- Cisco Community
- Technology and Support
- Security
- VPN
- AnyConnect split-tunnel to MPLS not working
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
AnyConnect split-tunnel to MPLS not working
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2022 12:16 PM - edited 06-23-2022 12:25 PM
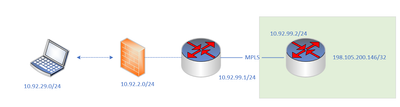
Have a long working RA-VPN environment with a request to route AnyConnect client traffic through the VPN and then across an MPLS connection a specific set of IPs. I have added those networks/IPs to the split-tunnel ACL, exempted them from NAT and made sure the ASA (FP running ASA code) has the correct routes. I cannot pass traffic from the RA VPN client to any of the IPs on the far side of the MPLS connection. The routes are there when connected, traceroute shows the core as the next hop and all LAN directed traffic works without issue.
I have no problem passing traffic from the inside interface of the ASA or from clients within the office, doing a packet capture shows ECHO requests being sent with no replies and traceroute shows a bunch of TCP retransmissions from AnyConnect clients.
Struggling to figure out why this isn't working. I have no access to the far side of the MPLS so I just have to assume there is a route back to my VPN clients but I don't know why there wouldn't be as its within the /16 of the office where all the traffic is able to pass. I asked the vendor to confirm but is there anything I can look at in the meantime?
What is strange is I see no no-NAT hits from the return traffic so I just assume that means nothing is coming back and the only reason that can be is there is no route back to my RA-VPN client subnet from the vendor side (#3 below)? Not even sure that is an issue because I can send traffic from the LAN to my vpn client and it works.
Manual NAT Policies (Section 1)
2 (outside-primary) to (inside) source static RA-VPN-Networks RA-VPN-Networks destination static DM_INLINE_NETWORK_2 DM_INLINE_NETWORK_2 no-proxy-arp route-lookup
translate_hits = 8444, untranslate_hits = 8991
3 (inside) to (outside-primary) source static DM_INLINE_NETWORK_8 DM_INLINE_NETWORK_8 destination static RA-VPN-Networks RA-VPN-Networks no-proxy-arp
translate_hits = 0, untranslate_hits = 0
4 (outside-primary) to (outside-primary) source dynamic RA-VPN-Networks interface
translate_hits = 12069, untranslate_hits = 3031
- Labels:
-
AnyConnect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2022 11:18 AM
I have done that to no end my man.
And note the CE ip route has always been there because this environment has been running for the better part of 10+ years. The only change is trying to route specific traffic through RA-VPN to MPLS. RA-VPN network and connectivity to and from on-prem is and has been working so that CE route is there and always has been.
3850#show run | i route router eigrp 9999 router bgp 65001 ip route 10.92.29.0 255.255.255.0 10.92.2.2 (ASA IP)
And ping works from the INSIDE interface of the ASA just not from an RA-VPN client.
1120(config)# route inside 198.105.200.146 255.255.255.255 10.92.2.1 1120# ping inside 198.105.200.146 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 198.105.200.146, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 250/252/260 ms
Will be a little while until I can test from RA-VPN client because I have to wait until no one is using it because when I make the changes (route/NO-NAT) it breaks this functionality for users connected to the VPN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-07-2022 02:02 PM
Update this got fixed and was due to not advertising routes back to the RA-VPN client towards the MPLS connection because of bad subnet mask on our end. Sometimes its the simplest things.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-07-2022 02:13 PM
thanks for update me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2022 10:46 PM
You can use the AnyConnect Diagnostics and Reporting Tool (DART) in order to collect the data that is useful for troubleshooting AnyConnect installation and connection problems. The DART Wizard is used on the computer that runs AnyConnect. The DART assembles the logs, status, and diagnostic information for the Cisco Technical Assistance Center (TAC) analysis and does not require administrator privileges to run on the client machine.
Install the DART
Complete these steps in order to install the DART:
Download the AnyConnect Client image from the Cisco website. In order to choose the correct image for download, refer to the Cisco AnyConnect Secure Mobility Client web page. A download link is provided on this page. Navigate to the download page and select the appropriate version. Perform a search for Full installation package - Window / Standalone installer (ISO).
Note: An ISO installer image is then downloaded (such as anyconnect-win-3.1.06073-pre-deploy-k9.iso).
Use WinRar or 7-Zip in order to extract the contents of the ISO package:
Browse to the folder to which the contents were extracted.
Run the Setup.exe file and select only Anyconnect Diagnostic And Reporting Tool:
Run the DART
Here is some important information to consider before you run the DART:
The issue must be recreated at least once before you run the DART.
The date and time on the user machine must be noted when the issue is recreated.
Run the DART from the Start Menu on the client machine:
Either Default or Custom mode can be selected. Cisco recommends that you run the DART in the Default mode so that all of the information can be captured in a single shot.
Once completed, the tool saves the DART bundle .zip file to the client desktop. The bundle can then be emailed to the TAC (after you open a TAC case) for further analysis.
Regards,
Rachel Gomez
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide