- Cisco Community
- Technology and Support
- Networking
- Switching
- yes definitely let us know if
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco 6506-E: Stateful Switchover (SSO) is not working in Core Switches as expected
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-27-2015 09:26 PM - edited 03-08-2019 01:57 AM
Hi,
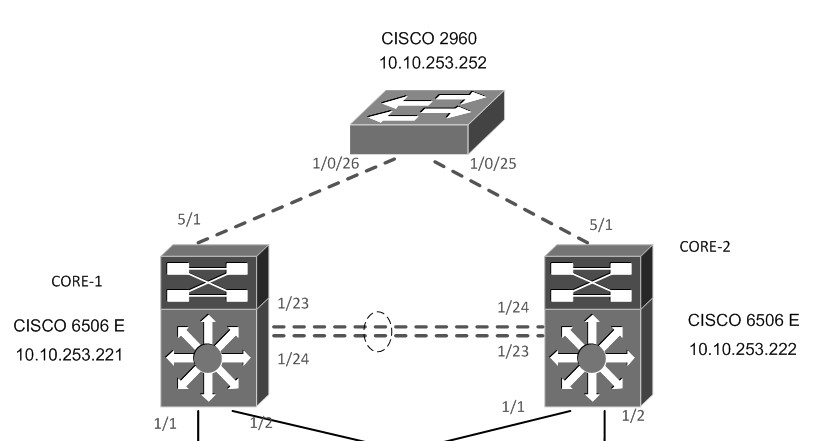
I would like to set-up a VSS on our clients 6506-E switches. But first things first, I checked if SSO is already working. However, upon checking, it seems that SSO is not working and found some observations based on the current status of our client 6506-E switches. Appreciate your advise on this.
- Stateful Switchover (SSO) is not working in Core Switches as expected.
- Communication status is in “Down” state
- Peer Information is not available. (PEER state is disabled)
Core-1:
SW-CORE-1#show version
Cisco IOS Software, s2t54 Software (s2t54-IPSERVICESK9-M), Version 15.0(1)SY2, RELEASE SOFTWARE (fc4)
System image file is "bootdisk:s2t54-ipservicesk9-mz.SPA.150-1.SY2.bin"
SW-CORE-1#show redundancy
Redundant System Information :
------------------------------
Available system uptime = 3 weeks, 5 days, 3 hours, 56 minutes
Switchovers system experienced = 0
Standby failures = 0
Last switchover reason = none
Hardware Mode = Simplex
Configured Redundancy Mode = sso
Operating Redundancy Mode = sso
Maintenance Mode = Disabled
Communications = Down Reason: Simplex mode
Current Processor Information :
-------------------------------
Active Location = slot 5
Current Software state = ACTIVE
Uptime in current state = 3 weeks, 5 days, 3 hours, 56 minutes
Image Version = Cisco IOS Software, s2t54 Software (s2t54-IPSERVICESK9-M), Version 15.0(1)SY2, RELEASE SOFTWARE (fc4)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2012 by Cisco Systems, Inc.
Compiled Tue 10-Jul-12 13:35 by prod_rel_team
BOOT =
Configuration register = 0x2102
Peer (slot: unavailable) information is not available because it is in 'DISABLED' state
redundancy
main-cpu
auto-sync running-config
mode sso
Core2:
SW-CORE-2#show version
Cisco IOS Software, s2t54 Software (s2t54-IPSERVICESK9-M), Version 15.0(1)SY2, RELEASE SOFTWARE (fc4)
System image file is "bootdisk:s2t54-ipservicesk9-mz.SPA.150-1.SY2.bin"
SW-CORE-2#show redundancy
Redundant System Information :
------------------------------
Available system uptime = 3 weeks, 5 days, 3 hours, 59 minutes
Switchovers system experienced = 0
Standby failures = 0
Last switchover reason = none
Hardware Mode = Simplex
Configured Redundancy Mode = sso
Operating Redundancy Mode = sso
Maintenance Mode = Disabled
Communications = Down Reason: Simplex mode
Current Processor Information :
-------------------------------
Active Location = slot 5
Current Software state = ACTIVE
Uptime in current state = 3 weeks, 5 days, 3 hours, 59 minutes
Image Version = Cisco IOS Software, s2t54 Software (s2t54-IPSERVICESK9-M), Version 15.0(1)SY2, RELEASE SOFTWARE (fc4)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2012 by Cisco Systems, Inc.
Compiled Tue 10-Jul-12 13:35 by prod_rel_team
BOOT =
Configuration register = 0x2102
Peer (slot: unavailable) information is not available because it is in 'DISABLED' state
redundancy
main-cpu
auto-sync running-config
mode sso
Module details:
SW-CORE-1#show module
Mod Ports Card Type Model Serial No.
--- ----- -------------------------------------- ------------------ -----------
1 24 CEF720 24 port 1000mb SFP WS-X6724-SFP SAL160639E1
2 48 CEF720 48 port 10/100/1000mb Ethernet WS-X6848-GE-TX SAL1639NESE
5 5 Supervisor Engine 2T 10GE w/ CTS (Acti VS-SUP2T-10G SAL1638N0FC
Mod MAC addresses Hw Fw Sw Status
--- ---------------------------------- ------ ------------ ------------ -------
1 c464.1304.8c88 to c464.1304.8c9f 5.1 12.2(18r)S1 15.0(1)SY2 Ok
2 30f7.0d7f.2b38 to 30f7.0d7f.2b67 1.0 12.2(18r)S1 15.0(1)SY2 Ok
5 e05f.b911.2e7f to e05f.b911.2e86 1.3 12.2(50r)SYS 15.0(1)SY2 Ok
Mod Sub-Module Model Serial Hw Status
---- --------------------------- ------------------ ----------- ------- -------
1 Centralized Forwarding Card WS-F6700-CFC SAL16095NK8 4.1 Ok
2 Distributed Forwarding Card WS-F6K-DFC4-A SAL1638NBVJ 1.2 Ok
5 Policy Feature Card 4 VS-F6K-PFC4 SAL1638MUNU 1.2 Ok
5 CPU Daughterboard VS-F6K-MSFC5 SAL1638MV1P 1.4 Ok
Mod Online Diag Status
---- -------------------
1 Pass
2 Pass
5 Pass
SW-CORE-2#show module
Mod Ports Card Type Model Serial No.
--- ----- -------------------------------------- ------------------ -----------
1 24 CEF720 24 port 1000mb SFP WS-X6724-SFP SAL160639EE
2 48 CEF720 48 port 10/100/1000mb Ethernet WS-X6848-GE-TX SAL1637MPMS
5 5 Supervisor Engine 2T 10GE w/ CTS (Acti VS-SUP2T-10G SAL1638N0EQ
Mod MAC addresses Hw Fw Sw Status
--- ---------------------------------- ------ ------------ ------------ -------
1 c464.1304.8cb8 to c464.1304.8ccf 5.1 12.2(18r)S1 15.0(1)SY2 Ok
2 6073.5cd9.8a70 to 6073.5cd9.8a9f 1.0 12.2(18r)S1 15.0(1)SY2 Ok
5 c471.fe7c.ec56 to c471.fe7c.ec5d 1.3 12.2(50r)SYS 15.0(1)SY2 Ok
Mod Sub-Module Model Serial Hw Status
---- --------------------------- ------------------ ----------- ------- -------
1 Centralized Forwarding Card WS-F6700-CFC SAL16095VCA 4.1 Ok
2 Distributed Forwarding Card WS-F6K-DFC4-A SAL1638NBUX 1.2 Ok
5 Policy Feature Card 4 VS-F6K-PFC4 SAL1638N3WY 1.2 Ok
5 CPU Daughterboard VS-F6K-MSFC5 SAL1638N3BG 1.4 Ok
Mod Online Diag Status
---- -------------------
1 Pass
2 Pass
5 Pass
Interface Configuration
Core 1:
interface GigabitEthernet1/23
no ip address
!
interface GigabitEthernet1/24
switchport
switchport trunk allowed vlan 10,20,30,101,102
switchport mode trunk
interface GigabitEthernet5/1
switchport
switchport trunk allowed vlan 10,20,30,101,102
switchport mode trunk
Core 2:
interface GigabitEthernet1/23
no ip address
spanning-tree guard loop
!
interface GigabitEthernet1/24
switchport
spanning-tree guard root
!
interface GigabitEthernet5/1
switchport
switchport trunk allowed vlan 10,20,30,101,102
Additional Questions:
- Is it needed that the 2 6506-E switches are connected via supervisors uplink interfaces (slot 5 on this set-up, fa5/1-3 or tengig5/4-5) for SSO to work, or any interfaces on the modules can be used. Because, based on the curent set-up, they link the 2 6506-E switch using interfaces of module in slot 1 (WS-X6724-SFP).
- What other items I need to check in addition on above details?
TIA
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2015 12:50 AM
Hi you prob have this but just in case have you set the priority on each switch like below and can you post show switch virtual redundancy instead of show switch redundancy as its vss , you should see standby as HOT switchover target
switch virtual domain 100
switch mode virtual
switch 1 priority 200
mac-address use-virtual
also I have a po between my 2 switches set with the virtual link
interface Port-channel66
description VSS Link_to_Switch2
no switchport
no ip address
switch virtual link 1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2015 01:12 AM
Hi Mark thanks for the inputs. Right now no VSS configuration yet is implemented. I just want to make sure that SSO is working first before moving to VSS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2015 02:11 AM
sorry half read that early morns :) I have my sups directly connected to each other by the 10GBs interfaces sup-sup , have you tried that as your in simplex mode so its not forming correctly and your active each side but your cards are matching and so is your ios and the config section looks ok too
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2015 03:00 AM
Thanks for the checking Mark. Nop, haven't tried it yet. I just remote the switch from their site. Once I got to their site, I try to do some connection changes and verify it from there. But right now, what I can do is to check their configs and check what are the possible problems/issues, the reason why their SSO is not working.
One more thing, I checked the running config on the interface portion and the interface configuration on fa1/23 and 1/24 for both switches doesn't make sense at all. What do you think?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2015 03:19 AM
Yes I don't see why there trunked like that , the whole point of the setup of VSS is that they act logically as 1 unit so when you log in you get both switches in config and you can check commands like show module switch 2 etc, I don't think there should be a trunk between them like that if they are to participate in VSS there should only be connections from sup to sup for the SSO and then the VSL link between them as well usually a port-channel
Just for my own setup we have no trunk like that , sups are directly connected to each other and then we also have the VSL port0cahhenl that's in it terms of physical connections between the 65s
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2015 03:38 AM
Thanks a bunch Mark! Yes, agree with the VSS operation. I think I will stick and continue to my plan now and try implement it once I got to their site. Will keep you posted for the results. Thanks for your time!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2015 04:17 AM
yes definitely let us know if you get it working
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


