- Cisco Community
- Technology and Support
- Security
- VPN
- AnyConnect with FTD and certificate-based authentication
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2021 12:14 AM
Hello,
Has anyone successfully implemented AnyConnect certificate-based user and/or machine authentication with FTD and Microsoft CA?
I've struggled for a while to get this to work and I have search the internet for step-by-step user guides but it's difficult to find something useful. The goal is to get AnyConnect authentication to work with user certificates for domain users and machine certificates for external consultants.
I've already distributed user and machine certificates via Group Policies from a Microsoft CA and also installed the
root and identity certificate on the FMC. Still I get "Certificate Validation Error " when trying to connect via AnyConnect.
I found the following Cisco support document when searching for this error.
https://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-firewalls/212972-anyconnect-vpn-client-troubleshooting-gu.html#anc50
This document is for the ASA, but I guess the commands should be similar for FTD.
Error: "Certificate Validation Failure"
Users are unable to launch AnyConnect and receive the Certificate Validation Failure error.
Solution
Certificate authentication works differently with AnyConnect compared to the IPSec client. In order for certificate authentication to work, you must import the client certificate to your browser and change the connection profile in order to use certificate authentication. You also need to enable this command on your ASA in order to allow SSL client-certificates to be used on the outside interface:
ssl certificate-authentication interface outside port 443
I don't have this command in my FTD config. Do I need it and if so, how do I add it? Should I use FlexConfig?
Here are the basic steps I've done so far:
- Downloaded a root certificate from the CA server and import it to FMC under Object->PKI->Trusted CAs
- On the FMC, I generated a CSR from Devices->Certificates> and then used Manual Enrollment and used the CSR to download an identity cert from the CA server using the web server template
- I created a new connection profile in FMC for RA VPN and selected Client certificate as Authentication Method
- Under tunnel-Group Access Interfaces, I selected the root certificate as Interface Trustpoint
- On my AD server, I Created Group Policy templates and distributed user and Machine certificates to the clients following this guide - http://www.network-node.com/blog/2015/12/24/server-2012-configuration-group-policy-creation and verified that the correct certificates was installed in the correct certification stores on the client.
Would appreciate some advised on how to troubleshoot this and also if someone know of a good guide that explains all the
steps for a working configuration for AnyConnect on FTD with MS CA.
Thanks
/Chess
Solved! Go to Solution.
- Labels:
-
AnyConnect
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2021 04:42 AM
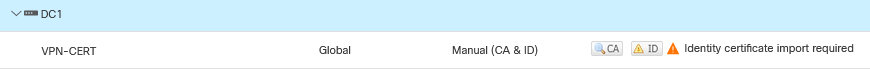
Oh, ok then. It looks that you are not using proper certificate on the headend side (FTD). You can easily verify that by opening browser session to URL/IP that you configured for users. Based on your debugs, I'm expecting to see whatever you configured under NEW-VPN-CERT.
Please go through cert installation document, and make sure you have enrolled successfully. I believe you wanted to use FTD-IDENTITY-CERT, but that one is not successfully enrolled:
ftd01# show crypto ca trustpoints
Trustpoint FTD-IDENTITY-CERT:
Not authenticated.
Once you enroll successfully, you need to modify SSL certificate too.
Also, please confirm that you do have certificate under FTD-ROOT-CA, by using command 'show crypto ca certificates'. It is crucial that your FTD can validate certificate that PC will use for authentication.
BR,
Milos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2021 04:43 AM - edited 08-09-2021 04:45 AM
Your certificate trustpoints do not look correct. Create a trustpoint that includes the identity and CA certificate.
Create a certificate enrollment (Objects > PKI > Cert Enrollment), select Enrollment Type as Manual.
Paste the contents of the CA certificate under the "CA information"
Under "Certificate Paramenters" input the CSR information.
Click Save
Navigate to Devices > Certificates
Click Add
Select Device and Cert Enrollment, click Add
Click the ID certificate to finish the id certificate import
Click Yes to generate the CSR
Copy the CSR information and get it signed (download it base 64)
Import the identity certificate from file
Use that new certificate trustpoint under the "Access Interface" section of the RAVPN config.
EDIT: Or use the offical cisco guide that @Milos_Jovanovic provided.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2021 01:21 AM - edited 08-09-2021 01:22 AM
Hi,
Most common thing for such usecase is missing configuration in user XML profile. You need to instruct PC to provide certificate for authentication and to know which certificate should it use. You are doing this by modifying user XML profile, and profile must be predeployed on PC before authentication attempt. If you are using machine certificate, you would need something like this in your XML profile:
<CertificateStore>Machine</CertificateStore>
<CertificateStoreOverride>true</CertificateStoreOverride>
This would instruct your PC to use machine credentials store, and to have enough permissions to access it. If you don't want your users to manually choose certificate, you would also add something like this:
<AutomaticCertSelection UserControllable="false">true</AutomaticCertSelection>
<CertificateMatch>
<MatchOnlyCertsWithKU>false</MatchOnlyCertsWithKU>
<DistinguishedName>
<DistinguishedNameDefinition Operator="Equal" Wildcard="Disabled" MatchCase="Enabled">
<Name>ISSUER-CN</Name>
<Pattern>YOUR ROOT NAME</Pattern>
</DistinguishedNameDefinition>
</DistinguishedName>
</CertificateMatch>
This would automatically choose certificate on behalf of your user, based on pattern you defined.
In case this doesn't solve your issue, you can find some usefull troubleshooting tips here. I found these very usefull:
debug webvpn 255
debug webvpn anyconnect 255
debug crypto ca 255
In order to troubleshoot endpoint side, you'll need to install AnyConnect DART, and analyze collected logs.
BR,
Milos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2021 01:29 AM
Thank you for the tips about the XML profiles. I will look into that. It sounds like that this could be the cause of the issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2021 04:27 AM
I modefied the user XML profiles, but I still got the same validation error.
However, the output from the debug commands when connecting, might show some useful information:
PKI[4]: Certificate verification error: self signed certificate in certificate chain
PKI[14]: map_ossl_error, pki_ossl_validate.c:62
PKI[4]: Unable to find trusted certificate chain
Also, I can see this in the FTD configuration when I do "show crypto ca trustpoint"
ftd01# show crypto ca trustpoints
Trustpoint FTD-ROOT-CA:
Not authenticated.
Trustpoint NEW-VPN-CERT:
Configured for self-signed certificate generation.
Trustpoint FTD-IDENTITY-CERT:
Not authenticated.
and this is the output from "show run crypto ca trustpoint"
crypto ca trustpoint FTD-ROOT-CA
enrollment terminal
keypair <Default-RSA-Key>
no ca-check
crl configure
crypto ca trustpoint NEW-VPN-CERT
enrollment self
subject-name OU=Firepower,O=LAB,CN=vpn.firepower.com,C=US
keypair <Default-RSA-Key>
crl configure
crypto ca trustpoint FTD-IDENTITY-CERT
enrollment terminal
keypair <Default-RSA-Key>
no ca-check
crl configure
Based on this, what can most likely be the issue? For me it looks like something is wrong/missing in the FTD configuration, but I can't figure out what it is.
Here is som screenshots from the FMC:

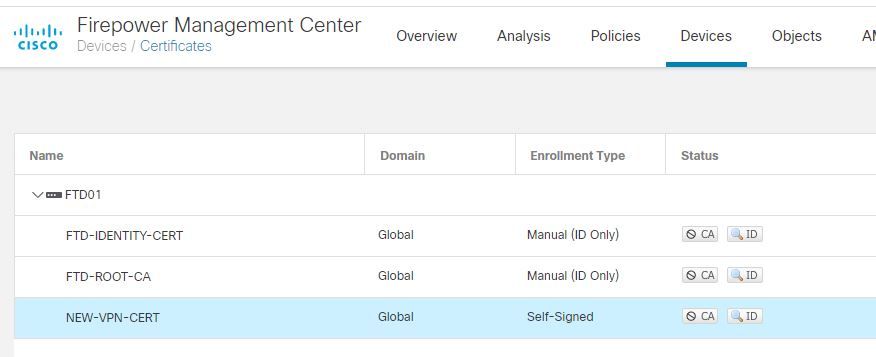
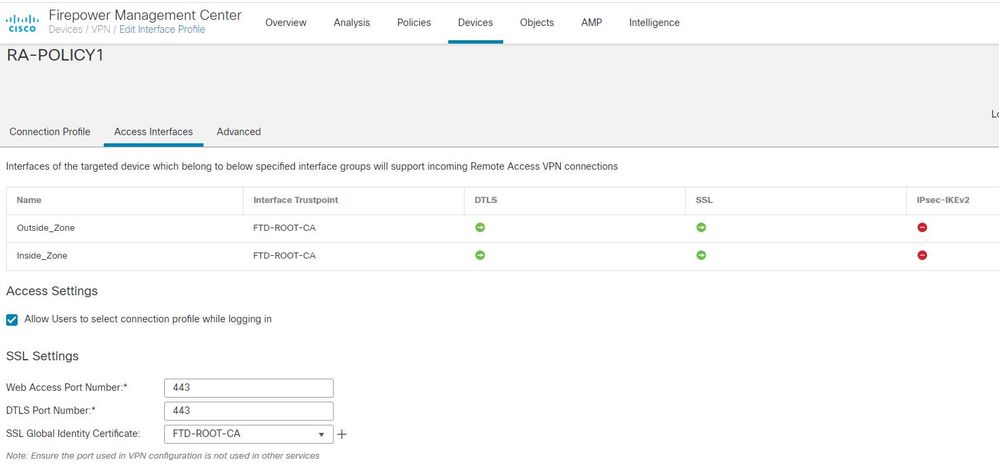
Thanks
/Chess
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2021 04:42 AM
Oh, ok then. It looks that you are not using proper certificate on the headend side (FTD). You can easily verify that by opening browser session to URL/IP that you configured for users. Based on your debugs, I'm expecting to see whatever you configured under NEW-VPN-CERT.
Please go through cert installation document, and make sure you have enrolled successfully. I believe you wanted to use FTD-IDENTITY-CERT, but that one is not successfully enrolled:
ftd01# show crypto ca trustpoints
Trustpoint FTD-IDENTITY-CERT:
Not authenticated.
Once you enroll successfully, you need to modify SSL certificate too.
Also, please confirm that you do have certificate under FTD-ROOT-CA, by using command 'show crypto ca certificates'. It is crucial that your FTD can validate certificate that PC will use for authentication.
BR,
Milos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2021 04:43 AM - edited 08-09-2021 04:45 AM
Your certificate trustpoints do not look correct. Create a trustpoint that includes the identity and CA certificate.
Create a certificate enrollment (Objects > PKI > Cert Enrollment), select Enrollment Type as Manual.
Paste the contents of the CA certificate under the "CA information"
Under "Certificate Paramenters" input the CSR information.
Click Save
Navigate to Devices > Certificates
Click Add
Select Device and Cert Enrollment, click Add
Click the ID certificate to finish the id certificate import
Click Yes to generate the CSR
Copy the CSR information and get it signed (download it base 64)
Import the identity certificate from file
Use that new certificate trustpoint under the "Access Interface" section of the RAVPN config.
EDIT: Or use the offical cisco guide that @Milos_Jovanovic provided.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2021 05:33 AM
Thanks so much for your help Milos & Rob,
After creating a new trustpoint that included both the identity and the CA cert, everything started to work and I'm now able to use certificate-based authentication.
Best regards
/Chess
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2022 03:45 AM
Hello, Chess_N
I faced the same problem. Could you elaborate on how you solved it? How to create a new transpoint with that included both the identity and the CA cert?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2022 10:49 PM
Hi @oa.sharonova,
One option to do this would be to combine various files into a single file, depending on your formating. You can Google it for, and here is one example.
I presonally prefer to use OpenSSL to manipulate with certificates. There should be a plethora of examples on the internet, but you can see another example here.
BR,
Milos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2022 09:17 AM
- Under tunnel-Group Access Interfaces, I selected the root certificate as Interface Trustpoint --- I do not think you need to do this step
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide