- Cisco Community
- Technology and Support
- Security
- VPN
- ASA logging to SysLog 'debug crypto ikev2 '(protocol|platform)' 255'?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2023 10:47 AM
I recently enabled logging to a SysLog Server of ALL Event Classes at Severity Level Debug ,
on our FirePower 2110 ASA 9.14(3) ASDM 7.14(1) router .
When I did so on the ASDM, I was informed Logging would no longer be available to Terminal or Console -
that would be OK, since we SHOULD be able to browse the logs created by rsyslog listening on our Linux
SysLog server host.
But now, when I go into the Terminal & enter 'configure terminal' mode, and enter :
...(config)# debug crypto ikev2 protocol 255
...(config)# debug crypto ikev2 platform 255
to temporarily increase ikev2 debugging to its maximum level, which used to include packet payload dumps in the output,
shown on the Terminal / Console , I no longer see any 'crypto' debugs at all in the logs on the SysLog server, and
Terminal/Console debug logging can no longer be enabled since we're redirecting it all to SysLog.
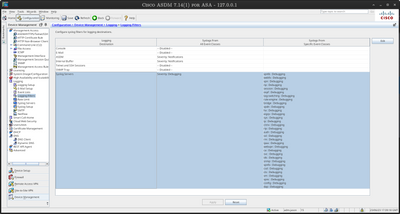
My SysLog filters look like :
I don't see any 'crypto' Event Class.
Any ideas on how to enable ALL crypto IKE debugging with maximum verbosity ,
including packet payload, to a SysLog server would be much appreciated.
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2023 12:54 PM
hostname(config)#logging list vpn-list level debugging class vpn
hostname(config)#logging trap vpn-list
hostname(config)#logging host inside x.x.x.x
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-23-2023
11:05 AM
- last edited on
06-23-2023
09:11 PM
by
rupeshah
![]()
The logging statements in 'running-config.cfg' are :
logging enable
logging timestamp rfc5424
logging emblem
logging buffer-size 16777216
logging asdm-buffer-size 512
logging buffered notifications
logging trap debugging
logging asdm notifications
logging from-address support@xxx
logging recipient-address support@xxx level errors
logging queue 8192
logging host Inside 10.150.2.106 format emblem
logging debug-trace
logging ftp-server 10.150.2.105 /shares/cisco-logs cisco Mountain.Lion49
logging permit-hostdown
logging class auth trap debugging
logging class bridge trap debugging
logging class config trap debugging
logging class ha trap debugging
logging class ids trap debugging
logging class ip trap debugging
logging class np trap debugging
logging class ospf trap debugging
logging class rip trap debugging
logging class rm trap debugging
logging class session trap debugging
logging class snmp trap debugging
logging class sys trap debugging
logging class vpdn trap debugging
logging class vpn trap debugging
logging class vpnc trap debugging
logging class vpnfo trap debugging
logging class vpnlb trap debugging
logging class webfo trap debugging
logging class webvpn trap debugging
logging class ca trap debugging
logging class svc trap debugging
logging class citrix trap debugging
logging class csd trap debugging
logging class ssl trap debugging
logging class eigrp trap debugging
logging class vm trap debugging
logging class dap trap debugging
logging class ipaa trap debugging
logging class cts trap debugging
logging class rule-engine trap debugging
logging class tag-switching trap debugging
When I try to enable extra ikev2 debugging in SSH configure terminal :
asa-vfw1/pri/act(config)# debug crypto ikev2 protocol 255
INFO: 'logging debug-trace' is enabled. All debug messages are currently being redirected to syslog:711001 and will not appear in any monitor session
asa-vfw1/pri/act(config)# debug crypto ikev2 platform 255
INFO: 'logging debug-trace' is enabled. All debug messages are currently being redirected to syslog:711001 and will not appear in any monitor session
and no updates are made to running-config.cfg , and no packet payload / verbose IKEv2 messages appear in the SysLog logs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2023 05:58 AM
logging asdm debug <<- this need
logging asdm-buffer-size 512 <<- increase this buffer
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2023 11:05 AM
I did try 'logging asdm-buffer-size 1024' , but ASDM says the maximum is 512 .
I don't particularly want to log debug messages to ASDM - 'notifications' (emergencies , errors, warnings ) is fine .
I really want only to get the 'debug crypto ikev2 ...' output sent to SysLog - I guess this is not possible ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2023 11:12 AM
logging asdm debug <<-
Did you add this ?
Do that and check log message ID'
Then we can change the level of only these message to upper layer'
But first we need to see the log message.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2023 05:03 AM
Trying to ping an address via the VTI connected linux router fails - here is result of packet trace :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2023 11:35 AM
The above is an example of what I'd like to enable verbose IKEv2 debugging for .
When I did enable it before, with 'logging monitor debuggging' and 'terminal monitor' set ,
I got messages like these displayed :
IKEv2-PROTO-7: (2618): SM Trace-> SA: I_SPI=D74878066B7639C4 R_SPI=1080A8BD31C26812 (R) MsgID = 00000293 CurState: INFO_R Event: EV_TRYSEND
(2618):
IKEv2-PROTO-4: (2618): Sending Packet [To 35.179.23.48:4500/From 62.216.238.169:4500/VRF i0:f0]
(2618): Initiator SPI : D74878066B7639C4 - Responder SPI : 1080A8BD31C26812 Message id: 659
(2618): IKEv2 INFORMATIONAL Exchange RESPONSEIKEv2-PROTO-5: (2618): Next payload: ENCR, version: 2.0 (2618): Exchange type: INFORMATIONAL, flags: RESPONDER MSG-RESPONSE (2618): Message id: 659, length: 80(2618):
Payload contents:
(2618): ENCR(2618): Next payload: NONE, reserved: 0x0, length: 52
(2618): Encrypted data: 48 bytes
(2618):
IKEv2-PROTO-7: (2618): SM Trace-> SA: I_SPI=D74878066B7639C4 R_SPI=1080A8BD31C26812 (R) MsgID = 00000293 CurState: INFO_R Event: EV_CHK_INFO_TYPE
IKEv2-PROTO-7: (2618): SM Trace-> SA: I_SPI=D74878066B7639C4 R_SPI=1080A8BD31C26812 (R) MsgID = 00000293 CurState: INFO_R Event: EV_START_DEL_NEG_TMR
IKEv2-PROTO-7: (2618): Action: Action_Null
IKEv2-PROTO-7: (2618): SM Trace-> SA: I_SPI=D74878066B7639C4 R_SPI=1080A8BD31C26812 (R) MsgID = 00000293 CurState: EXIT Event: EV_CHK_PENDING
IKEv2-PROTO-7: (2618): Sent response with message id 659, Requests can be accepted from range 660 to 660
IKEv2-PROTO-7: (2618): SM Trace-> SA: I_SPI=D74878066B7639C4 R_SPI=1080A8BD31C26812 (R) MsgID = 00000293 CurState: EXIT Event: EV_NO_EVENT
IKEv2-PROTO-7: (2618): SM Trace-> SA: I_SPI=D74878066B7639C4 R_SPI=1080A8BD31C26812 (R) MsgID = 00000292 CurState: EXIT Event: EV_FREE_NEG
IKEv2-PROTO-7: (2618): Deleting negotiation context for peer message ID: 0x292
IKEv2-PROTO-7: (3574): SM Trace-> SA: I_SPI=432BB2F7878DC073 R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_WAIT_INIT Event: EV_RE_XMT
IKEv2-PROTO-4: (3574): Retransmitting packet
(3574):
IKEv2-PROTO-4: (3574): Sending Packet [To 194.80.135.193:500/From 62.216.238.169:500/VRF i0:f0]
(3574): Initiator SPI : 432BB2F7878DC073 - Responder SPI : 0000000000000000 Message id: 0
(3574): IKEv2 IKE_SA_INIT Exchange REQUESTIKEv2-PROTO-5: (3574): Next payload: SA, version: 2.0 (3574): Exchange type: IKE_SA_INIT, flags: INITIATOR (3574): Message id: 0, length: 634(3574):
Payload contents:
(3574): SA(3574): Next payload: KE, reserved: 0x0, length: 232
(3574): last proposal: 0x2, reserved: 0x0, length: 116
Proposal: 1, Protocol id: IKE, SPI size: 0, #trans: 13(3574): last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
(3574): last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: SHA512
(3574): last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: SHA384
(3574): last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: SHA256
(3574): last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: SHA1
(3574): last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA512
(3574): last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA384
(3574): last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA256
(3574): last transform: 0x3, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_521_ECP/Group 21
(3574): last transform: 0x3, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_384_ECP/Group 20
(3574): last transform: 0x3, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_256_ECP/Group 19
(3574): last transform: 0x3, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_1536_MODP/Group 5
(3574): last transform: 0x0, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_1024_MODP/Group 2
(3574): last proposal: 0x0, reserved: 0x0, length: 112
Proposal: 2, Protocol id: IKE, SPI size: 0, #trans: 13(3574): last transform: 0x3, reserved: 0x0: length: 8
type: 1, reserved: 0x0, id: 3DES
(3574): last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: SHA512
(3574): last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: SHA384
(3574): last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: SHA256
(3574): last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: SHA1
(3574): last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA512
(3574): last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA384
(3574): last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA256
(3574): last transform: 0x3, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_521_ECP/Group 21
(3574): last transform: 0x3, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_384_ECP/Group 20
(3574): last transform: 0x3, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_256_ECP/Group 19
(3574): last transform: 0x3, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_1536_MODP/Group 5
(3574): last transform: 0x0, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_1024_MODP/Group 2
(3574): KE(3574): Next payload: N, reserved: 0x0, length: 140
(3574): DH group: 21, Reserved: 0x0
(3574):
(3574): 01 81 84 8f 6b 25 9b f7 b8 88 6b a1 31 de fe b8
(3574): 6a 6d 91 af 12 90 fc 33 89 98 ac 85 4e 8f 38 7c
(3574): 1a be 9b 91 59 f9 94 db a9 11 5e f5 49 21 0f cd
(3574): d7 ac 46 96 ee 87 20 50 aa 50 40 94 02 77 1e af
(3574): 2b 95 01 90 ef a9 66 83 5d 69 a3 64 31 b9 71 87
(3574): cc 77 78 2a 63 9c 80 af 75 e6 50 a6 2a e8 e0 af
(3574): fa 06 38 17 34 61 76 ea 18 37 c6 7f 1d 31 5b 5c
(3574): 46 31 6a 63 dd 72 91 c7 d7 4c cd 55 71 a1 61 45
(3574): 89 58 f9 df
(3574): N(3574): Next payload: VID, reserved: 0x0, length: 68
(3574):
(3574): 74 05 ae 2c 31 e5 c2 d6 f9 cd ca f8 03 67 2a 41
(3574): 4e d7 bf ec bb 2e c1 e6 85 f5 f7 16 e6 d1 d9 ce
(3574): bc 87 50 6b a1 2b e6 6d c6 fa 5d f7 28 da 30 e9
(3574): 69 79 46 be 42 f2 e5 b8 2f ae 60 28 0b 78 4e 9b
(3574): VID(3574): Next payload: VID, reserved: 0x0, length: 23
(3574):
(3574): 43 49 53 43 4f 2d 44 45 4c 45 54 45 2d 52 45 41
(3574): 53 4f 4e
(3574): VID(3574): Next payload: NOTIFY, reserved: 0x0, length: 59
(3574):
(3574): 43 49 53 43 4f 28 43 4f 50 59 52 49 47 48 54 29
(3574): 26 43 6f 70 79 72 69 67 68 74 20 28 63 29 20 32
(3574): 30 30 39 20 43 69 73 63 6f 20 53 79 73 74 65 6d
(3574): 73 2c 20 49 6e 63 2e
(3574): NOTIFY(NAT_DETECTION_SOURCE_IP)(3574): Next payload: NOTIFY, reserved: 0x0, length: 28
(3574): Security protocol id: IKE, spi size: 0, type: NAT_DETECTION_SOURCE_IP
(3574):
(3574): 4c a4 5c 21 7b 78 a0 d3 aa 5c 4b 63 35 a5 91 61
(3574): ba fd dd 96
(3574): NOTIFY(NAT_DETECTION_DESTINATION_IP)(3574): Next payload: NOTIFY, reserved: 0x0, length: 28
(3574): Security protocol id: IKE, spi size: 0, type: NAT_DETECTION_DESTINATION_IP
(3574):
(3574): 62 0c a5 82 14 ea 53 e4 22 ea f2 26 64 11 27 41
(3574): 17 95 7c ae
(3574): NOTIFY(IKEV2_FRAGMENTATION_SUPPORTED)(3574): Next payload: VID, reserved: 0x0, length: 8
(3574): Security protocol id: Unknown - 0, spi size: 0, type: IKEV2_FRAGMENTATION_SUPPORTED
(3574): VID(3574): Next payload: NONE, reserved: 0x0, length: 20
(3574):
(3574): 40 48 b7 d5 6e bc e8 85 25 e7 de 7f 00 d6 c2 d3
(3574):
IKEv2-PROTO-7: (3574): SM Trace-> SA: I_SPI=432BB2F7878DC073 R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_WAIT_INIT Event: EV_NO_EVENT
IKEv2-PROTO-7: (2618): Restarting DPD timer 9 secs
Now that I've enabled debug messages to be sent to a SysLog server, I no longer see them in SysLog output.
I'd really like to get these messages sent to the SysLog server somehow . Any ideas how ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2023 11:39 AM
Are those numbers in parentheses message numbers ?
ie . if I did :
...(config)# logging message 3574 2618 level 7
would they then appear in the log ?
Where could I find a complete list of the 'ikev2 '(protocol|platform)' 255' log message numbers?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2023 12:54 PM
hostname(config)#logging list vpn-list level debugging class vpn
hostname(config)#logging trap vpn-list
hostname(config)#logging host inside x.x.x.x
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2023 01:27 PM
Thank You so much ! It worked ! IKEV2-PROTO messages are now appearing in my SysLog host's log .
I did post above :
logging host Inside 10.150.2.106 format emblem
Several further questions arise :
o How can I inspect the 'vpn-list' I just created ?
(config)# show logging list vpn-list
^
ERROR: % Invalid input detected at '^' marker.
I'd like to create a 'Normal VPN debug logging list' and a 'platform 255' + 'protocol 255' list, and only enable
the latter temporarily when I am investigating issues .
How can I find out which messages are not trapped by the normal 'logging class vpn trap debugging' and
which are trapped by the new vpn-list ?
Much thanks , Best Regards, Jason
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2023 01:32 PM
So just summary topic here
Debug to asdm is work
Debug using vpn-list to syslog server is work
Sorry can you more elaborate your last request.
Thanks
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2023 02:30 PM
Thanks - I just wanted to know how to inspect the contents of that 'vpn-list' , and how it differs from the
messages trapped by 'logging class vpn trap debugging' .
If my running config contains both commands :
logging list vpn-list level debugging class vpn
logging trap vpn-list
logging class vpn trap debugging
Does the second trap override the former ? It would appear so . I guess I should remove 'logging trap vpn-list' from normal
config and only enable temporily when investigating issues.
Thanks once again - best regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-24-2023 02:37 PM
Get it'
First you are so welcome'
For different I will check and update you.
Have a nice weekend
MHM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide