- Cisco Community
- Technology and Support
- Security
- VPN
- Re: anyconnect vpn ssl - dont have access to internal resources
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2022 10:55 AM
Hi,
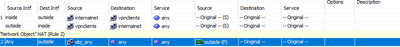
I configured vpn ssl with anyconnect. When I connect to vpn from my remote host i can ping only Asa's outside interface. From inside i have static route to internal network and i can ping all internal resources. From outside I have static route to any and i can ping internal resources and internet. Firewall permit any any. I configured NAT rule :
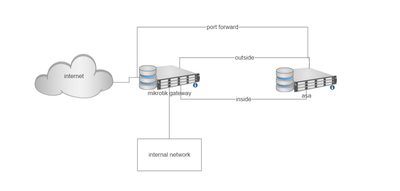
My topology looks that :
Anyone know where looking for solution ?
Solved! Go to Solution.
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2022 12:40 AM
My nat conf :
nat (inside,outside) source static internalnet internalnet destination static vpnclients vpnclients no-proxy-arp route-lookup
!
object network obj_any
nat (inside,outside) dynamic interface
internalnet - x.x.101.0/28
vpnclients - x.x.99.0/24
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2022 12:45 AM
@lukaszhar ok, but your screenshots confirmed you have a NAT problem, so there is likely another NAT rule causing a problem
run show nat detail from the CLI and provide the output for review.
run packet-tracer input outside icmp <x.x.99.44> 8 0 <x.x.101.5> and provide the output for review. Make sure the RAVPN IP address you use isn't already in use, that will provide a misleading result.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2022 01:05 AM
im shure that every adrress is unicat. When im pinging this adrress i get responce time out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2022 01:07 AM
when im pinging this address from remote host i get responce time out
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2022 01:10 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2022 01:16 AM
@lukaszhar can you run packet-tracer and show nat detail from the CLI as requested please?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2022 01:20 AM - edited 12-15-2022 01:26 AM
for me this is better using CLI than ASDM.
but webvpn and unknown egress interface can be from
You dont add route-lookup to your anyconnect NAT ? are you add it ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2022 01:33 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2022 01:39 AM
i finded solution. i had to add rule on firewall permit icmp.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2022 01:55 AM
OMG, we make big Loop and solution is simple.
thanks for sharing that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2022 01:27 AM
ciscoasa# packet-tracer input outside icmp x.x.99.44 8 0 x.x.101.5
Phase: 1
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop x.x.101.5 using egress ifc inside
Phase: 2
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (inside,outside) source static internalnet internalnet destination static vpnclients vpnclients no-proxy-arp route-lookup
Additional Information:
NAT divert to egress interface inside
Untranslate x.x.101.5/0 to x.x.101.5/0
Phase: 3
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group global_access global
access-list global_access extended permit ip any any
Additional Information:
Phase: 4
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (inside,outside) source static internalnet internalnet destination static vpnclients vpnclients no-proxy-arp route-lookup
Additional Information:
Static translate x.x.99.44/0 to x.x.99.44/0
Phase: 5
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 6
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 7
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
Additional Information:
Phase: 8
Type: NAT
Subtype: rpf-check
Result: ALLOW
Config:
nat (inside,outside) source static internalnet internalnet destination static vpnclients vpnclients no-proxy-arp route-lookup
Additional Information:
Phase: 9
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 11543, packet dispatched to next module
Phase: 10
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop x.x.101.5 using egress ifc inside
Phase: 11
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (inside,outside) source static internalnet internalnet destination static vpnclients vpnclients no-proxy-arp route-lookup
Additional Information:
NAT divert to egress interface inside
Untranslate x.x.101.5/0 to x.x.101.5/0
Phase: 12
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group global_access global
access-list global_access extended permit ip any any
Additional Information:
Phase: 13
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (inside,outside) source static internalnet internalnet destination static vpnclients vpnclients no-proxy-arp route-lookup
Additional Information:
Static translate x.x.99.44/0 to x.x.99.44/0
Phase: 14
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 15
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 16
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop x.x.101.5 using egress ifc inside
Phase: 17
Type: ADJACENCY-LOOKUP
Subtype: next-hop and adjacency
Result: ALLOW
Config:
Additional Information:
adjacency Active
next-hop mac address x.x.x hits 59 reference 4
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: inside
output-status: up
output-line-status: up
Action: allow
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2022 02:42 AM
Manual NAT Policies (Section 1)
1 (inside) to (outside) source static internalnet internalnet destination static vpnclients vpnclients no-proxy-arp route-lookup
translate_hits = 4, untranslate_hits = 8
Source - Origin: x.x.101.0/24, Translated: x.x.101.0/24
Destination - Origin: x.x.99.0/24, Translated: x.x.99.0/24
Auto NAT Policies (Section 2)
1 (inside) to (outside) source dynamic obj_any interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 0.0.0.0/0, Translated: x.x.100.1/30
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide