- Cisco Community
- Technology and Support
- Security
- VPN
- Can't ping sub interface gateways from my remote site VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-04-2012 09:28 AM
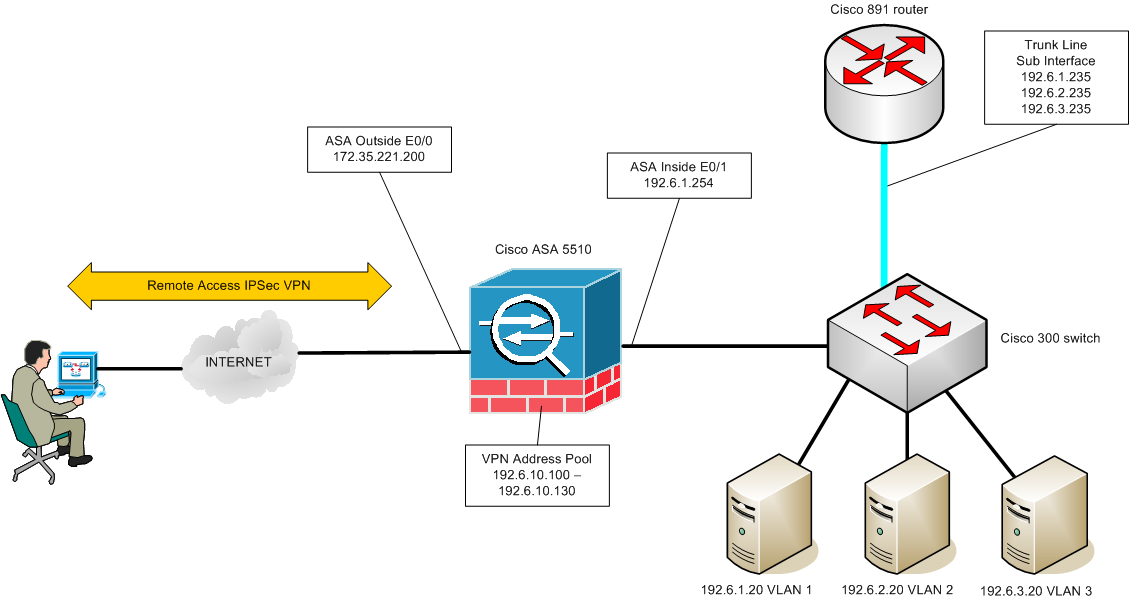
I cannot ping my sub interface gateways from my remote vpn connection
I can ping 192.6.1.0 network, but cannot ping 192.6.2.0 or 192.6.3.0 networks
When I remote desktop to 192.6.1.20 I can ping all networks including the sub interface gateways.
I believe something in my asa is incorrectly setup or not added
ASA NAT Rules:
Exempt NAT Interface: Inside
Source 192.6.0.0/16
Destination 192.6.10.96/27
Static NAT Interface: Inside (this is for local NAT from outside E0/0)
Source 192.6.1.1/16
Translated interface outside Destination: 172.35.221.200
Dynamic NAT Interface: Inside
Source: Any
Destination:Outside
ASA Access Rules:
Outside Permit
Source: Any
Destination: outside
Services: udp, tcp, tcp/http
Static Routes:
Interface:Outside > Network: any to outside DSL(doesn't show DSL in graphic)
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-05-2012 09:31 PM
Few incorrect configuration:
On the ASA:
1) Routes are incorrect, the default route should point to the next hop, ie: the internet router: 172.35.221.x, as follows:
route outside 0.0.0.0 0.0.0.0 172.35.221.x
---> where x should be the internet router interface ip address.
the existing routes should be removed:
no route outside 0.0.0.0 0.0.0.0 192.298.47.182 255
no route outside 0.0.0.0 0.0.0.0 172.35.209.81 tunneled
2) The following static NAT statement is incorrect too and should be removed:
static (inside,outside) USSLTA01_External USSLTA01 netmask 255.255.255.255
--> You can't NAT the interface on the ASA itself.
3) Subnet mask for the ASA inside interface should be 255.255.255.0, not 255.255.0.0. It should be the same as the router interface subnet mask:
interface Ethernet0/1
nameif inside
security-level 100
ip address 192.6.1.254 255.255.255.0
4) Route to access those sub interfaces subnet on the ASA as follows:
route inside 192.6.2.0 255.255.255.0 192.6.1.235
route inside 192.6.3.0 255.255.255.0 192.6.1.235
route inside 192.6.4.0 255.255.255.0 192.6.1.235
On the router, should configure default route as follows:
ip route 0.0.0.0 0.0.0.0 192.6.1.254
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-04-2012 10:52 PM
Can you ping the VLAN interface on the switch from the remote VPN?
Do you have route on the ASA for those VLAN?
Those VLANs have route for the remote vpn pool subnet?
Can you pls share the ASA and router config.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-05-2012 07:13 PM
Jennifer ,
- I cannot ping the VLAN interface from the remote VPN. I can ping all VLAN interfaces if I remote desktop via VPN to 192.6.1.20 server.
- I do not have a route for thoes VLANS on the ASA (need help there - attached files)
- do not have routes for the remote VPN pool( need help there- attached files)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-05-2012 09:31 PM
Few incorrect configuration:
On the ASA:
1) Routes are incorrect, the default route should point to the next hop, ie: the internet router: 172.35.221.x, as follows:
route outside 0.0.0.0 0.0.0.0 172.35.221.x
---> where x should be the internet router interface ip address.
the existing routes should be removed:
no route outside 0.0.0.0 0.0.0.0 192.298.47.182 255
no route outside 0.0.0.0 0.0.0.0 172.35.209.81 tunneled
2) The following static NAT statement is incorrect too and should be removed:
static (inside,outside) USSLTA01_External USSLTA01 netmask 255.255.255.255
--> You can't NAT the interface on the ASA itself.
3) Subnet mask for the ASA inside interface should be 255.255.255.0, not 255.255.0.0. It should be the same as the router interface subnet mask:
interface Ethernet0/1
nameif inside
security-level 100
ip address 192.6.1.254 255.255.255.0
4) Route to access those sub interfaces subnet on the ASA as follows:
route inside 192.6.2.0 255.255.255.0 192.6.1.235
route inside 192.6.3.0 255.255.255.0 192.6.1.235
route inside 192.6.4.0 255.255.255.0 192.6.1.235
On the router, should configure default route as follows:
ip route 0.0.0.0 0.0.0.0 192.6.1.254
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2012 04:36 AM
Thanks Jennifer,
I am showing just a section of the network, so the routes need to be in place ( good catch)
I installed iproute: ip route 0.0.0.0 0.0.0.0 192.6.1.254 within the router and all worked.
Thanks for all you assistance and direction.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

