- Cisco Community
- Technology and Support
- Security
- VPN
- After upgraded to Windows 10 anyconnect 3.0 can't connect to ASA SSL VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
After upgraded to Windows 10 anyconnect 3.0 can't connect to ASA SSL VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2015 07:40 AM
Hello,
i'm using Cisco AnyConnect Client to connect to my Cisco ASA 5505 security gateway router. I also use this to connect to my parents Linux box which use OpenConnect SSL VPN and both of them worked flawless before i had upgraded my box to Windows 10. After that i cannot connect anymore to my home ASA router i got -> Cisco AnyConnect was not able to establish a connection to the specified secure gateway.
The OpenConnect SSL VPN works fine. I'm very sure there is no changes for the server part. I've tried to reinstall the AnyConnect Client but this not resolved my issue.
Can somebody help me with this? I can provide logs or do some tests??
Thanks in advice.
- Labels:
-
Remote Access
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2015 08:38 AM
Anyconnect 3.0 is not supported.
AnyConnect 3.1MR10 (3.1.10010) and later are compatible with Windows 10 official release.
http://www.cisco.com/c/en/us/td/docs/security/vpn_client/anyconnect/anyconnect31/release/notes/anyconnect31rn.html#pgfId-320051
Please rate useful post and mark answers as "correct" if applicable.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-10-2015 04:34 AM
Ok, i'm using version 3.0 of AnyConnect because it works perfect when i can connect :-)
Next scenario: AnyConnect 4.1.04011 with fresh installation of Windows 10, the result:
I can connect to my home (ASA Security Gateway) but.. i can access only one of security routed networks... The AnyConnect client shows there is a three security routed networks, and one non-secured network which is 0.0.0.0.
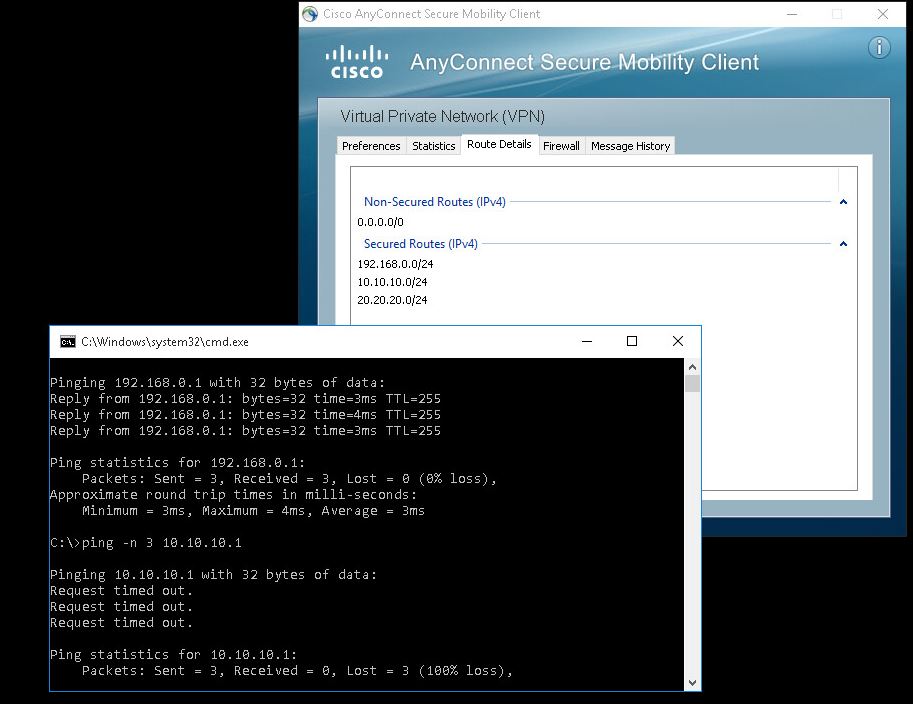
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-10-2015 11:46 PM
There is a configuration of my Cisco ASA firewall.
hellhound(config)# show version
Cisco Adaptive Security Appliance Software Version 8.2(5)
Device Manager Version 6.2(5)
Compiled on Fri 20-May-11 16:00 by builders
System image file is "disk0:/asa825-k8.bin"
Config file at boot was "startup-config"
hellhound up 143 days 10 hours
Hardware: ASA5505, 256 MB RAM, CPU Geode 500 MHz
Internal ATA Compact Flash, 128MB
BIOS Flash M50FW080 @ 0xffe00000, 1024KB
hellhound(config)#
hellhound(config)# show running-config | include Split
access-list Split_Tunnel extended permit ip 192.168.0.0 255.255.255.0 172.16.0.0 255.255.255.224
access-list Split_Tunnel extended permit ip 10.10.10.0 255.255.255.0 172.16.0.0 255.255.255.224
access-list Split_Tunnel extended permit ip 20.20.20.0 255.255.255.0 172.16.0.0 255.255.255.224
split-tunnel-network-list value Split_Tunnel
hellhound(config)#
hellhound(config)# show running-config access-list
access-list NAT_Exemption_Inside extended permit ip 192.168.0.0 255.255.255.0 172.16.0.0 255.255.255.224
access-list NAT_Exemption_Inside extended permit ip 192.168.0.0 255.255.255.0 10.10.10.0 255.255.255.0
access-list NAT_Exemption_Inside extended permit ip 192.168.0.0 255.255.255.0 20.20.20.0 255.255.255.0
access-list NAT_Exemption_DMZ extended permit ip 10.10.10.0 255.255.255.0 172.16.0.0 255.255.255.224
access-list NAT_Exemption_DMZ extended permit ip 10.10.10.0 255.255.255.0 192.168.0.0 255.255.255.0
access-list NAT_Exemption_DMZ extended permit ip 10.10.10.0 255.255.255.0 20.20.20.0 255.255.255.0
access-list Split_Tunnel extended permit ip 192.168.0.0 255.255.255.0 172.16.0.0 255.255.255.224
access-list Split_Tunnel extended permit ip 10.10.10.0 255.255.255.0 172.16.0.0 255.255.255.224
access-list Split_Tunnel extended permit ip 20.20.20.0 255.255.255.0 172.16.0.0 255.255.255.224
access-list Inside_to_Outside extended permit ip 192.168.0.0 255.255.255.0 any
access-list DMZ_to_Outside extended permit ip 10.10.10.0 255.255.255.0 any
access-list Guest_to_Outside extended permit ip 20.20.20.0 255.255.255.0 any
access-list NAT_Exemption_Guest extended permit ip 20.20.20.0 255.255.255.0 172.16.0.0 255.255.255.224
access-list NAT_Exemption_Guest extended permit ip 20.20.20.0 255.255.255.0 10.10.10.0 255.255.255.0
access-list NAT_Exemption_Guest extended permit ip 20.20.20.0 255.255.255.0 192.168.0.0 255.255.255.0
access-list Static_Inside_Traffic extended permit tcp any interface Outside eq 7000
access-list Static_Inside_Traffic extended permit tcp any interface Outside eq www
access-list Static_Inside_Traffic extended permit tcp any interface Outside eq https
access-list Static_Inside_Traffic extended permit tcp any interface Outside eq 3389
access-list DNS_from_DMZ_to_Inside extended permit tcp 10.10.10.0 255.255.255.0 host 192.168.0.7 eq domain
access-list DNS_from_DMZ_to_Inside extended permit udp 10.10.10.0 255.255.255.0 host 192.168.0.7 eq domain
access-list DNS_from_DMZ_to_Inside extended deny ip 10.10.10.0 255.255.255.0 192.168.0.0 255.255.255.0
access-list DNS_from_DMZ_to_Inside extended permit ip 10.10.10.0 255.255.255.0 any
hellhound(config)#
hellhound(config)# show running-config access-group
access-group Static_Inside_Traffic in interface Outside
access-group DNS_from_DMZ_to_Inside in interface DMZ
hellhound(config)#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-12-2015 05:42 AM
What is the network address from where you are connecting from?
Please rate useful post and mark answers as "correct" if applicable.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-12-2015 05:48 AM
The address from VPN network 172.16.0.0 255.255.255.224, i can show the Web VPN config section of my main config.
The problem is Windows not setting up second and third routes correctly. Because im seeing routers to this network on the AnyConnect software, but when i do from windows command promt: route print im seeing only one of routes which is for 192.168.0.0 network through 172.16.0.121 which is currently setted ip address to my Cisco AnyConnect virtual Adapter.
-------------------------------------
With version 3.0 and Windows 7 i dont have any problems.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

