- Cisco Community
- Technology and Support
- Security
- VPN
- ASA5505 with two route to ISP public IP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA5505 with two route to ISP public IP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-05-2013 10:31 PM
I have a problem:
One of our sites has a ASA5505, which created several IPSEC vpn.
Now we need to add one public IP into the ASA5505 for the people of that site to access one static IP (or to internet.)
As I am not very familar with the ASA5505, can it be ok to set up 2 public IP? How to do it ?
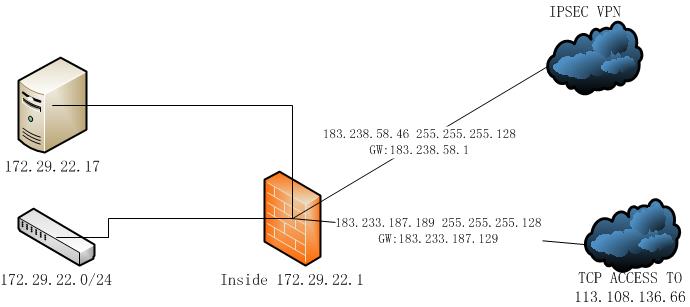
Here is a simple topology for this ASA .
One server need to access one static IP 113.108.136.66, the other IPs in the intranet still keep using the vpn .
Thank you ahead for all of the answers.
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-05-2013 10:42 PM
Are the two public IPs on the same subnet and/or from the same ISP. The only way to use a second IP in that scenario is to NAT the second IP to an address behind the firewall.
If you are connecting to a second ISP, you have to create new VLAN and apply that IP. Then you have to determine what destinations to route over that ISP.
Sent from Cisco Technical Support Android App
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-05-2013 11:21 PM
Hi Mike,
thank you for your reply.
These two IPs are from one fibre but only one RJ45 cable I have.
I think I need to connect a small switch to extend the cables.
In my understand, the related configuration is below
interface vlan3
nameif test
security-level 0
ip address 183.233.187.189 255.255.255.128
Interface Etherenet0/3
switchport access vlan3
no shutdown
global(test) 2 interface
nat(test) 2 172.29.22.77 255.255.255.255
-----------------------
But how to confirm the route ?
route test 113.108.136.66 255.255.255.255 183.233.187.129 1 \\ like this ?
Is it ok for inbond and outbond flow from local ip to remote ip ?
thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-05-2013 11:41 PM
That won't work, you need to NAT to the new IP on the outside interface. Start by deleting the test vlan. Then add the following command.
static (inside, outside) 183.233.187.189 172.29.22.77 netmask 255.255.255.255
As long as that IP block is routed to you, then your existing default gateway will take care of your outbound routing with the new IP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2013 12:06 AM
The gateway is not the same.
I just add the command you given, but it doesn't work.
----------------------------------
D:\Documents and Settings\yuxx>tracert 113.108.136.66
Tracing route to 113.108.136.66 over a maximum of 30 hops
1 * * * Request timed out.
2 * * * Request timed out.
3 * * * Request timed out.
4 * * * Request timed out.
5 * * * Request timed out.
6 * * * Request timed out.
7 * * * Request timed out.
8 * * * Request timed out.
9 * * * Request timed out.
10 * * * Request timed out.
11 * * * Request timed out.
12 * * * Request timed out.
13 * * * Request timed out.
14 * * * Request timed out.
15 * * * Request timed out.
16 * * * Request timed out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2013 12:23 AM
i think you will have to add default route
route test 0.0.0.0 0.0.0.0 gateway
please post the entire configuraiton of the device so that we can help you further.
shine
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2013 12:29 AM
Hi,
here is the configuration
ASA Version 7.2(4)
!
hostname essilorgz
domain-name GZ.essilorchina.com
enable password I/LyDxDkvewgz3kU encrypted
passwd I/LyDxDkvewgz3kU encrypted
names
!
interface Vlan1
nameif inside
security-level 100
ip address 172.29.22.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address 183.238.58.46 255.255.255.128
!
interface Ethernet0/0
speed 100
duplex full
shutdown
!
interface Ethernet0/1
speed 100
!
interface Ethernet0/2
switchport access vlan 2
speed 100
!
interface Ethernet0/3
shutdown
!
interface Ethernet0/4
shutdown
!
interface Ethernet0/5
shutdown
!
interface Ethernet0/6
shutdown
!
interface Ethernet0/7
shutdown
!
ftp mode passive
clock timezone PHST 8
dns server-group DefaultDNS
domain-name GZ.essilorchina.com
same-security-traffic permit intra-interface
object-group network ESSILOR-CORP
network-object 172.16.0.0 255.255.0.0
network-object 172.17.0.0 255.255.0.0
network-object 172.18.0.0 255.255.0.0
network-object 172.19.0.0 255.255.0.0
network-object 172.20.0.0 255.255.0.0
network-object 172.21.0.0 255.255.0.0
network-object 172.24.0.0 255.255.0.0
network-object 172.28.0.0 255.255.0.0
network-object 193.242.7.0 255.255.255.0
network-object 193.242.18.0 255.255.255.0
network-object 193.242.39.0 255.255.255.0
network-object 193.242.40.0 255.255.255.0
network-object 193.242.41.0 255.255.255.0
network-object 193.242.57.0 255.255.255.0
network-object 172.27.0.0 255.255.0.0
network-object 192.168.200.0 255.255.255.0
network-object 193.242.6.0 255.255.255.0
network-object 193.242.9.0 255.255.255.0
network-object 193.242.36.0 255.255.255.0
network-object 192.168.168.0 255.255.255.0
object-group network ESSILOR-APHQ
network-object 172.29.240.0 255.255.255.128
network-object 172.29.240.128 255.255.255.128
network-object 172.29.241.0 255.255.255.0
network-object 172.29.242.0 255.255.255.0
network-object 172.29.243.0 255.255.255.0
network-object 172.29.244.0 255.255.255.0
network-object 172.29.245.0 255.255.255.0
network-object 172.29.246.0 255.255.255.0
network-object 172.29.247.0 255.255.255.0
network-object 172.29.248.0 255.255.255.0
network-object 172.29.249.0 255.255.255.0
network-object 172.29.250.0 255.255.255.0
network-object 172.29.251.0 255.255.255.0
network-object 172.29.252.0 255.255.255.0
network-object 172.29.253.0 255.255.255.0
network-object 172.29.254.0 255.255.255.0
network-object 172.29.255.0 255.255.255.0
network-object 193.242.53.0 255.255.255.0
network-object 193.242.78.32 255.255.255.248
object-group network ESSILOR-SUBS
network-object 172.29.21.0 255.255.255.0
network-object 172.29.23.0 255.255.255.0
network-object 172.29.37.0 255.255.255.0
network-object 172.29.44.0 255.255.255.0
object-group network SUZHYT
network-object 172.29.64.10 255.255.255.255
network-object 172.29.64.11 255.255.255.255
network-object 172.29.64.12 255.255.255.255
network-object 172.29.64.13 255.255.255.255
network-object 172.29.64.14 255.255.255.255
object-group network ESSILOR-CHINA
network-object 172.29.21.0 255.255.255.0
network-object 172.29.44.0 255.255.255.0
object-group network Gmail_IMAP
network-object 216.239.32.0 255.255.255.0
network-object 64.233.160.0 255.255.255.0
network-object 66.249.80.0 255.255.255.0
network-object 72.14.192.0 255.255.255.0
network-object 209.85.128.0 255.255.255.0
network-object 66.102.0.0 255.255.255.0
network-object 64.18.0.0 255.255.255.0
network-object 74.125.0.0 255.255.255.0
network-object 207.126.144.0 255.255.255.0
network-object 209.85.229.0 255.255.255.0
network-object 74.125.0.0 255.255.0.0
network-object 173.194.0.0 255.255.0.0
access-list vpnnonat extended permit ip 172.29.22.0 255.255.255.0 object-group ESSILOR-CORP
access-list vpnnonat extended permit ip 172.29.22.0 255.255.255.0 object-group ESSILOR-APHQ
access-list vpnnonat extended permit ip 172.29.22.0 255.255.255.0 object-group ESSILOR-SUBS
access-list vpnnonat extended permit ip 172.29.22.0 255.255.255.0 172.29.24.0 255.255.255.0
access-list vpnnonat extended permit ip 172.29.22.0 255.255.255.0 object-group SUZHYT
access-list vpnnonat extended permit ip 172.29.22.0 255.255.255.0 172.29.106.0 255.255.255.0
access-list vpnnonat extended permit ip 172.29.22.0 255.255.255.0 172.29.129.0 255.255.255.0
access-list vpnnonat extended permit ip 172.29.22.0 255.255.255.0 172.29.138.0 255.255.255.0
access-list vpnnonat extended permit ip 172.29.22.0 255.255.255.0 172.29.139.0 255.255.255.0
access-list vpnaphq extended permit ip 172.29.22.0 255.255.255.0 object-group ESSILOR-APHQ
access-list vpnaphq extended permit ip 172.29.22.0 255.255.255.0 object-group ESSILOR-CORP
access-list vpnaphq extended permit ip 172.29.22.0 255.255.255.0 172.29.139.0 255.255.255.0
access-list vpnShanghai extended permit ip 172.29.22.0 255.255.255.0 object-group ESSILOR-CHINA
access-list vpnBeijing extended permit ip 172.29.22.0 255.255.255.0 172.29.23.0 255.255.255.0
access-list vpnChengdu extended permit ip 172.29.22.0 255.255.255.0 172.29.37.0 255.255.255.0
access-list vpnbang extended permit ip 172.29.22.0 255.255.255.0 172.29.24.0 255.255.255.0
access-list access_outside extended permit icmp any any echo-reply
access-list access_outside extended permit icmp any any source-quench
access-list access_outside extended permit icmp any any unreachable
access-list access_outside extended permit icmp any any time-exceeded
access-list access_outside extended permit tcp object-group ESSILOR-CHINA 172.29.22.0 255.255.255.0 eq netbios-ssn
access-list access_outside extended permit tcp object-group ESSILOR-CHINA 172.29.22.0 255.255.255.0 eq 137
access-list access_outside extended permit tcp object-group ESSILOR-CHINA 172.29.22.0 255.255.255.0 eq 138
access-list access_inside extended permit ip any 172.29.0.0 255.255.0.0
access-list access_inside extended permit icmp any any
access-list access_inside extended permit tcp any any eq domain
access-list access_inside extended permit udp any any eq domain
access-list access_inside extended permit tcp any any eq telnet
access-list access_inside extended permit tcp any any eq smtp
access-list access_inside extended permit tcp any any eq pop3
access-list access_inside extended permit ip any 193.242.53.0 255.255.255.0
access-list access_inside extended permit ip any 172.16.0.0 255.255.0.0
access-list access_inside extended permit ip any 172.17.0.0 255.255.0.0
access-list access_inside extended permit ip any 172.18.0.0 255.255.0.0
access-list access_inside extended permit ip any 172.21.0.0 255.255.0.0
access-list access_inside extended permit ip any 192.168.0.0 255.255.0.0
access-list access_inside extended permit tcp any any eq https
access-list access_inside extended permit tcp any host 210.51.21.7 eq www
access-list access_inside extended permit tcp host 172.29.22.67 any eq 22223
access-list access_inside extended permit tcp host 172.29.22.106 any
access-list access_inside extended permit tcp any host 210.5.152.18
access-list access_inside extended permit tcp any host 180.168.172.254
access-list access_inside extended permit tcp any host 113.108.136.67 eq 1433
access-list access_inside extended permit tcp any host 113.108.136.67 eq ftp
access-list access_inside extended permit tcp any host 113.108.136.67 eq ftp-data
access-list access_inside extended permit tcp any host 211.156.193.130 eq www
access-list access_inside extended permit tcp any host 203.156.255.122 eq www
access-list access_inside extended permit tcp host 172.29.22.69 any
access-list access_inside extended permit tcp any any eq 7002
access-list access_inside extended permit tcp any any eq 6565
access-list access_inside extended permit tcp host 172.29.22.88 any
access-list access_inside extended permit tcp host 172.29.22.96 any
access-list access_inside extended permit tcp any object-group Gmail_IMAP
access-list access_inside extended permit tcp host 172.29.22.97 any eq www
access-list access_inside extended permit tcp object-group Allow_WWW any eq www
access-list access_inside extended permit tcp any any eq 1433
access-list access_inside extended permit tcp host 172.29.22.12 any eq 7777
access-list access_inside extended permit tcp any any eq 4370
access-list access_inside extended permit tcp host 172.29.22.114 any
access-list access_inside extended permit tcp host 172.29.22.80 any
access-list access_inside extended permit ip any host 117.25.168.214
access-list access_inside extended permit ip any host 113.108.136.66
access-list access_inside extended permit ip host 172.29.22.116 any
access-list vpnsuzhyt extended permit ip 172.29.22.0 255.255.255.0 object-group
SUZHYT
access-list vpsh_wandu extended permit ip 172.29.22.0 255.255.255.0 172.29.106.
255.255.255.0
access-list chengduelec extended permit ip 172.29.22.0 255.255.255.0 172.29.138
0 255.255.255.0
pager lines 24
logging enable
logging asdm informational
mtu inside 1500
mtu outside 1500
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-524.bin
no asdm history enable
arp timeout 14400
global (outside) 1 interface
nat (inside) 0 access-list vpnnonat
nat (inside) 1 0.0.0.0 0.0.0.0
static (inside,outside) 183.233.187.189 172.29.22.77 netmask 255.255.255.255
access-group access_inside in interface inside
access-group access_outside in interface outside
route outside 0.0.0.0 0.0.0.0 183.238.58.1 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
http server enable
http 193.242.53.0 255.255.255.0 inside
http 172.29.22.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set myvpn esp-3des esp-sha-hmac
crypto ipsec transform-set myvpn2 esp-3des esp-md5-hmac
crypto ipsec transform-set remvpn esp-3des esp-md5-hmac
crypto ipsec security-association lifetime seconds 86400
crypto dynamic-map dynmap 5 set transform-set remvpn
crypto map vpnmap 10 match address vpnaphq
crypto map vpnmap 10 set peer 203.126.186.226
crypto map vpnmap 10 set transform-set myvpn2
crypto map vpnmap 20 match address vpnShanghai
crypto map vpnmap 20 set peer 210.13.65.14
crypto map vpnmap 20 set transform-set myvpn2
crypto map vpnmap 30 match address vpnBeijing
crypto map vpnmap 30 set peer 124.65.143.246
crypto map vpnmap 30 set transform-set myvpn2
crypto map vpnmap 40 match address vpnsuzhyt
crypto map vpnmap 40 set peer 58.210.202.114
crypto map vpnmap 40 set transform-set myvpn2
crypto map vpnmap 50 match address vpnbang
crypto map vpnmap 50 set peer 61.8.153.122
crypto map vpnmap 50 set transform-set myvpn2
crypto map vpnmap 60 match address vpsh_wandu
crypto map vpnmap 60 set peer 116.247.86.170
crypto map vpnmap 60 set transform-set myvpn2
crypto map vpnmap 70 match address chengduelec
crypto map vpnmap 70 set peer 221.237.155.102
crypto map vpnmap 70 set transform-set myvpn2
crypto map vpnmap 2000 ipsec-isakmp dynamic dynmap
crypto map vpnmap interface outside
crypto isakmp identity address
crypto isakmp enable outside
crypto isakmp policy 5
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash md5
group 2
lifetime 86400
crypto isakmp policy 65535
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
telnet 172.29.22.0 255.255.255.0 inside
telnet timeout 5
ssh timeout 5
console timeout 0
username misgz password Yc452ckyiSPEPriC encrypted
username admin password EI4G4rgVlvxAhQ5B encrypted
tunnel-group DefaultL2LGroup ipsec-attributes
pre-shared-key *
tunnel-group 203.126.186.226 type ipsec-l2l
tunnel-group 203.126.186.226 ipsec-attributes
pre-shared-key *
isakmp keepalive threshold 300 retry 2
tunnel-group 124.65.143.246 type ipsec-l2l
tunnel-group 124.65.143.246 ipsec-attributes
pre-shared-key *
isakmp keepalive threshold 300 retry 2
tunnel-group 218.6.242.52 type ipsec-l2l
tunnel-group 218.6.242.52 ipsec-attributes
pre-shared-key *
isakmp keepalive threshold 300 retry 2
tunnel-group 61.8.153.122 type ipsec-l2l
tunnel-group 61.8.153.122 ipsec-attributes
pre-shared-key *
isakmp keepalive threshold 300 retry 2
tunnel-group 210.13.72.170 type ipsec-l2l
tunnel-group 210.13.72.170 ipsec-attributes
pre-shared-key *
isakmp keepalive threshold 300 retry 2
tunnel-group 58.210.202.114 type ipsec-l2l
tunnel-group 58.210.202.114 ipsec-attributes
pre-shared-key *
isakmp keepalive threshold 300 retry 2
tunnel-group 116.247.86.170 type ipsec-l2l
tunnel-group 116.247.86.170 ipsec-attributes
pre-shared-key *
isakmp keepalive threshold 300 retry 2
tunnel-group 221.237.155.102 type ipsec-l2l
tunnel-group 221.237.155.102 ipsec-attributes
pre-shared-key *
isakmp keepalive threshold 300 retry 2
tunnel-group 210.13.65.14 type ipsec-l2l
tunnel-group 210.13.65.14 ipsec-attributes
pre-shared-key *
isakmp keepalive threshold 300 retry 2
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:9732e43afd8a0409d5fcea195c880da3
: end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2013 12:49 AM
the configuraiton you have pasted is showing good.
for what is this statment used
static (inside, outside) 183.233.187.189 172.29.22.77 netmask 255.255.255.255
in the diagram it is mentioned has ISP 183.233.187.189/25. it is better to remove this statemnet.
please expalin your requirment in detail.
Shine
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2013 01:08 AM
The configuration is what we are using.
I need to add a route to 113.108.136.66 through 183.223.187.189 as you can see on the diagram.
The server (172.29.22.77) behind the firewall route to 113.108.136.66 through 183.223.187.189.
The 183.223.187.189 is in the same fiber as 183.238.58.46, that means, these two IPs are in the same cable ?
if anything unclear,please tell me.
thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2013 01:26 AM
is ther any particular reason to route 113.108.136.66 through 183.223.187.189 ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2013 01:28 AM
If through the vpn port, the connection may often be down due to the badly ISP network.
So we try another optimization line.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2013 01:55 AM
You need to add an ACL entry inbound on the outside interface explicitly allowing traffic from 113.108.136.66 to 183.223.187.189.
access-list access_outside extended permit ip host 113.108.136.66 host 183.223.187.189
Other than that, the NAT statement looks fine and there is an ACL statement on the inside interface allowing any toward 113.108.136.66.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2013 02:04 AM
Since your old internet connection is not working.
first u need another interface for the ip 183.223.187.189/25
then add route, NAT,Accesslist.
and then u should be able to route traffic which is to 113.108136.66 through 183.223.187.189 which will be ur new internet service.
Shine
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2013 07:46 PM
This doesn't make sense. You want two subnets delivered to you on the same ISP connections. However, you stated that you are doing this because the ISP goes down often. If that is the case, the ISP outage will affect both subnets regardless of routing.
If you still want to proceed, here are my 2 cents.
You cannot have two subnets delivered with different default routes without getting multiple VLAN's from the ISP. This would require a trunk interface on your ASA and you need a security plus license for this to work, and you will need to be assigned VLANs from the ISP.
Without doing VLAN trunking, you can have them route the secondary subnet to you. At that point you can assign that subnet to another VLAN, but it will act like a LAN or DMZ interface. You cannot route out that VLAN to the ISP. You can also refrain from assigning this subnet to an interface and just use IP's from this subnet to NAT to internal IP addresses. The subnet does not actually need to be assigned to the firewall in order to NAT from it, it just needs routed to it. Again, you will not be able to use a gateway on a different subnet than your outside interface.
As a side note, this could be possible on a router using secondary interface IP addresses, but ASAs don't support secondary interface IP addresses.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

