- Cisco Community
- Technology and Support
- Security
- VPN
- Cisco Anyconnect CLI ignore server certificate
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco Anyconnect CLI ignore server certificate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2016 08:00 AM - edited 02-21-2020 08:44 PM
Hello,
I'm using Cisco AnyConnect CLI and i've come across a question. Cisco AnyConnect ui has an option to "Connect anyway" to the server with the untrusted VPN certificate, but CLI drops such connection anyway.
The question is:
is there any way to "Connect anyway" in CLI? Maybe a flag?
- Labels:
-
AnyConnect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-31-2016 10:08 AM
Hi,
The option you are talking about is a certificate warning generated by the SSL parent tunnel negotiation the AnyConnect client does with the firewall, if the ASA dose not have a trusted certificate for the client on the outside interface you will see the message. This process is called strict certificate checking and if this passes there should be no warning presented.
With this said, I'm unsure what you mean by the CLI not accepting this connection. If you are taking about the CLI of the ASA then this would be normal telnet or SSH connection to the BOX not SSL. so unless you are doing some sort of RSA authentication for your SSH sessions there should e no certificate involvement here and you may just have an issue with your SSH/Telnet configuration.
Can you be more explicit with what you are having issues with?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-31-2016 10:08 AM
Hello, William,
Thank you for quick response.
When i try to connect to VPN using Cisco Anyconnect graphical user interface i get this message

So i have an option to connect anyway, despite certificate problems.
But when i try to connect to the same server from terminal in Linux using command line interface
/cisco/anyconnect/bin/vpn connect *someserver*
the connection drops anyway and no choice (connect anyway or cancel connection) is available.
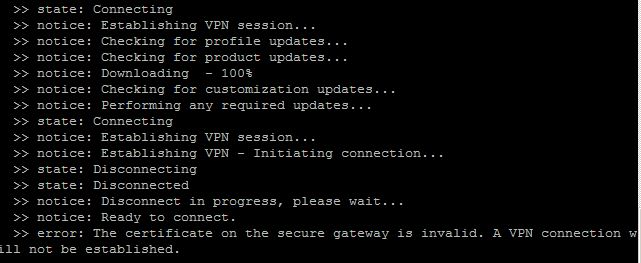
The question is:
Is there any way to avoid this error while connecting from the terminal?
Maybe some kind of flag, e.g. \anyconnect\vpn connect --force *some server*
My search endeavors failed so far
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2016 09:35 AM
Hi,
The error message you see is not really an error it is a warning, which is why, when using the AnyConnect client, you can connect either though you were presented with the error.
Nos this certificate warning happens due to the normal SSL negotiation, this can be avoided by using a certificate on the outside interface of the ASA. There are 3 ways you can do yhis:
1. Purchase a public certificate from a CA (certificate authority) like Verisign, GoDadday, Entrust, etc and install it on the outside interface of the firewall, you can find the process on how to request one here:
http://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-next-generation-firewalls/107956-renew-ssl.html
2. Use company issues certificates if you own an internal PKI server, enroll the ASA and install the certificate and apply it on the interface. The clients must have the CA certificate on their machine to see this certificate as trusted.
1. Create a self signed certificate on the ASA and apply it, you will have to manually install the certificate on all your PCs in the trusted certificate directory for them to see it as trusted, (unsure of the Linux process for this though).
This is the process for the clients connecting with SSL to see the ASA as a secure gateway and stop the warning message.
Now, as for the Linux CLI I'm unsure if this will clear the problem since I'm unsure what it is your are trying to do.
Hope this helps.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide