- Cisco Community
- Technology and Support
- Security
- VPN
- ASA Site to Site problem with 10.0.0.0/8 and remote host
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA Site to Site problem with 10.0.0.0/8 and remote host
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2012 01:49 PM
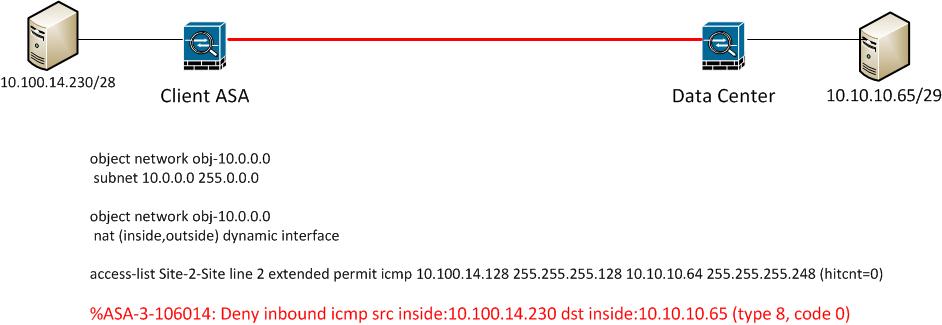
I am trying to configure a site to site VPN from a client ASA to a datacentre ASA
I have configured everything as per the documentation, however I am facing an isssue when trying to ping the remote host, my ping is getting denied on the ASA
%ASA-3-106014: Deny inbound icmp src inside:10.100.14.230 dst inside:10.10.10.65 (type 8, code 0)
Looking at the config of the firewall it appears that the address range 10.0.0.0/8 has been configured for the inside
object network obj-10.0.0.0
subnet 10.0.0.0 255.0.0.0
object network obj-10.0.0.0
nat (inside,outside) dynamic interface
So it is my assumption that the ASA thinks 10.10.10.65 is inside and is not allowing it out.
The fix I believe is to change the 10.0.0.0/8 network object to only reflect the actual inside networks of the client which will then allow this traffic to go out
Or is there anything else I can do?
There is another NAT on the firewall for a client VPN which works fine
nat (inside,outside) source static obj-10.0.0.0 obj-10.0.0.0 destination static vpn_clients vpn_clients route-lookup
The ASA is running 8.4(2)
I am hoping I can just do a no Nat for the remote subnet?
object network DataCenter
subnet 10.10.10.64 255.255.255.248
object network Client
subnet 10.100.14.128 255.255.255.128
access-l Site-2-Site-DataCenter line 1 extended permit ip object Client object DataCenter
access-l Site-2-Site-DataCenter line 2 extended permit icmp object Client object DataCenter
nat (inside,outside) source static Client Client destination static DataCenter DataCenter
Any help is appreciated
Thanks
Roger
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-21-2012 01:51 AM
Hi Roger
I think you can do the following things :
1.make sure that the two ASA have the right route of the VPN traffic . the packets from 10.100.14.230 to 10.10.10.65 should be sent out form the Client ASA outside interface , and the packets fome 10.10.10.65 to 10.100.14.230 should be sent out form the Data Center ASA outside interface . if you config crypto map is on the outside inferface .
2.make sure that , the packets from 10.100.14.230 to 10.10.10.65 should be not NAT in Client ASA , and the packets fome 10.10.10.65 to 10.100.14.230 should be not NAT in the Data Center ASA.
3.make sure that , both ASA have permit the ESP and ISAKMP on the outside ingerface
4.make sure that , the configration in both side is OK
5. make sure that , the PC and the SERVER have the route to each other .
6.BTW you should not do anything about the icmp , as the packets is encrypted by ASA .
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide