- Cisco Community
- Technology and Support
- Security
- VPN
- AnyConnect Always-On Exception
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
AnyConnect Always-On Exception
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2019 10:44 AM - edited 02-21-2020 09:37 PM
Hey all,
I have an interesting need here. We force AnyConnect to be always on for all users. We have a use-case where some users need an exception at times, but we can't allow it all the time. For instance, let's say I need to go configure a network device out in the field, but the only way to do this is to hardcode an IP on my laptop that should be able to talk to the field device. These devices don't have a console option. Obviously with Always-On enabled, you can't talk to anything until you're on a trusted network or you authenticate successfully on AnyConnect.
My Question:
Is there a way to always enforce Always-On, however, use Trusted Network Detection or some other option that only a few select users have rights to change on their PC in order to allow them to talk through their NIC to these network devices? We wouldn't want them to have internet access at all when using the exception to keep security in place.
One Example Test:
A test I tried, but did not work was to add 127.0.0.1 as a Trusted DNS Server. I then hardcoded my network adapter (wi-fi in this instance) to use DNS server of 127.0.0.1 but it still pushed me to get on VPN and no other network communications were working. I even rebooted but it never detected I was on a trusted network.
Any other thoughts on how I could possibly do this? Thanks!
- Labels:
-
AnyConnect
-
Remote Access
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2019 06:22 AM - edited 04-17-2019 06:24 AM
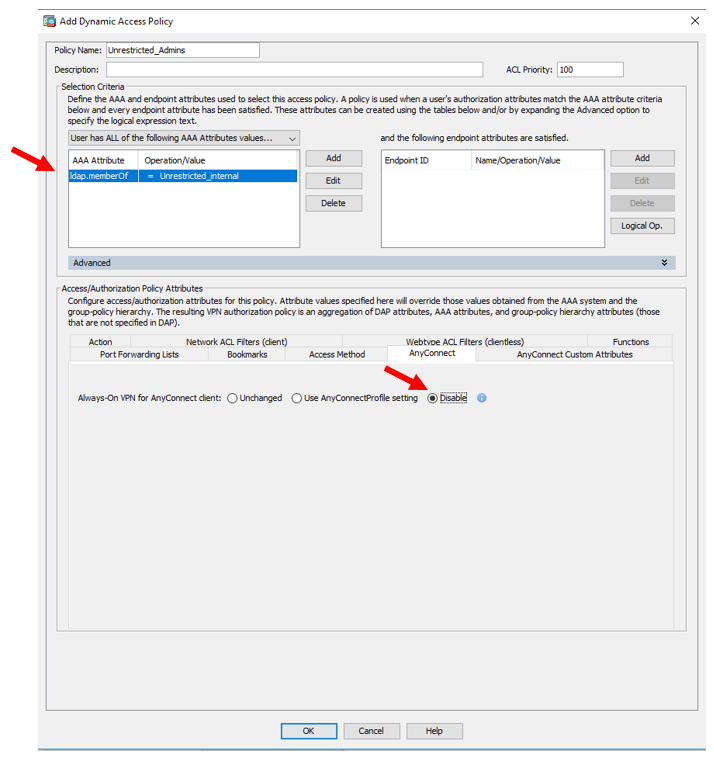
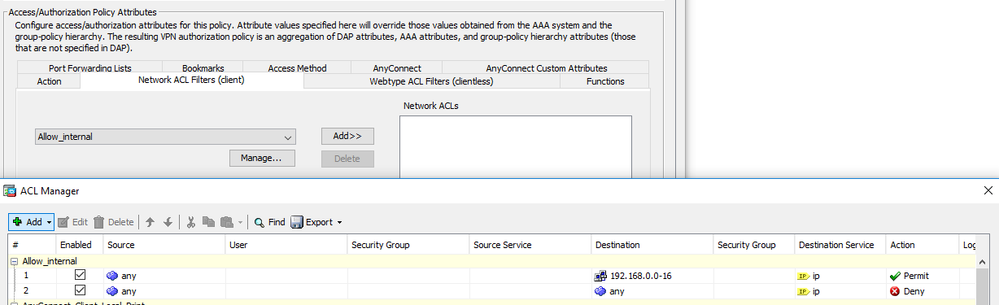
We do this very thing by using DAP. You need a DAP that will look at AD groups (or ldap). The DAP will be selected based on AD group, and within the DAP policy, always-on can be disabled. Then create an ACL for the DAP to restrict access. See screenshots.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2019 07:13 AM
Thanks for the reply. So are you saying DAP will allow Always-On to be enabled unless they're accessing a specific network? Just trying to make sense of the screenshots and that's what it looks like.
I do want Always-On to stay enabled if they were to access the internet. Sounds like you're creating some kind of "split-tunnel" option here using DAP. What licensing is required for DAP and would more software be needed on the AnyConnect installation?
Am I understanding how you have this working? Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2019 07:48 AM
Always-on is simplistic, it's either enabled or disabled. There's no white-listing of networks (I wish there were). The solution we use involves adding the user to an AD group so that the DAP turns off always-on for that user. You would need to add the user when access should be restricted and always-on disabled. And remove them when their work is complete.
No extra licensing is required to use DAP. I do believe you need the posture module, but the module can be pushed to the machine when the user logs in. No admin access is required. It may work without the posture module, but you would need to test. In any case, there is no extra cost or license for this solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2019 08:02 AM
I'm still messing around with the TND option and finding a way to force AnyConnect to see it as a trusted network by making changes to the NIC adapter. I'm looking at both IP and DNS Suffix settings. More testing to come.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2019 09:30 AM
With the DAP you can place an ACL on their traffic, which would get you the restrictions you're after -- If I'm fully understanding your requirements.
The problem is, it requires an on-demand request from the user for access. Something like: "This is Joe, please place me in the 'restrictedaccess_disablealwayson' AD group". Then: "This is Joe, please remove me from the 'restrictedaccess_disablealwayson' AD group".
I'd be interested to hear any other ideas. I'm open to alternatives myself.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide