- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Anyconnect client cannot access internal resources
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2020 07:15 AM - edited 03-18-2020 07:16 AM
Hi,
I'm facing a challenge to have an SSL VPN client access internal resources (172.23.26.0/23 subnet) and hope somebody can assist me with this.
1. Client connects without any problem to the ASA using Anyconnect with authentication happening over Radius.
2. Correct IP is assigned from the pool but client has no connectivity to internal resources.
3. ASA can ping both internal and external resources.
below is the config:
ASA Version 9.8(2)
!
hostname STMFW001
domain-name stm.com
enable password [removed]
xlate per-session deny tcp any4 any4
xlate per-session deny tcp any4 any6
xlate per-session deny tcp any6 any4
xlate per-session deny tcp any6 any6
xlate per-session deny udp any4 any4 eq domain
xlate per-session deny udp any4 any6 eq domain
xlate per-session deny udp any6 any4 eq domain
xlate per-session deny udp any6 any6 eq domain
names
ip local pool STM_SSL_VPN_POOL 192.168.6.129-192.168.6.200 mask 255.255.255.128
!
interface GigabitEthernet1/1
nameif INSIDE
security-level 100
ip address 172.23.27.250 255.255.254.0
!
interface GigabitEthernet1/2
nameif OUTSIDE
security-level 0
ip address [removed]
!
interface GigabitEthernet1/3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/5
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/6
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/7
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/8
shutdown
no nameif
no security-level
no ip address
!
interface Management1/1
management-only
shutdown
no nameif
no security-level
no ip address
!
ftp mode passive
clock timezone STM 1
dns server-group DefaultDNS
domain-name stm.com
same-security-traffic permit intra-interface
object network STM_LAN
subnet 172.23.26.0 255.255.254.0
description STM Internal IP addresses
object network Anyconnect
subnet 192.168.6.128 255.255.255.128
object network Internal_network
subnet 172.23.26.0 255.255.254.0
access-list STM_internal_network standard permit 172.23.26.0 255.255.254.0
access-list AnyConnect_Client_Local_Print extended deny ip any4 any4
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq lpd
access-list AnyConnect_Client_Local_Print remark IPP: Internet Printing Protocol
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 631
access-list AnyConnect_Client_Local_Print remark Windows' printing port
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 9100
access-list AnyConnect_Client_Local_Print remark mDNS: multicast DNS protocol
access-list AnyConnect_Client_Local_Print extended permit udp any4 host 224.0.0.251 eq 5353
access-list AnyConnect_Client_Local_Print remark LLMNR: Link Local Multicast Name Resolution protocol
access-list AnyConnect_Client_Local_Print extended permit udp any4 host 224.0.0.252 eq 5355
access-list AnyConnect_Client_Local_Print remark TCP/NetBIOS protocol
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 137
access-list AnyConnect_Client_Local_Print extended permit udp any4 any4 eq netbios-ns
access-list INSIDE_access_in extended permit ip any any
access-list SED_internal standard permit 10.0.0.0 255.0.0.0
access-list SED_internal standard permit 172.16.0.0 255.240.0.0
access-list OUTSIDE_access_in extended permit tcp any 172.23.26.0 255.255.254.0 eq https
pager lines 24
logging enable
logging asdm informational
mtu INSIDE 1500
mtu OUTSIDE 1500
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 16384
nat (INSIDE,OUTSIDE) source static Internal_network Internal_network destination static Anyconnect Anyconnect no-proxy-arp route-lookup
!
object network STM_LAN
nat (any,OUTSIDE) dynamic interface
access-group INSIDE_access_in in interface INSIDE
access-group OUTSIDE_access_in in interface OUTSIDE
route OUTSIDE 0.0.0.0 0.0.0.0 [removed IP]
route INSIDE 10.0.0.0 255.0.0.0 172.23.27.254 1
route INSIDE 172.16.0.0 255.240.0.0 172.23.27.254 1
route INSIDE 192.168.6.0 255.255.255.128 172.23.27.251 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
timeout conn-holddown 0:00:15
timeout igp stale-route 0:01:10
aaa-server RADIUS protocol radius
aaa-server RADIUS (INSIDE) host 10.248.24.45
key STM_Secret%2020
radius-common-pw STM_Secret%2020
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
aaa authentication login-history
http server enable 444
http 10.248.24.72 255.255.255.255 INSIDE
no snmp-server location
no snmp-server contact
service sw-reset-button
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpoint ASDM_TrustPoint0
enrollment terminal
crl configure
crypto ca trustpoint ASDM_TrustPoint1
enrollment terminal
crl configure
crypto ca trustpoint ASDM_TrustPoint2
crl configure
crypto ca trustpoint ASDM_TrustPoint3
enrollment terminal
crl configure
crypto ca trustpoint ASDM_TrustPoint4
crl configure
crypto ca trustpoint ASDM_TrustPoint5
crl configure
crypto ca trustpoint ASDM_TrustPoint6
crl configure
crypto ca trustpoint ASDM_TrustPoint7
crl configure
crypto ca trustpoint ASDM_TrustPoint8
crl configure
crypto ca trustpoint ASDM_TrustPoint9
crl configure
crypto ca trustpoint ASDM_TrustPoint10
crl configure
crypto ca trustpoint ASDM_TrustPoint11
crl configure
crypto ca trustpoint ASDM_TrustPoint12
crl configure
crypto ca trustpoint ASDM_TrustPoint13
keypair ASDM_TrustPoint13
crl configure
crypto ca trustpoint ASDM_TrustPoint13-1
crl configure
crypto ca trustpool policy
crypto ca certificate chain ASDM_TrustPoint0
certificate ca 083be056904246b1a1756ac95991c74a
308203af 30820297 a0030201 02021008 3be05690 4246b1a1 756ac959 91c74a30
0d06092a 864886f7 0d010105 05003061 310b3009 06035504 06130255 53311530
13060355 040a130c 44696769 43657274 20496e63 31193017 06035504 0b131077
77772e64 69676963 6572742e 636f6d31 20301e06 03550403 13174469 67694365
72742047 6c6f6261 6c20526f 6f742043 41301e17 0d303631 31313030 30303030
305a170d 33313131 31303030 30303030 5a306131 0b300906 03550406 13025553
31153013 06035504 0a130c44 69676943 65727420 496e6331 19301706 0355040b
13107777 772e6469 67696365 72742e63 6f6d3120 301e0603 55040313 17446967
69436572 7420476c 6f62616c 20526f6f 74204341 30820122 300d0609 2a864886
f70d0101 01050003 82010f00 3082010a 02820101 00e23be1 1172dea8 a4d3a357
aa50a28f 0b7790c9 a2a5ee12 ce965b01 0920cc01 93a74e30 b753f743 c4690057
9de28d22 dd870640 008109ce ce1b83bf dfcd3b71 46e2d666 c705b376 27168f7b
9e1e957d eeb748a3 08dad6af 7a0c3906 657f4a5d 1fbc17f8 abbeee28 d7747f7a
78995985 686e5c23 324bbf4e c0e85a6d e370bf77 10bffc01 f685d9a8 44105832
a97518d5 d1a2be47 e2276af4 9a33f849 08608bd4 5fb43a84 bfa1aa4a 4c7d3ecf
4f5f6c76 5ea04b37 919edc22 e66dce14 1a8e6acb fecdb314 6417c75b 299e32bf
f2eefad3 0b42d4ab b74132da 0cd4eff8 81d5bb8d 583fb51b e84928a2 70da3104
ddf7b216 f24c0a4e 07a8ed4a 3d5eb57f a390c3af 27020301 0001a363 3061300e
0603551d 0f0101ff 04040302 0186300f 0603551d 130101ff 04053003 0101ff30
1d060355 1d0e0416 041403de 503556d1 4cbb66f0 a3e21b1b c397b23d d155301f
0603551d 23041830 16801403 de503556 d14cbb66 f0a3e21b 1bc397b2 3dd15530
0d06092a 864886f7 0d010105 05000382 010100cb 9c37aa48 13120afa dd449c4f
52b0f4df ae04f579 7908a324 18fc4b2b 84c02db9 d5c7fef4 c11f58cb b86d9c7a
74e79829 ab11b5e3 70a0a1cd 4c889993 8c9170e2 ab0f1cbe 93a9ff63 d5e40760
d3a3bf9d 5b09f1d5 8ee353f4 8e63fa3f a7dbb466 df6266d6 d16e418d f22db5ea
774a9f9d 58e22b59 c04023ed 2d288245 3e795492 2698e080 48a837ef f0d67960
16deace8 0ecd6eac 4417382f 49dae145 3e2ab936 53cf3a50 06f72ee8 c457496c
612118d5 04ad783c 2c3a806b a7ebaf15 14e9d889 c1b9386c e2916c8a ff64b977
255730c0 1b24a3e1 dce9df47 7cb5b424 080530ec 2dbd0bbf 45bf50b9 a9f3eb98
0112adc8 88c69834 5f8d0a3c c6e9d595 956dde
quit
crypto ca certificate chain ASDM_TrustPoint1
certificate ca 08a5a246cd4b5c8c83d702b4bbab5349
308204b1 30820399 a0030201 02021008 a5a246cd 4b5c8c83 d702b4bb ab534930
0d06092a 864886f7 0d01010b 05003061 310b3009 06035504 06130255 53311530
13060355 040a130c 44696769 43657274 20496e63 31193017 06035504 0b131077
77772e64 69676963 6572742e 636f6d31 20301e06 03550403 13174469 67694365
72742047 6c6f6261 6c20526f 6f742043 41301e17 0d313731 31303631 32323333
335a170d 32373131 30363132 32333333 5a305e31 0b300906 03550406 13025553
31153013 06035504 0a130c44 69676943 65727420 496e6331 19301706 0355040b
13107777 772e6469 67696365 72742e63 6f6d311d 301b0603 55040313 14526170
69645353 4c205253 41204341 20323031 38308201 22300d06 092a8648 86f70d01
01010500 0382010f 00308201 0a028201 0100e52d a88a1128 f679e97b 3a33883b
71e1658b 2c2965fd ed2dd446 1e984e67 f8c80fe6 f89a1cbc be5691cf fa7757e4
3d7c20d2 2eb8057c c05ab6e8 a1795345 8d219890 a7a98bb4 85a351e5 833c0dbc
39eca14e 58fd4cb9 366decad 6ed154eb 2a5ba565 25b66bd8 e55f2782 ca42ee71
513428e9 7e70c40f 6911c89c cef32a0a 305cf827 8244f0de cd035b89 c1410531
4bc72ecd 2c70ba0f 66429c7b 02119b54 55d80c66 150c4991 d7fb60df 4f724922
7f65e09b 76f8f016 67d337f4 a97b1278 6bbce2e6 bd830ce3 cc8eed6d 30636b24
e94fefd7 a56b8156 fe9fbdaa c8e9b8a4 281f39f4 e48642ec 3bdd75e0 7ae17010
f1d3211a 14b64cee dff110f8 bb70ce79 24750203 010001a3 82016630 82016230
1d060355 1d0e0416 041453ca 1759fc6b c003212f 1aaee4aa a81c8256 da75301f
0603551d 23041830 16801403 de503556 d14cbb66 f0a3e21b 1bc397b2 3dd15530
0e060355 1d0f0101 ff040403 02018630 1d060355 1d250416 30140608 2b060105
05070301 06082b06 01050507 03023012 0603551d 130101ff 04083006 0101ff02
01003034 06082b06 01050507 01010428 30263024 06082b06 01050507 30018618
68747470 3a2f2f6f 6373702e 64696769 63657274 2e636f6d 30420603 551d1f04
3b303930 37a035a0 33863168 7474703a 2f2f6372 6c332e64 69676963 6572742e
636f6d2f 44696769 43657274 476c6f62 616c526f 6f744341 2e63726c 30630603
551d2004 5c305a30 37060960 86480186 fd6c0102 302a3028 06082b06 01050507
0201161c 68747470 733a2f2f 7777772e 64696769 63657274 2e636f6d 2f435053
300b0609 60864801 86fd6c01 01300806 0667810c 01020130 08060667 810c0102
02300d06 092a8648 86f70d01 010b0500 03820101 007e23c7 f2ca356e 5992515c
616b3c12 36e6d27c b329e642 d8a39561 1ecff207 af2b2b25 5a6e17a3 8052ccaa
f6df916c 278685b7 ac808afd 5e634b59 fd9375f1 b3864864 ada0473f 244e2870
8cebf0fe 4c835d64 4581db9a 0627af54 717a48b9 99279bdf d0c6c53a 490f8906
86ce655c da28e1ca 27522889 c0a6aa1f bbe1d9b6 abc9df29 30849a83 cdc952ac
9519cdad 58fa4ed3 7dbdfc25 aada4af2 aafeba39 2323c2e9 54cf4757 7f838741
ab11ec23 5f22bfb8 29271ce8 00654394 4317ce8f 19e13a91 dc124241 6207f710
cac372ab 48c40d04 e47dada9 8e6b96b4 c08d6c19 e1157058 7a37ee6c 885a51b1
2fd85390 0777426a ff853e0e 5e12f797 4d5c8c9c 6a
quit
[REMOVED NOT RELEVANT LINES]
crypto ikev2 remote-access trustpoint ASDM_TrustPoint13
telnet timeout 5
ssh stricthostkeycheck
ssh 10.248.24.72 255.255.255.255 INSIDE
ssh 10.248.88.72 255.255.255.255 INSIDE
ssh 172.21.50.20 255.255.255.255 INSIDE
ssh 172.23.27.14 255.255.255.255 INSIDE
ssh timeout 20
ssh key-exchange group dh-group1-sha1
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ntp server 172.23.27.253
ntp server 10.245.1.253 source INSIDE
ntp server 10.248.1.253 source INSIDE
ntp server 10.248.65.253 source INSIDE
ntp server 10.245.1.252 source INSIDE
ntp server 10.248.1.252 prefer
ntp server 10.248.65.252 source INSIDE
ssl trust-point ASDM_TrustPoint13 INSIDE
ssl trust-point ASDM_TrustPoint13 OUTSIDE
webvpn
enable OUTSIDE
anyconnect image disk0:/anyconnect-win-3.0.10055-k9.pkg 1
anyconnect enable
tunnel-group-list enable
cache
disable
error-recovery disable
group-policy DfltGrpPolicy attributes
dns-server value 172.23.26.6
vpn-tunnel-protocol ikev1 ikev2 l2tp-ipsec ssl-client ssl-clientless
group-policy STM-Group internal
group-policy STM-Group attributes
dns-server value 172.23.26.6 10.248.24.45
vpn-tunnel-protocol ssl-client ssl-clientless
default-domain value stm.org
split-tunnel-all-dns disable
webvpn
url-list none
dynamic-access-policy-record DfltAccessPolicy
username [Removed]
tunnel-group STM_Profile type remote-access
tunnel-group STM_Profile general-attributes
address-pool STM_SSL_VPN_POOL
authentication-server-group RADIUS LOCAL
default-group-policy STM-Group
tunnel-group STM_Profile webvpn-attributes
group-alias STM_Profile enable
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map global_policy
class inspection_default
inspect ftp
inspect h323 h225
inspect h323 ras
inspect ip-options
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect tftp
inspect sip
inspect xdmcp
inspect dns preset_dns_map
inspect icmp
policy-map type inspect dns migrated_dns_map_2
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map type inspect dns migrated_dns_map_1
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
Cryptochecksum:812175a9af7eb759bfd119ac0bf0b174
: end
Solved! Go to Solution.
- Labels:
-
AnyConnect
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-21-2020 04:31 AM
It's a bit of a hack, but you could put a persistent static host route in the web server to reach the VPN pool addresses via the new ASA's address. (The proper solution, of course, is to fix the unmanaged router.)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2020 06:55 PM
Are you pushing the acl AnyConnect_Client_Local_Printto your users?
Because the first statement is a deny io any any:
access-list AnyConnect_Client_Local_Print extended deny ip any4 any4
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-20-2020 02:45 AM
Thanks for your reply.
The ACL is not pushed to users (I did not even know it was possible).
I have removed all access lists as they were just for testing purpose.
I'm still unable to access internal resources.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-20-2020 06:23 PM
packet-tracer input inside icmp 172.23.27.10 8 0 192.168.6.130
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-20-2020 09:02 PM
Do your internal devices know to route to the ASA to reach the VPN pool addresses?
i.e., these:
ip local pool STM_SSL_VPN_POOL 192.168.6.129-192.168.6.200 mask 255.255.255.128
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-21-2020 03:04 AM - edited 03-21-2020 03:07 AM
Hijacking this question :-)
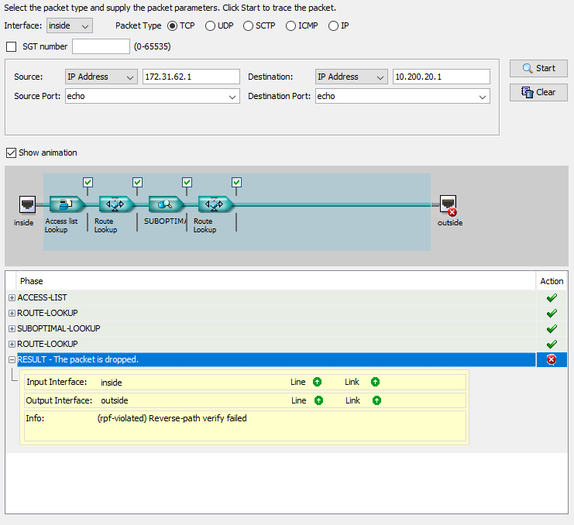
I'm having the same issue... just setup the same environment, just ran the packet tracer as suggested and i am getting; any assistance would be appreciated, been banging my head for a while.. let me know if config is required..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-21-2020 04:02 AM
Hi all and thanks for your help.
After digging a little bit, turns out my problem is not related to the configuration. It's a design problem (was supposed to be a temporary solution). I'm still very interested to know how to fix it so I've attached a diagram (only relevant parts and IP are mentioned).
Now, the play by play :)
1. Client connects using anyconnect and gets the IP 192.168.6.131 /25
2. client makes a request to webserver 172.23.26.7 (tested, the server gets the request)
3. server replies and send response to its default gateway- 172.23.27.254 (this is an unmanaged device, unfortunately)
4. the unmanaged gateway has a static route for 192.168.6.0/24 with the next hop being an old ASA (172.23.27.251)
5. Old ASA drops the traffic because of inspection (initial traffic did not flow through it and it sees reply traffic).
Any idea on how to fix this issue ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-21-2020 04:31 AM
It's a bit of a hack, but you could put a persistent static host route in the web server to reach the VPN pool addresses via the new ASA's address. (The proper solution, of course, is to fix the unmanaged router.)
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide