- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Cisco AnyConnect authentication via AD group (Realm)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco AnyConnect authentication via AD group (Realm)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2020 03:17 PM
Hello,
We have 3 ASAs (Cisco ASA 5516-X Theat Defense 6.2.3.4) administered by an FMC.
Users connect to VPN via Cisco AnyConnect, by Active Directory authentification.
We want to allow connection only for an AD group. Currently, all domain users can authenticate on Cisco AnyConnect and this is a security issue. The initial configuration of Cisco AnyConnect is complete (ipv4 Pool, certifcates …).
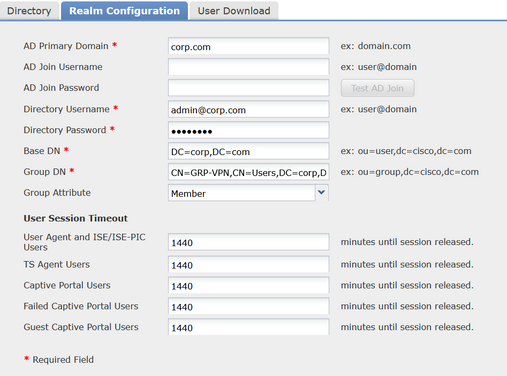
We have a Realm setup with our AD servers :
Our AD base looks like :
DC=corp,DC=com
And we want to allow connection only for this AD group : CN=GRP-VPN,CN=Users,DC=corp,DC=com
Can you explain the procedure to us?
Thank you in advance for your help
- Labels:
-
AnyConnect
-
Remote Access
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2020 05:43 PM
Do you use ISE in your environment? Its the easiest and best way to set this up what you are trying to achieve.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2020 05:05 AM
Hello,
No we do not use ISE.
I did not find a tutorial to restrict Cisco AnyConnect VPN login based on AD Group with AD Realm.
Regards.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide