- Cisco Community
- Technology and Support
- Security
- VPN
- AWS IKEv2 with Cisco ASA using Crypto ACL (no VTI)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
AWS IKEv2 with Cisco ASA using Crypto ACL (no VTI)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2022 08:58 AM
Hey, I'm trying to configure a Site to Site on AWS using IKEv2 on my Cisco ASA 9.8, but apparently they want me to add a virtual interface on the ASA.
It's not a big deal, but if I can I'd prefer to avoid.
Did any of you succesfully managed to configure a VPN with them without Route policy?
I configured my ASA with the correct parameters (except the part where you configure the VTI), but only the 1st phase succeeds, the second phase fails.
Jun 30, 2022 @ 15:06:59.000 Local:<my_pub_ip>:500 Remote:<aws_pub_ip>:500 Username:<aws_pub_ip> IKEv2 SA UP. Reason: New Connection Established
Jun 30, 2022 @ 15:07:18.000 Local:<my_pub_ip>:500 Remote:<aws_pub_ip>:500 Username:Unknown IKEv2 Received request to establish an IPsec tunnel; local traffic selector = Address Range: 10.2.xx.252-10.2.xx.252 Protocol: 0 Port Range: 0-65535; remote traffic selector = Address Range: 10.231.xx.111-10.231.xx.111 Protocol: 0 Port Range: 0-65535 Jun 30, 2022 @ 15:07:18.000 Local:<my_pub_ip>:500 Remote:<aws_pub_ip>:500 Username:<aws_pub_ip> IKEv2 Negotiation aborted due to ERROR: Failed to find a matching policy
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2022 09:08 AM
@MarcoLazzarotto I believe you are limited to one IPSec SA with AWS, hence why a VTI is recommended. If you limit a policy based VPN to one SA that will probably work.
The error states "failed to find a matching policy". What crypto, IKE/IPSec Policy, ACL etc configuration have you defined on your ASA?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2022 09:19 AM
@Rob Ingram I eventually find out about this limitation, but I am just allowing a /24 subnet on my side and a /24 subnet on AWS.
Can the fact that my ASA is in HA Active/Standby (full state) cluster be relevant?
Here are my settings:
crypto map Outside_map7 200 set peer <aws_pub_ip> crypto map Outside_map7 200 set ikev2 ipsec-proposal AES256 crypto map Outside_map7 200 set ikev2 pre-shared-key ***** crypto map Outside_map7 200 set security-association lifetime seconds 3600 crypto map Outside_map7 200 set nat-t-disable ---- tunnel-group <aws_pub_ip> type ipsec-l2l tunnel-group <aws_pub_ip> general-attributes default-group-policy Amazon-AWS-Lab tunnel-group <aws_pub_ip> ipsec-attributes isakmp keepalive threshold 10 retry 10 ikev2 remote-authentication pre-shared-key ***** ikev2 local-authentication pre-shared-key ***** ---- tunnel-group <aws_pub_ip> type ipsec-l2l tunnel-group <aws_pub_ip> general-attributes default-group-policy Amazon-AWS-Lab tunnel-group <aws_pub_ip> ipsec-attributes isakmp keepalive threshold 10 retry 10 ikev2 remote-authentication pre-shared-key ***** ikev2 local-authentication pre-shared-key ***** --- access-list Outside_cryptomap_208 extended permit ip 10.2.xxx.0 255.255.255.0 object Amazon-AWS-Lab
The IPsec proposal is
crypto ipsec ikev2 ipsec-proposal AES256 protocol esp encryption aes-256 protocol esp integrity sha-1 md5
And the IKEv2 policy (which I created to match the exact lifetime period)
crypto ikev2 policy 50 encryption aes-256 integrity sha384 group 19 prf sha384 lifetime seconds 28800
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2022 02:05 PM
No active standby firewall is not relevent. as mentioned above as long as you have (one subnet at your end and one subnet on remote end) you are good to use the policy based vpn.
in regarding to failed to find a mataching policy could you confrim the AWS is setup with same parameter the one you defiine on your firewall.
what are the acl and NAT rules. have you called in the object local and object remote in acl and in Nat as (Nat exemption)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2022 01:55 AM - edited 07-01-2022 01:57 AM
@Sheraz.Salim wrote:what are the acl and NAT rules. have you called in the object local and object remote in acl and in Nat as (Nat exemption)
NAT exempt is this:
nat (Inside,Outside) 116 source static NETWORK_OBJ_10.2.xx.0_24 NETWORK_OBJ_10.2.xx.0_24 destination static Amazon-AWS-Lab Amazon-AWS-Lab no-proxy-arp route-lookup description NAT Exempt for Amazon AWS
ACL is
access-list Amazon-AWS-Lab extended permit tcp object Amazon-AWS-Lab object-group DM_INLINE_TCP_7 10.2.199.0 255.255.255.0 access-list Amazon-AWS-Lab extended permit icmp object Amazon-AWS-Lab 10.2.199.0 255.255.255.0
The DM_INLINE_TCP_7 contains protocols http and https
I checked again the phase 1 and 2 parameters and looks fine.
EDIT: should I put anything here?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2022 03:17 AM
I do not see you calling your access-list in your "crypto map Outside_map7 200" can you confirm you have crypto acl defined in your config.
You need to define you access-list as
access-list AWS-VPN extended permit ip Object NETWORK_OBJ_10.2.xx.0_24 Object Amazon-AWS-Lab
and crypto map should be like this
crypto map Outside_map7 200 set peer <aws_pub_ip> crypto map Outside_map7 200 set ikev2 ipsec-proposal AES256 crypto map Outside_map7 200 set ikev2 pre-shared-key ***** crypto map Outside_map7 200 match address AWS-VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2022 05:06 AM - edited 07-01-2022 05:25 AM
You are correct, I don't know why I trimmed that line from my second post
My actual Crypto Map
crypto map Outside_map7 200 match address Outside_cryptomap_208 crypto map Outside_map7 200 set pfs group19 crypto map Outside_map7 200 set peer <aws_pub_ip> crypto map Outside_map7 200 set ikev2 ipsec-proposal AES256 AES256B AES192 crypto map Outside_map7 200 set ikev2 pre-shared-key <psk> crypto map Outside_map7 200 set security-association lifetime seconds 3600 crypto map Outside_map7 200 set nat-t-disable
My access-list associated witht the cryto map
access-list Outside_cryptomap_208 extended permit ip 10.2.xx.0 255.255.255.0 object Amazon-AWS-Lab
EDIT
If it can help, yesterday during the final step of the wizard, the ASDM showed me the classic box with all the commands, and then I remember that I could have clickled again on Finish and this time it proposed to me a smaller list of commands (creation of another crypto map), and I thought that it was just a bug, but now this makes me think that I may be missing a part of the vpn.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2022 09:34 AM
The "Failed to find a matching policy" would suggest that the crypto params are not matching between the ASA and AWS, below the last line you shared on the logs it would show you which are the received and expected policies. If you are a 100% sure you configure the same settings, try please to move the crypto IKEv2 policy from 50 to be the first one on the list.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-05-2022 01:51 AM
Thank you all for the help.
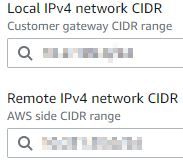
My only mistake was to invert the local and remote subnet on AWS (I thought that Local was referred to AWS and Remote was referred to my on-prem subnet)
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide