packets - these are punted – layer3 interface only. |
| IPV6_TTL_ERROR IPV6_TTL_ERROR_EXCD | Ingress IPV6 frames that have a TTL error – these are punted – layer3 interface only. |
| IPV6_PLU_PUNT IPV6_PLU_PUNT_EXCD | Ingress or Egress punt of IPV6 frames with punt flag set in Leaf results or RECURSIVE ADJACENCY results – layer3 interface only. |
| IPV6_PLU_RCV IPV6_PLU_RCV_EXCD | Not implemented by software. |
| IPV6_ROUT_HEAD IPV6_ROUT_HEAD_EXCD | Ingress IPV6 frames received that are router header packets – these are punted – layer3 interface only. |
| IPV6_TOO_BIG IPV6_TOO_BIG_EXCD | Egress IPV6 frames that are too bit – exceed MTU – these are punted – layer3 interface only. |
| IPV6_MISS_SRC IPV6_MISS_SRC_EXCD | Not implemented by software. |
| IPV6MC_DC_CHECK IPV6MC_DC_CHECK_EXCD | Not implemented by software. |
| IPV6MC_DO_ALL IPV6MC_DO_ALL_EXCD | Not implemented by software. |
| IPV6MC_DO_ALL_BUT_FWD IPV6MC_DO_ALL_BUT_FWD_EXCD | Not implemented by software. |
| MPLS_PLU_PUNT (MPLS_FIB_PUNT) MPLS_PLU_PUNT_EXCD | Ingress MPLS frame punted due to Punt set in the Leaf or RECURSIVE ADJACENCY, or an Ingress MPLS router alert frame – these are punted. |
| MPLS_FOR_US MPLS_FOR_US_EXCD | Ingress MPLS frame punted due to IFIB (for-us) set in the Leaf or RECURSIVE ADJACENCY. |
| PUNT_VCCV_PKT PUNT_VCCV_PKT_EXCD | Ingress MPLS frame that is a PW VCCV frame – must be a PWtoAC de-aggregation flow. |
| PUNT_STATISTICS PUNT_STATISTICS_EXCD | Statistics gathering frame punted to LC host – generated by statistics scanning machine. |
| NETIO_RP_TO_LC_CPU_PUNT NETIO_RP_TO_LC_CPU_PUNT_EXCD | Preroute egress inject frame received from the RP that is sent to the LC host. |
| MOFRR_PUNT MOFRR_PUNT_EXCD | IPV4 multicast over fast reroute punt frames. |
| VIDMON_PUNT VIDMON_PUNT_EXCD | IPV4 multicast video monitoring punt frames. |
| VIDMON_PUNT_FLOW_ADD VIDMON_PUNT_FLOW_ADD_EXCD | IPV4 multicast video monitoring new flow added punt frames. |
| PUNT_DBGTRACE | Debug Trace frames that are punted. |
| PUNT_SYNCE | Punt Ingress SYNCE protocol frames – layer3 interface only. |
Related Information
n/a
Xander Thuijs - CCIE #6775
Sr Tech Lead ASR9000
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
We introduced in IOS-XR 4.3.1 and 5.1.0 a command to get counters description via the CLI.
This enhancement is tracked by CSCue18665 - NP counter descriptions.
The counter description can be retrieved with the following command:
sh controllers np descriptions location 0/x/cpu0
For those who are running a version that doesn't include this feature, here is the list of counters currently present in IOS-XR 5.1.1:
Counter Drop Feature Description
-------------------------------------------------------------------------------
NULL_STAT_0 Infra Invalid counter was incremented due to inconsistent software state. This should not occur but may be harmless
NULL_STAT_1 Infra Invalid counter was incremented due to inconsistent software state. This should not occur but may be harmless
NULL_STAT_2 Infra Invalid counter was incremented due to inconsistent software state. This should not occur but may be harmless
NULL_STAT_3 Infra Invalid counter was incremented due to inconsistent software state. This should not occur but may be harmless
NULL_STAT_4 Infra Invalid counter was incremented due to inconsistent software state. This should not occur but may be harmless
NULL_STAT_5 Infra Invalid counter was incremented due to inconsistent software state. This should not occur but may be harmless
NULL_STAT_6 Infra Invalid counter was incremented due to inconsistent software state. This should not occur but may be harmless
NULL_STAT_7 Infra Invalid counter was incremented due to inconsistent software state. This should not occur but may be harmless
NULL_STAT_8 Infra Invalid counter was incremented due to inconsistent software state. This should not occur but may be harmless
NULL_STAT_9 Infra Invalid counter was incremented due to inconsistent software state. This should not occur but may be harmless
NULL_STAT_10 Infra Invalid counter was incremented due to inconsistent software state. This should not occur but may be harmless
NULL_STAT_11 Infra Invalid counter was incremented due to inconsistent software state. This should not occur but may be harmless
NULL_STAT_12 Infra Invalid counter was incremented due to inconsistent software state. This should not occur but may be harmless
NULL_STAT_13 Infra Invalid counter was incremented due to inconsistent software state. This should not occur but may be harmless
NULL_STAT_14 Infra Invalid counter was incremented due to inconsistent software state. This should not occur but may be harmless
NULL_STAT_15 Infra Invalid counter was incremented due to inconsistent software state. This should not occur but may be harmless
MDF_TX_LC_CPU Infra Frames sent (punted) to linecard CPU. Includes packets and some messages between NPs.
MDF_TX_WIRE Infra Frames transmitted from NP to the Ethernet port Traffic Manager. These frames are destined for egress output on the Ethernet wire(s) but may be dropped by the egress Traffic Manager due to egress port congestion or link down.
MDF_TX_WIRE 1 Infra See BASE counter - replicated for performance
MDF_TX_WIRE 2 Infra See BASE counter - replicated for performance
MDF_TX_WIRE 3 Infra See BASE counter - replicated for performance
MDF_TX_FABRIC Infra Frames sent into the system central switch fabric - ingress frames and frames sent into the switch fabric from the linecard CPU. These may go to other LCs or the RSP and includes some messages between NPs.
MDF_TX_FABRIC 1 Infra See BASE counter - replicated for performance
MDF_TX_FABRIC 2 Infra See BASE counter - replicated for performance
MDF_TX_FABRIC 3 Infra See BASE counter - replicated for performance
PARSE_ENET_SAT_RECEIVE_CNT Infra Frames received from Ethernet Satellite ports by this NP
PARSE_ENET_SAT_RECEIVE_1 Infra See BASE counter - replicated for performance
PARSE_ENET_SAT_RECEIVE_2 Infra See BASE counter - replicated for performance
PARSE_ENET_SAT_RECEIVE_3 Infra See BASE counter - replicated for performance
PARSE_INTER_NP_RECEIVE_CNT Infra Frames received on the special connection between paired NPs of a 100GE port.
PARSE_INTER_NP_RECEIVE_CNT_1 Infra See BASE counter - replicated for performance
PARSE_INTER_NP_RECEIVE_CNT_2 Infra See BASE counter - replicated for performance
PARSE_INTER_NP_RECEIVE_CNT_3 Infra See BASE counter - replicated for performance
PARSE_FAB_RECEIVE_CNT Infra Frames received from the system central switch fabric. These may go to ethernet or the linecard CPU and includes some messages between NPs.
PARSE_FAB_RECEIVE_1 Infra See BASE counter - replicated for performance
PARSE_FAB_RECEIVE_2 Infra See BASE counter - replicated for performance
PARSE_FAB_RECEIVE_3 Infra See BASE counter - replicated for performance
PARSE_INTR_RECEIVE_CNT Infra Interrupt frames received - internal NP messages
PARSE_INTR_RECEIVE_1 Infra See BASE counter - replicated for performance
PARSE_INTR_RECEIVE_2 Infra See BASE counter - replicated for performance
PARSE_INTR_RECEIVE_3 Infra See BASE counter - replicated for performance
PARSE_INJ_RECEIVE_CNT Infra Frames from the LC CPU. May go to Ethernet link or system fabric
PARSE_INJ_RECEIVE_1 Infra See BASE counter - replicated for performance
PARSE_INJ_RECEIVE_2 Infra See BASE counter - replicated for performance
PARSE_INJ_RECEIVE_3 Infra See BASE counter - replicated for performance
PARSE_ENET_RECEIVE_CNT Infra Frames received from Ethernet ports by this NP
PARSE_ENET_RECEIVE_1 Infra See BASE counter - replicated for performance
PARSE_ENET_RECEIVE_2 Infra See BASE counter - replicated for performance
PARSE_ENET_RECEIVE_3 Infra See BASE counter - replicated for performance
PARSE_TM_LOOP_RECEIVE_CNT Infra Internal NP Loopback frames received from Traffic Manager - generally used for egress multicast replication
PARSE_TM_LOOP_RECEIVE_1 Infra See BASE counter - replicated for performance
PARSE_TM_LOOP_RECEIVE_2 Infra See BASE counter - replicated for performance
PARSE_TM_LOOP_RECEIVE_3 Infra See BASE counter - replicated for performance
PARSE_TOP_LOOP_RECEIVE_CNT Infra Internal NP Loopback frames received from Pipeline - generally used for packets requiring complex multi-pass processing in the NP
PARSE_TOP_LOOP_RECEIVE_1 Infra See BASE counter - replicated for performance
PARSE_TOP_LOOP_RECEIVE_2 Infra See BASE counter - replicated for performance
PARSE_TOP_LOOP_RECEIVE_3 Infra See BASE counter - replicated for performance
PARSE_UNKNOWN_DIR_DROP Drop Infra Frames dropped due to input source unknown - should not occur. Software error.
PARSE_UNKNOWN_DIR_1 Drop Infra See BASE counter - replicated for performance
PARSE_UNKNOWN_DIR_2 Drop Infra See BASE counter - replicated for performance
PARSE_UNKNOWN_DIR_3 Drop Infra See BASE counter - replicated for performance
PRS_ING_LINK_PROTOCOL_DISABLED Drop Infra Ingress NP discards Slow protocol packets on L2 VPLS when the protocol is not configured.
PARSE_ING_DISCARD Drop Infra Ingress frames discarded by NP (during Parse phase). Each discard should also be included in a more specific discard reason count.
PARSE_EGR_DISCARD Drop Infra Egress frames discarded by NP (during Parse phase). Each discard should also be included in a more specific discard reason count.
PARSE_FRM_ERR_CNT Drop Infra Sum of all DROP_FRM_* counters above.
PRS_CTX_WAIT_TIMEOUT Drop Infra Frames dropped due to Software error
RSV_CTX_WAIT_TIMEOUT Drop Infra Frames dropped due to Software error
MDF_CTX_WAIT_TIMEOUT Drop Infra Frames dropped due to Software error
PRS_HEALTH_MON Infra Periodic internal heartbeat packet used to monitor NP health
PRS_HEALTH_MON_DISCARD Drop Infra Health monitoring packets that were discarded due to CRC errors. Should never occur. Indicates NP buffer corruption
INTR_FRAME_TYPE_0 Infra Interrupt frames - internal NP messaging
INTR_FRAME_TYPE_1 Infra Interrupt frames - internal NP messaging
INTR_FRAME_TYPE_2 Infra Interrupt frames - internal NP messaging
INTR_FRAME_TYPE_3 Infra Interrupt frames - internal NP messaging
INTR_FRAME_TYPE_4 Infra Interrupt frames - internal NP messaging
INTR_FRAME_TYPE_5 Infra Interrupt frames - internal NP messaging
INTR_FRAME_TYPE_6 Infra Interrupt frames - internal NP messaging
INTR_FRAME_TYPE_7 Infra Interrupt frames - internal NP messaging
INTR_FRAME_TYPE_8 Infra Interrupt frames - internal NP messaging
INTR_FRAME_TYPE_9 Infra Interrupt frames - internal NP messaging
INTR_FRAME_TYPE_10 Infra Interrupt frames - internal NP messaging
INTR_FRAME_TYPE_11 Infra Interrupt frames - internal NP messaging
INTR_FRAME_TYPE_12 Infra Interrupt frames - internal NP messaging
INTR_FRAME_TYPE_13 Infra Interrupt frames - internal NP messaging
INTR_FRAME_TYPE_14 Infra Interrupt frames - internal NP messaging
INTR_FRAME_TYPE_15 Infra Interrupt frames - internal NP messaging
DBG_PRS_EP_L_PRS_PL_PW_DISPOSE L2 Ingress packets entering loopback for PW disposition
DBG_PRS_EP_L_PRS_VPLS_PW_IMPOSE L2 Ingress packets entering loopback for VPLS PW imposition
DBG_PRS_EP_L_PRS_VPLS_DOT1AH_LP L2 Ingress packets entering loopback for VPLS DOT1AH
DBG_PRS_EP_L_PRS_PL_ABF L3 Ingress packets entering loopback for ABF processing
DBG_PRS_EP_L_PRS_PL_L2TP_DECAP_PASS2 L2TP Ingress packets entering loopback L2TP decapsulation 2nd pass
DBG_PRS_EP_L_PRS_EGR_L2TP L2TP Egress packets entering L2TP processing
DBG_PRS_EP_L_PRS_PL_L2TP_ING L2TP Ingress packets entering LAC imposition pipeline loopback
DBG_PRS_NO_RFD_FOR_PREFETCH Infra Attempts by the NP to allocate a new NP buffer for some form of internal frames replication and no buffers were available. Should only occur rarely under very heavy NP load.
PARSE_ING_INTER_NP_THRU_TRAFFIC Infra Frames passed between a pair of NPs that service a 100GE interface
PARSE_ING_INTER_NP_IPC Infra Messages passed between a pair of NPs that service a 100GE interface
PARSE_L2_EGR_INJECT Infra L2 egress frames injected by RSP or LC CPU
PARSE_ING_8023 L2 Ingress 802.3 frames received
PARSE_ING_8023_JUMBO L2 Ingress 802.3 frames received with payload greater than 1500 bytes
PARSE_ING_L3_CFM EOAM Ingress L3 CFM frames
PARSE_ING_L2_CFM EOAM Ingress L2 CFM frames
PARSE_ING_SLOW_PROTO EOAM Ingress IEEE slow protocol frames (LACP / SYNCE / EFM)
PARSE_ING_IPV6_LINK_LOCAL L3 Ingress ipv6 Link Local frames
PARSE_RSP_INJ_L2_PREROUTE Infra Injected L2 pre-routed frames received by egress NP
PARSE_RSP_INJ_L2_INWARD Infra Injected L2 frames from RSP received by egress NP
PARSE_RSP_INJ_L2_EGRESS Infra Injected L2 frames received by egress NP
PARSE_RSP_INJ_FAB_CNT Infra Injected frames received by egress NP from fabric
PARSE_RSP_INJ_PORT_CNT Infra Injected frames received by egress NP from inject port
PARSE_RSP_INJ_DIAGS_CNT Infra Internal diagnostics frames received by NP from RSP
PARSE_EGR_INJ_PKT_TYP_UNKNOWN Infra Frames received from RSP of unknown type (internal error)
PARSE_EGR_INJ_PKT_TYP_IPV4 Infra IPv4 packets received from RSP or LC CPU
PARSE_EGR_INJ_PKT_TYP_IPV6 Infra IPv6 packets received from RSP or LC CPU
PARSE_EGR_INJ_PKT_TYP_MPLS Infra MPLS frames received from RSP or LC CPU
PARSE_EGR_INJ_PKT_TYP_CLNS Infra OSI CLNS packets received from RSP or LC CPU
PARSE_EGR_INJ_PKT_TYP_IPV4_PREROUTE Infra Pre-routed IPv4 packets received from RSP or LC CPU
PARSE_EGR_INJ_PKT_TYP_IPV6_PREROUTE Infra Pre-routed IPv6 packets received from RSP or LC CPU
PARSE_EGR_INJ_PKT_TYP_IPV6_LINK_LOCAL L3 IPv6 Link Local frames injected from control plane to network
PARSE_LC_INJ_L2_PREROUTE Infra Pre-routed L2 frames received from LC CPU
PARSE_LC_INJ_L2_INWARD Infra Injected L2 frames received from LC CPU
PARSE_LC_INJ_L2_EGRESS Infra Injected L2 frames received from LC CPU by egress NP
PARSE_LC_INJ_FAB_CNT Infra Frames received from LC CPU and passed to fabric
PARSE_LC_INJ_PORT_CNT Infra Frames received from LC CPU
PARSE_LC_INJ_DIAGS_CNT Infra Internal diagnostic frames received from LC CPU
PARSE_DROP_FAB_UNKNOWN_INJ Drop Infra Frames received from RSP of unknown type (internal error)
PARSE_DROP_UNKNOWN_TIMER_FEAT Drop Infra Frames received from TM Loopback has unknown feature mask
PARSE_HOST_INJ_BFD_IPV4_L3_INWARD BFD Transmitted BFD Multihop packet counters that are injected into the NP from host on which the bfd_session is hosted.
PARSE_HOST_INJ_BFD_IPV6_L3_INWARD L3 IPv6 BFD frames from control plane
PARSE_HOST_INJ_BFD_MPLS_L3_INWARD L3 BFD MPLS frames from control plane
PARSE_ING_L3_CFM_DROP Drop EOAM L3 CFM frames dropped by ingress NP
PARSE_ING_ISIS L3 IS-IS protocol packets received from Ethernet
PARSE_ING_PIM_IFIB MCAST PIM protocol packets detected and punted via LPTS
PARSE_EGRESS_BFD_PUNT_CNT BFD BFD packets that have reached the egress LC (on which the bfd session is hosted) and which have been remote punted from a ingress LC
PARSE_DROP_IN_EFM_BLOCK Drop EOAM Ingress EFM frames discarded due to ingress EFM block configured at ingress port
PARSE_DROP_IN_EFM_LOOPBACK_DATA EOAM Ingress EFM frames looped back in ingress NP
PARSE_DROP_IN_UIDB_TCAM_MISS Drop Infra Ingress frames dropped because they did not match to a configured interface encap (etype/vlan)
PARSE_DROP_IN_UIDB_NO_ENTRY Drop Infra Frames dropped due to inconsistent software state which may occur during reprogramming
PARSE_DROP_IN_ENET_UNKNOWN Drop Infra Frames dropped due to unknown ethertype at ingress NP
PARSE_DROP_IN_UIDB_DOWN Drop Infra Frames dropped due to interface/subinterface in shutdown state
PARSE_DROP_INJ_IN_UIDB_NO_MATCH Drop Infra Frames dropped due to inconsistent software state which may occur during reprogramming
PARSE_DROP_IPV4_DISABLED Drop L3 IPv4 packets dropped on receipt from Ethernet due to IPv4 not enabled on interface/subinterface
PARSE_DROP_IPV4_MCAST_NOT_ENABLED Drop MCAST IPv4 multicast packets dropped on receipt from Ethernet due to IPv4 multicast not enabled on interface/subinterface
PARSE_DROP_IPV4_CHECKSUM_ERROR Drop L3 IPv4 packets dropped on receipt from Ethernet due to IP header checksum error
PARSE_IPV4_SANITY_ADDR_CHK_FAILURES Drop L3 IPv4 packets dropped on receipt from Ethernet due to illegal IP addresses
PARSE_DROP_IPV4_LENGTH_ERROR Drop L3 IPv4 packets dropped on receipt from Ethernet due to IP packet length field inconsistent with L2 frame length
PARSE_DROP_MPLS_DISABLED Drop L3 MPLS frames dropped on receipt from Ethernet due to MPLS not enabled on interface/subinterface
PARSE_DROP_ING_MPLS_LABEL_INVALID Drop L3 MPLS frames dropped on receipt from Ethernet due to invalid MPLS labelingsuch as reserved MPLS label; too many explicit NULL labels; or EOS not set on last label
PARSE_DROP_ING_MPLS_TTL_ERROR Drop L3 MPLS frames dropped on receipt from Ethernet due to MPLS time-to-live expiry
PARSE_DROP_EGR_MPLS_LABEL_INVALID Drop L3 Egress MPLS frames dropped due to invalid MPLS label (tag value less than 15)
PARSE_L2MC_DROP_ROUTER_GUARD Drop L2 Ingress IGMP frames dropped due to router guard
PARSE_ING_DROP_DHCP_UNTRUSTED Drop L2 Ingress DHCP frames dropped on untrusted interface
PARSE_EGR_DROP_DHCP_UNTRUSTED Drop L2 Egress DHCP frames dropped on untrusted interface
PARSE_ING_L2_MSTP_DROP Drop L2 Ingress MSTP frames dropped on blocked ingress bridge port
PARSE_UNKNOWN_LC_CPU_INJ_DROP Drop Infra Unknown frames received from LC CPU dropped
PARSE_INJECT_NATIVE Infra Native injected frames received from LC CPU
PARSE_L2_DOT1Q_DROP Drop L2 Ingress L2 frames dropped due to DOT1Q protocol filtering
PARSE_L2_DOT1AD_DROP Drop L2 Ingress L2 frames dropped due to DOT1AD protocol filtering
PARSE_L2_DOT1Q_VTP_DROP Drop L2 Ingress L2 frames dropped due to DOT1Q VTP protocol filtering
PARSE_L2_DOT1AH_ISID_DROP Drop L2 Ingress L2 frames dropped due to DOT1AH invalid ISID
PARSE_DROP_IPV6_DISABLED Drop L3 IPv6 packets dropped on receipt from Ethernet due to IPv6 not enabled on interface/subinterface
PARSE_DROP_IPV6_LENGTH Drop L3 Ingress or egress frames with invalid IPv6 header length field (conflicts with L2 length)
PARSE_IPV6_SANITY_ADDR_CHK_FAILURES Drop L3 IPv6 packet dropped on receipt from Ethernet due to invalid IPv6 SA
PARSE_DROP_IPV6_MCAST_NOT_ENABLED Drop MCAST IPv6 multicast packets dropped on receipt from Ethernet due to IPv6 multicast not enabled on interface/subinterface
PARSE_DROP_IPV6_MCAST_NODE_LOCAL Drop MCAST IPv6 multicast packets dropped on receipt from Ethernet due to invalid destination address scope
PARSE_EGR_L2_CFM EOAM CFM frames received by egress NP
PARSE_L3_TAGGED_PUNT_DROP Drop L3 Dropped L2 link level protocol received at L3 interface with vlan tag (LLDP, MSTP, UDLD, CDP)
PARSE_MSTP_DOT1D L2 MSTP DOT1D frames received by ingress NP
PARSE_MSTP_DOT1AD L2 MSTP DOT1AD frames received by ingress NP
PARSE_MVRP_DOT1D L2 MVRP DOT1D frames received by ingress NP
PARSE_MVRP_DOT1AD L2 MVRP DOT1AD frames received by ingress NP
PARSE_UNKNOWN_NPH_TYPE_DROP Drop Infra Egress frames dropped due to unknown internal header type (internal error)
PARSE_OPEN_NETWORK_SERVICE_WRONG_INSTRUCTION Drop Service frames dropped due to Inline Service Internal error
PARSE_OPEN_NETWORK_SERVICE_MESSAGE_SANITY_FAIL Drop Service frames dropped due to Inline Service Internal error
PARSE_OPEN_NETWORK_SERVICE_KEY_ACTION_UNKNOWN Drop Service frames dropped due to Inline Service Internal error
PARSE_OPEN_NETWORK_SERVICE_SVC_LKUP Service Inline Service event
PARSE_OPEN_NETWORK_SERVICE_FWD_V4_LKUP Service Inline Service event
PARSE_OPEN_NETWORK_SERVICE_FWD_V6_LKUP Service Inline Service event
GRE_ING_ENCAP_P2_PRS GRE Frames entering GRE encapsulation 2nd pass processing on ingress NP
GRE_EGR_ENCAP_P2_PRS GRE Frames entering GRE encapsulation 2nd pass processing on egress NP
GRE_ING_DECAP_P1_QUAL_NO_MATCH GRE Frames entering GRE decapsulation processing but dropped because it did not match any configured GRE tunnel
GRE_ING_DECAP_P2_PRS GRE Frames entering GRE decapsulation 2nd pass processing on ingress NP
GRE_ING_DECAP_P2_CHKSUM_RSV1_NONZERO Drop GRE GRE decapsulation frames which has GRE header with checksum field but the 2 bytes after that was non-zero. This is not supported and the frame is dropped
GRE_ING_DECAP_P2_DECAP_P2_GRE_INVALID_KEY Drop GRE GRE decapsulation frames which has GRE header with 1:1 key did not match or is not present. Hence the frame is dropped
GRE_ING_DECAP_P2_GRE_KEY_PRESENT_DROP Drop GRE GRE decapsulation frames which has GRE header with key field present. This is not supported and the frame is dropped
GRE_ING_DECAP_P2_GRE_SEQ_PRESENT_DROP Drop GRE GRE decapsulation frames which has GRE header with sequence number field present. This is not supported and the frame is dropped.
GRE_ING_DECAP_P2_GRE_NONZERO_VER_DROP Drop GRE GRE decapsulation frames which has GRE header with non-zero value in version field. This is not supported and the frame is dropped.
GRE_ING_DECAP_P2_GRE_NONZERO_RSVD0_DROP Drop GRE GRE decapsulation frames which has GRE header with any of bits 1 or 4-12 set. This is not supported and the frame is dropped.
GRE_ING_DECAP_P2_PROT_UNSUPPORTED Drop GRE GRE decapsulation frame which has GRE header with protocol value which is not supported. The frame is dropped.
GRE_ING_DECAP_P2_NESTED_GRE_DROP Drop GRE GRE decapsulation frame which has another GRE encapsulated frames after decapsulation of the outer IP and GRE header. This is not supported and the frame is dropped.
GRE_ING_DECAP_P2_CLNS_NO_ISIS_DROP Drop GRE GRE decapsulation frame which has GRE header with protocol field value for CLNS but there is no ISIS frame following the header. This is error condition and the frame is dropped.
GRE_ING_DECAP_P2_NO_UIDB_DROP Drop GRE GRE decapsulation frame for which the tunnel UIDB was not found. This is an internal error and the frame is dropped.
GRE_ING_DECAP_P2_UIDB_DOWN Drop GRE GRE decapsulation frame received on a tunnel interface which is protocol down. The frame is dropped
GRE_ING_DECAP_P2_KA_PROTO_DOWN Drop GRE GRE keepalive frames received on a tunnel interface which is protocol down. The frame is processed even though the interface is down.
LISP_ING_DECAP_P2_PRS LISP LISP Decap event
LISP_ING_DECAP_P2_UNSUPPORTED
LISP_ING_DECAP_P2_NO_UIDB_DROP
CAP_IPV4_PRS_P1 LI IPv4 Frames being matchedfor Lawful Intercept processing.
CAP_IPV6_PRS_P1 LI IPv6 Frames being matched for Lawful Intercept processing.
CAP_PRS_P2 LI IP frames entering Lawful Intercept 2nd pass processing after replication.
PARSE_VIDMON_PKT_CNT Vidmon Packets processed for Video monitoring
VIDMON_SEM_RETRY_TIMEOUT Vidmon Packets for which Vidmon failed to acquire a semaphore
VIDMON_FLOW_UPDATE_CNT Vidmon Vidmon flows updated
PARSE_MOFRR_INTERRUPT MCAST Interrupt frames received due to mcast-only FRR activity or loss monitoring
PARSE_MOFRR_FRR_MSG_RECV MCAST Inter-NP MoFRR switchover notifications received
PARSE_IPIW_NON_IP_DROP Drop IPIW L2 frames dropped due to non-IP pacekt received on ipiw interface
PARSE_ELMI L2 ELMI frames received and punted by ingress NP
PARSE_PVST L2 PVST frames received by ingress NP
PARSE_LLDP L2 LLDP frames received by ingress NP
ELMI_ADDR_TYPE_ERROR Drop L2 ELMI frames dropped due to address type error
UNKNOWN_L2_ON_L3_DISCARD Drop L2 L2 frames with unknown ether-type received on L3 interface dropped
PARSE_EGRESS_PTP_CNT IEEE1588 Injected IPv4 PTP packets processed by egress NP
PARSE_BFD_NOT_MY_MAC Drop BFD BFD packets received but not to my mac by ingress NP
PARSE_BFD_IPv4_DISABLED Drop BFD Received BFD packet and IPV4 not enabled in L3 ingress ingress interface
PARSE_PPP_KEEPALIVE_HW_REPLY PPPoE PPPoE+PPP echo request (keepalive) packets that arrived on a PTA subscriber interface. The NP generated the reply instead of punting the packet.
INGRESS_L2TP_LOOKUP_MISS Drop L2TP Packets for which the ingress core-facing linecard has no entry in the L2TP session table that matches the packets tunnel id and session id. These packet are dropped.
PARSE_INGRESS_L2TP_VRF_NOMATCH Drop L2TP [not used]
PARSE_INGRESS_L2TP_IP_NOMATCH Drop L2TP [not used]
L2TP_ING_DECAP_SIP_DROP Drop L2TP Packets whose source IP address does not match the entry in the L2TP session table. These packets are dropped.
L2TP_ING_DECAP_TID_DROP Drop L2TP Frames dropped due to L2TP tunnel ID miss
L2TP_ING_DECAP_VER_DROP Drop L2TP L2TP frames dropped due to invalid version
PARSE_BFD_UIDB_DOWN Drop BFD Received BFD packet for which the ingress interface is down
PARSE_BVI_L3_ING L3 Frames received on BVI L3 interface by ingress NP
PARSE_BVI_L3_EGR L3 Frames to BVI L3 interface by egress NP
PARSE_BVI_L2_ING L3 Frames received on BVI L2 interface by ingress NP
PARSE_L3_SNF_SETUP Netflow Internal debug count
PARSE_ING_MVPN_PIM_ALL_RTRS MCAST Ingress GRE-encapped MVPN core packets recognized as PIM packets destined to all routers. These are punted.
PARSE_UDLD EOAM UDLD frames received by ingress NP
PARSE_SPAN_LPBK SPAN Span frames received after loopback (2nd pass) by ingress NP
PARSE_P2MP_MPLS_LPBK P2MP Egress P2MP/MLDP packets looped back after replication for MPLS interfaces
PARSE_P2MP_IP_LPBK P2MP Egress P2MP/MLDP packets looped back for IP decap processing
PARSE_P2MP_BUD_NOT_OAM Drop P2MP Ingress P2MP/MPLS packets replicated and looped back to check for OAM/PIM packet type. If packet are not OAM/PIM we drop these replicated copies; otherwise we process them as needed for OAM/PIM frames.
PARSE_IPMC_GENERIC_ENCAP_FIRST_PASS MCAST Internal debug event
PARSE_IPMC_GENERIC_ENCAP_SECOND_PASS_VRF MCAST Internal debug event
PARSE_IPMC_GENERIC_ENCAP_SECOND_PASS_CORE MCAST Internal debug event
PARSE_MVPN_ENCAP_THIRD_PASS MCAST Egress MVPN/GRE head node packets after encapsulation and before replication for a given GRE tunnel
PARSE_BGP_PA_LPBK BGPPA FYI. Internal debug. BGP-Policy Accounting loopbacks
IN_SATELLITE_DISCOVERY_DISCARD
EGR_SATELLITE_NOT_LOCAL_DROP
EGR_SATELLITE_PORT_DISABLE_DROP
PARSE_EGR_REMOTE_RACK_ENCAP_CNT Infra Internal debug event
PARSE_ING_FABRIC_INTERNAL_CNT Infra Internal debug event
PARSE_MAC_NOTIFY_RCVD L2 Internal event. Message received from other NPs to learn MAC addresses on a bridge domain
PARSE_MAC_DELETE_RCVD L2 Internal event. Message received from other NPs to delete MAC addresses from a bridge domains MAC table
PARSE_REV_MAC_NOTIFY_RCVD L2 Internal event. Reverse MAC Notify message received
PARSE_ING_PL_MLDP_PEEK_CNT Infra Internal debug event
PARSE_ING_PIM_DROP_CNT
PARSE_UNKNOWN_INTERRUPT_RCVD Infra Internal event. Unknown NP interrupt message received
PARSE_DROP_PPPOE_NOT_ENABLED Drop PPPoE Ingress frames dropped on port with PPPoE not enabled
PARSE_DROP_PPPOE_DATA_PKT_ON_DOWN_UIDB Drop PPPoE Frame discards due to a PPPoE Data packet being received on a PPPoE enabled parent interface when the subscribers UIDB protocol status is down
PARSE_FAST_DISCARD_LOW_PRIORITY_DROP_0
PARSE_FAST_DISCARD_LOW_PRIORITY_DROP_1
PARSE_FAST_DISCARD_LOW_PRIORITY_DROP_2
PARSE_FAST_DISCARD_LOW_PRIORITY_DROP_3
VIDMON_RTP_FLOW_UPDATE_CNT Vidmon Internal debug event
VIDMON_RTP_RESYNC_CNT Vidmon Internal debug event
PARSE_VIDMON_RTP_INVALID_CNT
VIDMON_RTP_LEFT_PROBATION_CNT Vidmon Internal debug event
PARSE_PWHE_ING_UIDB_MISS_DROP
PARSE_PWHE_VPORT_MISS_DROP
PARSE_PWHE_ING_NUM_VLAN_MISMATCH_DROP
PARSE_PWHE_DECAP_ING_EP pwhe Internal debug event
PARSE_PWHE_ENCAP_EGR_EP pwhe Internal debug event
PARSE_MVPN_MLDP_TURNAROUND_RX MCAST Internal debug event
PARSE_VIDMON_INVALID_CNT
PARSE_EOS0_DROP
PARSE_BFD_HWOFF_PASS_2
PARSE_VPLS_LSM_PW_DSP_ING_CNT
PARSE_L2_VPLS_LSM_EGR_LPBK_CNT
PARSE_L2_VPLS_LSM_EGR_CNT
PARSE_L_PRS_EGR_CGN_SERVICE
PARSE_SAT_EXACT_DROP SAT Internal debug event
PARSE_SAT_PORT_DISABLE_DROP SAT Internal debug event
PARSE_L_PRS_ING_MiM_SAT_DATA
PARSE_L_PRS_ING_MiM_SAT_CTRL
DBG_PRS_EP_L_PRS_PL_FLOWQOS FLOWQOS Packets entering loopback for Flow QoS learning
PARSE_EGR_GRE_KEY_PROCESS BNG GRE egress encap with GRE KEY
PARSE_DROP_ROUTED_SUB_SECURITY_DROP Drop BNG Ingress frames inner VLAN doesnt match that in Session Table
PARSE_ROUTED_SUB_LOOKUP_MISS BNG Ingress frames src ip didnt match session table so forwarding on parent
PARSE_ROUTED_SUB_PARENT_UIDB_LOOKUP_DROP Drop BNG ip session table failure and parent uidb lookup miss
DBG_RSV_EP_L2_INGRESS_VPWS_PW_IMPOSE L2 Internal debug event
DBG_RSV_EP_L_RSV_ING_ISIS Punt FYI. Internal debug. Count of ingress ISIS frames
DBG_RSV_EP_L_RSV_ING_L3_IFIB Punt Ingress LPTS lookup attempts for L3 packets
DBG_RSV_EP_L_RSV_ING_L3_IFIB_MATCH Punt L3 packets flagged for punting due to ingress LPTS lookup match
DBG_RSV_EP_L_RSV_ING_L3_IFIB_PUNT_LOCAL Punt L3 packets flagged for punting to LC CPU
DBG_RSV_EP_L_RSV_ING_L3_IFIB_PUNT_LOCAL1 Punt L3 packets flagged for punting to LC CPU
DBG_RSV_EP_L_RSV_ING_L3_RSLTS_MATCH Punt FYI. Internal debug count
DBG_RSV_EP_L_RSV_ING_PUNT Punt Ingress packets punted
RSV_OPEN_NETWORK_SERVICE_TRIGGER_SVC Service Internal debug event
DBG_RSV_EP_L_RSV_ING_L2MC MCAST Ingress L2 multicast packets received from Ethernet
DBG_RSV_EP_L_RSV_ING_L2 L2 Ingress L2 packets received from Ethernet
DBG_RSV_EP_L_RSV_EGR_MCST MCAST Egress L3 Multicast packets received from fabric
DBG_RSV_EP_L_RSV_EGR_L2MC MCAST Egress L2 multicast packets received from fabric
DBG_RSV_EP_L_RSV_EGR_L2 L2 [not used]
DBG_RSV_EP_L_RSV_EGR_L2_FLD_LPBK L2 [not used]
DBG_RSV_EP_L_RSV_EGR_FLOOD L2 L2 frames received from fabric to be flooded to bridge domain
DBG_RSV_EP_L_RSV_EGR_MCST_LPBK MCAST Egress frames looped back after multicast replication
DBG_RSV_EP_L_RSV_EGR_IPMC_COPY MCAST Internal debug event
DBG_RSV_EP_L_RSV_EGR_L2MC_LPBK MCAST Egress L2 frames looped back after multicast replication (IGMP Snooping)
DBG_RSV_EP_L_RSV_PW_DISPOSE L2 Frames entering PW disposition
DBG_RSV_EP_L_RSV_VPLS_PW_IMPOSE L2 VPLS frames entering PW imposition
DBG_RSV_EP_L_RSV_DOT1AH_PASS2 L2 DOT1AH frames entering 2nd pass at ingress NP
DBG_RSV_EP_L_RSV_ABF_PASS1 L3 Ingress frames being sent to 2nd pass ABF - Acl Based Forwarding
DBG_RSV_EP_L_RSV_ABF_PASS2 L3 Ingress frames finishing up 2nd pass Acl Based Forward
DBG_RSV_EP_L_RSV_L2TP_CHECK L2TP Ingress IP-for-me packets checked for L2TP protocol
DBG_RSV_EP_L_RSV_L2TP_PASS2 L2TP Ingress decapsulations of an IP-for-me L2TP packet
DBG_RSV_EP_L_RSV_L2TP_ING_LAG L2TP Ingress decapsulations of an IP-for-me L2TP packet and is sending it to a bundle/LAG interface
DBG_RSV_EP_L_RSV_EGR_L2TP L2TP Decapsulations of L2TP packets on egress
DBG_RSV_EP_L_RSV_ING_MPLS_TP MPLS-TP Frames hitting ingress MPLS TP path
DBG_RSV_ING_LEARN_LOOP L2 MAC addresses learned in ingress direction
DBG_RSV_EGR_LEARN_LOOP L2 MAC addresses learned in egress direction
ING_RSV_PW_DHCP_UNTRUSTED_DROP Drop L2 Frames on PW dropped due to a DHCP untrusted host
RSV_ING_BFD BFD Ingress BFD frames (for this router)
RSV_OPEN_NETWORK_SERVICE_PHASE Service Internal debug event
RSV_DROP_ING_BFD Drop BFD BFD frames dropped because BFD is not enabled on the receiving interface
RSV_DROP_ING_IFIB_OPT
RSV_DROP_EGR_UIDB_NO_MATCH Drop Infra Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_EGR_UIDB_DOWN Drop Infra Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_EGR_HWOFF_NO_MATCH Drop Infra Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_EGR_HWOFF_UIDB_DOWN Drop Infra Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_IPV4_LEAF_NO_MATCH Drop L3 Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_IPV6_LEAF_NO_MATCH Drop L3 Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_IPV4_NRLDI_NO_MATCH Drop L3 Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_IPV6_NRLDI_NO_MATCH Drop L3 Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_MPLS_NRLDI_NO_MATCH Drop L3 Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_IPV4_RXADJ_NO_MATCH Drop L3 Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_IPV6_RXADJ_NO_MATCH Drop L3 Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_MPLS_RXADJ_NO_MATCH Drop L3 Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_IPV4_TXADJ_NO_MATCH Drop L3 Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_IPV6_TXADJ_NO_MATCH Drop L3 Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_MPLS_TXADJ_NO_MATCH Drop L3 Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_IPV4_DROP_NULL_RTE Drop L3 dropped due to Tx-Adjacency linked to a null route. (TBD: why would this happen?)
RSV_DROP_IPV6_DROP_NULL_RTE Drop L3 dropped due to Tx-Adjacency linked to a null route. (TBD: why would this happen?)
RSV_DROP_MPLS_DROP_NULL_RTE Drop L3 dropped due to Tx-Adjacency linked to a null route. (TBD: why would this happen?)
RSV_DROP_IPV4_DROP_RP_DEST Drop L3 dropped because packet at Linecard interface attempted to route to the RSP management interface
RSV_DROP_IPV6_DROP_RP_DEST Drop L3 dropped because packet at Linecard interface attempted to route to the RSP management interface
RSV_DROP_IPV4_RXADJ_DROP Drop L3 dropped due to Rx-Adjacency set to drop all packets for this route. (TBD: why would this happen?)
RSV_DROP_IPV6_RXADJ_DROP Drop L3 dropped due to Rx-Adjacency set to drop all packets for this route. (TBD: why would this happen?)
RSV_DROP_MPLS_RXADJ_DROP Drop L3 dropped due to Rx-Adjacency set to drop all packets for this route. (TBD: why would this happen?)
RSV_DROP_IPV4_NRLDI_NOT_LOCAL Drop L3 Frames dropped due to mismatch of Ingress linecard vs Egress linecase forwarding information base. Should be a very rare event during route updates only
RSV_DROP_IPV6_NRLDI_NOT_LOCAL Drop L3 Frames dropped due to mismatch of Ingress linecard vs Egress linecase forwarding information base. Should be a very rare event during route updates only
RSV_DROP_MPLS_NRLDI_NOT_LOCAL Drop L3 Frames dropped due to mismatch of Ingress linecard vs Egress linecase forwarding information base. Should be a very rare event during route updates only
RSV_DROP_TE_NH_INCOMPLETE Drop L3 dropped due to incomplete Adjacency of a TE-tunnel Nexthop (TBD: Could this be do to mis-config or network error? Or is this a software bug? Could it happen briefly during transitions?)
RSV_DROP_ING_LAG_NO_MATCH Drop LAG Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_EGR_LAG_NO_MATCH Drop LAG Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_UNSUPPORTED_TUNNEL Drop L3 Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_ACL_DENY Drop ACL Ingress or Egress frames dropped because of a deny action set in the access-list
RSV_DROP_QOS_DENY Drop ACL Ingress or Egress frames dropped because of a qos action set in the config
RSV_DROP_IPV4_TXADJ_DROP Drop L3 dropped due to Tx-Adjacency set to drop all packets for this route. (TBD: why would this happen?)
RSV_DROP_IPV6_TXADJ_DROP Drop L3 dropped due to Tx-Adjacency set to drop all packets for this route. (TBD: why would this happen?)
RSV_DROP_MPLS_TXADJ_DROP Drop L3 dropped due to Tx-Adjacency set to drop all packets for this route. (TBD: why would this happen?)
RSV_DROP_IPV4_URPF_CHK Drop L3 dropped due to Unicast RPF check. Also counted as a URPF protocol drop at the interface level
RSV_DROP_IPV6_URPF_CHK Drop L3 dropped due to Unicast RPF check. Also counted as a URPF protocol drop at the interface level
RSV_DROP_L2MC_ING_RTE_DROP Drop MCAST Ingress L2 multicast frames dropped due as there is no route match
RSV_DROP_L2MC_EGR_RTE_DROP Drop MCAST Egress L2 multicast frames dropped due as there is no route match
RSV_DROP_L2MC_NO_OLIST Drop MCAST Egress L2 multicast frames dropped due to having no output interfaces on this NP
RSV_DROP_IPM4_ING_RTE_DROP Drop MCAST Ingress IPv4 multicast packets dropped due to not matching any mroute
RSV_DROP_IPM4_ING_RTE_DFLAG_DROP Drop MCAST Ingress IPv4 multicast packets dropped due to D flag in mroute
RSV_DROP_IPM4_EGR_RTE_DROP Drop MCAST Egress IPv4 multicast packets dropped due to not matching any mroute
RSV_DROP_IPM4_EGR_TTL_DROP Drop MCAST Egress IPv4 multicast packets dropped due to IP header time-to-live expiry
RSV_DROP_IPM4_EGR_FILTER_DROP Drop MCAST Egress IPv4 multicast packets dropped rather than transmitting back on source port
RSV_DROP_IPM4_EGR_RPF_FAIL_DROP Drop MCAST Egress IPv4 multicast packets dropped due to Reverse Path Forwarding check failure
RSV_DROP_IPM4_NO_OLIST Drop MCAST Egress IPv4 multicast packets dropped due to not having any egress ports on this NP - should be a very rare event only during removal of the multicast group.
RSV_DROP_IPM4_NO_UIDB Drop MCAST Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_IPM4_MVPN_RTE_NOT_MASTER Drop MCAST Egress IPv4 multicast packets that would be punted for signalling but are dropped due to not being on the master LC/NP
RSV_DROP_IPM4_MVPN_RPF_NOT_MASTER Drop MCAST Egress IPv4 multicast packets that would be punted for Reverse Path Forwarding check failure but are dropped due to not being on the master LC/NP
RSV_DROP_IPM4_MVPN_DECAP_NO_MATCH Drop MCAST Egress MVPN packets to be decapsulated but dropped due to MVPN decap table lookup failure
RSV_DROP_IPM4_ING_ENCAP_INVALID Drop MCAST Ingress MVPN/P2MP/MLDP packets dropped due to invalid encap table entry
RSV_DROP_IPM4_EGR_ENCAP_NO_MATCH Drop MCAST Egress MVPN/P2MP/MLDP packets dropped due to encap entry lookup failure
RSV_DROP_IPM4_EGR_ENCAP_INVALID Drop MCAST Egress MVPN/P2MP/MLDP packets dropped due to invalid encap table entry
RSV_DROP_IPM4_ENCAP_LEAF_NO_MATCH Drop MCAST Egress MVPN Generic Encap 2nd pass packets dropped due to encap output list entry (tunnel entry) lookup failure
RSV_DROP_IPM4_ENCAP_LEAF_INVALID Drop MCAST Egress MVPN Generic Encap 2nd pass packets dropped due to invalid encap output list entry
RSV_DROP_IPM4_MVPN_MTU Drop MCAST Egress MVPN packets to be encapsulated but dropped due to exceeding tunnel MTU
RSV_DROP_IPM4_NO_ENCAP_OLIST Drop MCAST Egress MVPN encap packets with no encapsulation output list entries
RSV_DROP_IPM4_PIT_MISS
RSV_IPM4_GRE_OLE GRE Internal debug event
RSV_DROP_IPM6_ING_RTE_DROP Drop MCAST Ingress IPv6 multicast packets dropped due to not matching any mroute
RSV_DROP_IPM6_ING_RTE_DFLAG_DROP Drop MCAST Ingress IPv6 multicast packets dropped due to D flag in mroute
RSV_DROP_IPM6_EGR_RTE_DROP Drop MCAST Egress IPv6 multicast packets dropped due to not matching any mroute
RSV_DROP_IPM6_EGR_TTL_DROP Drop MCAST Egress IPv6 multicast packets dropped due to IP header time-to-live expiry
RSV_DROP_IPM6_EGR_FILTER_DROP Drop MCAST Egress IPv6 multicast packets dropped rather than transmitting back on source port
RSV_DROP_IPM6_EGR_RPF_FAIL_DROP Drop MCAST Egress IPv6 multicast packets dropped due to Reverse Path Forwarding check failure
RSV_DROP_IPM6_NO_OLIST Drop MCAST Egress IPv6 multicast packets dropped due to not having any egress ports on this NP
RSV_DROP_IPM6_NO_UIDB Drop MCAST Egress IPv6 multicast packets dropped due to egress interface lookup failure
RSV_DROP_IPM6_MVPN_MDT_MTU
RSV_DROP_IPM6_MVPN_RTE_NOT_MASTER
RSV_DROP_IPM6_MVPN_RPF_NOT_MASTER
RSV_DROP_MLDP_MDT_MTU
RSV_DROP_MLDP_ING_NRLDI_NO_MATCH
RSV_DROP_MLDP_ING_NRLDI_INVALID
RSV_DROP_MC_FLD_IGNORE_IRL MCAST Packet not forwarded on IRL to avoid traffic duplication
RSV_DROP_IPMC_PWHE_MTU_EXCEED
RSV_DROP_MPLS_LEAF_NO_MATCH Drop L3 Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_ING_MPLS_PLU Drop L3 generic MPLS drop count
RSV_DROP_EGR_MPLS_PLU Drop L3 generic MPLS drop count
RSV_DROP_XID_NO_MATCH Drop L2 Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_DXID_NO_MATCH_OR_UNBOUND Drop L2 Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_L2VPNLDI_NO_MATCH Drop L2 Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_MPLS_CSC_CHK_FAIL Drop L3 dropped due to MPLS Carrier-supporting-Carrier VPN security check. VPN of the allocated MPLS label did not match the VPN of the incoming interface.
RSV_DROP_NHINDEX Drop L3
RSV_DROP_BD_MEMBER_TYPE_NO_MATCH Drop L2 Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_BD_MEMBER_TYPE_NO_MEMBER Drop L2 Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_IFIB_TTL_CHECK Drop Punt Dropped due to control plane filtering. Packet TTL was less than the minimum TTL required by the control plane to punt this protocol for processing. (There are no protocol counts or captured information to know which protocol is being dropped).
RSV_DROP_IP_TOS_CHECK
RSV_DROP_MPLS_TTL_EXPIRED Drop L3 dropped due to MPLS TTL
RSV_DROP_MPLS_MTU_EXCEEDED Drop L3 dropped due to MPLS frame size - MTU exceeded
RSV_DROP_PRRT_UIDB_MISS Drop Punt Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_DROP_IN_L3_NOT_MYMAC Drop L3 Unicast frames dropped on layer3 ingress interface because they do not match the interface MAC address (packet not destined for this next-hop).
RSV_PUNT_PIT_MISS Drop Punt Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_PUNT_IP_MTU_EXCEEDED L3 Egress IP packets that exceed the interface MTU. IPv4 frames are punted to LC CPU to be fragmented. IPv6 frames are punted to LC CPU be dropped and generate ICMP response.Punt rate limit is very low to protect LC CPU
RSV_PUNT_8023_MTU_EXCEEDED L3 Frames punted due to MTU exceeded
RSV_ING_PUNT_AND_FWD Infra Summary count of Ingress frames that are both forwarded to fabric and punted
RSV_EGR_PUNT_AND_FWD Infra Summary count of Egress frames that are both forwarded to fabric and punted
RSV_ING_L2_SMAC_MISS L2 Frames received with a previously un-Learned source MAC
RSV_ING_L2_BD_FLUSH L2 FYI. MAC Entries deleted due to Bridge Domain flush
RSV_ING_L2_PORT_FLUSH L2 FYI. MAC Entries deleted due to port flush
RSV_ING_L2_LEARN L2 FYI. MAC Addresses learned on ingress
RSV_ING_L2_MOVE L2 L2 Mac learn - mac move detected
RSV_ING_L2_FLUSH L2 L2 Mac table flushed entry
RSV_ING_L2_NG_SKIP_LEARN L2 FYI. MAC Address egress learn attempts that have timed out
RSV_NO_RFD_DROP Drop Infra Frames dropped due to lack of Internal NP buffering resource
RSV_ING_L2_FLOOD_BLOCK Drop L2 Frames dropped due to floods being blocked on an interface
RSV_EGR_L2_DROP_FLOOD_NO_MEMBER Drop L2 dropped due to no bridge members on the NP. May occur in some cases where packet replication in the system fabric sends a copy of the traffic to an egress NP that does not need it.
RSV_EGR_L2_FLOOD_BD_MISS Drop L2 Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_ING_L2_VPLS_MAC_FILTER Drop L2 dropped due to MAC filtering
RSV_ING_L2_SRC_XID_MISS Drop L2 Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_ING_L2_DST_XID_MISS
RSV_ING_L2_SRC_XID_UNBOUND Drop L2 dropped due to L2 interface down
RSV_EGR_L2_DEST_XID_UNBOUND Drop L2 dropped due to L2 interface down
RSV_ING_VPLS_ERR_DROP Drop L2 Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_ING_VPWS_ERR_DROP Drop L2 Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_ING_VPWS_INVALID_XID_DROP Drop L2 Frames dropped due to Ingress VPWS with undefined destination XID
RSV_ING_L2_BD_MISS Drop L2 Frames dropped due to inconsistent software state which may occur during reprogramming
RSV_ING_L2_REFLECT_FILTER Drop L2 Frames dropped to avoid forwarding a flood back out the source port on ingress
RSV_EGR_L2_REFLECT_FILTER Drop L2 Frames dropped to avoid forwarding a flood back out the source port on egress
RSV_EGR_L2_NOT_MEMBER Drop L2 Frames dropped due to bridge member not found for multicast
RSV_EGR_L2_INACTIVE_MEMBER Drop L2 Frames dropped due to bridge member inactive for multicast
RSV_EGR_L2_NG_SKIP_LEARN L2 FYI. MAC Address learning not done due to NP busy but will try again next time address seen
RSV_L2_ING_SHG_DROP Drop L2 Ingress Frames dropped due to split horizon
RSV_L2_EGR_SHG_DROP Drop L2 Egress Frames dropped due to split horizon
RSV_EGR_L2_MSTP_DROP Drop L2 Frames dropped due to MSTP blocking state
RSV_VPLS_LEARN_LIMIT_ACTION_DROP_CNT Drop L2 Frames dropped due to bridge learn limit
RSV_VPLS_MCAST_SRC_MAC_DROP_CNT Drop L2 Frames dropped due to multicast source MAC
RSV_VPLS_SECURE_MAC_DROP_CNT Drop L2 Frames dropped due to secure MAC
RSV_VPLS_SECURE_MAC_NOTIFY_CNT L2 Secure MAC notify events
RSV_VPLS_DAI_VIOLATION_DROP_CNT Drop L2 Frames dropped due to DAI violation
RSV_VPLS_DAI_NOTIFY_CNT Drop L2 DAI notify events
RSV_VPLS_IPSG_VIOLATION_DROP_CNT L2 Frames dropped due to IPSG violation
RSV_VPLS_IPSG_NOTIFY_CNT L2 IPSG notify events
RSV_VPLS_EGR_MAC_MOVE_DENIED_CNT Drop L2 Frames dropped due to egress MAC move denial
RSV_VPLS_MAC_MOVE_CNT L2 MAC moves
RSV_VPLS_STATIC_MAC_MOVE_DROP_CNT Drop L2 Frames dropped because static MACs cannot move
RSV_LEARN_FROM_NOTIFY_CNT L2 Count of mac learn notifications that result in newly learned macs.
RSV_VPLS_MAC_NOTIFY_LOCAL_DROP_CNT Drop L2 [not used]
RSV_VPLS_MAC_NOTIFY_ERR_DROP_CNT Drop L2 Count of mac learn notifications that cant be processed by the NP due to an error. Bridge domain lookup miss; mac entry is already there and static; or xid lookup miss and xid is global.
RSV_VPLS_MAC_DELETE_ERR_DROP_CNT Drop L2 Count of mac delete notifications that cant be process by the NP due to an error. See above.
RSV_VPLS_MAC_DELETE_SECURE_DROP_CNT Drop L2 Count of mac delete notifications that cant be processed by the NP due to the entry having mac secure settings.
RSV_FLUSH_FROM_NOTIFY_CNT L2 Mac table entry flushed
RSV_REFRESH_FROM_NOTIFY_CNT L2 Count of mac learn notifications that result in the mac entry being refreshed. This updates the timestamp so that entry wont be aged out. For mac addresses that are actively being forwarded.
RSV_MOVE_FROM_NOTIFY_CNT L2 Count of mac learn notifications that result in the mac entry being moved to a different interface (XID).
RSV_DELETE_FROM_NOTIFY_CNT L2 [not used]
RSV_DELETE_FROM_MSG_CNT L2 Count of mac delete notifications that result in the mac entry being deleted.
RSV_ING_LEARN_ONLY_DROP_CNT Drop L2 Count of vpls frames that are dropped due to the bridge being in learn only state. In this state source mac addresses are learned by not forwarded.
RSV_EGR_EFP_FILTER_TCAM_MISS_DROP_CNT Drop L2 Count of vpls frames that are dropped by EFP filtering due to the vlan encapsulation on the wire not matching any transmit interface. Can only increment if EFP filtering is enabled.
RSV_EGR_EFP_FILTER_MISS_DROP_CNT Drop L2 Count of vpls frames that are dropped by EFP filtering due to the vlan encapsulation on the wire not matching the interface that the frame is transmitted on. Can only increment if EFP filtering is enabled.
RSV_EGR_PREFILTER_VLAN_DROP_CNT Drop L2 Count of vpls frames that are dropped by EFP filtering due to the vlan encapsulation on the fabric not matching the interface that the frame is transmitted on. Can only increment if EFP filtering is enabled. Can only increment if EFP filtering is enabled.
RSV_EGR_VLAN_NUM_DROP_CNT Drop L2 Count of vpls frames that are dropped due to the vlan encapsulation on the fabric not having enough tags to support the egress vlan ops. This prevents the ucode from corrupting the frame if vlan tags are popped on egress.
RSV_ING_L2_VPLS_STORM_DROP_CNT Drop L2 Total number of flood frame drops due to vpls storm control. These are broadcast or multicast or unknown unicast. Only valid if vlps storm control is enabled.
RSV_ING_L2_DOT1AH_ISID_DROP_CNT Drop L2 Total dot1ah vpls frame drops due to dot1ah isid lookup miss when the provider destination mac that matches the my-backbone-mac of the box.
RSV_ING_L2_DOT1AH_CORE_LOOP_DROP_CNT Drop L2 Total dot1ah vpls frame drops due to a provider source mac that is already programmed as the my-backbone-mac of the box. Indicates a loop on the core side of the dot1ah connection.
VIDMON_TCAM_LKUP_MISS_CNT Vidmon Vidmon policy lookup was done and it was not successful
VIDMON_INTF_HASH_LKUP_MISS_CNT Vidmon Vidmon interface hash lookup was done and it was not successful
VIDMON_RSV_FLOW_ADD_CNT Vidmon Vidmon flows learned
VIDMON_RSV_MDI_FLOW_ADD_CNT Vidmon Vidmon flows learned
VIDMON_FLOW_DEL_ABORT_CNT
VIDMON_OD_SCAN_CNT Vidmon Vidmon scan event
VIDMON_PROBATION_DELETE_CNT
VIDMON_FLOW_LIMIT_EXCD_CNT Vidmon Vidmon flows attempted to be added but the NP is already at the limit
VIDMON_IDX_Q_EMPTY_CNT Vidmon Vidmon flows attempted to be added but the NP is already at the limit
VIDMON_MDI_IDX_Q_EMPTY_CNT
VIDMON_NG_LEARN_ABORT_CNT
VIDMON_AGE_DELETE_CNT
RSV_EGR_LAG_NOT_LOCAL_DROP_CNT Drop LAG Normal egress discard after multicast/broadcast packet replication to an NP that did not need a copy of the packet; or during transition of link-bundle output. This egress filtering ensures that flood/multicast packets go out only one bundle link
RSV_EGR_PW_DHCP_UNTRUSTED_DROP Drop L2 Frames on PW dropped due to a DHCP untrusted host
RSV_MOFRR_ING MCAST Ingress IPv4 packets received on MoFRR mroutes
RSV_MOFRR_WD_UPDATE MCAST Ingress IPv4 packets received on MoFRR mroute from interface for which traffic is being passed - incrementing watchdog
RSV_MOFRR_ACT_PUNT MCAST MoFRR activity watchdog interrupt notifications received - punted
RSV_MOFRR_LOSS_MSG
RSV_MOFRR_INTR_CNT MCAST MoFRR watchdog interrupt notifications received
RSV_MOFRR_HRT_LKUP_FAIL_DROP_CNT Drop MCAST MoFRR watchdog interrupt notifications ignored due to watchdog entry lookup failure
RSV_MOFRR_FWD_IRL MCAST MoFRR FRR notification forwarded on cluster IRL
RSV_MOFRR_WDT_INVALID_RES_DROP_CNT Drop MCAST MoFRR watchdog interrupt notifications ignored due to watchdog entry being in an invalid state (monitoring neither activity nor loss)
RSV_MOFRR_SKIP_LRN_CNT MCAST Failed attempts to record an MoFRR switchover due to learn timeout
RSV_MOFRR_HRT_UPDATE_CNT MCAST MoFRR switchovers recorded
RSV_MOFRR_SEQ_NUM_FAIL_DROP_CNT Drop MCAST MoFRR switchover notifications ignored due to sequence number mismatch
RSV_MOFRR_RPF_FAIL MCAST MoFRR switchover message heeded but not punted because of RPF mismatch
RSV_TIMOFRR_EGR_SRC_REPLACE
RSV_TIMOFRR_ING_STANDBY
RSV_ABF_NON_DEFAULT_RTE L3 Frames which matched ABF rule which had default-route check enabled but the frame had a non-default route. ABF is not applied to the frame.
RSV_L2TP_ING_STR_MISS_DROP_CNT Drop L2TP While processing a packet from a PPPoE LAC subscriber the ingress linecard unexpectedly did not find an entry in the L2TP session table
RSV_L2TP_BAD_TUNNEL_ROUTE_DROP_CNT Drop L2TP While processing a packet from a PPPoE LAC subscriber the ingress linecard unexpectedly could not route the encapsulated packet to the LNS. The packet was about to be punted or dropped or routed into a GRE tunnel.
RSV_L2BC_BVI L2 Count of flooded broadcast or multicast vpls frames that are sent to the BVI. Only increments if the BVI interface is part of the VPLS flood group.
RSV_L2MC_BVI MCAST Count of layer2 multicast routed frames that are sent to the BVI. Only increments if the BVI interface is part of the multicast group.
RSV_ING_SPAN SPAN [not used]
RSV_EGR_SPAN SPAN Count of egress span frames replciated by resolve.
ACL_CAPTURE_NO_SPAN SPAN Matched ACL capture entry but no span session configured
UTURNCHECK_FRR_DROP Drop L3 [not used]
ERP_ING_PUNT EOAM Ethernet Ring Protection Switching protocol (G.8032 ERPS). Generic path count. Should also be counted as PUNT_ERP_*
RSV_SNF_SAMPLE_PROCESS Netflow [not used]
RSV_SNF_SAMPLE_PKT Netflow Frames which are sampled by Netflow processing and punted to local LC CPU
RSV_SNF_IPV4 Netflow Frames which are sampled by Netflow processing and send to 2nd pass processing for Source IP lookup.
RSV_SNF_ING_PUNT Netflow Ingress frames which are sampled by Netflow processing
RSV_SNF_EGR_PUNT Netflow Egress frames which are sampled by Netflow processing
RSV_MVPN_ENCAP MCAST FYI. Debug. MVPN Encap operation
RSV_P2MP_EGR_SEND_IP_PL P2MP Egress P2MP/MLDP packets being replicated and prepped to loop back for IP decap processing
RSV_P2MP_EGR_SEND_TAIL_PL P2MP Ingress P2MP/MLDP packets being prepped to loop back for Tail IP decap processing
RSV_P2MP_EGR_SEND_BUD_PL P2MP Ingress P2MP/MLDP packets being replicated and prepped to loop back for other checks like OAM/PIM.
RSV_P2MP_NO_OLE Drop P2MP Egress P2MP packets being dropped as there are no interfaces on this NP for this tunnel or the IP Legs.
RSV_P2MP_IP_LOOKUP_FAIL Drop P2MP Egress P2MP/MLDP packets needing IP lookup, but the lookup failed.We continue to forward on MPLS tunnel.
RSV_P2MP_RPF_FAIL Drop P2MP Egress P2MP packets needing IP lookup, but the RPF check failed.We continue to forward on MPLS tunnel.
RSV_BGP_PA_EGR_DROP Drop L3 FYI. BGP-Policy Accounting failed for SA - packet NOT dropped
RESOLVE_INV_REMOTE_RACK_UIDB_DROP_CNT
RESOLVE_EGR_REMOTE_RACK_ENCAP_CNT Infra Internal debug event
RESOLVE_ING_REMOTE_RACK_DECAP_CNT Infra Internal debug event
RSV_SEND_MAC_NOTIFY_TO_IRL Infra Internal debug event
RSV_MAC_ACC_SA_MISS L2 Mac Accounting frame SMAC no match
RSV_MAC_ACC_DA_MISS L2 Mac Accounting frame DMAC no match
RSV_NO_REMOTE_RACK_PORTS
RSV_GET_CTX_TMOUT_EFP_FILTER Drop L2 Frames dropped due to Internal context timeout - software error
RSV_GET_CTX_TMOUT_IFIB_RSLTS Drop L3 Frames dropped due to Internal context timeout - software error
RSV_GET_CTX_TMOUT_IFIB_RSLTS_GRE Drop GRE Frames dropped due to Internal context timeout - software error
RSV_GET_CTX_TMOUT_IFIB_RSLTS_LISP Drop LISP Frames dropped due to Internal context timeout - software error
RSV_GET_CTX_TMOUT_ING_UIDB_EXT Drop Infra Frames dropped due to Internal context timeout - software error
RSV_GET_CTX_TMOUT_FLOWQOS_CTX Drop QOS CAC Redirect frames dropped - Internal context timeout - software error
RSV_GET_CTX_TMOUT_ACL_CTX Drop ACL Frames dropped due to Internal context timeout - software error
RSV_GET_CTX_TMOUT_PARENT_QOS_CTX Drop QOS Frames dropped due to Internal context timeout - software error
RSV_GET_CTX_TMOUT_PARENT_QOS_IF_CTX Drop QOS Frames dropped due to Internal context timeout - software error
RSV_GET_CTX_TMOUT_PARENT_QOS_LPBK_CTX Drop QOS Frames dropped due to Internal context timeout - software error
RSV_GET_CTX_TMOUT_TM_PART2_CTX Drop Infra Frames dropped due to Internal context timeout - software error
RSV_EGR_CLUSTER_SH_DROP_CNT
RSV_MLDP_ING_PEEK_PL Infra Internal debug event
RSV_DBA_FLOW_ADD DBA Internal debug event - Dest based accounting flow added
RSV_DBA_FLOW_DEL DBA Internal debug event - Dest based accounting flow removed
RSV_DBA_LEARN_LIMIT_REACHED DBA Destination based accounting - learn limit reached
DBA_LRN_SCAN_MSG_CNT DBA Destination based accounting - learn scan event
DBA_LRN_IDX_Q_EMPTY_CNT DBA Destination based accounting - not able to learn due to resource limits
DBA_LRN_ADD_ABORT_CNT DBA Destination based accounting - learn failed
DBA_LRN_ADD_FAIL_CNT DBA Destination based accounting - learn failed
DBA_LRN_FLOW_DEL_FAIL_CNT DBA Destination based accounting - learn failed
LRN_MSG_Q_FULL_CNT Infra Learn machine event - update failed due to np resource limits - will retry
RSV_MLDP_ING_DROP
RSV_MLDP_EGR_DROP
RSV_DBA_FLOW_DEL_drop DBA Destination based accounting - learn event
RSV_DBA_NG_LEARN_CNT DBA Destination based accounting - learn event
RSV_PWHE_DECAP_ING_CNT PWHE internal debug event
RSV_PWHE_ENCAP_ING_UNSUPP
RSV_PWHE_ENCAP_ING_2ND_CNT PWHE internal debug event
VIDMON_RTP_PT_LKUP_MISS_CNT
RSV_TUNNEL_RPF_FAILED
RSV_EGR_BNG_V6_LINK_LOCAL BNG IPv6 Link local rx on BNG
RSV_EGR_IPV6_LINK_LOCAL L3 IPv6 Link local rx
VIDMON_RTP_INVALID_CNT Drop Vidmon
MPLS_RPF_DROP Drop L3
RSV_ING_L2_EVPN_DF_BLOCK Drop
RSV_EGR_L2_EVPN_DF_BLOCK Drop
RSV_EGR_L2_EVPN_ESI_DROP Drop
RSV_ING_L2_EVPN_NO_PROV_BD_DROP Drop
RSV_ING_L2_EVPN_NO_SMAC_DROP Drop
RSV_ING_L2_EVPN_NO_DMAC_DROP Drop
RSV_ING_L2_EVPN_SAME_ESI_DROP Drop
RSV_ING_L2_EVPN_REFLECT_FILTER Drop
RSV_L2TPV3OV6_ENCAP_LKP_FAIL Drop
RSV_L2TPV3OV6_DECAP_LKP_FAIL Drop
RSV_L2TPV3OV6_COOKIE_MISS Drop
RSV_Y1731_LMMR_DROP Drop
RSV_L2_VPLS_LSM_ING
RSV_L2_VPLS_LSM_EGR
RSV_L2MC_VPLS_LSM_HEAD_ING_CNT
RSV_L2MC_VPLS_LSM_BUD_ING_CNT
RSV_L2MC_VPLS_LSM_EGR_CNT
RSV_EGR_CGN_PROC_RTN
RSV_ING_ETHERNET_LOOPBACK EDPL Frames looped back by the Ethernet Dataplane Loopback feature
DBG_L_RSV_FLOWQOS_LRN_CNT FLOWQOS Count of frames identified as new flow and being considered for learning into the Flow QoS entry table per NP
RSV_FLOWQOS_FLOW_CNT_EXCEED FLOWQOS Flow QoS entry table per NP (UBRL) or per class (CAC) is fullNo more flow entries can be learnt until older entries age out / get deleted
DBG_L_RSV_FLOWQOS_PASS2_ADD_CNT FLOWQOS Replica frames finishing up 2nd pass Flow QoS learningThese are copies of original frames just for learn and discard
RSV_DROP_CAC_REJECT Drop FLOWQOS Ingress or Egress frames dropped because of per-class Flow aware CAC flow count exceed
LRN_FLOWQOS_CAC_CNT_EXCEED FLOWQOS Per class h/w entry table for Flow aware CAC is fullNo more flow entries can be learnt until older entries age out / get deleted
LRN_FLOWQOS_TBL_INDEXQ_EMPTY FLOWQOS H/w programming inconsistency - Per flow hardware resourcequeue is empty. No more flow entries can be learnt and allocatedper-flow resource until queue is replenished with flow age/delete
PUNT_INVALID Punt software error in punt path
PUNT_INVALID_DROP Punt software error in punt path
PUNT_ALL Punt software error in punt path
PUNT_ALL_EXCD Punt software error in punt path
CDP Punt Punt Ingress CDP protocol frames - layer3 interface only
CDP_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
ARP Punt Punt Ingress ARP protocol frames - layer3 interface only
ARP_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
RARP Punt Punt Ingress Reverse ARP protocol frames - layer3 interface only
RARP_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
CGMP Punt Punt Ingress CGMP protocol frames - layer3 interface only
CGMP_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
LOOP Punt Punt Ingress ELOOP protocol frames - layer3 interface only
LOOP_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
SAP_PUNT Punt unused
SAP_PUNT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
BUNDLE_PROTO_PUNT Punt LACP protocol - punted to CPU for processing
BUNDLE_PROTO_PUNT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
UNKNOWN_OSI Punt Unknown OSI frame - punted to CPU for processing
UNKNOWN_OSI_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
DIAGS Punt unused
DIAGS_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
SNIFF Punt unused
SNIFF_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_GLOBAL_IFHANDLE_TCAM_MISS Punt unused
PUNT_GLOBAL_IFHANDLE_TCAM_MISS_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
DROP_PACKET Punt unused
DROP_PACKET_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
CFM_OTHER Punt Ingress NP Punt or Egress NP Punt of CFM other packets (link trace or perf. mon.). Ingress punts can occur on a Layer2 or Layer3 interface Egress punts occur on a Layer2 interface only.
CFM_OTHER_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
CFM_OTHER_RSP_PUNT Punt Ingress NP Punt or Egress NP Punt of CFM other packets (link trace or perf. mon.). Ingress punts can occur on a Layer2 or Layer3 interface Egress punts occur on a Layer2 interface only. - Received on a virtual/bundle interface, so punting to RSP CPU for processing
CFM_OTHER_RSP_PUNT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
DHCP_SNOOP_REQ Punt Ingress Punt of DHCP snoop request frames - layer2 interface only and DHCP snooping enabled
DHCP_SNOOP_REQ_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
DHCP_SNOOP_REPLY Punt Ingress Punt of DHCP snoop reply frames - layer2 interface only and DHCP snooping enabled
DHCP_SNOOP_REPLY_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
MSTP Punt Ingress NP Punt or Egress NP Punt of MSTP frames. For Layer2 VPLS or Layer3, punt is on ingress frames only. For Layer3 VPWS, punt is on egress frames only.
MSTP_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
MSTP_PB Punt Ingress NP Punt or Egress NP Punt of MSTP Provider Bridge frames. For Layer2 VPLS or Layer3, punt is on ingress frames only. For Layer3 VPWS, punt is on egress frames only.
MSTP_PB_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
DAI Punt ARP packet punted from L2 interface for Dynamic Arp Inspection
DAI_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
IGMP_SNOOP Punt Ingress punt of snooped IGMP or PIM frames - layer2 interface only and IGMP snooping enabled
IGMP_SNOOP_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
IPSUB Punt Punted to CPU to establish IP-Subscriber session
IPSUB_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PPPOE Punt Punted to CPU to establish PPPoE session
PPPOE_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PPP Punt PPP Control frame - punted to CPU for processing
PPP_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
EFM Punt EFM (Ethernet First Mile) OAM Protocol frames - punted to CPU for processing
EFM_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
IPv4_OPTIONS Punt Ingress Punt of IP frames with options - layer3 interface only - IPV4, IPV6
IPv4_OPTIONS_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
IPV4_PLU_PUNT Punt Ingress or Egress punt of IPV4 frames to CPU for routes needing CPU processing
IPV4_PLU_PUNT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
IPV4MC_DO_ALL Punt IPV4 Mcast control frames punted to CPU (not forwarded by NP, may be forwarded by CPU)
IPV4MC_DO_ALL_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
IPV4MC_DO_ALL_BUT_FWD Punt IPV4 Mcast control frames punted to CPU and forwarded in the NP.
IPV4MC_DO_ALL_BUT_FWD_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
IPV4_DOUBLE_TUNNEL Punt Not implemented by ucode
IPV4_DOUBLE_TUNNEL_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_NO_MATCH Punt IP Unreachable - punted to CPU for ICMP Unreachable response
PUNT_NO_MATCH_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
IPV4_TUNNEL_FORUS Punt Not implemented by ucode
IPV4_TUNNEL_FORUS_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
IPV4_FRAG_TUNNEL Punt Not implemented by ucode
IPV4_FRAG_TUNNEL_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
IPV4_CANNOT_FRAG Punt Not implemented by ucode
IPV4_CANNOT_FRAG_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
IPV4_TTL_ERROR Punt Ingress IPV4 frames with TTL = 1, punted to CPU for ICMP response. (TTL of 0 is dropped in NP)
IPV4_TTL_ERROR_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
IPV4_FRAG_NEEDED_PUNT Punt IP MTU Exceeded. Punted to CPU for fragmentation
IPV4_FRAG_NEEDED_PUNT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
IPV4_BFD Punt BFD - punted to CPU for processing
IPV4_BFD_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
RP_PUNT Punt punted to RSP for additional processing of packets to a specific Adjacency
RP_PUNT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_IFIB Punt Generic count of IP packets punted to the layer3 control plane for processing after CoPP/IFIB filtering.
PUNT_IFIB_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_ADJ Punt Ingress IPV4 ucast or MPLS frames with the adjacency punt bit set in the NR-LDI or RX adjacency. Egress IPV4 ucast or MPLS frames with the adjacency punt bit set in the NR-LDI or TX adjacency.
PUNT_ADJ_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_UNKNOWN_IFIB Punt Ingress IPV4 ucast frames with the IFIB bit set in the LEAF or R-LDI and the IFIB lookup does not get a match, OR ingress MPLS frames with the IFIB bit set in the LEAF or R-LDI
PUNT_UNKNOWN_IFIB_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_ACL_DENY Punt Ingress or Egress frames with a deny action set in the ACL policy and ACL punt (instead of drop) is enabled
PUNT_ACL_DENY_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_ACL_LOG Punt Ingress or Egress frames with an ACL policy match and ACL logging is enabled. Layer3 frames only.
PUNT_ACL_LOG_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_ACL_LOG_L2 Punt Ingress or Egress frames with an ACL policy match and ACL logging is enabled. Layer2 frames only.
PUNT_ACL_LOG_L2_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
IPV6_LINK_LOCAL Punt Ingress IPV6 frames received that are link local packets - these are punted - layer3 interface only
IPV6_LINK_LOCAL_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
IPV6_HOP_BY_HOP Punt Ingress IPV6 frames received that are hop by hop packets - these are punted - layer3 interface only
IPV6_HOP_BY_HOP_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
IPV6_TTL_ERROR Punt Ingress IPV6 frames that have a TTL error - these are punted - layer3 interface only
IPV6_TTL_ERROR_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
IPV6_PLU_PUNT Punt Ingress or Egress punt of IPV6 frames with punt flag set in Leaf results or R-LDI results - layer3 interface only
IPV6_PLU_PUNT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
IPV6_PLU_RCV Punt Not implemented by ucode
IPV6_PLU_RCV_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
IPV6_ROUT_HEAD Punt Ingress IPV6 frames received that are router header packets - these are punted - layer3 interface only
IPV6_ROUT_HEAD_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
IPV6_TOO_BIG Punt Egress IPV6 frames that are too bit - exceed MTU - these are punted - layer3 interface only
IPV6_TOO_BIG_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
IPV6_MISS_SRC Punt Not implemented by ucode
IPV6_MISS_SRC_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
IPV6_SRC_LINK_LOCAL Punt IPv6 source address is link-local - punted to CPU for processing
IPV6_SRC_LINK_LOCAL_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
IPV6MC_DO_ALL Punt IPV6 Mcast control frames punted to CPU (not forwarded by NP, may be forwarded by CPU)
IPV6MC_DO_ALL_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
IPV6MC_DO_ALL_BUT_FWD Punt IPV6 Mcast control frames punted to CPU and forwarded by NP
IPV6MC_DO_ALL_BUT_FWD_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
MPLS_PLU_PUNT Punt Ingress MPLS frames punted due to Punt set in the Leaf or R-LDI, plus Ingress MPLS router alert frames, which are punted
MPLS_PLU_PUNT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
MPLS_FOR_US Punt MPLS received with a label allocated to a local router address - punted to CPU for processing
MPLS_FOR_US_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_L2TP_COOKIE_MISMATCH Punt Not implemented by ucode
PUNT_L2TP_COOKIE_MISMATCH_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_L2TP_TUNNEL_DOWN Punt Not implemented by ucode
PUNT_L2TP_TUNNEL_DOWN_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
GRE_BAD_FLAGS Punt Not implemented by ucode
GRE_BAD_FLAGS_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
GRE_NON_IPV4 Punt Not implemented by ucode
GRE_NON_IPV4_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
IPV4_TUNNEL_NOT_CONFIGD Punt Not implemented by ucode
IPV4_TUNNEL_NOT_CONFIGD_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_VCCV_PKT Punt Ingress MPLS frames that are PW VCCV frames - must be PWtoAC de-aggregation flows
PUNT_VCCV_PKT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_QNET_PKT Punt Not implemented by ucode
PUNT_QNET_PKT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_SERVICE_CARD Punt Not implemented by ucode
PUNT_SERVICE_CARD_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_STATISTICS Punt Statistics gathering frames punted to LC host - generated by statistics scanning machine
PUNT_STATISTICS_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_DIAGS_RSP_ACT Punt Not implemented by ucode
PUNT_DIAGS_RSP_ACT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_DIAGS_RSP_STBY Punt Not implemented by ucode
PUNT_DIAGS_RSP_STBY_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
NETIO_RP_TO_LC_CPU_PUNT Punt Preroute egress inject frames received from the RP that are sent to the LC host
NETIO_RP_TO_LC_CPU_PUNT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
MOFRR_PUNT Punt IPV4 multicast-only fast reroute punts. These are notices to the LC to indicate traffic activity or loss. NOTE: Subtract MDF_MOFRR_SWITCH_IGNORED from this to find the actual number of punts, since this counter is incremented prior to the switch-ignored check.
MOFRR_PUNT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
VIDMON_PUNT Punt Video monitoring punt frames
VIDMON_PUNT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
VIDMON_PUNT_FLOW_ADD Punt Video monitoring new flow added punt frames
VIDMON_PUNT_FLOW_ADD_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
DBGTRACE_PUNT Punt Debug Trace Packets
DBGTRACE_PUNT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
SYNCE_PUNT Punt Synchronous ethernet packets punted
SYNCE_PUNT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
CFM_CC Punt Continuity Fault Management
CFM_CC_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
CFM_CCM_RSP_PUNT Punt Continuity Fault Management Packets punted to RSP
CFM_CCM_RSP_PUNT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
MSTP_RSP_PUNT Punt STP packets through normal bridging
MSTP_RSP_PUNT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
MSTP_PB_RSP_PUNT Punt STP packets through bundle interface, punted to RSP
MSTP_PB_RSP_PUNT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
MVRP_PUNT Punt MVRP 1D packets punted
MVRP_PUNT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
MVRP_PB_PUNT Punt MVRP 1AD packets punted
MVRP_PB_PUNT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
MVRP_RSP_PUNT Punt MVRP1D packets coming over bundle and getting punted to RSP
MVRP_RSP_PUNT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
MVRP_PB_RSP_PUNT Punt MVRP 1AD packets coming over bundle and punted to RSP
MVRP_PB_RSP_PUNT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_NETFLOW Punt frames copied for Netflow accounting - punted to CPU for processing
PUNT_NETFLOW_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_OF_FSOL Punt Punt OF FSOL packets
PUNT_OF_FSOL_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
MPLS_FRAG_NEEDED_PUNT Punt MPLS packet for which fragmentation is required
MPLS_FRAG_NEEDED_PUNT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
MPLS_TTL_ONE_PUNT Punt MPLS packet for which TTL expired
MPLS_TTL_ONE_PUNT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_IPV4_ADJ_NULL_RTE Punt IPv4 packets with NULL route adjacency
PUNT_IPV4_ADJ_NULL_RTE_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_IPV6_ADJ_NULL_RTE Punt IPv6 packets with NULL route adjacency
PUNT_IPV6_ADJ_NULL_RTE_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_L2_IPIW_ARP Punt L2VPN IP Interworking ARP packets
PUNT_L2_IPIW_ARP_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_MAC_SECURE_VIOLATION Punt MAC security violation packets
PUNT_MAC_SECURE_VIOLATION_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_MAC_SECURE_VIOLATION_SHUT Punt Packets punted as shutdown MAC secure violations
PUNT_MAC_SECURE_VIOLATION_SHUT_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_DAI_VIOLATION Punt Packets punted for Dynamic Arp Inspection violation
PUNT_DAI_VIOLATION_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_IPSG_VIOLATION Punt Packets punted for IP Source Guard violation
PUNT_IPSG_VIOLATION_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_LLDP Punt Link Layer Discovery Protocol(LLDP) packets punted
PUNT_LLDP_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_LLDP_RSP Punt Link Layer Discovery Protocol(LLDP) packets over bundle punted to RSP
PUNT_LLDP_RSP_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_ELMI Punt Enhanced Local Management Interface(ELMI) packets punted
PUNT_ELMI_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_PVST Punt Packet punted for Per Vlan Spanning Tree Protocol
PUNT_PVST_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_ERP_LC Punt Ethernet Ring Protection Switching protocol (G.8032 ERPS) - punted to LC CPU for processing
PUNT_ERP_LC_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_ERP_RSP Punt Ethernet Ring Protection Switching protocol (G.8032 ERPS) - punted to RSP CPU for processing
PUNT_ERP_RSP_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_NETIO_LC_TO_RSP Punt packets from netio of LC punted to RSP
PUNT_NETIO_LC_TO_RSP_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_DBA Punt Destination based netflow packets punted
PUNT_DBA_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_CLUSTER_LINKMON Punt Cluster link monitoring packets punted
PUNT_CLUSTER_LINKMON_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_CLUSTER_DSC Punt Cluster Distributed Shelf Controller packets punted
PUNT_CLUSTER_DSC_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_CLUSTER_TEST Punt Cluster Test packets punted
PUNT_CLUSTER_TEST_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_PTP_ETHERNET Punt PTP ethernet frames punted
PUNT_PTP_ETHERNET_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_PTP_IPV4 Punt Point-to-point IPv4 packets punted
PUNT_PTP_IPV4_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_PTP_IPV6 Punt Point-to-point Ipv6 packets punted
PUNT_PTP_IPV6_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_DIAGS_RX_BUFF Punt Diagnostic Receive Buffer packets punted
PUNT_DIAGS_RX_BUFF_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_PPP_RSP Punt On a bundle subscriber interface, a PPP Control packet was received on a PPPoE enabled parent interface and punted to the RSP
PUNT_PPP_RSP_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_PPPOE_RSP Punt On a bundle subscriber interface, a PPPoE Ctrl packet was received on a PPPoE enabled parent interface and punted to the RSP
PUNT_PPPOE_RSP_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_PPPOE_PACKET_CONFIG_MISMATCH Punt On a non-bundle subscriber interface, a PPPoE Control or Data packet was received on a PPPoE parent interface, met one of the following conditions and was punted to the RSP. 1. SRC Mac did not match sessions SRC Mac, 2. VLAN ID(s) inner and/or outer did not match sessions VLAN IDs, 3. Session ID was invalid.
PUNT_PPPOE_PACKET_CONFIG_MISMATCH_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_PPPOE_PACKET_CONFIG_MISMATCH_RSP Punt On a bundle subscriber interface, a PPPoE Control or Data packet was received on a PPPoE parent interface, met one of the following conditions and was punted to the RSP. 1. SRC Mac did not match sessions SRC Mac, 2. VLAN ID(s) inner and/or outer did not match sessions VLAN IDs, 3. Session ID was invalid.
PUNT_PPPOE_PACKET_CONFIG_MISMATCH_RSP_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_PPPOE_L2TPV2 Punt Layer 2 Tunneling Protocol Version 2 packets punted
PUNT_PPPOE_L2TPV2_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_MAC_CACHE_MSG Punt MAC cache message packets
PUNT_MAC_CACHE_MSG_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_UDLD Punt Unidirectional link detection packets punted
PUNT_UDLD_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_HTTPR Punt Policy Based HTTP Redirect punt
PUNT_HTTPR_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_SDP Punt Cisco Nv Network Virtualization Satellite Discovery Protocol
PUNT_SDP_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_MIRP Punt Punt MIRP - 802.1ah bridge multiple i-tag registration protocol
PUNT_MIRP_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_UNCLASSIFIED Punt Punt BNG subscriber first sign of life packet
PUNT_UNCLASSIFIED_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_UNCLASSIFIED_RSP Punt Punt BNG subscriber first sign of life packet
PUNT_UNCLASSIFIED_RSP_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_PVST_RSP Punt Packet punted for Per Vlan Spanning Tree Protocol
PUNT_PVST_RSP_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_LISP_ADJ Punt Lawful Intercept Support Platform
PUNT_LISP_ADJ_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_MLD_SNOOP Punt Punt IPv6 MLD - multicast listener discovery protocol
PUNT_MLD_SNOOP_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_INLINE_SERVICE Punt Generic Inline Service punt
PUNT_INLINE_SERVICE_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_PTP_LAG Punt PTP on link bundle
PUNT_PTP_LAG_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_MPLS_TP_BFD Punt Punt BFD protocol over MPLS-TP
PUNT_MPLS_TP_BFD_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_CDP_RSP Punt Punt CDP packets to RSP
PUNT_CDP_RSP_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_NETFLOW_RESERVED Punt Punt Netflow reaserved
PUNT_NETFLOW_RESERVED_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_PAGENT1 Punt Punt Pagent1
PUNT_PAGENT1_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_PAGENT2 Punt Punt Pagent2
PUNT_PAGENT2_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_EFM_RSP Punt Punt EFM to RSP
PUNT_EFM_RSP_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
CFM_HWO_OTHER Punt Offloaded Packets(3.3 and 10ms)for which rx table lookup fails or whose mac mis-matches. These packets have to be rate limited since these can cause actual offloaded packets to get dropped
CFM_HWO_OTHER_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_IFIB_OPT_MISS Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
PUNT_IFIB_OPT_MISS_EXCD Punt Frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
DROP_FRM_CRC_ERR_XAUI0 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_XAUI0 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_XAUI1 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_XAUI1 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_XAUI2 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_XAUI2 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_XAUI3 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_XAUI3 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_XAUI4 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_XAUI4 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_XAUI5 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_XAUI5 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_XAUI6 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_XAUI6 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_XAUI7 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_XAUI7 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_XAUI8 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_XAUI8 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_XAUI9 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_XAUI9 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_ILKN0 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_ILKN0 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_ILKN1 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_ILKN1 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_ILKN2 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_ILKN2 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_NULL13 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_NULL13 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_NULL14 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_NULL14 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_NULL15 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_NULL15 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII0 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII0 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII1 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII1 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII2 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII2 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII3 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII3 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII4 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII4 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII5 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII5 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII6 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII6 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII7 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII7 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII8 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII8 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII9 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII9 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII10 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII10 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII11 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII11 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII12 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII12 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII13 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII13 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII14 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII14 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII15 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII15 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII16 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII16 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII17 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII17 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII18 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII18 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII19 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII19 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII20 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII20 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII21 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII21 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII22 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII22 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII23 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII23 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII24 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII24 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII25 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII25 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII26 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII26 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII27 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII27 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII28 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII28 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII29 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII29 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII30 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII30 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII31 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII31 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII32 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII32 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII33 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII33 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII34 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII34 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII35 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII35 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII36 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII36 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII37 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII37 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII38 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII38 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII39 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII39 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII40 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII40 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII41 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII41 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII42 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII42 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII43 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII43 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII44 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII44 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII45 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII45 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII46 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII46 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_SGMII47 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_FRM_ERR_SGMII47 Drop Infra Ingress Frames dropped due to Ethernet CRC or input overrun error - either because they were received with a CRC error from the wire (which will be counted in show interface error counts), or due to input FIFO overrun (which can occur under extreme NP packet per second overload conditions)
DROP_FRM_CRC_ERR_HOST_SGMII Drop Infra Frames from linecard CPU dropped due to CRC or overrun error. Either due to an NP FIFO overrun (which can occur under extreme NP packet per second overload conditions); or NP software in a bad state; or errors on the internal link.
DROP_FRM_FRM_ERR_HOST_SGMII Drop Infra Frames from linecard CPU dropped due to CRC or overrun error. Either due to an NP FIFO overrun (which can occur under extreme NP packet per second overload conditions); or NP software in a bad state; or errors on the internal link.
DROP_FRM_CRC_ERR_OTHER_INT Drop Infra Frames from linecard CPU dropped due to CRC or overrun error. Either due to an NP FIFO overrun (which can occur under extreme NP packet per second overload conditions); or NP software in a bad state; or errors on the internal link.
DROP_FRM_FRM_ERR_OTHER_INT Drop Infra Frames from linecard CPU dropped due to CRC or overrun error. Either due to an NP FIFO overrun (which can occur under extreme NP packet per second overload conditions); or NP software in a bad state; or errors on the internal link.
RSV_BFD_HWOFF_TIMEOUT_PUNT
RSV_HWOFF_EGR_FWD
RSV_BFD_HWOFF_LPBK_RX_DISC
RSV_BFD_HWOFF_LPBK_RX_V6_CRC_DROP
RSV_BFD_HWOFF_LPBK_RX_PKT_CNT
RSV_BFD_HWOFF_LPBK_RX_ECHO_CNTR
RSV_BFD_HWOFF_LPBK_RX_PUNT
MDF_PIPE_LPBK Infra FYI. Internal Debug. NP internal loopback for further processing
MDF_PIPE_LPBK_EXCEPTION_DROP Drop Infra dropped due to not enough NP buffer resources. This drop occurs during NP internal loopback processing and may be dropping a copy of the frame rather than the original. This error could also possibly indicate a software error if drop is occurs when the NP is not under extreme load.
MDF_PIPE_LPBK_BUFFER_PREFETCH Infra FYI. Debug. NP extra buffer allocation during internal loopback.
MDF_DROP_RPF_FAIL Drop MCAST IP multicast frames that failed reverse-path-forwarding check but not punted due to NPRF (RPF punt table) result
MDF_OPEN_NETWORK_SERVICE_MODULE_ENTER Service internal debug event
MDF_OPEN_NETWORK_SERVICE_SEND_TO_CONTROLLER Service internal debug event
MDF_OPEN_NETWORK_SERVICE_PICK UNKNOWN ACTION Drop Service inline service - internal error - frames dropped
MDF_OPEN_NETWORK_SERVICE_DONE_WTIH_SVC Service inline service - internal event
MDF_OPEN_NETWORK_SERVICE_TRGR_FWD_LKUP Service inline service - internal event
MDF_OPEN_NETWORK_SERVICE_TRGR_SVC_LKUP Service inline service - internal event
MDF_OPEN_NETWORK_SERVICE_ACTION_DROP
MDF_OPEN_NETWORK_SERVICE_SANITY_CHECK_FAIL
MDF_OPEN_NETWORK_SERVICE_WRG_KEY_BUILDER
MDF_MOFRR_SWITCH_IGNORED MCAST MoFRR switchover message heeded but not punted because NP ID mismatch. Only the NP that sends the message punts it. Note that this value should be subtracted from the MOFRR_PUNT counter (incremented prior to this one).
MDF_HWOFF_UNIDIR_NP_REDUN_DROP Drop HW Offload redundant drop - timeout (in unidir egress NP) OR TX frame (in unidir ingress NP).
MDF_MOFRR_LOSS_PUNT MCAST MoFRR switchover messages punted to LC CPU for signalling
MDF_PUNT_POLICE_DROP Drop Infra Aggregate drop count for Control Plane punt policing. There should be a more specific _EXCD counter incremented for the punt reason code.
MDF_DROP_PUNT_REASON_NO_MATCH Drop Infra dropped due to software error while attempting to punt a frame to CPU
MDF_DROP_EGR_PORT_NO_MATCH Drop Infra Frames dropped due to inconsistent software state which may occur during reprogramming
MDF_DROP_RACK_NO_MATCH
MDF_DROP_EGR_MN_PORT_NO_MATCH Drop Infra Count of mac notifies that are skipped due to egress port table lookup miss. Indicates a programming error.
MODIFY_SPAN_MISS_DROP Drop SPAN Frames dropped due to inconsistent software state which may occur during reprogramming
MDF_PUNT_RSP_VIA_HOST_PORT Infra FYI. Debug. Special Punt handling
MODIFY_PUNT_REASON_MISS_DROP Drop Infra Frames dropped due to inconsistent software state which may occur during reprogramming
BFD_NEIGHBOR BFD BFD ASYNC received - punting to CPU for processing
BFD_NEIGHBOR_DROP Drop BFD BFD frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
BFD_LOOP BFD BFD ECHO received - punting to CPU for processing
BFD_MULTIHOP BFD BFD MULTIHOP received - punting to CPU for processing
BFD_MULTIHOP_DROP Drop BFD BFD frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
BFD_IPv6_NEIGHBOR BFD BFD ASYNC received - punting to CPU for processing
BFD_IPv6_NEIGHBOR_DROP Drop BFD BFD frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
BFD_IPv6_LOOP BFD BFD ECHO received - punting to CPU for processing
BFD_IPv6_LOOP_DROP Drop BFD BFD frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
BFD_REMOTE_PUNT_DISC_0 BFD BFD received for session that must be synchronized with all LC CPUS - multicasting punt to all LC CPUs
BFD_REMOTE_PUNT_DISC_0_DROP Drop BFD BFD frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
BFD_REMOTE_PUNT_DISC_1 BFD BFD received for session that is running on another LC - punting to CPU on other LC
BFD_REMOTE_PUNT_DISC_1_DROP Drop BFD BFD frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
BFD_REMOTE_PUNT_DISC_2 BFD BFD received for session that is running on another LC - punting to CPU on other LC
BFD_REMOTE_PUNT_DISC_2_DROP Drop BFD BFD frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
BFD_REMOTE_PUNT_DISC_3 BFD BFD received for session that is running on another LC - punting to CPU on other LC
BFD_REMOTE_PUNT_DISC_3_DROP Drop BFD BFD frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
BFD_REMOTE_PUNT_DISC_4 BFD BFD received for session that is running on another LC - punting to CPU on other LC
BFD_REMOTE_PUNT_DISC_4_DROP Drop BFD BFD frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
BFD_REMOTE_PUNT_DISC_5 BFD BFD received for session that is running on another LC - punting to CPU on other LC
BFD_REMOTE_PUNT_DISC_5_DROP Drop BFD BFD frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
BFD_REMOTE_PUNT_DISC_6 BFD BFD received for session that is running on another LC - punting to CPU on other LC
BFD_REMOTE_PUNT_DISC_6_DROP Drop BFD BFD frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
BFD_REMOTE_PUNT_DISC_7 BFD BFD received for session that is running on another LC - punting to CPU on other LC
BFD_REMOTE_PUNT_DISC_7_DROP Drop BFD BFD frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
BFD_REMOTE_PUNT_DISC_8 BFD BFD received for session that is running on another LC - punting to CPU on other LC
BFD_REMOTE_PUNT_DISC_8_DROP Drop BFD BFD frames that would normally be punted to CPU but were dropped due to Control Plane Policing. The pps policed limit is aggregated across the NP for all punts of this reason/protocol. (See description of counter without _EXCD for details of the frame being punted)
MODIFY_BFD_TABLE_LOOP_ERROR Drop BFD dropped unexpected BFD packet received over virtual interface or software error
MODIFY_BFD_TABLE_INDEX_ERROR Drop BFD dropped unexpected BFD response - Discriminator does not match what we sent
MODIFY_BFD_TABLE_ENTRY_ERROR Drop BFD dropped unexpected BFD response - Discriminator does not match what we sent
MODIFY_PUNT_NF_MSG Netflow FYI. Internal Debug. Special handling of buffers for PUNT_NETFLOW
MODIFY_PUNT_NF_IPV4 Netflow FYI. Internal Debug. Special handling of buffers for PUNT_NETFLOW
MODIFY_SEND_TO_INTER_RACK_NP_CNT Infra Internal debug event
MODIFY_NF_PUNT_RFD_PREFETCH_FAIL Netflow FYI. Internal Debug. Special handling of buffers for PUNT_NETFLOW
MODIFY_SIM_ONLY_WRED_MATCH_CNT Infra Internal debug event
MODIFY_SIM_ONLY_Q_PRI Infra Internal debug event
MODIFY_EFM_PORT_EGR_BLOCK Drop EOAM Ethernet OAM dropped egress frame because port is in blocked/loopback oam mode
MDF_EGR_MiM_SAT_DATA
DBG_LRN_EP_L_ON_DEMAND Infra Learn machine event - ON-DEMAND MAC learn in Flush and Scan modes
DBG_LRN_REFRESH_ABORT_CNT Infra Learn machine event - Abort refresh due to queue full
DBG_LRN_ADD_CNT Infra Learn machine event - added entry
DBG_LRN_DELETE_CNT Infra Learn machine event - removed entry
DBG_LRN_MAC_CACHE_QUEUE_FULL_CNT Infra Learn machine event - Number of times Scan message needed to wait for room on the queue
DBG_LRN_DEL_MSG_QUEUE_FULL_CNT Infra Learn machine event - Number of times checking whether the message queue is full
LRN_ON_DEMAND_FLUSH_DELETE_ENTRY Infra Learn machine event - Number of mac entries deleted by all on-demand flush requests from the host.
LRN_PERIODIC_AGING_DELETE_ENTRY Infra Learn machine event - Number of mac entries deleted by the aging scan machine due to aging out, or due to a learn key mismatch detected.
LRN_L2FIB_MAC_TBL_FULL Infra Learn machine event - Counts of missed learns due to mac hash table full. Only possible at high scale.
VIDMON_LRN_ADD_ABORT_CNT Infra Learn machine event - Vidmon flow learn operations aborted
VIDMON_LRN_ADD_FAIL_CNT Infra Learn machine event - Vidmon flow learn operations that failed
VIDMON_MDI_LRN_ADD_FAIL_CNT Vidmon Learn machine event - Vidmon learn
VIDMON_RSV_TIMEOUT Vidmon Learn machine event - Vidmon learn timeout
VIRTUAL_IF_LAYER2_UCAST_INPUT_CNT Infra Dummy interface accounting for certain internal loopback servicing of frames
VIRTUAL_IF_LAYER2_MCAST_INPUT_CNT Infra Dummy interface accounting for certain internal loopback servicing of frames
VIRTUAL_IF_LAYER2_BCAST_INPUT_CNT Infra Dummy interface accounting for certain internal loopback servicing of frames
VIRTUAL_IF_PROTO_IPV4_MCST_INPUT_CNT Infra Dummy interface accounting for certain internal loopback servicing of frames
VIRTUAL_IF_GENERIC_INPUT_DROP Drop Infra Dummy interface accounting for certain internal loopback servicing of frames
VIRTUAL_IF_PROTO_IPV6_MCST_INPUT_CNT Infra Dummy interface accounting for certain internal loopback servicing of frames
VIRTUAL_IF_PROTO_MPLS_INPUT_CNT Infra Dummy interface accounting for certain internal loopback servicing of frames
VIRTUAL_IF_PROTO_IPV4_UCST_INPUT_CNT Infra Dummy interface accounting for certain internal loopback servicing of frames
VIRTUAL_IF_PROTO_IPV6_UCST_INPUT_CNT Infra Dummy interface accounting for certain internal loopback servicing of frames
VIRTUAL_IF_LAYER2_BCAST_EXCD_DROP_CNT Drop Infra Dummy interface accounting for certain internal loopback servicing of frames
VIRTUAL_IF_LAYER2_MCAST_EXCD_DROP_CNT Drop Infra Dummy interface accounting for certain internal loopback servicing of frames
VIRTUAL_IF_LAYER2_UNK_UCAST_EXCD_DROP_CNT Drop Infra Dummy interface accounting for certain internal loopback servicing of frames
VIRTUAL_IF_GENERIC_UNK_PROT_DROP_CNT Drop Infra Dummy interface accounting for certain internal loopback servicing of frames
Fred Cuiller
Network Consulting Engineer @ Cisco
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for the explanations. However, i have these increamenting counters and i am not sure what to do to resolve them: Any suggestions will be very appreciated.
#show drops np np6 location 0/4/cpu0
Mon Aug 11 20:26:47.166 UTC
Node: 0/4/CPU0:
----------------------------------------------------------------
NP 6 Drops:
----------------------------------------------------------------
PARSE_INGRESS_DROP_CNT 1
PARSE_EGRESS_DROP_CNT 100
RESOLVE_INGRESS_DROP_CNT 13
RESOLVE_AGE_MAC_STATIC_DROP_CNT 204
XID_ZERO_DISCARD 1
L2FLOOD_SRCDST_DROP 100
RESOLVE_MAC_NOTIFY_CTRL_DROP_CNT 13
RESOLVE_EGR_LAG_NOT_LOCAL_DROP_CNT 110
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
the first two Parse__ are just aggregate counters, indiciting the direction and stage in the npu that experiences the drops.
mac-notify are mac control frames in the system that is used for mac move and learning (hw mac learning) and these control frames are dropped after processing (in resolve).
xid zero discard is a packet that was linked to a sub interface which has an internal cross connect ID (XID) and that lookup was zero and that cant happen. being it only one this is not an issue.
age_mac is seen when there is a mac control packet going around to age out a packet, but we are not timing this mac out because it is static or some other persistent config that prevents us the aging.
lag_not local is the fact that we received a packet for transmission on a bundle member while this bundle member based on the hash val should not have been chosen. can be seen when the sw injects a packet to the wrong member or in very rare ocasions the ingress LC made the wrong decision.
l2flood/srcdest is seen when the soruce and destination are the same for a given packet, eg some sort of split horizon kicking in during the flooding of an l2 packet.
cheers
xander
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Just to add to Xander's reply. The lab_not_local counter is also normal to see in L2 environments. If you have L2 transport interfaces as part of a bridge domain on a bundle, we will send flooded traffic (mcast/bcast/unknown) to all members. Then each member runs the hashing to determine which should forward it. All the members that shouldn't forward it will drop it via this counter.
Thanks,
Bryan
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
hi Xander,
how can i solve this (the descriptions says that his error are internal):
RP/0/RSP0/CPU0:NAP-COR-001#show drops np np0 location 1/0/CPU0
Wed Sep 3 19:05:21.428 UTC
Node: 1/0/CPU0:
----------------------------------------------------------------
NP 0 Drops:
----------------------------------------------------------------
PARSE_EGR_INJ_PKT_TYP_UNKNOWN 60898912
PARSE_DROP_IN_UIDB_TCAM_MISS 364
PARSE_DROP_IN_UIDB_DOWN 2188267
PARSE_DROP_IPV4_DISABLED 9769
PARSE_DROP_IPV6_DISABLED 7600
RSV_DROP_EGR_UIDB_NO_MATCH 5860
RSV_DROP_IPV4_TXADJ_NO_MATCH 188656
RSV_DROP_IPV6_TXADJ_NO_MATCH 11
RSV_DROP_IPV4_NRLDI_NOT_LOCAL 1121
RSV_DROP_IFIB_TTL_CHECK 1
RESOLVE_INV_REMOTE_RACK_UIDB_DROP_CNT 18596
PUNT_NO_MATCH_EXCD 7497291
IPV4_TTL_ERROR_EXCD 3878000
PUNT_ADJ_EXCD 90171
PUNT_IPV4_ADJ_NULL_RTE_EXCD 42441800
MDF_PUNT_POLICE_DROP 53907707
MDF_DROP_RACK_NO_MATCH 1506510
MODIFY_PUNT_REASON_MISS_DROP 4
----------------------------------------------------------------
RP/0/RSP0/CPU0:NAP-COR-001#show controllers np descriptions location 1/0/CPU0 | i PARSE_EGR_INJ_PKT_TYP_UNKNOWN
Wed Sep 3 19:05:36.883 UTC
PARSE_EGR_INJ_PKT_TYP_UNKNOWN Infra Frames received from RSP of unknown type (internal error)
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
hi oscar,
that would be a sw bug. as it should not happen.
but considering the fact that I dont see rate counters in your sample output, makes me believe you are running a very very old code is that right?
I think this may be pre 40<something>.
unfortunately, 39x and 40x are all end of support already, so while I am not denying that this is a sw bug, it will be hard to tshoot this further also in those releases. I woudl want to recommend evaluating 434 or 513 (out 9/5).
xander
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Xander,
Here is the output from command 'show controller np count np0 loc 0/5/CPU0 | in DROP' on ASR with ios xr 4.3.4. We are having some multicast performance issue at the moment. Could you let me know which DROP could contribute to the multicast issue on ASR? Thanks.
Fri Oct 24 14:22:41.182 AEST
31 PARSE_INGRESS_DROP_CNT 1811361 1
33 RESOLVE_INGRESS_DROP_CNT 20244163 0
34 RESOLVE_EGRESS_DROP_CNT 298233873 3
96 RESOLVE_AGE_NOMAC_DROP_CNT 1 0
154 DROP_IPV4_NOT_ENABLED 1 0
321 RESOLVE_L2_EGR_PW_UIDB_MISS_DROP_CNT 294926946 2
333 RESOLVE_VPLS_EGR_FLD_NO_MEMBERS_DROP_CNT 2100721 1
339 RESOLVE_MAC_NOTIFY_CTRL_DROP_CNT 20244154 0
340 RESOLVE_MAC_DELETE_CTRL_DROP_CNT 75 0
354 RESOLVE_IPMC_ING_DFLAG_DROP_CNT 1206122 1
356 RESOLVE_IPM4_EGR_RTE_DROP_CNT 8 0
447 UIDB_TCAM_MISS_AGG_DROP 3767 0
454 UIDB_TCAM_MISS_PORT6_DROP_FOR_HOST 3767 0
Regards, Leo
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
hard to say not knowing the topo or config, also the drop rates are very low.
the only thing that stands out that there appears to be a flooding issue inside a BD (2pps),
but it is not significant enough that rate to attribute to mcast lost, only thing I can visualize based on this is that the IGMP snooping is not set up correctly and we flood mcast in the BD, but that would be a config issue.
xander
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Could you explain the counter RSV_DROP_ING_IFIB_OPT? I have seen too many input drops on a specif interface and I couldnt figure out what is causing that, the only thing I can see is that the counter RSV_DROP_ING_IFIB_OPT keep incrementing.
Thanks in advance,
Renato Reis
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Renato,
this drop counter is set when IGMP, ISIS, OSPF (v2/v3) or PIM are received on an interface that doesnt have it configured. So IFIB (internal FIB redirecting "for me" packets) wants to sent it over to an LC or RP CPU, but is getting dropped because there is no configured proto for it, what it detected before/during punting.
If this is related to OSPF and you have security TTL configured, you may be running into CSCui01487
xander
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for your reply,
Can you help me to figure out why I have all these input drops on the interface below?
RP/0/RSP0/CPU0:router#sh interfaces tenGigE 0/0/0/9
Wed Jan 14 07:14:57.970 BRA
TenGigE0/0/0/9 is up, line protocol is up
Interface state transitions: 3
Hardware is TenGigE, address is 10f3.1133.6771 (bia 10f3.1133.6771)
Layer 1 Transport Mode is LAN
Description: RJOFRGSTR04-ETH09 - VLAN 732
Layer 2 Transport Mode
MTU 1514 bytes, BW 10000000 Kbit (Max: 10000000 Kbit)
reliability 255/255, txload 0/255, rxload 3/255
Encapsulation ARPA,
Full-duplex, 10000Mb/s, link type is force-up
output flow control is off, input flow control is off
loopback not set,
Last input 00:00:00, output 00:00:00
Last clearing of "show interface" counters 5d23h
5 minute input rate 122959000 bits/sec, 12361 packets/sec
5 minute output rate 13162000 bits/sec, 1933 packets/sec
32952012619 packets input, 43943466286410 bytes, 507954464 total input drops
0 drops for unrecognized upper-level protocol
Received 73338 broadcast packets, 0 multicast packets
0 runts, 0 giants, 0 throttles, 0 parity
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort
5129587238 packets output, 5367086709092 bytes, 0 total output drops
Output 152405949 broadcast packets, 54487 multicast packets
0 output errors, 0 underruns, 0 applique, 0 resets
0 output buffer failures, 0 output buffers swapped out
0 carrier transitions
RP/0/RSP0/CPU0:router#
[]'s
Renato Reis
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
the input drops reported there are an accumulation of ANY drop that is related to the interface. This includes ACL drops, policer drops, scheduler drops, and all that.
"errors" are phy related ones such as CRC and aborts etc.
So with this number of input drops, you want to verify that against the most common items such as ACL/QOS etc
the remainder can be due to other kinds as depicted in the NP counters very likely to be verified with a show (controller np counter) drops command.
it might make sense to clear the np counters nad interface counter first to derive an "ongoing" issue.
Next I would also reference the Cisco Live id 2904 from Orlando and Sanfran which have specific sections about verifying input drops specifically.
cheers!
xander
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I have the same input drops under bundle-ether MPLS links.
RSV_DROP_MPLS_LEAF_NO_MATCH 56
Interfaces works correct (no flapping), nobody touch them. Interface config is very simple:
interface TenGigE0/0/1/0
bundle id 1 mode passive
!
interface TenGigE0/0/1/0
bundle id 1 mode passive
!
interface Bundle-Ether1
mtu 9014
ipv4 mtu 1500
ipv4 address X.X.X.X 255.255.255.252
I have about 50 drops per 5 minutes. How i can determine the reason?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
could be many reasons for this Dmitriy, it could be a sw bug or an LSP taht has not been built yet while we receive packets for that rsvp/lsp.
if you have typhoon linecards you can capture packets that match this reason and we can decode them to see if that destination/label matches any configured services so we can relate to the precise circuit that is causing this.
without the capture and release/smu info, it will be wild guessing :).
when you have the packet capture, best to open a new discussion on the main forum for everyone to see, learn from and contribute.
cheers
xander
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Xander,
I guess this is typo .. isn’t it? since there is same description for MODIFY_INGRESS_DROP_CNT.
MODIFY_EGRESS_DROP_CNT : Total packets dropped by ingress NP in the modify engine
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: