- Cisco Community
- Technology and Support
- Networking
- Switching
- How can I block two port communication
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How can I block two port communication
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2015 09:34 PM - edited 03-08-2019 03:13 AM
I have Switch 3560 48POE (i forget accurate IOS version, i think is 12.X), i don't known how to complete following task:
Q1) When ANY DEVICE connect Port 1, they can ONLY talk to port 2. And they can't talk to other Port (port 3 - 48).
Q2) Base on Q1, when ANY DEVICE connect Port 48, they can't talk to Port 1, but they can talk to port 2 - 47.
Q3) Base on Q1 and Q2, Port 2 can talk to ALL PORT.
Request:
1) You can't use VLAN and Private VLAN.
I think ACL is not work, because i don't know what IP address(es) and mac address(es) will access port 1 and port 48.
And I use TP-Link L2 Switch is very very easy and simple to complete these task.
But this time I need use 3560.
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2015 10:38 PM
you can use Port ACLs see below extract from
http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst3560/software/release/12-2_52_se/configuration/guide/3560scg/swacl.html#wp1689472
Port ACLs
Port ACLs are ACLs that are applied to Layer 2 interfaces on a switch. Port ACLs are supported only on physical interfaces and not on EtherChannel interfaces and can be applied only on interfaces in the inbound direction. These access lists are supported:
•![]() Standard IP access lists using source addresses
Standard IP access lists using source addresses
•![]() Extended IP access lists using source and destination addresses and optional protocol type information
Extended IP access lists using source and destination addresses and optional protocol type information
•![]() MAC extended access lists using source and destination MAC addresses and optional protocol type information
MAC extended access lists using source and destination MAC addresses and optional protocol type information
The switch examines ACLs associated with all inbound features configured on a given interface and permits or denies packet forwarding based on how the packet matches the entries in the ACL. In this way, ACLs control access to a network or to part of a network. Figure 34-1 is an example of using port ACLs to control access to a network when all workstations are in the same VLAN. ACLs applied at the Layer 2 input would allow Host A to access the Human Resources network, but prevent Host B from accessing the same network. Port ACLs can only be applied to Layer 2 interfaces in the inbound direction.
Figure 34-1 Using ACLs to Control Traffic to a Network
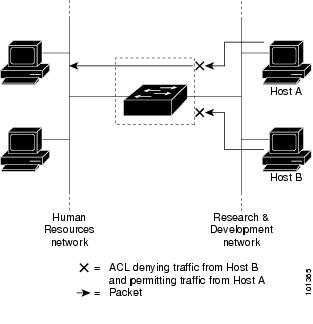
When you apply a port ACL to a trunk port, the ACL filters traffic on all VLANs present on the trunk port. When you apply a port ACL to a port with voice VLAN, the ACL filters traffic on both data and voice VLANs.
With port ACLs, you can filter IP traffic by using IP access lists and non-IP traffic by using MAC addresses. You can filter both IP and non-IP traffic on the same Layer 2 interface by applying both an IP access list and a MAC access list to the interface.

Note ![]() You cannot apply more than one IP access list and one MAC access list to a Layer 2 interface. If an IP access list or MAC access list is already configured on a Layer 2 interface and you apply a new IP access list or MAC access list to the interface, the new ACL replaces the previously configured one.
You cannot apply more than one IP access list and one MAC access list to a Layer 2 interface. If an IP access list or MAC access list is already configured on a Layer 2 interface and you apply a new IP access list or MAC access list to the interface, the new ACL replaces the previously configured one.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2015 11:47 PM
Look into the configuration guide and what is Protected Ports.
Some of the feature functionality should be used for your case:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2015 08:06 AM
Hello,
I think for your requirement , PACL are best as per suggested by Richard because The port ACL (PACL) feature provides the ability to perform access control on specific Layer 2 ports. A Layer 2 port is a physical LAN or trunk port that belongs to a VLAN.
Port ACLs are applied only on the ingress traffic. The port ACL feature is supported only in hardware (port ACLs are not applied to any packets routed in software).
Have a look on the below configuration link..
http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst6500/ios/12-2SY/configuration/guide/sy_swcg/port_acls.html
Hope it Help..
-GI
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

