- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Ask Me Anything- VPN Configuration and Troubleshooting on Firepower and ASA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Ask Me Anything- VPN Configuration and Troubleshooting on Firepower and ASA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-03-2019 04:16 PM - edited 02-21-2020 09:44 PM
This topic is a chance to discuss more about the best configuration and troubleshooting practices on Firepower and Adaptive Security Appliance (ASA). The session focuses on solving all queries related to the deployment of VPN on Cisco Firepower and ASA.
To participate in this event, please use the ![]() button below to ask your questions
button below to ask your questions
Ask questions from Wednesday 4th to Friday 20th of September, 2019
Featured Experts

 Puneesh Chhabra is a Technical Consulting Engineer in the Cisco High-Touch Technical Services (HTTS) team. He has total of 10 years of experience in network security. He has delivered multiple trainings on Cisco firewalls and VPN solutions. Prior to joining Cisco, he worked at IBM and HCL as network security consultant. He holds a bachelor of Science degree in IT. He has achieved his CCIE certification in Security. (CCIE Security #30128)
Puneesh Chhabra is a Technical Consulting Engineer in the Cisco High-Touch Technical Services (HTTS) team. He has total of 10 years of experience in network security. He has delivered multiple trainings on Cisco firewalls and VPN solutions. Prior to joining Cisco, he worked at IBM and HCL as network security consultant. He holds a bachelor of Science degree in IT. He has achieved his CCIE certification in Security. (CCIE Security #30128)
Aditya & Puneesh might not be able to answer each question due to the volume expected during this event. Remember that you can continue the conversation on the VPN and AnyConect community.
Find further events on https://community.cisco.com/t5/custom/page/page-id/Events?categoryId=technology-support
**Helpful votes Encourage Participation! **
Please be sure to rate the Answers to Questions
- Labels:
-
AnyConnect
-
Other VPN Topics
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2019 10:11 AM
Hi,
Traditionally, an end-entity that participates in IKE receives a single ID certificate from a CA. The same CA or another CA issues an ID certificate to the peer IKE device. As long as a mutual trust exists between the IKE devices and the CAs, a successful IKE authentication occurs.
An end-entity can receive two certificates from a single CA or from two different CAs, and each of these certificates is used for a unique purpose, such as authentication of two different IKE sessions. The current configuration mechanism fails to provide the required outcome.
The chain validation between multiple subordinate CAs in different Virtual Routing and Forwarding (VRF) tables that lead to a single root-CA also contribute to the complication.
For these reasons, behavior changes have been incorporated into the Cisco IOS in order to make the use of multi-tier PKI hierarchy in IKEv1 feasible.
The two new enhancements include:
- The responder defers the CERT selection until after it processes the MM5 stage, which is when the responder locks the correct ISAKMP profile based on the match identity or match certificate <certificate-map> statement. Now the best match refers to the selection of the first signing certificate from the list of ca trust-point statements under the matched ISAKMP profile.
- The initiator adds the extra security measure while it processes the certificate payload in the MM6 stage, where it authorizes the responder certificate against the certificate map that is configured under the ISAKMP profile.
Could you please provide more details on the type of VPN you're running so I can assist you with the sample configuration.
Regards,
Puneesh
Please share helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2019 01:42 AM
Thak you very much for response. I'm using IPsec tunnel mode.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2019 08:25 PM
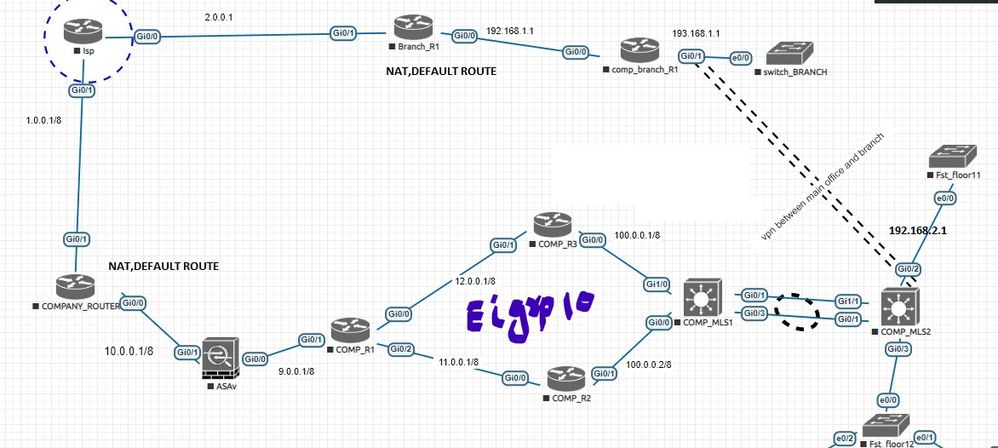
can we establish gre tunnel or vpn between these two LAN i.e 192.168.1.0 and 192.168.2.0 followed by public ip
if its possible then
1 how we can make connectivity between these LAN because there is isp involved and isp just do static ip
2 please provide me the steps to make reach ability i mean 192.168.1.1 can ping to 192.168.2.1 passing throughout isp.
3 I have already configured NAT,DHCP,Default route and redistribute default route in to eigrp.
4 but these can reach me to 2.0.0.2 network and forward of this cannot succes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2019 11:33 PM
Hi Wajib,
We may need to check hop by hop where exactly are the packets being dropped.
Could you share the output of the traceroute command from the source to the destination?
This seems simply a config issue. We may need to ensure proper destination routing is configured on all the intermediate devices or they must be in a state to forward those packets.
If that does not work try taking packet captures on the devices as well. This would help you to understand if the packets are even hitting the ingress interface of that device.
Regards,
Aditya
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-22-2019 06:58 AM
Hi,
What is the packet flow in case of VPN traffic detected and encrypted by ASA/FTD.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2019 04:30 AM
Hi Subin,
There are no major changes except the packet is subjected to crypto engine checks.
If the crypto engine is able to encrypt/decrypt the traffic (depending on the rules) it will forward the packet for normal checks (like L4/L3 checks) but first the packet has to be decrypted to find the actual payload/packet.
Regards,
Aditya
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2019 11:39 PM
Dear @Aditya Ganjoo and @Puneesh Chhabra thank you so much sharing your knowledge and for assisting all queries on this session. Thanks to you many will be able to maintain their business/network secure
- « Previous
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

