- Cisco Community
- Technology and Support
- Security
- VPN
- ASA 7.2 SSL VPN Internet Access no SPLIT TUNNEL
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA 7.2 SSL VPN Internet Access no SPLIT TUNNEL
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2011 12:39 PM
I have one client that I am using for SSL vpn access to the network behind the ASA. I can get this all to work just fine and have access to DNS resolution behind within the ASA's internal LAN but I'm not able to access the Internet through this ASA. I don't want to do split tunneling. I want all traffic sent and handled on the ASA. I'm giving out DHCP to this SSL VPN client from the server inside the ASA's network so the SSL client is on the same network subnet as the remote LAN.
Please advise on what I should do to give Internet access to this remote VPN SSL client. I'm guessing it' s a NAT issue but I'm not sure. here's how it looks.
SSL CLIENT 192.168.0.60/24 ----------- asa -------192.168.0.0/24 inside network
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2011 02:03 PM
Hello Jesse,
“I'm giving out DHCP to this SSL VPN client from the server inside the ASA's network so the SSL client is on the same network subnet as the remote LAN.”
Recommendation:
In order to avoid an overlap of IP addresses in the network, assign a completely different pool of IP addresses to the VPN Client (For example, 192.168.10.x).
This requires some routing changes within your network.
About your specific request, If your goal is to handle the Internet traffic through the ASA you might want to configure VPN on a Stick, and you achieve it configuring Hairpining .
E.g
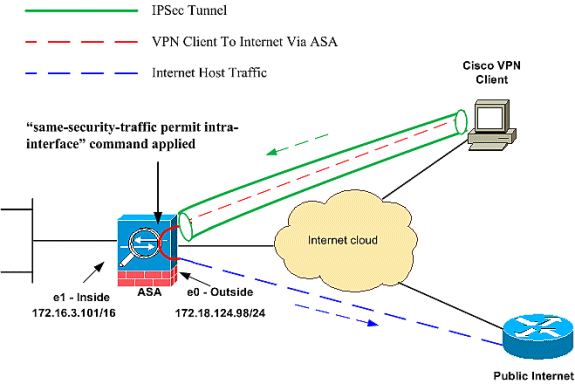
The hairpining feature is useful for VPN traffic that enters an interface but is then routed out of that same interface.
1. same-security-traffic
Use the same-security-traffic command in order to allow traffic to enter and exit the same interface.
securityappliance(config)#same-security-traffic permit intra-interface
2. NAT
The goal is that the traffic coming from the SSL Clients (192.168.10.0) can be translated with an outside IP address (in case you have one available) or the interface itself.
ciscoasa(config)#global (outside) 1 interface
!—Use the interface as the translated IP.
ciscoasa(config)#nat (inside) 1 0.0.0.0 0.0.0.0
!—This translates the inside network to the interface IP.
ciscoasa(config)#nat (outside) 1 192.168.10.0 255.255.255.0
!—This translates the pool network to the interface IP.
The rest is working fine as you described before.
Regards,
Marco Vega
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2011 07:30 PM
ok I got this to work thank you very much using this article and your help.
http://www.cisco.com/en/US/products/ps6496/products_configuration_example09186a008096fcf5.shtml
How can I get access to the LAN inside the ASA? right now all traffic hits the asa and heads to the internet. I know this is some kind of access-list nat statement and I tried the following with the logic of not nating anything that hits the asa from the 192.168.100.0/24 subnet and is headed to the 192.168.0.0/24 subnet. this didn't work and i get destination host unreacheable.
access-list nonatsslclient extended permit ip 192.168.0.0 255.255.255.0 192.168.100.0 255.255.255.0
access-list nonatsslclient extended permit ip 192.168.100.0 255.255.255.0 192.168.0.0 255.255.255.0
nat (outside) 0 access-list nonatsslclient
thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2011 03:54 PM
can anyone help me with this:
How can I get access to the LAN inside the ASA? right now all traffic hits the asa and heads to the internet. I know this is some kind of access-list nat statement and I tried the following with the logic of not nating anything that hits the asa from the 192.168.100.0/24 subnet and is headed to the 192.168.0.0/24 subnet. this didn't work and i get destination host unreacheable.
access-list nonatsslclient extended permit ip 192.168.0.0 255.255.255.0 192.168.100.0 255.255.255.0
access-list nonatsslclient extended permit ip 192.168.100.0 255.255.255.0 192.168.0.0 255.255.255.0
nat (outside) 0 access-list nonatsslclient
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2011 09:57 PM
Base on your original topology diagram:
SSL CLIENT 192.168.0.60/24 ----------- asa -------192.168.0.0/24 inside network
the SSL Client assigned address is in the same subnet as the ASA internal/inside network.
Firstly, you would need to change the SSL Client assigned address to be in a completely unique subnet, let's say 192.168.5.0/24
Then you will need to configure NONAT as per your latest post:
access-list nonat permit ip 192.168.0.0 255.255.255.0 192.168.5.0 255.255.255.0
nat (inside) 0 access-list nonat
Then "clear xlate", and you should be able to access your internal network.
Please also check if your internal hosts have any personal firewall, etc that might block inbound connection from different subnet. Also default gateway is pointing towards the ASA inside interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2011 10:21 PM
I applied everything from Marco Vegas's post with the ip changes and have it working. I applied all the commands in my last post to get access to the LAN inside the ASA and have issues with the destination network missing errors. This is where I need assistance from. Getting all traffic from the remote VPN client to talk to the remote network behind the ASA. Please help with this.
thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2011 12:17 AM
Can you please share the existing ASA config, and which remote subnet you are trying to access from the SSL VPN?
That would help with configuring the correct and exact subnet in the config.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

