- Cisco Community
- Technology and Support
- Security
- VPN
- Cisco Anyconnect FQDN and certificates
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2020 07:08 AM - edited 02-21-2020 09:51 PM
I've recently setup and configured a Cisco ASA 5508. The Anyconnect VPN works fine, users can login and can access resources in the network. The only problem I keep getting that I want to fix is the certificate warning. Users have to enter the IP address of the firewall instead of a FQDN connecting to the firewall via the Anyconnect client. How can I configure my firewall so it pushes a FQDN instead of an IP address and stops giving off the certificate warnings?
Solved! Go to Solution.
- Labels:
-
AnyConnect
-
Remote Access
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2020 08:51 AM
If you're set on going down the no-public-DNS service you could always modify the hosts file on clients to include the FQDN to IP address mapping. The client will check a local hosts file and prefer that over anything in (or absent in) the configured DNS resolver.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2020 07:12 AM
You would need to register the FQDN with your external provider, the FQDN must resolve to the IP address of the ASA. The FQDN would need to match the common name (CN) defined in the certificate.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2020 08:11 AM
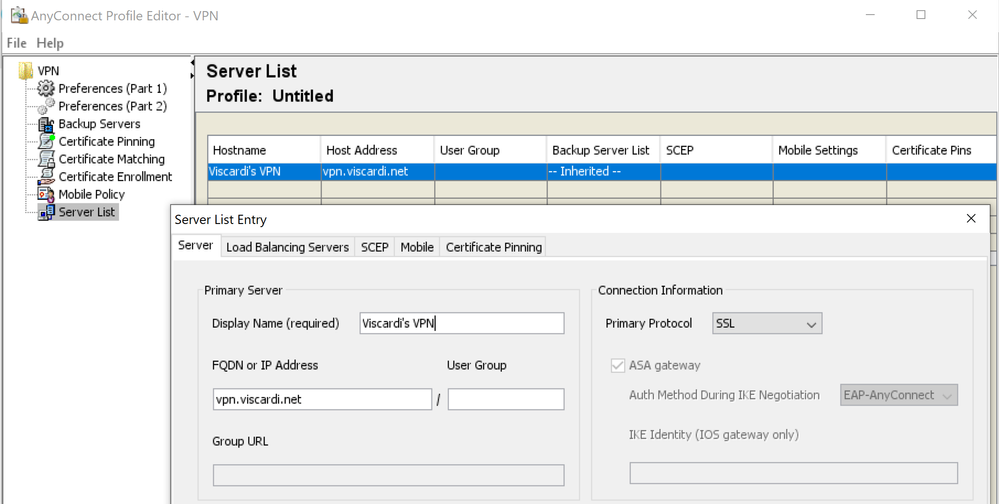
In addition to what @Rob Ingram said, you should also use the AnyConnect profile editor (within ASDM or as standalone application) to create a VPN profile that will be pushed to users upon login. In it you can define both the FQDN and a more user-friendly name for the VPN. Something like this:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2020 07:43 AM
Thanks for the reply, I will look into getting a FQDN and matching the self-signed certificate CN so it matches the FQDM. Just a quick question on how self signing works, my boss is asking why don't we just use a self-signed certificate and why doesn't just work, like why do I need to map a FQDN to the CN of the certificate in order to stop getting the errors.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2020 07:28 PM
You will continue to get certificate warnings even with FQDN matching the CN in the certificate if you use self-signed certificate. That is unless you go into each client and tell it to trust the appliance as a root CA. (very laborious and generally not an effective solution beyond the lab)
The reason is because that's fundamentally how PKI works - clients only automatically trust a presented certificate if:
1. The issuing Certificate Authority (CA) is trusted and
2. The Common Name (CN) in the certificate matches the Fully Qualified Domain Name (FQDN) of the site being accessed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2020 01:58 AM - edited 02-18-2020 06:19 AM
Hello Marvin,
Thanks for the quick reply. So in order to fully fix in problem, I will need to export the self-signed certificate (with the correct CN that matches the FQDN) and install into the clients devices, and setup a FQDN that matches the public IP address of my ASA?
Or do I even need to register a FQDN with a domain name register, can I just put the public IP address in the certificate CN? As currently the users just put the ASA's public IP address in the anyconnect client.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2020 06:18 AM
If you want to go the self-signed route, a client can save the certificate by browsing to the VPN headend. If the self-signed certificate has the FQDN and the URL is publicly resolvable, there's no need to include the IP address as a Subject Alternative Name (SAN) in the certificate. Just make sure to have a VPN profile that pushes the FQDN down to clients upon connect.
It would be very unusual and contrary to the purpose of DNS to use the IP address only and not have a public FQDN. the only times I've seen that done is when the admin is trying to obfuscate the existence of the VPN or just doing it temporarily for a lab or testing and doesn't
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2020 06:34 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2020 08:51 AM
If you're set on going down the no-public-DNS service you could always modify the hosts file on clients to include the FQDN to IP address mapping. The client will check a local hosts file and prefer that over anything in (or absent in) the configured DNS resolver.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2020 04:34 AM
I've managed to get it running using the local host file, thank you very much for your help.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide