- Cisco Community
- Technology and Support
- Security
- VPN
- authentication failed due to retrieving the single sign-on cookie FRP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
authentication failed due to retrieving the single sign-on cookie FRP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2023 03:14 AM
Hello Guys,
i'm currently trying to configure azure MFA on a firepower running version 7.0.4 to authenticate users connecting via vpn.
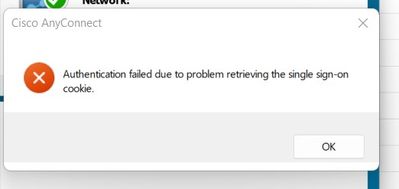
I'm using 5 dedicated connection profiles for each Business unit, i configured MFA on one group and worked correctly, but if i try to configure it on a second group instead i get the error: "authentication failed due to problem retrieving the single sign-on cookie", i'm usign the same single sign on option as per the first connection profile working.
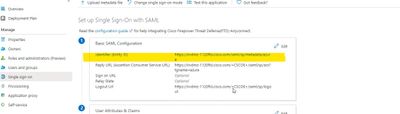
On azure side, I added under the" basic saml configuration " the second connection profile but it doesn't work.
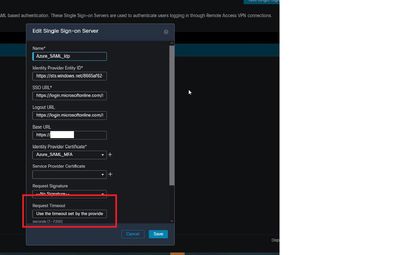
I searched the forum and some users address to this bug https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvi23605 while others report to put "request timeout " of the SSO server option to a blank/empty value but it doesn't seem to work.
is it necessary to open a case?
if it was a configuration problem i would have expected it shouldn't have worked on both connection profiles, instead, it works on one and on the other one it doesn't.
can you confirm that it is possible to enable mfa on multiple connection profiles?
the last aure screenshot is an example, i need to know if i need to add the string for every my connection profile.
thank you
regards
- Labels:
-
AnyConnect
-
Other VPN Topics
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2023 07:00 AM
Hello,
I am facing exactly the same issue in the customer's environment. SAML works fine for first connection profile (with "default" check box marked on Azure side) and second connection profile does not work.
If I move "default" check box mark on the Azure side to second connection profile, second connection profile starts to work, however first one is facing the same issue mentioned above.
Nevertheless, same configuration with multiple connection profiles works fine in my LAB environment.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide