- Cisco Community
- Technology and Support
- Security
- VPN
- Anyconnect authentication using Microsoft ADFS SAML
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2018 10:31 AM
Hello,
I'm trying to authenticate Anyconnect (or Clientless VPN) using Microsoft ADFS, but I can't get it to work.
I'm especially clueless on how to configure the ADFS side.
I've done this to authenticate an ISE Sponsor portal, it's very easy, ISE provides a nice XML configuration file that I can import into ADFS, but there's nothing like it on the ASA documentation, not even how to do it manually.
Is there anyone who can help me?
Thanks,
Silla Rizzoli
Solved! Go to Solution.
- Labels:
-
AnyConnect
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2018 08:07 PM
Hello,
"Show the ASA's SAML SP metadata:
You can get the ASA's SAML SP metadata from https://172.23.34.222/saml/sp/metadata/cloud_idp_onelogin. In the URL, cloud_idp_onelogin is the tunnel group name."
Here is an example from a lab we had a couple years ago using PingFederate as the IDP
10.1.100.254 is the ASAv
https://10.1.100.254/saml/sp/metadata/saml << the last saml is the name of my tunnel group in the lab

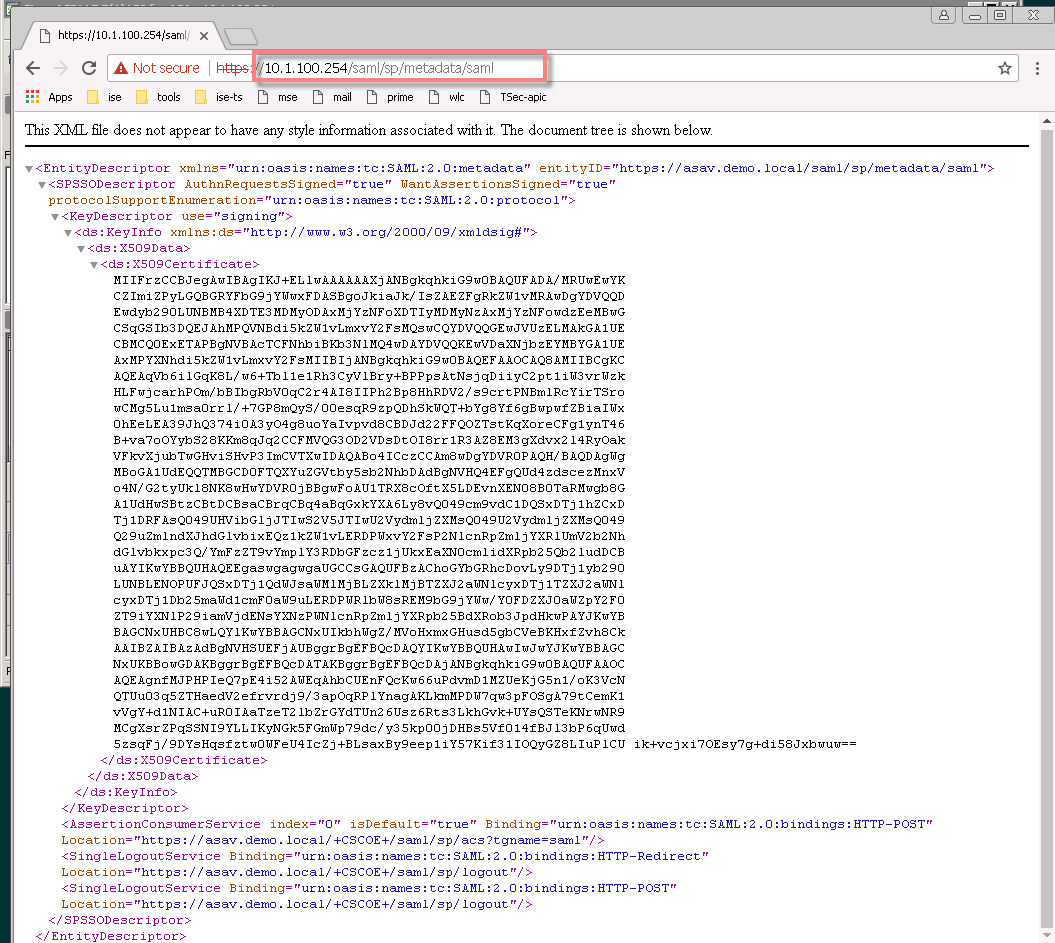
HTH
Best regards,
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2018 08:07 PM
Hello,
"Show the ASA's SAML SP metadata:
You can get the ASA's SAML SP metadata from https://172.23.34.222/saml/sp/metadata/cloud_idp_onelogin. In the URL, cloud_idp_onelogin is the tunnel group name."
Here is an example from a lab we had a couple years ago using PingFederate as the IDP
10.1.100.254 is the ASAv
https://10.1.100.254/saml/sp/metadata/saml << the last saml is the name of my tunnel group in the lab


HTH
Best regards,
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2018 04:21 PM
Hello Paul,
thank you for your very quick and useful answer! Using the XML I got from the ASA, now I get redirected to the IdP, and if I input a set of correct credentials I get redirected back to the ASA, however I cannot login.
I activated "debug webvpn saml 255" and "debug webvpn 255" and I get the following error messages:
[SAML] consume_assertion: The identifier of a provider is unknown to #LassoServer. To register a provider in a #LassoServer object, you must use the methods lasso_server_add_provider() or lasso_server_add_provider_from_buffer().
[saml] webvpn_login_primary_username: SAML assertion validation failed
I edited the Claim Rules on ADFS to send to the ASA the NameID attribute, which I tried to populate with the User-Principal-Name, samAccountName, Given-Name, but none worked.
Do you have any other suggestions? Are there other debug commands that I can use to understand what's going on?
Thanks again,
Silla
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2018 05:21 PM
Such failures usually due to a wrong value specified for idp-entityID.
Configure a SAML 2.0 Identity Provider (IdP) says,
...
...
We may find the entityID element by downloading the metadata XML from ADFS @ https://<ADFS-SPN>/federationmetadata/2007-06/federationmetadata.xml
Or, check the tool "AD FS Management" > Federation Service Properties > Federation Service identifier.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2018 03:20 AM
And that did it! Thank you hslai for the ADFS tip!
Thank you both very much!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2020 03:22 PM
How did you get the xml file from the ASA?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2021 04:51 AM
Can anyone provide some screenshots of the ADFS configuration? I get the error consumer "association: status code is not success" when debuging the saml auth on the tunnel-group. Looks for me that the Claim rule si not correct. What has to be in der NameID Claim Rule regarding LDAP attributes?
Thank you so much
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2021 12:09 AM
I can answer my question myself by now
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide