- Cisco Community
- Technology and Support
- Security
- VPN
- AnyConnect Certificate Matching does not work as expected.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
AnyConnect Certificate Matching does not work as expected.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2023 07:43 AM - edited 06-09-2023 08:01 AM
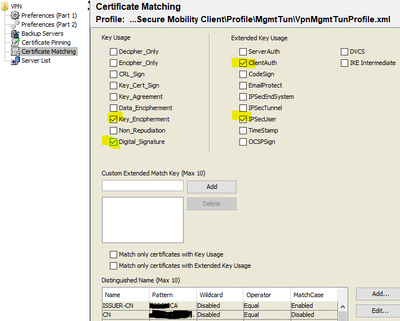
In AnyConnect Profile Editor, Certificate Matching:
If no certificate matching criteria is specified, AnyConnect applies the following certificate matching rules:
-
Key Usage: Digital_Signature
-
Extended Key Usage: Client Auth
If any criteria matching specifications are made in the profile, neither of these matching rules are applied unless they are specifically listed in the profile.
-
Key Usage—Use the following Certificate Key attributes for choosing acceptable client certificates:
-
<snipped>
-
Digital_Signature—Verifying digital signatures other than Non_Repudiation, Key_Cert_Sign or CRL_Sign.
-
-
Extended Key Usage—Use these Extended Key Usage settings. The OIDs are included in parenthesis:
-
ClientAuth (1.3.6.1.5.5.7.3.2)
-
First of all, I have to say, such sentence "If any criteria matching specifications are made in the profile, neither of these matching rules are applied unless they are specifically listed in the profile." could sound unclear, but later in the text is said: "Use the following Certificate Key attributes for choosing acceptable client certificates" or "Use these Extended Key Usage settings. The OIDs are included in parenthesis".
Second, it seems it does not work as it is described.
I have a certificate which is located in windows machine certificate store. There are 3 of them, but I need to select one from 3.
Here are my selection criteria:
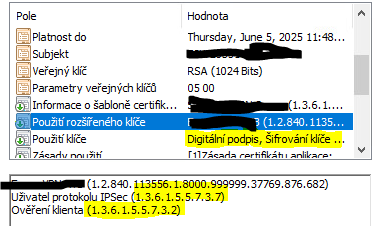
I need to select this certificate which has Key_Encipherment, Digital_Signature, ClientAuth and also IPSecUser.
Do you see OID 1.3.6.1.5.5.7.3.7 and 1.3.6.1.5.5.7.3.2 ? It is IPSecUser and ClientAuth.
From Windows Event Log Cisco AnyConnect Secure Mobility Client
1) msg:
Function: CCertStore::GetCertificates
File: c:\temp\build\thehoff\phoenix_mr50.755010980685\phoenix_mr5\vpn\commoncrypt\certificates\certstore.cpp
Line: 238
Certificate does not match criteria: ISSUER-CN=11111 CA,CN=^111111111.1111.11 <<<<what is this ^ ?>>>>
Certificate details:
Store: Microsoft Machine, Subject: CN=111111111.1111.11, Common Name: 111111111.1111.11, Issuer: DC=11, DC=11111, CN=11111 CA, Not Valid Before: Jun 6 09:48:12 2023 GMT, Not Valid After: Jun 5 09:48:12 2025 GMT, Serial: 77000036FC944733B27C12216F0004000036FC, SHA1 Fingerprint: 202BC9D745864DE10CB2007FF005570888F883F2, DNS Name: 111111111.1111.11
2) msg:
Function: CVerifyExtKeyUsage::compareEKUs
File: c:\temp\build\thehoff\phoenix_mr50.755010980685\phoenix_mr5\vpn\commoncrypt\certificates\verifyextkeyusage.cpp
Line: 330
EKU not found in certificate: 1.3.6.1.5.5.7.3.7
Am I blind or is it bug or is it misconfig or what is this ?
3) msg:
Function: CVerifyExtKeyUsage::Verify
File: c:\temp\build\thehoff\phoenix_mr50.755010980685\phoenix_mr5\vpn\commoncrypt\certificates\verifyextkeyusage.cpp
Line: 100
Extended key usage verification failed
4) msg:
Function: COpenSSLCertUtils::VerifyExtKeyUsage
File: c:\temp\build\thehoff\phoenix_mr50.755010980685\phoenix_mr5\vpn\commoncrypt\certificates\opensslcertutils.cpp
Line: 1262
Invoked Function: CVerifyExtKeyUsage::Verify
Return Code: -31391722 (0xFE210016)
Description: CERTIFICATE_ERROR_VERIFY_ENHKEYUSAGE_FAILED:The certificate did not contain the required Extended Key Usages
5) msg:
Function: COpenSSLCertUtils::VerifyExtKeyUsage
File: c:\temp\build\thehoff\phoenix_mr50.755010980685\phoenix_mr5\vpn\commoncrypt\certificates\opensslcertutils.cpp
Line: 1262
Invoked Function: CVerifyExtKeyUsage::Verify
Return Code: -31391722 (0xFE210016)
Description: CERTIFICATE_ERROR_VERIFY_ENHKEYUSAGE_FAILED:The certificate did not contain the required Extended Key Usages
There are few publicly available info about this certificate matching in anyconnect prfofile editor. Before I open tac case, I would like to ask how to explain this nonsense.
- Labels:
-
AnyConnect
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-27-2023 06:57 AM
I'm sorry to ask if you counted the number of "1"s correctly in your matching criteria. Because '^' in the CN=^111111111.1111.11 probably means that CN doesn't match. Honestly, I'm not sure. Other messages might correspond to other certificates.
What doc means is that KU and EKU are not used by default as a search criteria in certificate matching rules. From my experience, most users omit match criteria for KU and EKU entirely and use only Issuer Name or Subject Name or something like this in the matching criteria. For example, this works for us:
<CertificateMatch>
<MatchOnlyCertsWithKU>false</MatchOnlyCertsWithKU>
<DistinguishedName>
<DistinguishedNameDefinition Operator="Equal" Wildcard="Enabled" MatchCase="Disabled">
<Name>ISSUER-CN</Name>
<Pattern>something</Pattern>
</DistinguishedNameDefinition>
<DistinguishedNameDefinition Operator="Equal" Wildcard="Enabled" MatchCase="Disabled">
<Name>OU</Name>
<Pattern>Users</Pattern>
</DistinguishedNameDefinition>
</DistinguishedName>
</CertificateMatch>
You also need <CertificateStore>All</CertificateStore> for machine store, but this is most likely configured.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide