- Cisco Community
- Technology and Support
- Security
- VPN
- ASA: Anyconnect single tunnel-group with multiple group-policy setup
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2018 10:09 AM - edited 03-12-2019 04:52 AM
Ok folks,
I have really tried with this and not having any luck. Seems like it should be simple and straight-forward, but for the life of me I am not getting this to work.
I have the ASA setup to authentication via windows NPS/RADIUS. The authentication works just fine. However, when trying to get the group policy selection based on the Class attribute (25), it doesn't work.
I have the tunnel-group:
tunnel-group Remote_Access type remote-access
tunnel-group Remote_Access general-attributes
address-pool Support
authentication-server-group Windows_NPS
default-group-policy GroupPolicy_Remote_Access
tunnel-group Remote_Access webvpn-attributes
group-alias Remote_Access enable
I also have a few group policies:
group-policy NOACCESS internal
group-policy NOACCESS attributes
vpn-simultaneous-logins 0
vpn-tunnel-protocol ikev1 ikev2 ssl-client ssl-clientless
group-policy DfltGrpPolicy attributes
vpn-tunnel-protocol ikev1 ikev2 l2tp-ipsec ssl-client ssl-clientless
group-lock value Remote_Access
group-policy GroupPolicy_Remote_Access internal
group-policy GroupPolicy_Remote_Access attributes
wins-server none
dns-server value ***** *****
vpn-tunnel-protocol ikev2 ssl-client ssl-clientless
group-lock none
default-domain value ******
webvpn
anyconnect profiles value Remote_Access_client_profile type user
group-policy IT internal
group-policy IT attributes
vpn-simultaneous-logins 3
msie-proxy method no-modify
vlan 2206
address-pools value IT
webvpn
anyconnect keep-installer installed
I do get a response from radius:
Radius: Type = 25 (0x19) Class
Radius: Length = 46 (0x2E)
Radius: Value (String) =
4a 74 05 9e 00 00 01 37 00 01 02 00 0a 33 05 18 | Jt.....7.....3..
00 00 00 00 00 00 00 00 00 00 00 00 01 d3 74 b4 | ..............t.
f1 8b 78 75 00 00 00 00 00 0b 5d 3b | ..xu......];
Here is the NPS:
I always get the default group policy and not the one that should match the Class attribute.
is-a-rax01# sh vpn-sessiondb anyconnect
Session Type: AnyConnect
Username : test Index : 56
Assigned IP : ****** Public IP : *******
Protocol : AnyConnect-Parent SSL-Tunnel
License : AnyConnect Essentials, AnyConnect for Mobile
Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)AES256
Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA1
Bytes Tx : 3686 Bytes Rx : 7611
Group Policy : GroupPolicy_Remote_Access
Tunnel Group : Remote_Access
Login Time : 08:24:17 UTC Fri Jan 5 2018
Duration : 0h:00m:17s
Inactivity : 0h:00m:00s
NAC Result : Unknown
VLAN Mapping : N/A VLAN : none
Any ideas?
Thanks,
Marcus
Solved! Go to Solution.
- Labels:
-
Other VPN Topics
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2018 02:03 PM
Interesting. I just tested this in my lab and it worked flawlessly.
ciscoasa# sh vpn-sessiondb anyconnect
Session Type: AnyConnect
Username : rahul Index : 5
Assigned IP : 172.16.50.1 Public IP : 192.168.1.77
Protocol : AnyConnect-Parent SSL-Tunnel DTLS-Tunnel
License : AnyConnect Premium
Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)AES-GCM-256 DTLS-Tunnel: (1)AES256
Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA384 DTLS-Tunnel: (1)SHA1
Bytes Tx : 15358 Bytes Rx : 8940
Group Policy : Test Tunnel Group : VPN
Login Time : 21:59:24 UTC Fri Jan 5 2018
Duration : 0h:00m:42s
Inactivity : 0h:00m:00s
VLAN Mapping : N/A VLAN : none
Audt Sess ID : c0a8010d000050005a4ff53c
Security Grp : none
ciscoasa#
ciscoasa#
ciscoasa# sh run tunnel-group
tunnel-group VPN type remote-access
tunnel-group VPN general-attributes
address-pool VPN-Pool
authentication-server-group NPS LOCAL
default-group-policy GroupPolicy_VPN
tunnel-group VPN webvpn-attributes
group-alias VPN enable
Radius: Type = 25 (0x19) Class
Radius: Length = 46 (0x2E)
Radius: Value (String) =
b3 70 09 8e 00 00 01 37 00 01 02 00 c0 a8 01 01 | .p.....7........
00 00 00 00 0c 90 17 e4 3f 57 fe fe 01 d3 86 6a | ........?W.....j
7d ac 0f b4 00 00 00 00 00 00 00 0f | }...........
Any chance that you are not hitting the right CRP or NP on the NPS server?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2018 10:17 AM
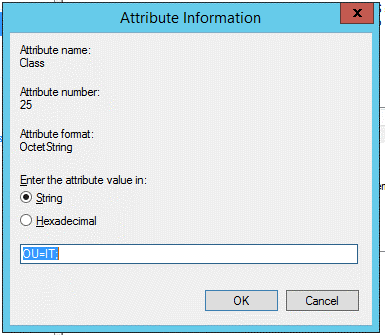
Config looks correct on quick review. Can you try removing the ";" after "OU=IT" on the Class attribute setting?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2018 10:23 AM
I can, but everything that I was reading said that had to be in there. I will try and see what happens.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2018 10:25 AM
I tried with the ; removed. same result.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2018 02:03 PM
Interesting. I just tested this in my lab and it worked flawlessly.
ciscoasa# sh vpn-sessiondb anyconnect
Session Type: AnyConnect
Username : rahul Index : 5
Assigned IP : 172.16.50.1 Public IP : 192.168.1.77
Protocol : AnyConnect-Parent SSL-Tunnel DTLS-Tunnel
License : AnyConnect Premium
Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)AES-GCM-256 DTLS-Tunnel: (1)AES256
Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA384 DTLS-Tunnel: (1)SHA1
Bytes Tx : 15358 Bytes Rx : 8940
Group Policy : Test Tunnel Group : VPN
Login Time : 21:59:24 UTC Fri Jan 5 2018
Duration : 0h:00m:42s
Inactivity : 0h:00m:00s
VLAN Mapping : N/A VLAN : none
Audt Sess ID : c0a8010d000050005a4ff53c
Security Grp : none
ciscoasa#
ciscoasa#
ciscoasa# sh run tunnel-group
tunnel-group VPN type remote-access
tunnel-group VPN general-attributes
address-pool VPN-Pool
authentication-server-group NPS LOCAL
default-group-policy GroupPolicy_VPN
tunnel-group VPN webvpn-attributes
group-alias VPN enable
Radius: Type = 25 (0x19) Class
Radius: Length = 46 (0x2E)
Radius: Value (String) =
b3 70 09 8e 00 00 01 37 00 01 02 00 c0 a8 01 01 | .p.....7........
00 00 00 00 0c 90 17 e4 3f 57 fe fe 01 d3 86 6a | ........?W.....j
7d ac 0f b4 00 00 00 00 00 00 00 0f | }...........
Any chance that you are not hitting the right CRP or NP on the NPS server?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2018 12:07 PM
Your comment about matching the correct policy on the NPS led me to the answer. I was able to track down the fact that the policy wasn't being hit as expected. I found the one that was being matched, copied it, made the modifications to send the class attribute and BAM!!!
Thanks for your help.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide