- Cisco Community
- Technology and Support
- Service Providers
- Service Providers Knowledge Base
- ASR9000/XR: Understanding BGP flowspec (BGP-FS)
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
06-07-2014 01:55 PM - edited 08-08-2019 08:04 AM
Introduction
BGP flow spec is a new tool that can be used to assist in DDOS mitigation in a dynamic fashion, levering BGP.
When I first started working and looking at BGP-FS I was a bit confused and in this article I would like to try and unravvle some of the specifics of BGP-FS, what you can do with it and how it works.
DDOS mitigation via RTBH (remote triggered blackhole)
Conceptually in this picture:
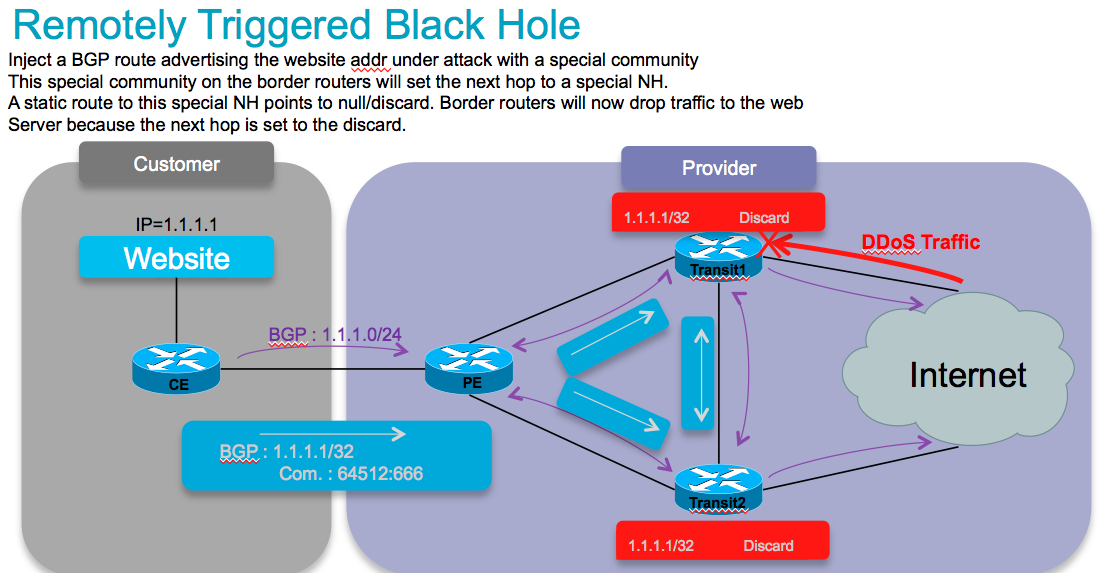
DDOS mitigation with the help of BGP is generally done via RTBH (remote triggered blackhole). And this comes basically in 2 key flavors: Source and Destination based.
The concept is that a BGP edge speaker has a static route defined to a "special next hop" to null0.
From a central point we inject a new route for a particular destination (eg our affected webserver) with a next hop pointing to that special next hop. This means that now at our border routers, our webserver address is set to a next hop, and this next hop is drop, and we prevent this traffic from hitting our server. This protects it nicely. But it removes the ability to reach this server completely!
The source based model is a similar concept whereby we KNOW where an attack comes from and now we send in a bgp path for that source with the special next hop, which then points to null.
Now when we use uRPF (reverse path forwarding), when a packet from that suspect source comes in, we apply RPF, we find the nexthop set to null0/discard. This would make RPF fail and we drop the packet from that host (or subnet for that matter).
Both options work great, but are big hammers.
BGP flowspec allows for a more granular appraoch and effectively construct instructions to match a particular flow with source AND destination, and L4 parameters and packet specifics such as length, fragment etc, and allow for a dynamic installation of an action at the border rotuers to either:
- drop the traffic
- inject it in a different vrf (for analysis)
- or allow it, but police it at a specific defined rate.
Cool. Now that we got that theory out of the way, how about Flowspec then, what does it do and how is it different?!
BGP flowspec definitions
This conceptually describes how flowspec works:
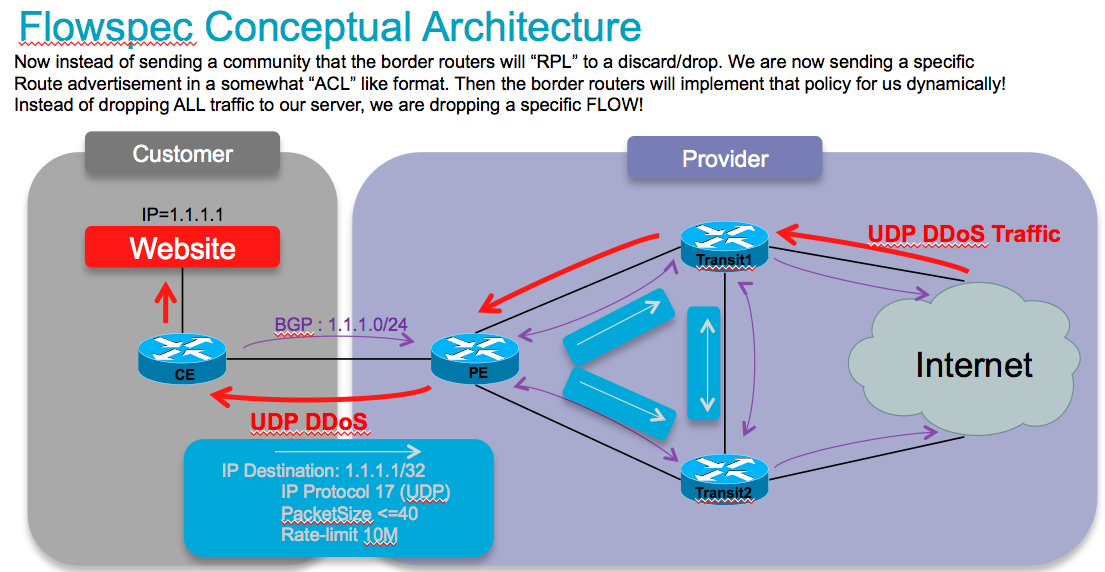
So instead of sending/injecting a route for our server or server subnet with a special community that the border routers will associated with a nexthop to drop in their route policy language, in this case we are sending the new flowspec attribute format down to the border routers instructing them to create a sort of ACL with class-map and policy-map to implement this rule that we are advertising!
Very nifty, am lovin it. So in order to do that, we need to extend the BGP protocol a bit, and this is how the RFC is defining that approach:
BGP FS adds a new NLRI (network layer reachability info) to the BGP protocol:
NLRI defined (AFI=1, SAFI=133)
It adds the following packet/attribute format:
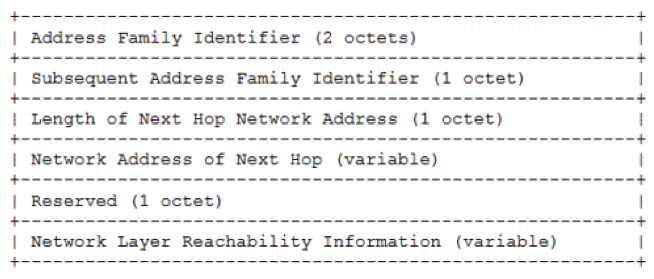
It allows for the following parameters to be defined:
6.Source Port (+1 component)
7.ICMP Type (asr9k has support for this yet, CRS does also)
8.ICMP Code (asr9k has support for this yet, CRS does also)
9.TCP Flags (asr9k supports lower byte, crs can not look at all bits)
10.Packet length
11.DSCP
12.Fragment
The actions that can be associated to a flow that we matched on by the parameters specified above are encoded as follows:

And the available actions that we can define are:
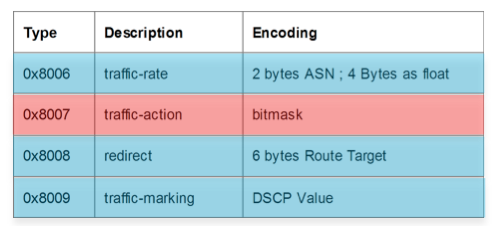
So with these new rules we can define a prefix or prefix set and not just that, we can base it on L3 source, L3 dest, its L4 specifics and even on packet length and L3 header options such as fragments! Then we can specify what actions we want to associate with that flow, redirect it, remark it, drop it or police it. And that is the full flow info.
All actions are supported by both CRS and ASR9000.
Ok this is all awesome, now that we got the theory out of the way, you want to go set it up I am sure!
Client/Server Model
In BGP-FS there is a client and a server. What that effectively means is that there is a device that injects the new flowspec entry (for the lack of a better word I guess) and there is a device (BGP speaker) that receives that NRLI and has to implement something in the hardware forwarding to act on that instruction.
So the device sending or injecting the NRLI is what I call the server, and the device that receive the NRLI and programs the hardware forwarding is called the client.
Visually:
CLIENT
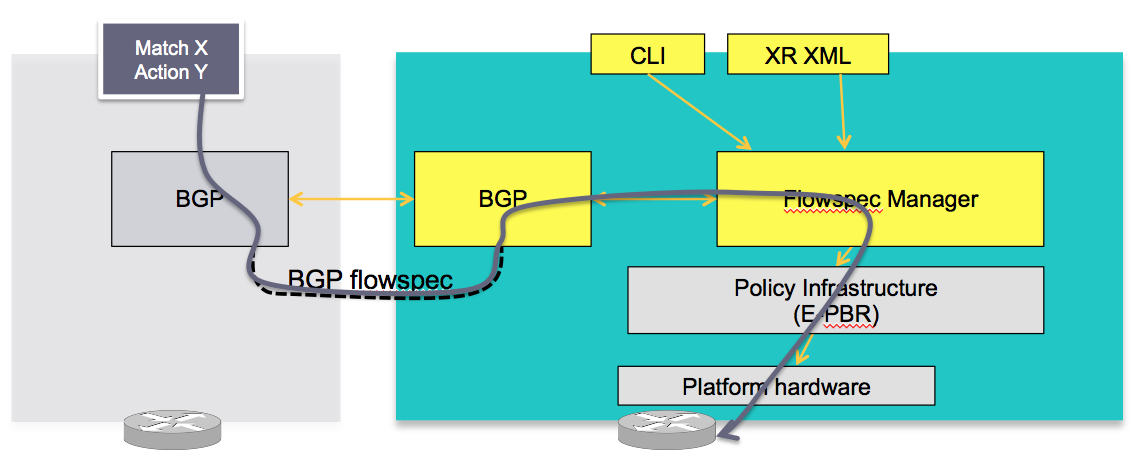
In this concept the server in the grey box injects the flowspec NRLI and the client in the right box receives the information, sends it to the flow spec manager, configures the ePBR (enhance Policy based routing) infrastructure who then in turn programs the hardware from the underlaying platform in use.
SERVER
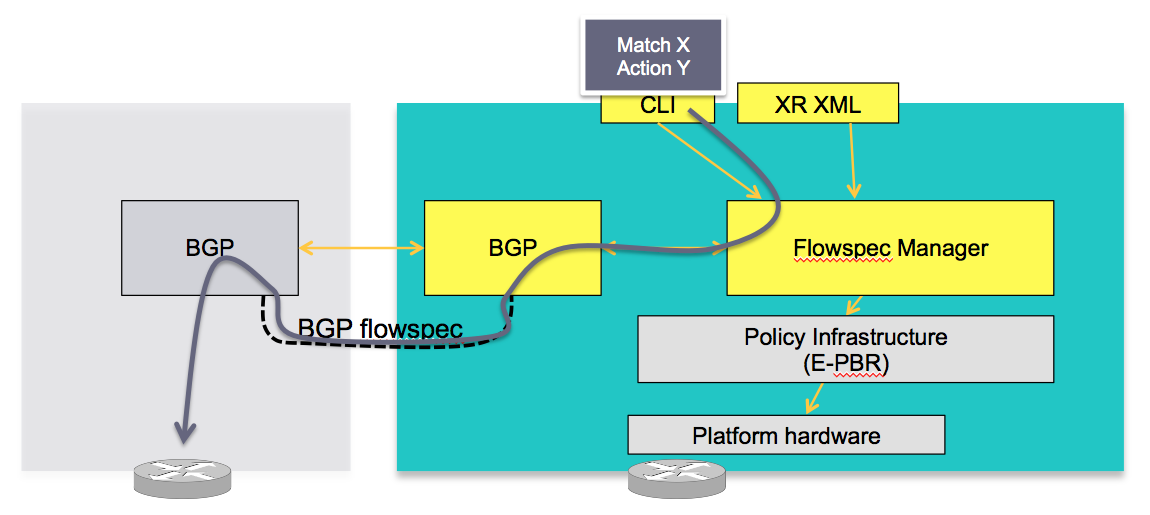
The server is configured either via CLI or XML to provide that entry for NRLI injection.
Note that XRv, virtual XR, can be a Server, it can inject those NRLI's for an asr9000 or CRS to act on those. Obviously XRv, not having a hardware forwarding layer is not a client
Configuration
conceptually
BGP
applicable to both client and server, we need to enable the new address family for advertisement:
router bgp 100
address-family ipv4 flowspec
! Initializes the global address family
address-family ipv6 flowspec
!
neighbor 1.1.1.1
remote-as 100
address-family ipv4 flowspec
! Ties it to a neighbor configuration
address-family ipv6 flowspec
!
Interface
You can disable flowspec on the interface as follows:
Interface gigabit0/0/0/0
ipv4 flowspec disable
!
Client
requires no special config other then a flowspec enabled peer.
Server
The server side configuration includes the policy-map definition and the association to the ePBR config consists of 2 portions, the class definition, and using that class in ePBR to define the action.
Classification
class-map type traffic match-all <class-name>
<match statement> #Any combination of tuples 1-13 match statements goes here.
end-class-map
!
!
Tuple definition possibilities:
#Type 1: match destination-address {ipv4| ipv6} <IPv4/v6 address>/<mask-length>
#Type 2: match source-address {ipv4| ipv6} <IPv4/v6 address>/<mask-length>
#Type 3: match protocol { <value> | <min_value> - <max_value> }
<!In case of IPv6, it will map to last next-header >
#Type 4: create two class-maps one with source-port and another with destionation-port
match source-port { <value> | <min_value> - <max_value> }
match destination-port { <value> | <min_value> - <max_value> }
<! Applicable only for TCP and UDP protocol !>
#Type 5: match destination-port { <value> | <min_value> - <max_value> }
#Type 6: match source-port { <value> | <min_value> - <max_value> }
#Type 7: match {ipv4 | ipv6} icmp-type { <value> | <min_value> - <max_value>}
#Type 8: match {ipv4 | Ipv6} icmp-code { <value> | <min_value> - <max_value>}
#Type 9: match tcp-flag <value> bit-mask <mask-value>
#Type 10: match packet length { <value> | <min_value> - <max_value> }
#Type 11: match dscp { <value> | <min_value> - <max_value> }
match ipv6 traffic-class { <value> | <min_value> - <max_value> }
[for providing 8 bit traffic class value]
#Type 12: match fragment-type {dont-fragment, is-fragment, first-fragment, last-fragment}
#Type 13: match ipv6 flow-label { <value> | <min_value> - <max_value> }
policy-map type pbr <policy-name>
class type traffic <class-name>
<action> #Any one of the extend community action listed below
class class-default
end-policy-map
ACTIONS:
##Traffic rate:
police rate < > | drop
#Traffic action:
sample-log
#Traffic marking:
set dscp <6 bit value> |
set ipv6 traffic-class <8 bit value>
#VRF redirect based on route-target:
redirect {ipv6} extcommunity rt <route_target_string>
# Redirect IP nexthop support
redirect {ipv6} next-hop <ipv4/v6 address> {ipv4/v6 address}
The following ties the flowspec to the PBR policies defined earlier.
flowspec
[local-install interface-all]
address-family ipv4
[local-install interface-all]
service-policy type pbr <policy-name>
service-policy type pbr <policy-name>
address-family ipv6
[local-install interface-all]
service-policy type pbr <policy-name>
service-policy type pbr <policy-name>
!
!
vrf <vrf-name>
address-family ipv4
[local-install interface-all]
service-policy type pbr <policy-name>
service-policy type pbr <policy-name>
address-family ipv6
[local-install interface-all]
service-policy type pbr <policy-name>
service-policy type pbr <policy-name>
!
!
!
Example use case/configuration:
Target:
all packets to 10.0.1/24 from 192/8 and destination-port {range [137, 139] or 8080, rate limit to 500 bps in blue vrf and drop it in vrf-default. Also disable flowspec getting enabled on gig 0/0/0/0.
Associated copy paste config:
class-map type traffic match-all fs_tuple
match destination-address ipv4 10.0.1.0/24
match source-address ipv4 192.0.0.0/8
match destination-port 137-139 8080
end-class-map
!
!
policy-map type pbr fs_table_blue
class type traffic fs_tuple
police rate 500 bps
!
!
class class-default
!
end-policy-map
policy-map type pbr fs_table_default
class type traffic fs_tuple
drop
!
!
class class-default
!
end-policy-map
flowspec
local-install interface-all
address-family ipv4
service-policy type pbr fs_table_default
!
!
vrf blue
address-family ipv4
service-policy type pbr fs_table_blue local
!
!
!
!
Interface GigabitEthernet 0/0/0/0
vrf blue
ipv4 flowspec disable
BGP Flowspec and local QoS configuration
When flowspec is implemented on an interface that is also having local QoS configuration, local config will come before flowspec processing.
Local config will police and dscp-mark the packets and pass them to flowspec.
Flowspec will then do its processing (police, redirect) except dscp marking.
Flowspec will retain dscp marking as dictated by local qos config.
Say, we have the following:
inbound qos config : police 100Mbps, mark dscp af11
=============================================================
ipv4 access-list acl_ipv4_qos_stream
6 permit ipv4 any host 200.255.5.2
!
!
class-map match-any cm_ipv4_qos_stream
match access-group ipv4 acl_ipv4_qos_stream
end-class-map
!
policy-map pm_ipv4_qos_stream
class cm_ipv4_qos_stream
police rate 100 mbps
!
set dscp af11
!
class class-default
!
end-policy-map
!
interface hundredGigE 0/4/0/35
service-policy input pm_ipv4_qos_stream
=============================================================
Then we receive the following in flowspec advertisement.
flowspec config : police 50Mbps, mark dscp af43, redir vrf.
=============================================================
RP/0/RP0/CPU0:fretta-50#sh flowspec ipv4 detail | b 200.255.5.2
Flow :Dest:200.255.5.2/32
Actions :Traffic-rate: 50000000 bps DSCP: af43 Redirect: VRF honeypot Route-target: ASN2-4787:13 (bgp.1)
Statistics (packets/bytes)
Matched : 116570713/12822778430
Transmitted : 57360817/6309689870
Dropped : 59209896/6513088560
=============================================================
Then the outcome will be:
- traffic will be policed by flowspec at 50Mbps.
- traffic will be redirected by flowspec to VRF honeypot.
- flowspec will not overwrite dscp marking, traffic will be forwarded using dscp af11 instead of af43.
NCS5500 platform will also display this same behavior.
Related Information
Special thanks to Nic Fevrier whose pictures I used for some of the visuals above.
Xander Thuijs CCIE#6775
Principal Engineer, ASR9000
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Nicolas,
That is what it looks like isn't it? That's something that I tried before my last post. It doesn't seem to make a difference though:
!!!!!!!!!!!! on the client:
router bgp 200
neighbor 10.1.1.20
use neighbor-group RRR
!
router bgp 200
neighbor-group RRR
remote-as 200
capability additional-paths receive
capability additional-paths send
update-source Loopback0
send-buffer-size 131072 131072
receive-buffer-size 131072 131072
address-family vpnv4 unicast
route-policy VPNV4-IN in
maximum-prefix 16000000 75 warning-only
route-policy VPNV4-OUT out
!
address-family vpnv6 unicast
route-policy VPNV6-OUT out
!
address-family l2vpn vpls-vpws
route-policy L2VPN-VPLS-VPWS-OUT out
!
address-family ipv4 rt-filter
!
address-family l2vpn evpn
!
address-family ipv4 flowspec
validation disable
!
address-family ipv6 flowspec
validation disable
!
address-family vpnv4 flowspec
!
!
!
!!!!!!!!!!!!!!! on the reflector:
router bgp 200
neighbor 10.1.1.3
use neighbor-group PE
!
router bgp 200
neighbor-group PE
remote-as 200
capability additional-paths receive
capability additional-paths send
update-source Loopback1
send-buffer-size 131072 131072
receive-buffer-size 131072 131072
address-family vpnv4 unicast
route-reflector-client
maximum-prefix 16000000 75 warning-only
!
address-family vpnv6 unicast
route-reflector-client
maximum-prefix 16000000 75 warning-only
!
address-family l2vpn vpls-vpws
route-reflector-client
!
address-family ipv4 rt-filter
default-originate
!
address-family l2vpn evpn
route-reflector-client
!
address-family ipv4 flowspec
route-reflector-client
validation disable
!
address-family ipv6 flowspec
route-reflector-client
validation disable
!
address-family vpnv4 flowspec
route-reflector-client
!
!
!
!!!!!!!!!!!!!!! on the controller:
router bgp 200
neighbor 10.1.1.20
use neighbor-group RRR
!
router bgp 200
neighbor-group RRR
remote-as 200
capability additional-paths receive
capability additional-paths send
update-source Loopback0
send-buffer-size 131072 131072
receive-buffer-size 131072 131072
address-family vpnv4 unicast
maximum-prefix 16000000 75 warning-only
route-policy VPNV4_OUT out
!
address-family vpnv6 unicast
route-policy VPNV6_OUT out
!
address-family l2vpn vpls-vpws
route-policy L2VPN_VPLS-VPWS_OUT out
!
address-family ipv4 rt-filter
!
address-family l2vpn evpn
!
address-family ipv4 flowspec
validation disable
!
address-family ipv6 flowspec
validation disable
!
address-family vpnv4 flowspec
!
!
!!!!!!!!!!!! show commands on the client:
RP/0/RSP0/CPU0:9006-3-LAB#show bgp vpnv4 flowspec summary
BGP router identifier 10.1.1.3, local AS number 200
BGP generic scan interval 60 secs
Non-stop routing is enabled
BGP table state: Active
Table ID: 0x0 RD version: 0
BGP main routing table version 1
BGP NSR Initial initsync version 1 (Reached)
BGP NSR/ISSU Sync-Group versions 0/0
BGP scan interval 60 secs
BGP is operating in STANDALONE mode.
Process RcvTblVer bRIB/RIB LabelVer ImportVer SendTblVer StandbyVer
Speaker 1 1 1 1 1 0
Neighbor Spk AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down St/PfxRcd
10.1.1.20 0 200 5559202 67822 1 0 0 01:54:08 0
!!!!!!!!! show commands on the reflector:
RP/0/RSP0/CPU0:9006-1-LAB#show bgp vpnv4 flowspec summary
Thu Jan 29 19:30:19.964 UTC
BGP router identifier 10.1.1.20, local AS number 200
BGP generic scan interval 60 secs
Non-stop routing is enabled
BGP table state: Active
Table ID: 0x0 RD version: 0
BGP main routing table version 1
BGP NSR Initial initsync version 1 (Reached)
BGP NSR/ISSU Sync-Group versions 0/0
BGP scan interval 60 secs
BGP is operating in STANDALONE mode.
Process RcvTblVer bRIB/RIB LabelVer ImportVer SendTblVer StandbyVer
Speaker 1 1 1 1 1 0
Neighbor Spk AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down St/PfxRcd
10.1.1.3 0 200 133928 15649260 1 0 0 01:55:13 0
10.1.1.4 0 200 108611 14313510 1 0 0 01:55:13 0
!!!!!!!!!! show commands on the controller:
RP/0/RSP0/CPU0:9006-4-LAB#show bgp vpnv4 flowspec summary
BGP router identifier 10.1.1.4, local AS number 200
BGP generic scan interval 60 secs
Non-stop routing is enabled
BGP table state: Active
Table ID: 0x0 RD version: 0
BGP main routing table version 1
BGP NSR Initial initsync version 1 (Reached)
BGP NSR/ISSU Sync-Group versions 0/0
BGP scan interval 60 secs
BGP is operating in STANDALONE mode.
Process RcvTblVer bRIB/RIB LabelVer ImportVer SendTblVer StandbyVer
Speaker 1 1 1 1 1 0
Neighbor Spk AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down St/PfxRcd
10.1.1.20 0 200 14349512 112864 1 0 0 01:56:31 0
10.1.1.21 0 200 7991764 131883 1 0 0 01:54:31 0
RP/0/RSP0/CPU0:9006-4-LAB#show bgp vpnv4 flowspec
<no output>
RP/0/RSP0/CPU0:9006-4-LAB#show bgp vpnv4 flowspec advertised
<no output>
Thanks for the help guys, keep it coming!
b
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I will give it a try this week-end in my lab but I thought we needed also a statement in the VPNV4 VRF address-family.
Something more or less like:
router bgp 100
address-family vpnv4 flowspec
!
address-family vpnv6 flowspec
!
neighbor 1.1.1.1
remote-as 100
address-family vpnv4 flowspec
!
address-family vpnv6 flowspec
!
!
vrf foo
address-family ipv4 flowspec
!
address-family ipv6 flowspec
!
neighbor 10.10.10.10
remote-as 100
address-family ipv4 flowspec
!
address-family ipv6 flowspec
!
I'll do my best to get two boxes peering during the WE and give it a try myself.
Cheers,
N.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Nicolas,
Thanks for the feedback, I appreciate it. Looks like what was missing was the enabling of the ipv4 flowspec address-family under the actual vrf. I had the vpnv4 flowspec address-family enabled but that wasn't correct.
So the working config is all of what was pasted above, and the following:
!!!!!!!! on controller
vrf BLA01
address-family ipv4 flowspec
export route-target
666:999
!!!!!!!! on clients
vrf BLA01
address-family ipv4 flowspec
import route-target
666:999
I knew it was something simple that I was missing. I just wish there was some additional documentation that made this a little less painful. But it's all working now. Thanks again for all the help guys!
b
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Good job :)
We will produce some whitepapers in the next coming weeks (well, I've been promising them for a while, so it's time to re-prioritize this task) to address this lack of proper documentation.
Glad you found the missing config and that it works now.
Cheers,
N.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Actually on the open-source part, ExaBGP should work as a flowspec enabled speaker (only on control-plane part, ExaBGP would not interact with dataplane since it's a pure control-plane technology).
Given ExaBGP flexibility it would not be that hard to plug into an already existing opensource Netflow technology to add the react part, given you can already detect with Netflow.
So basically we need a Netflow technology (like flowd or flow-tools to stay in open-source field), some customization and you can plug into ExaBGP to react when conditions are met.
BR/
AC
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
ExaBGP is indeed a good controller.
For the rest, I've seen this: https://github.com/FastVPSEestiOu/fastnetmon
(but didn't try it yet).
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello Xander
and thanks for a very good introduction for FlowSpec. I have questions regarding the resources needed to implement the flow-spec policies. To my understanding flow-spec policies use TCAM resources (so they compete with ACL, QoS policies etc)
Can you point us to a set of commands that we can use to monitor the TCAM consumption for a particular linecard / np in ASR9000?
Thanx
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Vikas,
unfortunately, no simple command to check the allocation today on 9k.
Probably something like:
sh prm server tcam summary all PBR np0 location 0/0/CPU0
(for each NP of your linecard) can give you an hint.
Cheers,
N.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
yeah that is correct Vikas, they will use TCAM resources for the classification and possibly a policer if applied.
Interestingly you asked since I had a section in this years Cisco Live preso I did this morning!
Dont know if they are available for download already, but when, you probably want to pull the cisoc live sandiego id 2904 session for that tcam resource utilization piece.
Here an exerpt, ah that didnt paste well, 2 pics attached then.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi, Xander/Nick:
The "or divert it to a new next-hop address or to leak into a different VRF" part might come in really handy for a customer of ours. So, XRv is not an option at all? Would I be able to see the installed flows even if it doesn't actually leak the traffic into a different VRF?
Thanks,
c.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Carlos,
I'm not sure I understand the question: "Would I be able to see the installed flows even if it doesn't actually leak the traffic into a different VRF?"
XRv can be used as a controller to program an action of redirect-to-IP or redirect-to-VRF that will be received and programed by a physical client (in our case, CRS-3, ASR9000, NCS6000, ASR1000, etc...).
Please help clarify the last question, may be with an example ?
Thanks,
N.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Sure, Nicolas.
I do not have a 9k or CRS to test with. I do have XRv 5.3.1 (5.3.0 doesn't have the flowspec command) and I was wondering if, even though the data plane operation cannot be tested, at least take a look at the control plane for BGP-FS. Is this possible?
Thanks,
c.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Looks like no such luck. This if from the XRv demo releases.
RP/0/0/CPU0:RR5(config)#flowspec local-install interface-all
RP/0/0/CPU0:RR5(config)#commi
Fri Jun 12 09:24:52.305 UTC
% Failed to commit one or more configuration items during a pseudo-atomic operation. All changes made have been reverted. Please issue 'show configuration failed [inheritance]' from this session to view the errors
RP/0/0/CPU0:RR5(config)#show configuration failed
Fri Jun 12 09:24:59.985 UTC
!! SEMANTIC ERRORS: This configuration was rejected by
!! the system due to semantic errors. The individual
!! errors with each failed configuration command can be
!! found below.
flowspec
local-install interface-all
!!% 'FlowSpec' detected the 'warning' condition 'FS MGR': Not supported
!
end
RP/0/0/CPU0:RR5(config)#
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
yeah while the XRv can be used as a "controller" so we can inject the updates for flowspec to "real devices", xrv cannot be used as a client to receive such rules and install them.
XRv doesnt have a tcam and all that hence it wouldnt be a true valid test either.
the commands I gave earlier on the hw entries require a "true" device as that output is pulled from the forwarding asics directly.
cheers
xander
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Carlos,
as clearly explained by Xander, no chance to use the virtual XRv used as a client. It will be possible with the future XRv-9000 but not at FCS (this summer, it will be also only used as a controller or route-reflector).
All you are right about the 5.3.0 lacking all BGP FS features, we fixed this mistake in 5.3.1.
Cheers,
N.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: