- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Can two AnyConnect connection profiles use the same SAML IdP?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Can two AnyConnect connection profiles use the same SAML IdP?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2019 07:02 AM - edited 02-21-2020 09:45 PM
I would like have my two connection profiles "DefaultWEBVPNGroup" and "Azure_MFA" use SAML authentication. And I have already configured both certificates in the ASA. But I just realized in the SAML idp, I only can configure one "trustpoint idp" to unique tunnel group profile...
My question is how to make both Anyconnect profiles use SAML authentication at the same time? Thanks!
Webvpn
Saml idp https://sts.windows.net/******/
url sign-in https://login.microsoftonline.com/****/
url sign-out https://login.microsoftonline.com/***/
trustpoint idp <tunnel-group name>
trustpoint sp ASDM_TrustPoint1
no force re-authenticate
no signature
base-url https://.....
- Labels:
-
AnyConnect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2022 03:22 AM
Hi did you ever get a resolution for this as we are hitting the same issue ?
Damian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2022 02:39 PM
Hi @groupccologin,
Yes, you can use same IdP within multiple tunnel groups.
What is wrong in the initial statement here is that for the "trustpoint idp" command, you are supposed to use trustpoint containing certificate used in Azure application, not the tunnel-group.
You can find great configuration guide here.
BR,
Milos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2023 01:11 AM - edited 02-20-2023 02:28 AM
Hello @Milos_Jovanovic ,
is there a guide to to the same on a firepower via GUI?
furthermore the "trustpoint sp ASDM_TrustPoint1" is mandatory or i just can use the "trustpoint idp" [IdP Trustpoint]?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2023 06:49 AM
Hi guys,
I have found the solution. It is not on the VPN side.
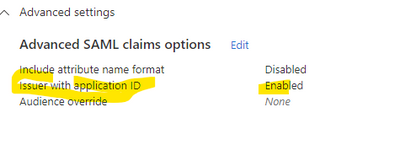
There is a function on Azure SAML, by enabling "Advanced SAML claims options" - "Append application ID to issuer" under the VPN profile,
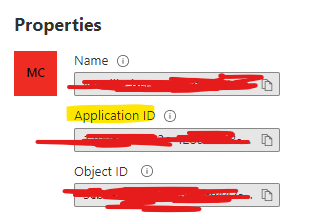
You can have "Application ID" under Properties. On ASA, you can use saml idp + Application ID looks like this,
webvpn
saml idp https://sts.windows.net/{{ idp }}/{{ Application ID }}
So you can create multiple profiles for SAML auth by using different application IDs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2023 07:16 AM
Hello Lina,
can you post a screen regarding the azure side?
i would like to use only one saml idp an more than one connection profile on the firepower
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2023 05:42 PM
Hi Lina,
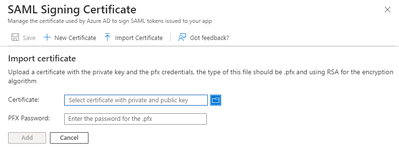
What certificate should the second enterprise application will use? Is it possible to use the same SAML certificate from the first enterprise application? If yes, can you share me how? I downloaded the .cer file from the first application but when I try to upload it on the second application, it is asking for .pfx file and a password.
Please share to me your workaround with regards to SAML certificate on both applications. Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2023 11:18 AM
Regarding this, I just downloaded the certificate for the new application and uploaded it in the ASA and used it under saml idp configuration for my backup VPN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2023 12:57 AM
I implemented this solution and it worked! Thanks @lina.cao !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-27-2023 04:57 AM
@lina.cao @aumali We are facing the same scenario in our product where we have multiple Tunnel Groups in ASA for Cisco Anyconnect and we have a Single Azure tenant where multiple Enterprise Application is set up for each tunnel group. When I configured the SAML IDP using the "saml idp https://sts.windows.net/{{ idp }}/{{ Application ID }}" method on ASA it took that config however when I tried accessing the Anyconenct for that Tunnel group I got the error "Authentication failed due to problem retrieving the single sign-on cookie" after entering my Azure credentials on the Client machine.
Not sure how it's working for you guys.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-27-2023 09:45 AM - edited 09-27-2023 09:57 AM
Hi @aaggarwal23 , Can you provide below information ?
1.ASA version
2.Are you using same certificate ( used for signing assertion ) on Azure for those multiple Enterprise Application or you are leaving it default ?
3.Would you be able to enable below debug ,replicate the issue and provide the outputs
debug webpvn saml 255
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-27-2023 10:05 AM - edited 09-27-2023 10:06 AM
Hi @aaggarwal23
You need to enable "Append application ID to issuer" on Attributes & Claims > Advanced SAML claims options on both Azure Enterprise application where the VPN is enabled (see screenshot from @lina.cao on 02-20-2023 07:56 AM)
Also make sure both certificates are uploaded in ASA. Configure two tunnel groups, two saml IDPs, and two VPN URLs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2023 05:52 AM
@aumali Thanks for your prompt reply.
I am able to get it through after enabling the above option in Azure also there was an issue with the SAML idp configuration I have done where in the URL after putting Application ID I mistakenly added / in the end. I removed it and it started working fine as expected.
Thanks for your help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2024 04:52 AM - edited 06-20-2024 06:41 AM
lina.cao is right.
After a lot of debugging I could implement this solution, even with the DefaultWEBVPNGroup and a 2nd group which only uses a different group-url (no tunnel-group alias is used, and no 'tunnel-group-list enable' under the webvpn config is used).
Be careful, there are a few things you should take a closer look:
- The option 'Append application ID to issuer' must be enabled only in the 2nd,3rd ... group. Not in the first one which uses the normal identity string
- In the webvpn config. the saml idp line hast to end with a '/' in the normal/first group like 'saml idp https://sts.windows.net/{{ idp }}/'
- The other groups which use the format saml idp https://sts.windows.net/{{ idp }}/{{ Application ID }} are NOT allowed to use a '/' at the end
- The Reply URL in Azure has to use the tunnel-group name also (the Pattern hint in the webinterface is confusing) like:
https://my-asa-domain/+CSCOE+/saml/sp/acs?tgname=my-tunnel-group
- Do not use the group-url path (for example /my-tunnel-group) in the base-url config. under webvpn, only the FQDN (https://my-asa-domain)
- Do not use the group-url in the Identifier (Entity ID) or Reply URL in Azure
I also implemented a solution with a 3rd party SSL cert. importet into every AnyConnect Enterprise App - and into the (single) ASA webvpn idp config.
I had some issues with specifi self singed ssl cert. (some key lengths are not allowed - error when trying to import the .pkcs12).
But in general this solution works too to use several VPN / Tunnel-Groups with Azure SAML MFA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2023 07:56 AM
enable application ID under Attributes & Claims, see below,
then you can get application ID under "Overview"
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide