- Cisco Community
- Technology and Support
- Security
- VPN
- Cisco AnyConnect - Hostname / certificate mismatch
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2015 02:32 AM - edited 02-21-2020 08:25 PM
Hello!
I have had Cisco AnyConnect up and running with a self signed certificate for a few months now.Yesterday, I bought a SSL Plus certificate for connect.norsar.no from DigiCert, installed this to my Cisco ASA 5505 and assigned the certificate to the AnyConnect profile.
Device Management > Certificate Management > Identity Certificates > Install (connect.norsar.no.cert)
Device Management > Certificate Management > CA Certificates > Add (DigiCertCA.cert)
Remote Access VPN > AnyConnect Connection Profiles > Device Certificate
Removed the old self signed certificate.
When launching Cisco AnyConnect Secure Mobility Client with hostname 'connect.norsar.no', I get the connection up and running and the certificate works fine.
The second time - and consequtive times - I start the AnyCnnect client, the hostname in the client GUI is displayed as 'connect (IPsec) IPv4'. When I try to connect, I get a warning saying that this is an untrusted VPN server and the connection is blocked. See attachment.
I know I can turn off 'Block connections from untrused servers' via the tools menu, but this is not a good solution. If I set the hostname explicitly to connect.norsar.no in the user preferences file Users\xxx\AppData\Local\Cisco\Cisco AnyConnect Secure Mobility Client\preferences.xml all works well, but I do not want to instruct my users to do this...
I need to know why the client replaces hostname 'connect.norsar.no' with 'connect (IPsec) IPv4'. I'm not able to find references to this anywhere...
Suggestions are very welcome.
BR,
Nils
Solved! Go to Solution.
- Labels:
-
AnyConnect
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2015 04:41 AM
Hello norsar,
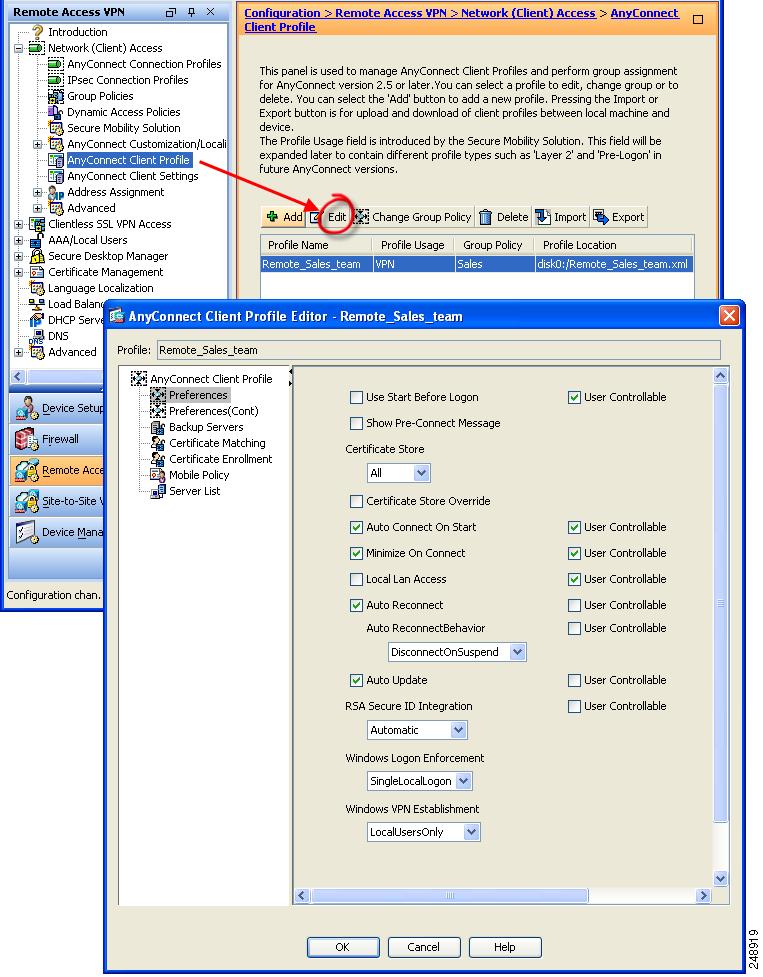
The reason it changes the display name from FQDN to connect (IPsec) IPv4 is because you might not have anyconnect profile correctly configured for the users.
You are on the right path by modifying the preferences.xml but this will get override once the configuration is pushed from the ASA. Thus , you can edit the client profile form the ASA and then you would not need to make changes on the client.
Please make sure the new certificate is not only installed , it is also applied on the outside interface.
Make sure you remove the older command and add it with correct trustpoint (which has the new certificate)
no ssl trust-point <trustpoint name of old certificate> outside
ssl trust-point <trustpoint name of new certificate> outside
For modifying the client profile:-
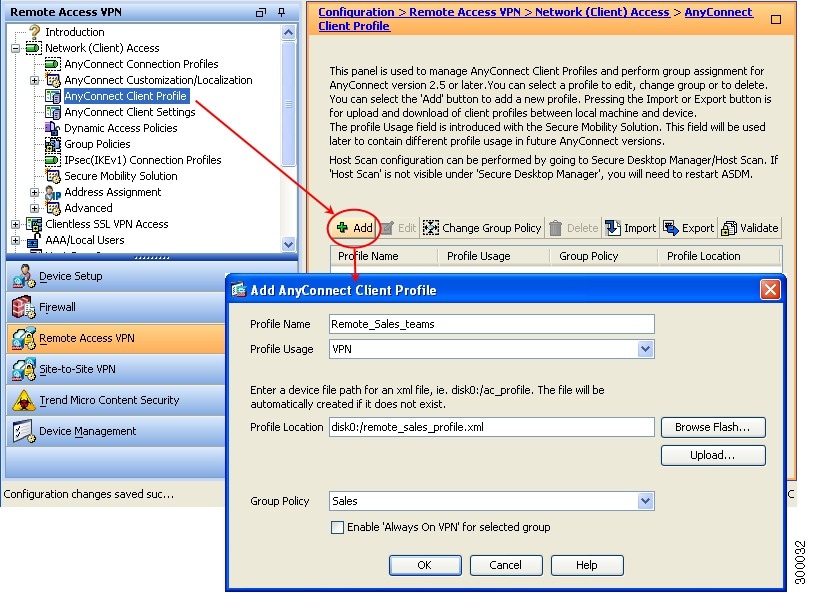
Go to Configuration> Remote Access VPN > Anyconnect Profile >
Name the profile.
Associate this anyconnect profile with the group policy assigned to the users.
You will be able to see “server list” option.
Just click on Server List, then click on ADD. Fill in the hostname of the firewall where you have “Hostname(required)” and “Host Adress” options.
Click on OK and save the configuration.
Once the profile is pushed , AnyConnect users will be able to see the hostname of the firewall and can enter the username and password to connect to the firewall.
Ref: http://www.cisco.com/c/en/us/td/docs/security/vpn_client/anyconnect/anyconnect30/administration/guide/anyconnectadmin30/ac02asaconfig.html#pgfId-1111773
Regards,
Dinesh Moudgil
P.S. Please rate helpful posts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2015 04:41 AM
Hello norsar,
The reason it changes the display name from FQDN to connect (IPsec) IPv4 is because you might not have anyconnect profile correctly configured for the users.
You are on the right path by modifying the preferences.xml but this will get override once the configuration is pushed from the ASA. Thus , you can edit the client profile form the ASA and then you would not need to make changes on the client.
Please make sure the new certificate is not only installed , it is also applied on the outside interface.
Make sure you remove the older command and add it with correct trustpoint (which has the new certificate)
no ssl trust-point <trustpoint name of old certificate> outside
ssl trust-point <trustpoint name of new certificate> outside
For modifying the client profile:-
Go to Configuration> Remote Access VPN > Anyconnect Profile >
Name the profile.
Associate this anyconnect profile with the group policy assigned to the users.
You will be able to see “server list” option.
Just click on Server List, then click on ADD. Fill in the hostname of the firewall where you have “Hostname(required)” and “Host Adress” options.
Click on OK and save the configuration.
Once the profile is pushed , AnyConnect users will be able to see the hostname of the firewall and can enter the username and password to connect to the firewall.

Ref: http://www.cisco.com/c/en/us/td/docs/security/vpn_client/anyconnect/anyconnect30/administration/guide/anyconnectadmin30/ac02asaconfig.html#pgfId-1111773
Regards,
Dinesh Moudgil
P.S. Please rate helpful posts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2015 04:54 AM
Problem solved. Thanks Dinesh Moudgil!!
BR,
Nils
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide