- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Cisco ipsec site to site vpn not showing results ?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2019 06:06 AM - edited 02-21-2020 09:38 PM
Hello , the last 3 days i have been struggling with ipsec configuration on cisco routers here is my topology on gns 3
both sites can ping with each other but without encryption

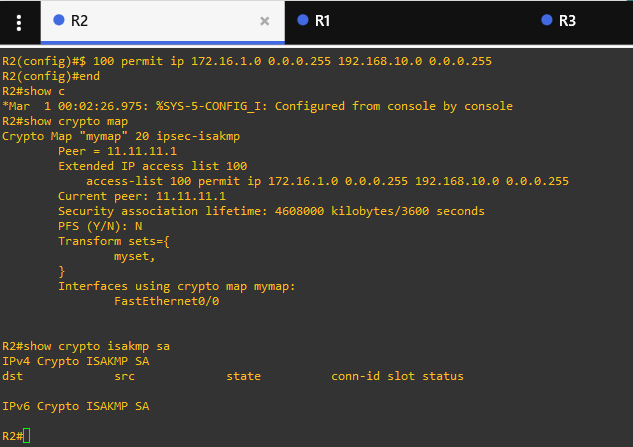
this is the ipsec configuration


and whech i chek the ecryption i always got nothing with
#R2 show crypto isakmp sa
neither with
#R2 show crypto ipsec sa
( 0 pkt enc/dec )

#R2 debug crypto isakmp
or
#R2 debug crypto isakmp
"debugging is on" with no results too
Solved! Go to Solution.
- Labels:
-
IPSEC
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2019 08:46 AM
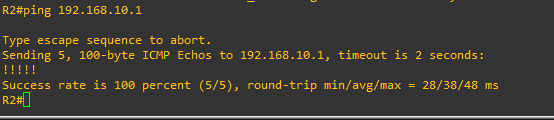
Are you definitely pinging from the correct source interface?
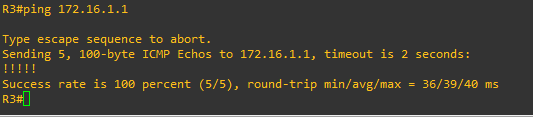
On R3 router > ping 192.168.10.1 source fas 0/1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2019 06:11 AM
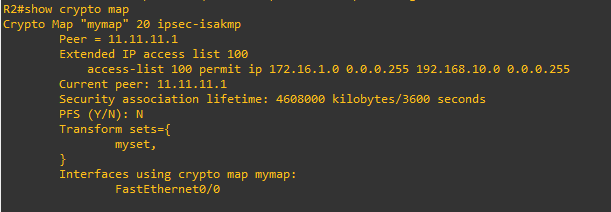
The ACL 100 on R2 is incorrect, it has the destination network of 192.168.1.0/24 not 192.168.10.0/24, therefore it does not mirror the configuration of the other router and will fail. Modify the ACL and try again.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2019 06:35 AM
I fixed the ACL but i still have the same issue with
show crypto ipsec sa
show crypto isakmp sa
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2019 06:39 AM - edited 05-13-2019 06:51 AM
Please post the full configuration of both routers
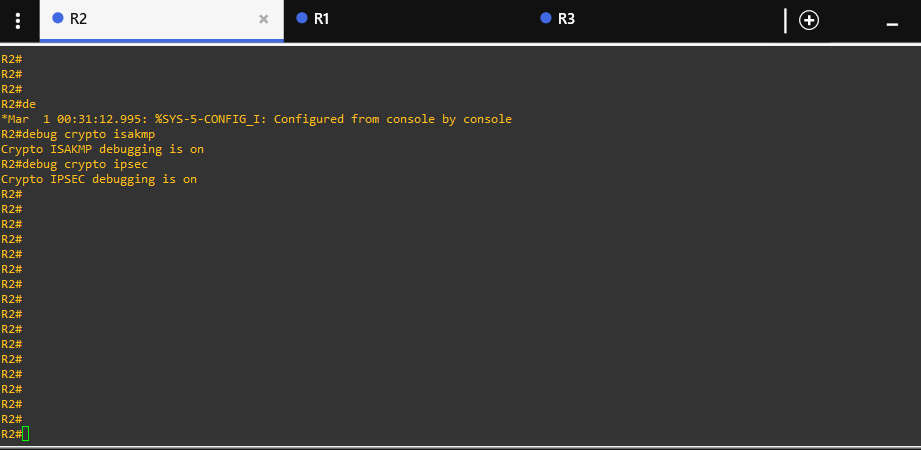
Also enabled debugging "debug crypto isakmp" and upload the output of the debug
Are you generating some traffic in order to bring up the tunnel? The VPN will not establish until interesting traffic is generated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2019 07:02 AM
R2 configuration:
R2(config)#int f0/0
R2(config-if)# ip address 10.10.10.1 255.255.255.0
R2(config-if)# no sh
R2(config-if)# ex
R2(config)#int f0/1
R2(config-if)# ip address 172.16.1.1 255.255.255.0
R2(config-if)# no sh
R2(config-if)# ex
R2(config)# ip route 0.0.0.0 0.0.0.0 10.10.10.2
R2(config)# crypto isakmp enable
R2(config)#crypto isakmp policy 20
R2(config-isakmp)#authentication pre-share
R2(config-isakmp)#encryption 3des
R2(config-isakmp)#hash md5
R2(config-isakmp)#group 1
R2(config-isakmp)#lifetime 3600
R2(config-isakmp)#exit
R2(config)#crypto isakmp key cisco123 address 11.11.11.1
R2(config)#crypto ipsec transform-set myset esp-3des esp-md5-hmac
R2(config)#acess-list 100 permit ip 172.16.1.0 0.0.0.255 192.168.10.0 0.0.0.255
R2(config)#crypto map mymap 20 ipsec-isakmp
R2(config-crypto-map)#set peer 11.11.11.1
R2(config-crypto-map)#set transform-set myset
R2(config-crypto-map)#exit
R2(config)#int f0/0
R2(config-if)# crypto map mymap
R3 configuration:
R3(config)#int f0/0
R3(config-if)# ip address 11.11.11.1 255.255.255.0
R3(config-if)# no sh
R3(config-if)# ex
R3(config)#int f0/1
R3(config-if)# ip address 192.168.10.1 255.255.255.0
R3(config-if)# no sh
R3(config-if)# ex
R3(config)# ip route 0.0.0.0 0.0.0.0 11.11.11.2
R3(config)# crypto isakmp enable
R3(config)#crypto isakmp policy 20
R3(config-isakmp)#authentication pre-share
R3(config-isakmp)#encryption 3des
R3(config-isakmp)#hash md5
R3(config-isakmp)#group 1
R3(config-isakmp)#lifetime 3600
R3(config-isakmp)#exit
R3(config)#crypto isakmp key cisco123 address 10.10.10.1
R3(config)#crypto ipsec transform-set myset esp-3des esp-md5-hmac
R3(config)#acess-list 100 permit ip 192.168.10.0 0.0.0.255 172.16.1.0 0.0.0.255
R3(config)#crypto map mymap 20 ipsec-isakmp
R3(config-crypto-map)#set peer 10.10.10.1
R3(config-crypto-map)#set transform-set myset
R3(config-crypto-map)#exit
R3(config)#int f0/0
R3(config-if)# crypto map mymap
debug isn't working i got this everytime i try
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2019 07:16 AM
Run a ping on one of the router to the destination network, make sure you define the correct source interface, that matches the ACL.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2019 07:43 AM - edited 05-13-2019 07:43 AM
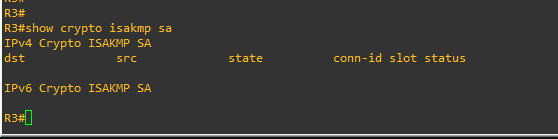
even after i pinged R2 to R3 nothing changed still got the same issue and i dont think the problem is related to no exchaged traffic because i think the IKE phase 1 isn't established yet since this command show no active SA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2019 07:58 AM
I assume the routers can ping each other?
Do you have nat configured? If so you will need deny traffic from the local network to the remote network.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2019 08:05 AM
yeah each router ping the other
but how can i check about the NAT config ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2019 08:08 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2019 08:17 AM
R1 configuration
R2(config)#int f0/0
R2(config-if)# ip address 10.10.10.2 255.255.255.0
R2(config-if)# no sh
R2(config-if)# ex
R2(config)#int f0/1
R2(config-if)# ip address 11.11.11.2 255.255.255.0
R2(config-if)# no sh
R2(config-if)# ex
R2(config)# ip route 172.16.1.0 255.255.255.0 10.10.10.1
R2(config)# ip route 192.168.10.0 255.255.255.0 11.11.11.1
-------------------------------------------------------------------
R2 configuration
R2(config)#int f0/0
R2(config-if)# ip address 10.10.10.1 255.255.255.0
R2(config-if)# no sh
R2(config-if)# ex
R2(config)#int f0/1
R2(config-if)# ip address 172.16.1.1 255.255.255.0
R2(config-if)# no sh
R2(config-if)# ex
R2(config)# ip route 0.0.0.0 0.0.0.0 10.10.10.2
R2(config)# crypto isakmp enable
R2(config)#crypto isakmp policy 20
R2(config-isakmp)#authentication pre-share
R2(config-isakmp)#encryption 3des
R2(config-isakmp)#hash md5
R2(config-isakmp)#group 1
R2(config-isakmp)#lifetime 3600
R2(config-isakmp)#exit
R2(config)#crypto isakmp key cisco123 address 11.11.11.1
R2(config)#crypto ipsec transform-set myset esp-3des esp-md5-hmac
R2(config)#acess-list 100 permit ip 172.16.1.0 0.0.0.255 192.168.10.0 0.0.0.255
R2(config)#crypto map mymap 20 ipsec-isakmp
R2(config-crypto-map)#set peer 11.11.11.1
R2(config-crypto-map)#set transform-set myset
R2(config-crypto-map)#exit
R2(config)#int f0/0
R2(config-if)# crypto map mymap
--------------------------------------------------------------
R3 configuration:
R3(config)#int f0/0
R3(config-if)# ip address 11.11.11.1 255.255.255.0
R3(config-if)# no sh
R3(config-if)# ex
R3(config)#int f0/1
R3(config-if)# ip address 192.168.10.1 255.255.255.0
R3(config-if)# no sh
R3(config-if)# ex
R3(config)# ip route 0.0.0.0 0.0.0.0 11.11.11.2
R3(config)# crypto isakmp enable
R3(config)#crypto isakmp policy 20
R3(config-isakmp)#authentication pre-share
R3(config-isakmp)#encryption 3des
R3(config-isakmp)#hash md5
R3(config-isakmp)#group 1
R3(config-isakmp)#lifetime 3600
R3(config-isakmp)#exit
R3(config)#crypto isakmp key cisco123 address 10.10.10.1
R3(config)#crypto ipsec transform-set myset esp-3des esp-md5-hmac
R3(config)#acess-list 100 permit ip 192.168.10.0 0.0.0.255 172.16.1.0 0.0.0.255
R3(config)#crypto map mymap 20 ipsec-isakmp
R3(config-crypto-map)#set peer 10.10.10.1
R3(config-crypto-map)#set transform-set myset
R3(config-crypto-map)#exit
R3(config)#int f0/0
R3(config-if)# crypto map mymap
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2019 08:23 AM
E.g:-
crypto map mymap 20 ipsec-isakmp
match address 100
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2019 08:29 AM
i forget to write "match address 100" here in this post but i did included it on R2 and R3 crypto map settings as u can see from this ss
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2019 08:32 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2019 08:39 AM
Building configuration...
Current configuration : 1346 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R2
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
no ip icmp rate-limit unreachable
ip cef
!
!
!
!
no ip domain lookup
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
archive
log config
hidekeys
!
!
crypto isakmp policy 20
encr 3des
hash md5
authentication pre-share
lifetime 3600
crypto isakmp key cisco123 address 11.11.11.1
!
!
crypto ipsec transform-set myset esp-3des esp-md5-hmac
!
crypto map mymap 20 ipsec-isakmp
set peer 11.11.11.1
set transform-set myset
match address 100
!
!
!
ip tcp synwait-time 5
!
!
!
!
interface FastEthernet0/0
ip address 10.10.10.1 255.255.255.0
duplex auto
speed auto
crypto map mymap
!
interface FastEthernet0/1
ip address 172.16.1.1 255.255.255.0
duplex auto
speed auto
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 10.10.10.2
!
!
no ip http server
no ip http secure-server
!
access-list 100 permit ip 172.16.1.0 0.0.0.255 192.168.10.0 0.0.0.255
no cdp log mismatch duplex
!
!
!
!
!
!
control-plane
!
!
!
!
!
!
!
!
!
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
line vty 0 4
login
!
!
end
R2#
R2#
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide