- Cisco Community
- Technology and Support
- Small Business Support Community
- Routers - Small Business
- Site to Site VPN between RV340 & RV345 - need help setting up
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2019 12:46 AM - edited 07-11-2019 02:19 AM
Hello,
I have an issue i can't work it out on my own (i'm not a big expert) despite the many hours I spent trying things and reading articles and howtos...
Situation:
Router A, an RV340, using PPPoE Internet access and non-dynamic (fixed) IP granted by ISP. LAN behind it uses 10.10.100.0/24
Router B, an RV345, using PPPoE Internet access and dynamic IP granted by ISP. LAN behind it uses 10.10.200.0/24
Both routers were upgraded to 1.0.03.15, first thing as they were delivered. All config is done on this version.
Also, both routers have a DDNS name registered & updated regularly.
Target:
I want to be able to access resources from both networks via a site-to-site VPN, and Internet to be accessed via each location's ISP link. I do not want to route all traffic through one of the routers - i just need to make sure 10.10.100.x clients can access any 10.10.200.x devices and the other way around... (need to centralize some network control features and stop moving around equipment when i need it).
Problem:
The VPN does not come up, at all.
Setup:
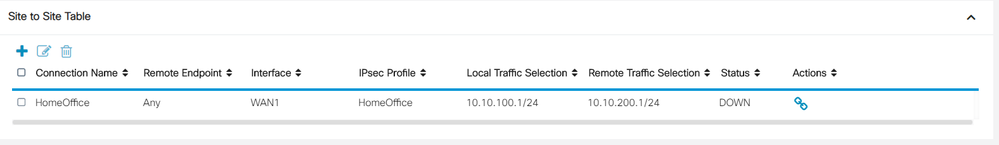
Router A (RV340)
Connection Name: HomeOffice
IPsec Profile: HomeOffice
Interface: WAN1
Remote Endpoint: FQDN / locationB.ddns.net
Pre-shared Key: test123 <- will set something more secure once I get this to work
Local Group Setup
Local Identifier Type: Local WAN IP
Local Identifier: <non-dynamic WAN IP provided by ISP>
Local IP Type: Subnet
IP Address: 10.10.100.1
Subnet Mask: 255.255.255.0
Remote Group Setup
Remote Identifier Type: Remote FQDN
Remote Identifier: locationB.ddns.net
Remote IP Type: Subnet
IP Address: 10.10.200.1
Subnet Mask: 255.255.255.0
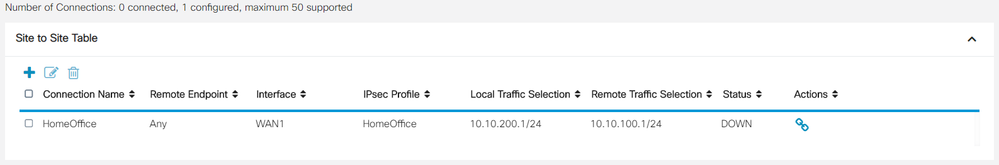
Router B (RV345)
Connection Name: HomeOffice
IPsec Profile: HomeOffice
Interface: WAN1
Remote Endpoint: FQDN / locationA.ddns.net
Pre-shared Key: test123 <- will set something more secure once I get this to work
Local Group Setup
Local Identifier Type: Local WAN IP
Local Identifier: <dynamic WAN IP currently assigned by ISP>
Local IP Type: Subnet
IP Address: 10.10.200.1
Subnet Mask: 255.255.255.0
Remote Group Setup
Remote Identifier Type: Remote FQDN
Remote Identifier: locationA.ddns.net
Remote IP Type: Subnet
IP Address: 10.10.100.1
Subnet Mask: 255.255.255.0
No other settings and features are activated (from Advanced or Failover tabs).
IPSec profile:
By the tech article Configure a Site-to-Site Virtual Private Network (VPN) Connection on an RV340 or RV345 Router it should be good, yet the tunnel never comes up
Router A:
Router B:
Logs (sanitized):
Router A:
2019-07-11T09:37:10+02:00 <info>charon: 07[IKE] IKE_SA s2s_HomeOffice[3125] state change: CONNECTING => DESTROYING
2019-07-11T09:37:10+02:00 <info>charon: 07[IKE] received AUTHENTICATION_FAILED error notify
2019-07-11T09:37:10+02:00 <info>charon: 07[ENC] parsed INFORMATIONAL_V1 request 2442253721 [ HASH N(AUTH_FAILED) ]
2019-07-11T09:37:10+02:00 <info>charon: 07[NET] received packet: from IP_B[500] to IP_A[500] (84 bytes)
2019-07-11T09:37:10+02:00 <info>charon: 12[NET] sending packet: from IP_A[500] to IP_B[500] (92 bytes)
2019-07-11T09:37:10+02:00 <info>charon: 12[ENC] generating ID_PROT request 0 [ ID HASH N(INITIAL_CONTACT) ]
2019-07-11T09:37:10+02:00 <info>charon: 12[IKE] MAIN_MODE task
2019-07-11T09:37:10+02:00 <info>charon: 12[IKE] ISAKMP_VENDOR task
2019-07-11T09:37:10+02:00 <info>charon: 12[IKE] reinitiating already active tasks
2019-07-11T09:37:10+02:00 <info>charon: 12[IKE] Searching for PSK with :my_id,me,other_id,other: 'IP_A'[IP_A] - 'locationB.ddns.net'[IP_B]
2019-07-11T09:37:10+02:00 <info>charon: 12[ENC] parsed ID_PROT response 0 [ KE No NAT-D NAT-D ]
2019-07-11T09:37:10+02:00 <info>charon: 12[NET] received packet: from IP_B[500] to IP_A[500] (236 bytes)
2019-07-11T09:37:10+02:00 <info>charon: 14[NET] sending packet: from IP_A[500] to IP_B[500] (236 bytes)
2019-07-11T09:37:10+02:00 <info>charon: 14[ENC] generating ID_PROT request 0 [ KE No NAT-D NAT-D ]
2019-07-11T09:37:10+02:00 <info>charon: 14[IKE] MAIN_MODE task
2019-07-11T09:37:10+02:00 <info>charon: 14[IKE] ISAKMP_VENDOR task
2019-07-11T09:37:10+02:00 <info>charon: 14[IKE] reinitiating already active tasks
2019-07-11T09:37:10+02:00 <info>charon: 14[IKE] received NAT-T (RFC 3947) vendor ID
2019-07-11T09:37:10+02:00 <info>charon: 14[IKE] received FRAGMENTATION vendor ID
2019-07-11T09:37:10+02:00 <info>charon: 14[IKE] received Cisco Unity vendor ID
2019-07-11T09:37:10+02:00 <info>charon: 14[IKE] received DPD vendor ID
2019-07-11T09:37:10+02:00 <info>charon: 14[IKE] received XAuth vendor ID
2019-07-11T09:37:10+02:00 <info>charon: 14[ENC] parsed ID_PROT response 0 [ SA V V V V V ]
2019-07-11T09:37:10+02:00 <info>charon: 14[NET] received packet: from IP_B[500] to IP_A[500] (176 bytes)
2019-07-11T09:37:10+02:00 <info>charon: 08[NET] sending packet: from IP_A[500] to IP_B[500] (196 bytes)
2019-07-11T09:37:10+02:00 <info>charon: 08[ENC] generating ID_PROT request 0 [ SA V V V V V V ]
2019-07-11T09:37:10+02:00 <info>charon: 08[IKE] IKE_SA s2s_HomeOffice[3125] state change: CREATED => CONNECTING
2019-07-11T09:37:10+02:00 <info>charon: Last message '08[IKE] initiating M' repeated 1 times, supressed by syslog-ng on RV340Apt
2019-07-11T09:37:10+02:00 <info>charon: 08[IKE] initiating Main Mode IKE_SA s2s_HomeOffice[3125] to IP_B
2019-07-11T09:37:10+02:00 <info>charon: 08[IKE] sending draft-ietf-ipsec-nat-t-ike-02\n vendor ID
2019-07-11T09:37:10+02:00 <info>charon: 08[IKE] sending NAT-T (RFC 3947) vendor ID
2019-07-11T09:37:10+02:00 <info>charon: 08[IKE] sending FRAGMENTATION vendor ID
2019-07-11T09:37:10+02:00 <info>charon: 08[IKE] sending Cisco Unity vendor ID
2019-07-11T09:37:10+02:00 <info>charon: 08[IKE] sending DPD vendor ID
2019-07-11T09:37:10+02:00 <info>charon: 08[IKE] sending XAuth vendor ID
2019-07-11T09:37:10+02:00 <info>charon: 08[IKE] activating ISAKMP_NATD task
2019-07-11T09:37:10+02:00 <info>charon: 08[IKE] activating ISAKMP_CERT_POST task
2019-07-11T09:37:10+02:00 <info>charon: 08[IKE] activating MAIN_MODE task
2019-07-11T09:37:10+02:00 <info>charon: 08[IKE] activating ISAKMP_CERT_PRE task
2019-07-11T09:37:10+02:00 <info>charon: 08[IKE] activating ISAKMP_VENDOR task
2019-07-11T09:37:10+02:00 <info>charon: 08[IKE] activating new tasks
2019-07-11T09:37:10+02:00 <info>charon: 08[IKE] queueing QUICK_MODE task
2019-07-11T09:37:10+02:00 <info>charon: 08[IKE] queueing ISAKMP_NATD task
2019-07-11T09:37:10+02:00 <info>charon: 08[IKE] queueing ISAKMP_CERT_POST task
2019-07-11T09:37:10+02:00 <info>charon: 08[IKE] queueing MAIN_MODE task
2019-07-11T09:37:10+02:00 <info>charon: 08[IKE] queueing ISAKMP_CERT_PRE task
2019-07-11T09:37:10+02:00 <info>charon: 08[IKE] queueing ISAKMP_VENDOR task
2019-07-11T09:37:10+02:00 <info>charon: 10[CFG] received stroke: initiate 's2s_HomeOffice-1'
2019-07-11T09:37:10+02:00 <notice>VPN-cfg: Bringing UP tunnel s2s_HomeOffice ...
2019-07-11T09:37:10+02:00 <notice>VPN-RPC: Executing RPC for connection HomeOffice to bring up
Router B:
2019-07-11T09:43:57+02:00 <info>charon: 07[IKE] IKE_SA s2s_HomeOffice[1401] state change: DELETING => DESTROYING
2019-07-11T09:43:57+02:00 <info>charon: 07[NET] sending packet: from IP_B[500] to IP_A[500] (84 bytes)
2019-07-11T09:43:57+02:00 <info>charon: 07[ENC] generating INFORMATIONAL_V1 request 2893026995 [ HASH D ]
2019-07-11T09:43:57+02:00 <info>charon: 07[IKE] IKE_SA s2s_HomeOffice[1401] state change: CONNECTING => DELETING
2019-07-11T09:43:57+02:00 <info>charon: 07[IKE] sending DELETE for IKE_SA s2s_HomeOffice[1401]
2019-07-11T09:43:57+02:00 <info>charon: Last message '07[IKE] deleting IKE' repeated 1 times, supressed by syslog-ng on RV345Vila
2019-07-11T09:43:57+02:00 <info>charon: 07[IKE] deleting IKE_SA s2s_HomeOffice[1401] between IP_B[IP_B]...IP_A[%any]
2019-07-11T09:43:57+02:00 <info>charon: 07[IKE] activating ISAKMP_DELETE task
2019-07-11T09:43:57+02:00 <info>charon: 07[IKE] activating new tasks
2019-07-11T09:43:57+02:00 <info>charon: 07[IKE] queueing ISAKMP_DELETE task
2019-07-11T09:43:57+02:00 <info>charon: 07[IKE] IDir 'IP_A' does not match to 'locationA.ddns.net'
2019-07-11T09:43:57+02:00 <info>charon: 07[ENC] parsed ID_PROT response 0 [ ID HASH ]
2019-07-11T09:43:57+02:00 <info>charon: 07[NET] received packet: from IP_A[500] to IP_B[500] (68 bytes)
2019-07-11T09:43:57+02:00 <info>charon: 05[NET] sending packet: from IP_B[500] to IP_A[500] (92 bytes)
2019-07-11T09:43:57+02:00 <info>charon: 05[ENC] generating ID_PROT request 0 [ ID HASH N(INITIAL_CONTACT) ]
2019-07-11T09:43:57+02:00 <info>charon: 05[IKE] MAIN_MODE task
2019-07-11T09:43:57+02:00 <info>charon: 05[IKE] ISAKMP_VENDOR task
2019-07-11T09:43:57+02:00 <info>charon: 05[IKE] reinitiating already active tasks
2019-07-11T09:43:57+02:00 <info>charon: 05[IKE] Searching for PSK with :my_id,me,other_id,other: 'IP_B'[IP_B] - 'locationA.ddns.net'[IP_A]
2019-07-11T09:43:57+02:00 <info>charon: 05[ENC] parsed ID_PROT response 0 [ KE No NAT-D NAT-D ]
2019-07-11T09:43:57+02:00 <info>charon: 05[NET] received packet: from IP_A[500] to IP_B[500] (236 bytes)
2019-07-11T09:43:57+02:00 <info>charon: 14[NET] sending packet: from IP_B[500] to IP_A[500] (236 bytes)
2019-07-11T09:43:57+02:00 <info>charon: 14[ENC] generating ID_PROT request 0 [ KE No NAT-D NAT-D ]
2019-07-11T09:43:57+02:00 <info>charon: 14[IKE] MAIN_MODE task
2019-07-11T09:43:57+02:00 <info>charon: 14[IKE] ISAKMP_VENDOR task
2019-07-11T09:43:57+02:00 <info>charon: 14[IKE] reinitiating already active tasks
2019-07-11T09:43:57+02:00 <info>charon: 14[IKE] received NAT-T (RFC 3947) vendor ID
2019-07-11T09:43:57+02:00 <info>charon: 14[IKE] received FRAGMENTATION vendor ID
2019-07-11T09:43:57+02:00 <info>charon: 14[IKE] received Cisco Unity vendor ID
2019-07-11T09:43:57+02:00 <info>charon: 14[IKE] received DPD vendor ID
2019-07-11T09:43:57+02:00 <info>charon: 14[IKE] received XAuth vendor ID
2019-07-11T09:43:57+02:00 <info>charon: 14[ENC] parsed ID_PROT response 0 [ SA V V V V V ]
2019-07-11T09:43:57+02:00 <info>charon: 14[NET] received packet: from IP_A[500] to IP_B[500] (176 bytes)
2019-07-11T09:43:57+02:00 <info>charon: 16[NET] sending packet: from IP_B[500] to IP_A[500] (196 bytes)
2019-07-11T09:43:57+02:00 <info>charon: 16[ENC] generating ID_PROT request 0 [ SA V V V V V V ]
2019-07-11T09:43:57+02:00 <info>charon: 16[IKE] IKE_SA s2s_HomeOffice[1401] state change: CREATED => CONNECTING
2019-07-11T09:43:57+02:00 <info>charon: Last message '16[IKE] initiating M' repeated 1 times, supressed by syslog-ng on RV345Vila
2019-07-11T09:43:57+02:00 <info>charon: 16[IKE] initiating Main Mode IKE_SA s2s_HomeOffice[1401] to IP_A
2019-07-11T09:43:57+02:00 <info>charon: 16[IKE] sending draft-ietf-ipsec-nat-t-ike-02\n vendor ID
2019-07-11T09:43:57+02:00 <info>charon: 16[IKE] sending NAT-T (RFC 3947) vendor ID
2019-07-11T09:43:57+02:00 <info>charon: 16[IKE] sending FRAGMENTATION vendor ID
2019-07-11T09:43:57+02:00 <info>charon: 16[IKE] sending Cisco Unity vendor ID
2019-07-11T09:43:57+02:00 <info>charon: 16[IKE] sending DPD vendor ID
2019-07-11T09:43:57+02:00 <info>charon: 16[IKE] sending XAuth vendor ID
2019-07-11T09:43:57+02:00 <info>charon: 16[IKE] activating ISAKMP_NATD task
2019-07-11T09:43:57+02:00 <info>charon: 16[IKE] activating ISAKMP_CERT_POST task
2019-07-11T09:43:57+02:00 <info>charon: 16[IKE] activating MAIN_MODE task
2019-07-11T09:43:57+02:00 <info>charon: 16[IKE] activating ISAKMP_CERT_PRE task
2019-07-11T09:43:57+02:00 <info>charon: 16[IKE] activating ISAKMP_VENDOR task
2019-07-11T09:43:57+02:00 <info>charon: 16[IKE] activating new tasks
2019-07-11T09:43:57+02:00 <info>charon: 16[IKE] queueing QUICK_MODE task
2019-07-11T09:43:57+02:00 <info>charon: 16[IKE] queueing ISAKMP_NATD task
2019-07-11T09:43:57+02:00 <info>charon: 16[IKE] queueing ISAKMP_CERT_POST task
2019-07-11T09:43:57+02:00 <info>charon: 16[IKE] queueing MAIN_MODE task
2019-07-11T09:43:57+02:00 <info>charon: 16[IKE] queueing ISAKMP_CERT_PRE task
2019-07-11T09:43:57+02:00 <info>charon: 16[IKE] queueing ISAKMP_VENDOR task
2019-07-11T09:43:57+02:00 <info>charon: 06[CFG] received stroke: initiate 's2s_HomeOffice-1'
2019-07-11T09:43:57+02:00 <notice>VPN-cfg: Bringing UP tunnel s2s_HomeOffice ...
2019-07-11T09:43:57+02:00 <notice>VPN-RPC: Executing RPC for connection HomeOffice to bring up
What am i doing wrong please?
Solved! Go to Solution.
- Labels:
-
RV340
-
Small Business Routers
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2019 09:49 AM - edited 08-01-2019 09:51 AM
Hi,
Sorry for the delay, i have finally set it up so that it reconnects when the Router_B changes IP or is rebooted.
Final setup is (for others to use it as an example):
Router_A:
Connection Name: HomeOffice
IPsec Profile: HomeOffice
Interface: WAN1
Remote Endpoint: FQDN / Router_B.ddns.net
Pre-shared Key: <secure key>
Local Group Setup
Local Identifier Type: Local WAN IP
Local Identifier: Router_A_IP
Local IP Type: Subnet
IP Address: 10.10.100.1
Subnet Mask: 255.255.255.0
Remote Group Setup
Remote Identifier Type: Remote FQDN
Remote Identifier: Router_B.ddns.net
Remote IP Type: Subnet
IP Address: 10.10.200.1
Subnet Mask: 255.255.255.0
Router_B:
Connection Name: HomeOffice
IPsec Profile: HomeOffice
Interface: WAN1
Remote Endpoint: Static IP / Router_A_IP
Pre-shared Key: <secure key>
Local Group Setup
Local Identifier Type: Local FQDN
Local Identifier: Router_B.ddns.net
Local IP Type: Subnet
IP Address: 10.10.200.1
Subnet Mask: 255.255.255.0
Remote Group Setup
Remote Identifier Type: Remote WAN IP
Remote Identifier: Router_A_IP
Remote IP Type: Subnet
IP Address: 10.10.100.1
Subnet Mask: 255.255.255.0
This works just fine...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2019 04:59 AM - edited 07-11-2019 05:01 AM
From Router A log:
2019-07-11T09:37:10+02:00 <info>charon: 07[IKE] IKE_SA s2s_HomeOffice[3125] state change: CONNECTING => DESTROYING
2019-07-11T09:37:10+02:00 <info>charon: 07[IKE] received AUTHENTICATION_FAILED error notify
2019-07-11T09:37:10+02:00 <info>charon: 07[ENC] parsed INFORMATIONAL_V1 request 2442253721 [ HASH N(AUTH_FAILED) ]
2019-07-11T09:37:10+02:00 <info>charon: 07[NET] received packet: from IP_B[500] to IP_A[500] (84 bytes)
2019-07-11T09:37:10+02:00 <info>charon: 12[NET] sending packet: from IP_A[500] to IP_B[500] (92 bytes)
2019-07-11T09:37:10+02:00 <info>charon: 12[ENC] generating ID_PROT request 0 [ ID HASH N(INITIAL_CONTACT) ]
2019-07-11T09:37:10+02:00 <info>charon: 12[IKE] MAIN_MODE task
From Router B log:
2019-07-11T09:43:57+02:00 <info>charon: 07[IKE] deleting IKE_SA s2s_HomeOffice[1401] between IP_B[IP_B]...IP_A[%any]
2019-07-11T09:43:57+02:00 <info>charon: 07[IKE] activating ISAKMP_DELETE task
2019-07-11T09:43:57+02:00 <info>charon: 07[IKE] activating new tasks
2019-07-11T09:43:57+02:00 <info>charon: 07[IKE] queueing ISAKMP_DELETE task
2019-07-11T09:43:57+02:00 <info>charon: 07[IKE] IDir 'IP_A' does not match to 'locationA.ddns.net'
2019-07-11T09:43:57+02:00 <info>charon: 07[ENC] parsed ID_PROT response 0 [ ID HASH ]
2019-07-11T09:43:57+02:00 <info>charon: 07[NET] received packet: from IP_A[500] to IP_B[500] (68 bytes)
2019-07-11T09:43:57+02:00 <info>charon: 05[NET] sending packet: from IP_B[500] to IP_A[500] (92 bytes)
2019-07-11T09:43:57+02:00 <info>charon: 05[ENC] generating ID_PROT request 0 [ ID HASH N(INITIAL_CONTACT) ]
In short Router B rejects the authentication.
Looks like there is something wrong with the ddns.
When Router B compares the incomming IP with the IP from the ddns it does not match.
Check what might be wrong with the DDNS.
But also, I would suggest trying with static ip first. (instead of FQDN).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2019 01:57 PM
Hi,
I have managed to get it UP by doing the tunnel on static IP on both sides. This proves comm is fine on IP to IP basis...
But I have dynamic IP on the locationB and it'll change without me being actually informed, or maybe able to connect to fix things... I'd like to avoid re-configuring the VPN every other day...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-30-2019 11:27 PM
If not and we know static IP works, we can only assume that for some reason the DDNS did not update properly or is somehow cached.
Check the DNS the router is using. How long does it cache records. What updates the DDNS? and how often?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2019 09:49 AM - edited 08-01-2019 09:51 AM
Hi,
Sorry for the delay, i have finally set it up so that it reconnects when the Router_B changes IP or is rebooted.
Final setup is (for others to use it as an example):
Router_A:
Connection Name: HomeOffice
IPsec Profile: HomeOffice
Interface: WAN1
Remote Endpoint: FQDN / Router_B.ddns.net
Pre-shared Key: <secure key>
Local Group Setup
Local Identifier Type: Local WAN IP
Local Identifier: Router_A_IP
Local IP Type: Subnet
IP Address: 10.10.100.1
Subnet Mask: 255.255.255.0
Remote Group Setup
Remote Identifier Type: Remote FQDN
Remote Identifier: Router_B.ddns.net
Remote IP Type: Subnet
IP Address: 10.10.200.1
Subnet Mask: 255.255.255.0
Router_B:
Connection Name: HomeOffice
IPsec Profile: HomeOffice
Interface: WAN1
Remote Endpoint: Static IP / Router_A_IP
Pre-shared Key: <secure key>
Local Group Setup
Local Identifier Type: Local FQDN
Local Identifier: Router_B.ddns.net
Local IP Type: Subnet
IP Address: 10.10.200.1
Subnet Mask: 255.255.255.0
Remote Group Setup
Remote Identifier Type: Remote WAN IP
Remote Identifier: Router_A_IP
Remote IP Type: Subnet
IP Address: 10.10.100.1
Subnet Mask: 255.255.255.0
This works just fine...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2019 10:17 AM
Hi! It seems that you are doing almost the exact thing I want to do, though both my routers are expected to be RV345 models. Basically, we just got a vacation cottage, so I'd like to put a router there and let my devices at the cottage access the devices at my home as if they were local to one another. So, my Roku at the cottage could access my mail server, security cameras, Plex, PlayOn, HDHomeRun, etc ... just as if these were at the cottage as well.
Could you confirm that this fits the concept of what you've done? Also, does Cisco impose a licensing fee for this basic use? I have no interest in user remote-to-VPN, just this site-to-site.
Thanks!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide