- Cisco Community
- Technology and Support
- Security
- VPN
- Cisco ASA 5545 IPv6 SSL VPN query
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco ASA 5545 IPv6 SSL VPN query
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2014 12:28 AM
Hi,
we are planning to migrate out network to IPv6 standard. Preferably Dual Stack.
Currently we enabled SSL VPN using Anyconnect client, where the VPN users will get connected with the ASA 5545 and then able to access the internal network. We are planning to enable dual stack in the outside interface of ASA and the Internal network will remain in IPV4 network.
A user with IPv6 IP need to access the IPv4 internal network using the SSL vpn (the IP address assigned to Anyconnect interface will be an IPv4 address.).
Currently the ASA version is 8.0(4) .
my query is, what are the things i need to consider prior to the migration.
1) Which ASA software version will support IPv6 SSL VPN using Anyconnect Client ( Please note, we don't need IPSec)
2) Similarly which Anyconnect Client will support IPv6 SSL connection.
3) What could be the best practice for this kind of deployment.
Kindly help.
Any helpful answers will be appreciated.
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2014 01:42 AM
You should consider going for at least ASA 9.0:
- New NAT config
- Unified IPv6 and IPv4 ACLs.
If you want basics:
- ASA IPv6 with failover you need 8.2.2
- ASA IPv6 VPN you need 9.0
- Anyconnect IPv6 you need 3.0 (but there is no reason not to run 3.1)
FYI, all this info can be found in release notes
http://www.cisco.com/c/en/us/support/security/asa-5500-series-next-generation-firewalls/products-release-notes-list.html
http://www.cisco.com/c/en/us/support/security/anyconnect-secure-mobility-client/products-release-notes-list.html
As for best practices, there's not much to it, it should work, it's just a different transport and overlay tech.
Scan the configuration guides for limitations, there's not too many but you should make sure it's not a show stopper for you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2014 01:12 AM
Hi Marcin,
Thanks alot... pls help me to clear these doubts.... please refer the diagram.
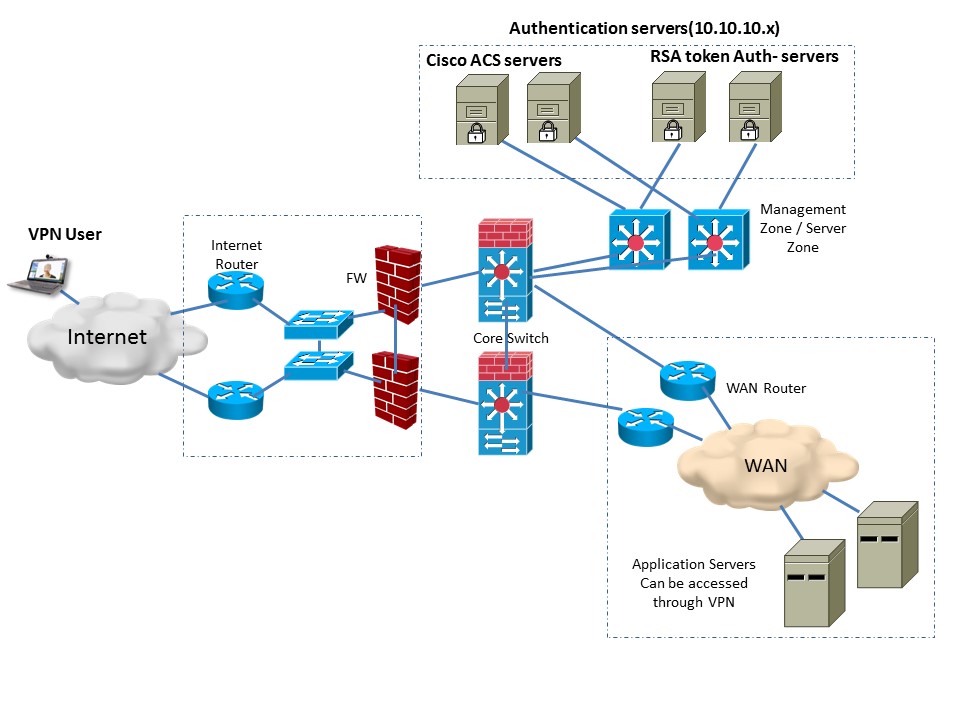
Current Scenario
IPv6 scenario
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2014 05:49 AM
The ASA-> Authentication server flow in SSL VPN is separate TCP/UDP from connectivity between client and headend. ASA will take the credentials and pass them to corresponding server(s).
From ASA's perspective you configure pools, IPv4, IPv6, or both to determine what you're like to assign, it may happen that the client does not support some of the protocols. As long as the OS supports it you should be able to assign IPv6 and IPv4 and use it accordingly.
ASA 9.0 and Anyconnect 3.1 the minimum you should consider for IPv6 deployment. (this includes connectivity with IPv6 and failover).
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide