- Cisco Community
- Technology and Support
- Data Center and Cloud
- Unified Computing System (UCS)
- Unified Computing System Blogs
- AppDynamics on Cisco Container Platform's Kubernetes
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
There has been a few announcements lately regarding Cisco's Container Platform (a.k.a: CCP) and they've all been good. Having integration with AWS allows CCP to deploy Kubernetes clusters on vSphere or EKS from the same control point. But another great integration that's been there for the last few months is the App Dynamics (AppD) Kubernetes support announced earlier this year.
Let's show how we can make this AppD work on top of CCP!
Step 1: Get a CCP Kubernetes cluster up and running
If you have CCP then you are golden, spin up a new cluster and it just works!
If you don't have CCP you can try it out in two easy ways:
- If you have vSphere 6.5 and nodes running in HA mode on a servers with processors at a minimum of IvyBridge then you can download the 90 day trial versions and get them running. The install can be done in under an hour.
- If you don't have an environment, use the Cisco Sandbox! You can spin up a container platform in just a few clicks and have it for several hours. Plenty to get going with!
Step 2: Install AppD Controller Console
We'll be running the controller console onprem. AppD also has a SaaS based offering that is simpler to get going quickly. Let's show how we can install this onPrem.
2.1 Create free trial account
You can create a free trial account at https://www.appdynamics.com/free-trial/ by just signing up.
2.2 Install a virtual machine for the AppD controller
We'll be going small so we'll install a quick virtual machine with Ubuntu 18.04
- 8GB of RAM
- 100GB of hard drive space and
- 2 vCPUs
Be sure your specs are similar because the application checks to make sure there is enough free RAM in the system as well as CPU and disk space. Let's set it up:
sudo apt-get update sudo apt-get upgrade
There are also several dependencies that we are told to install from the installation guide. Let's install those too:
sudo apt-get install libaio1 numactl tzdata
2.3 Download the Enterprise Console
Once there we need to download the controller. We run:
curl https://download.appdynamics.com/download/downloadfilelatest/ | python -m json.tool | less
Looking through this we find the file we want to download:
{
"bit": "64",
"creation_time": "2018-09-26T20:32:49.126787Z",
"description": "Enterprise Console is tool developed by AppDynamics to install, configure and update the AppDynamics Platform.",
"download_path": "https://download.appdynamics.com/download/prox/download-file/enterprise-console/4.5.1.14088/platform-setup-x64-linux-4.5.1.14088.sh",
"extension": "sh",
"file_size": "2470.7",
"filename": "platform-setup-x64-linux-4.5.1.14088.sh",
"filetype": "enterprise-console",
"id": 16081,
"installation_link": "",
"is_beta": false,
"is_fcs": false,
"is_visible": true,
"md5_checksum": "30ed50526b8041371dff517437ca08ab",
"os": "linux",
"post_download_information": "",
"required_controller_version": null,
"s3_path": "download-file/enterprise-console/4.5.1.14088/platform-setup-x64-linux-4.5.1.14088.sh",
"sha256_checksum": "7e0baad40e792e1d41233a7128ae8a939089d4a5af356ec3665610e928907a80",
"title": "Enterprise Console - 64-bit linux (sh)",
"version": "4.5.1.14088"
},
To get this download we can use the curl command to first get our OAUTH token:
curl -X POST -d '{"username": "vbeninco", "password": "MySecretPassword#" , "scopes": ["download"]}' https://identity.msrv.saas.appdynamics.com/v2.0/oauth/token
This will return an obscene string that is too offensive to print here... well actually no, its just a long meaningless string to identify my future requests to the server and authenticate. With this token we can do:
export TOKEN=eyJraWQiOiJmRGxr......
Now to get the bits we use the token and the URL we fetched above:
curl -L -O -H "Authorization: Bearer $TOKEN" https://download.appdynamics.com/download/prox/download-file/enterprise-console/4.5.4.15417/platform-setup-x64-linux-4.5.4.15417.sh
You may want to make sure the size of this file is big enough and not some error web page to ensure you got the right file. With the controller downloaded we can now install it on our server.
2.4 Configure the Installation file and parameters
Once downloaded we can define our variable file to make our install faster. This file we create and call it response.varfile. The contents are:
serverHostName=appd-controller sys.languageId=en disableEULA=true platformAdmin.port=9191 platformAdmin.databasePort=3377 platformAdmin.dataDir=/opt/appdynamics/platform/mysql/data platformAdmin.databasePassword= CIsco.123! platformAdmin.databaseRootPassword= CIsco.123! platformAdmin.adminPassword= CIsco.123! platformAdmin.useHttps$Boolean=false sys.installationDir=/opt/appdynamics/enterpriseconsole
Let's create the directory we specified above so our non-root user can install in this directory:
sudo mkdir /opt/appdynamics sudo chown ubuntu:ubuntu /opt/appdynamics
2.5 Install the Binary
We now install with:
chmod +x ./platform-setup*.sh
./platform-setup*.sh -q -varfile ~/response.varfile
Once the installation finishes we can log into the console using the port we specified (9191) and use the admin password we specified above: CIsco.123!
If the system reboots at any point to restart AppD just use this command:
/opt/appdynamcis/enterpriseconsole/platform-admin/bin/platform-admin.sh start-platform-admin
Step 3: Install the Enterprise Controller and Events Service
Now we want to add the console. You can follow the simple install using the GUI:
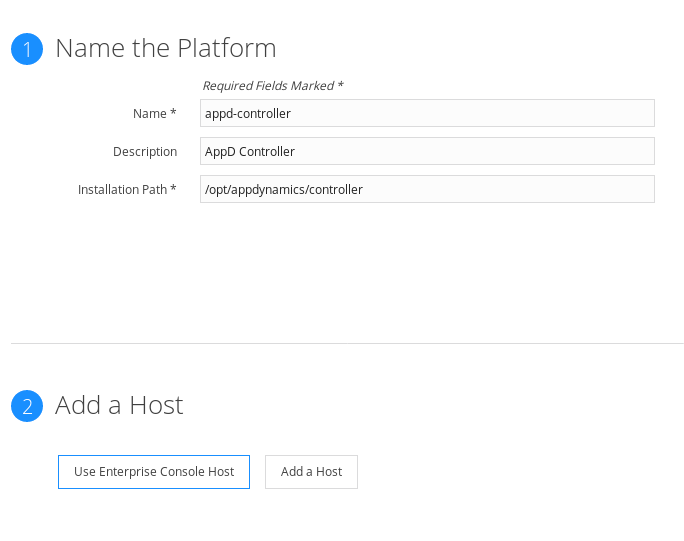
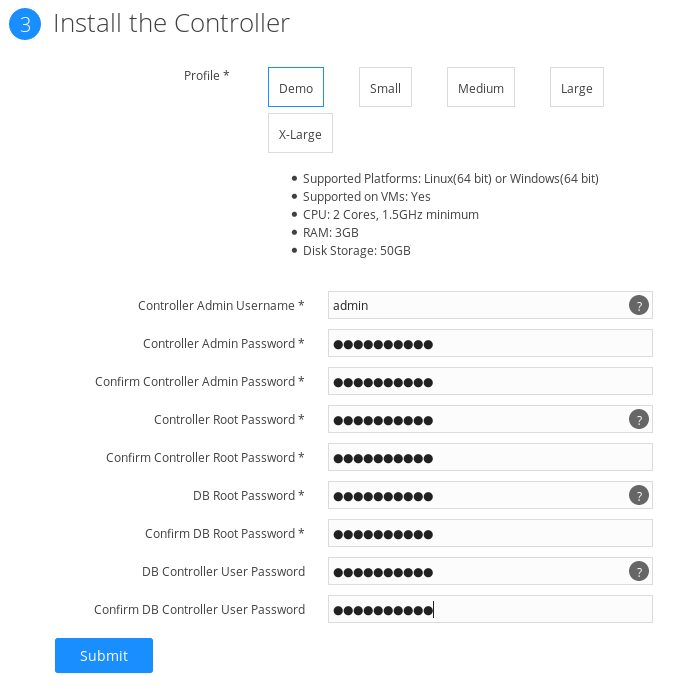
You can use this method and it works pretty well. It will take a while for the machine to install. I found, however that it doesn't give all the error messages that you may need in a demo environment. I instead followed the command line instructions:
cd /opt/appdynamics/enterpriseconsole/platform-admin/ ./platform-admin.sh create-platform --name controller1 --installation-dir /opt/appdynamics/controller ./platform-admin.sh add-hosts --hosts localhost ./platform-admin.sh submit-job --service controller --job install --args controllerPrimaryHost=localhost controllerAdminUsername=admin controllerAdminPassword=CIsco.123 controllerRootUserPassword=CIsco.123! mysqlRootPassword=CIsco.123!
This job took 9 minutes and 18 seconds to install. It failed originally because I didn't have enough RAM on the virtual machine.
You should now be able to log into this service at port :8090 (in my case with admin / CIsco.123 ). Also notice that the controllerAdminPassword should be different than the controllerRootUserPassword.
When complete the Event Service and Controller service should be running.
3.1 License
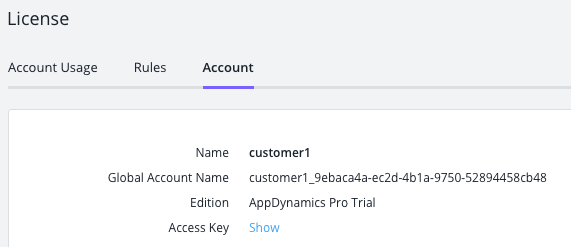
You'll need to obtain a license file from your friendly AppD account team. The license (named license.lic) should be placed in the controller subdirectory. In my case I put it in /opt/appdynamics/controller/controller.
You can then see what you were licensed for by examining the settings / licensing:
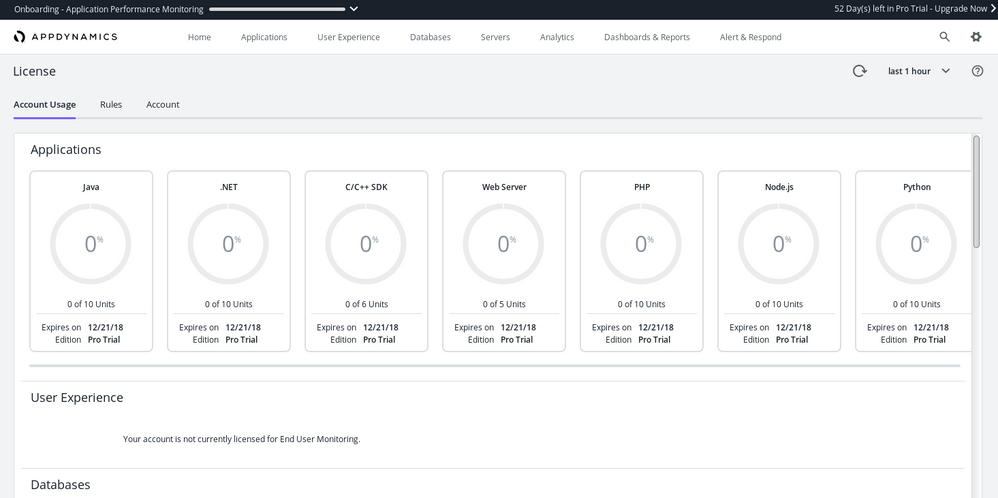
4. AD Capital Kubernetes Monitoring
To show how AppDynamics can monitor Kubernetes we'll install a sample application called AD Capital. To get this you can run:
git clone https://github.com/Appdynamics/AD-Capital-Kube.git
Let's configure several parameters to install it.
4.1 ConfigMap
Here we are presented with several files that we can modify to install the machine agents we need to modify. Let's first modify the env-configmap.yaml
cd AD-Capital-Kube/Kubernetes vi env-configmap.yaml
Here we will change the following values (don't put the + in I just added those to show what needed to be changed).
apiVersion: v1 data: APPD_DIR: /appdynamics + APPD_ES_HOST: 10.93.140.74 APPD_ES_PORT: "9080" APPD_ES_SSL: "false" + APPD_EVENT_ACCOUNT_NAME: customer1_9ebaca4a-ec2d-4b1a-9750-52894458cb48 APPDYNAMICS_AGENT_ACCOUNT_ACCESS_KEY: bdaafad5-2c8a-47d9-92b9-11a88f8b460a APPDYNAMICS_AGENT_ACCOUNT_NAME: customer1 + APPDYNAMICS_AGENT_APPLICATION_NAME: appd-kubernetes + APPDYNAMICS_CONTROLLER_HOST_NAME: 10.93.140.74 APPDYNAMICS_CONTROLLER_PORT: "8090" APPDYNAMICS_CONTROLLER_SSL_ENABLED: "False" APPDYNAMICS_NETVIZ_AGENT_PORT: "3892" RETRY: 10s TIMEOUT: 300s kind: ConfigMap metadata: creationTimestamp: null name: env-map
Notice that the account name and the access key will be gotten from your AppD console in the settings.
The agent application name is just whatever you want to name this application. We also added the IP address of our AppD controller that we installed in the previous steps.
4.2 Secrets
The other change is to add our own secrets. We first need get our name. In my case it is customer1. These values need to be base64 encoded:
echo -n customer1 | base64 Y3VzdG9tZXIx
Next we get the base64 encoded Access Key that we put in the ConfigMap above:
echo -n bdaafad5-2c8a-47d9-92b9-11a88f8b460a | base64 YmRhYWZhZDUtMmM4YS00N2Q5LTkyYjktMTFhODhmOGI0NjBh
Now we put these base64 encoded values into the secret.yaml file in this directory:
apiVersion: v1 kind: Secret metadata: name: mysecret type: Opaque data: accesskey: YmRhYWZhZDUtMmM4YS00N2Q5LTkyYjktMTFhODhmOGI0NjBh accountname: Y3VzdG9tZXIx
4.3 Deploy Application
The application can simply be deployed with:
kubectl create -f . deployment.extensions/adcapitaldb created service/adcapitaldb created deployment.extensions/approval created service/approval created configmap/env-map created pod/load created service/load created deployment.extensions/portal created service/portal created deployment.extensions/processor created service/processor created deployment.extensions/rabbitmq created service/rabbitmq created deployment.extensions/rest created service/rest created secret/mysecret created deployment.extensions/verification created service/verification created
This may take several minutes for the containers to download and for the agents to register in AppD. You can check on the status by running
kubectl get pods -o wide -w
When finished you should be able to see them in the AppD application console
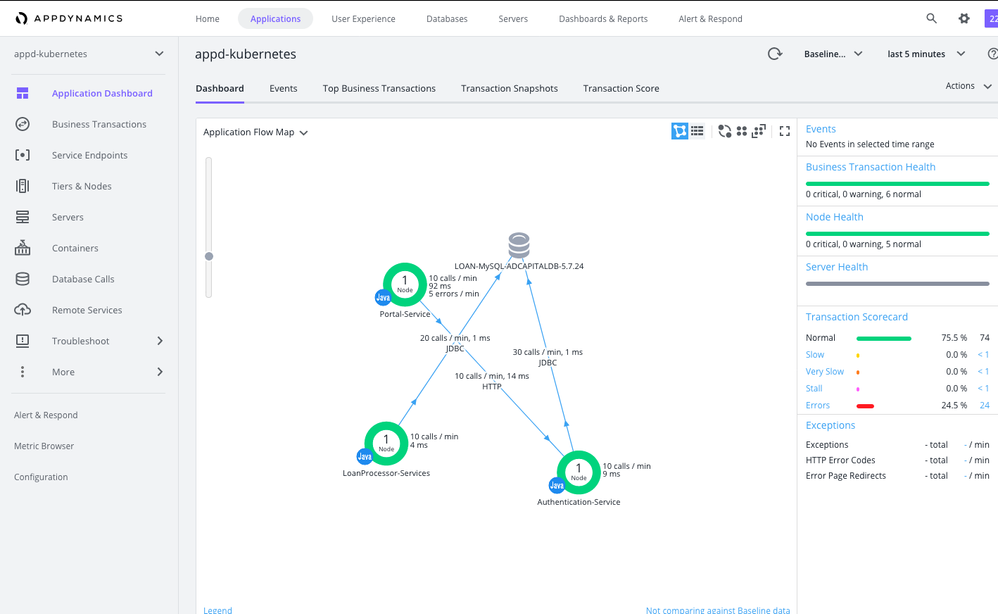
4.4 Deploy Machine Agents
We can also deploy the machine agents on Kubernetes
cd ../KubernetesMachineAgent kubectl create -f monitor-deployment.yaml
A daemon set will be installed on every kubernetes VM to give machine monitoring information like CPU or Memory usage
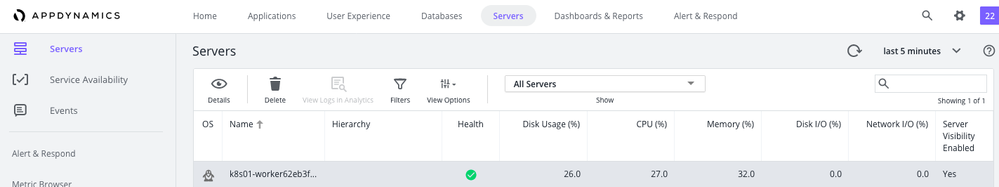
At this point our apps and our Kubernetes cluster is all set up with AppD ready to monitor and get insight into the applications that are running on Cisco Container Platform.
5. Summary
In this blog post we showed how to install AppD and then show a sample application on Kubernetes. We also showed how machine agents can be installed. The Github repository we referenced has more information and ideas you could try to get more visibility into your CCP Kubernetes cluster and the containers running on top of it. We highly recommend reading through that document as the most difficult part of filling out the environment variables and bringing up a Kubernetes cluster has been complete!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: