- Cisco Community
- Technology and Support
- DevNet
- DevNet Services
- Services Discussions
- Re: Why is CVRF updating its Known Affected ProductIDs freqently?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Why is CVRF updating its Known Affected ProductIDs freqently?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2023 08:28 PM
Hi Cisco PSIRT Team,
About Us: We are a team working on Vulnerability Assessment of Cisco devices.
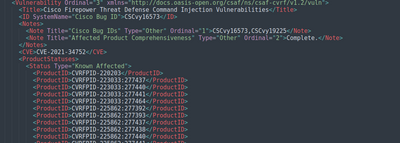
Problem Statement: We completely rely on CVRF for vulnerable versions. Our way of extracting affected version includes collecting Known Affected ProductIDs for a CVE (refer to Image below).
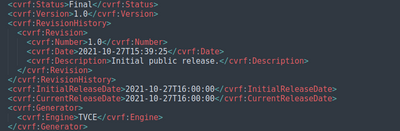
The problem here is, this "ProductIDs" are updating very frequently (like some time day-by-day) without mentioning the reason for update in <cvrf:revision> or anywhere (refer image below).
This frequent updates are killing our time and productivity because of reflecting those update in our vulnerability detection rules.
So, could anyone from "cisco psirt" team answer the below questions?
- Why is cisco updating PIDs without information in revision?
- On what situations cisco is updating PIDs?
- Do we need to consider this as major changes that needs to be reflected in vulnerability rules?
Thanks in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2023 12:14 PM - edited 02-16-2023 12:20 PM
Thank you for notifying us of the issue. Some automated updates as new releases are available for products can result in changes to the CVRF output. We understand that this can be frustrating and we apologize for any inconvenience this is causing. We are currently investigating the reasons behind these changes and exploring ways to minimize any future disruption. We will keep you informed of any progress and our plan of action as soon as possible.
I understand that's a pretty generic response, but in short, there's a lot of complexity behind the scenes and we'll need to spend some time to arrive at the best solution. We'll update this thread as soon as we can.
Wade Williams
Cisco PSIRT Development
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2023 02:51 AM
Hi Williams,
Thanks for the reply, I and my team will be waiting for the updates.
Also, I forgot to raise one more point above.
Scenario: Let's assume a new CVE published in cisco security advisory, and in PID's of CVRF given '16.12.5' IOS-XE Software version as vulnerable. In the very next day or after some days the PID's in CVRF got updated without information in <cvrf:revision>, now the version '16.12.5' is missing in those PID's.
Ques1: From the above case, Can we consider '16.12.5' as vulnerable all the time for the given CVE?
Ques2: If yes, Can you please provide the reason for CVRF removing that version from affected list? In this case if we update our vulnerability detection content on regular basis with CVRF, then we'll be producing "False Negative" content.
Ques3: If no, Why security advisories are releasing with "False Positive" cases in vulnerable versions? Is there any other way to get accurate vulnerable version list for CVEs?
Sorry, If I have asked too many question in a single post :(. But this information will be useful for keeping Cisco device secure against latest vulnerabilities. I hope I`ve made my points clear.
Thank you
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide