- Cisco Community
- Technology and Support
- Security
- VPN
- I tried. The echo gets to
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 10:06 AM
Hello everyone,
i am trying to setup a Site to Site VPN between a branch site and the main campus. i am using the latest cisco packet tracer version since i do not physically have the ASA. Here below my network topology.
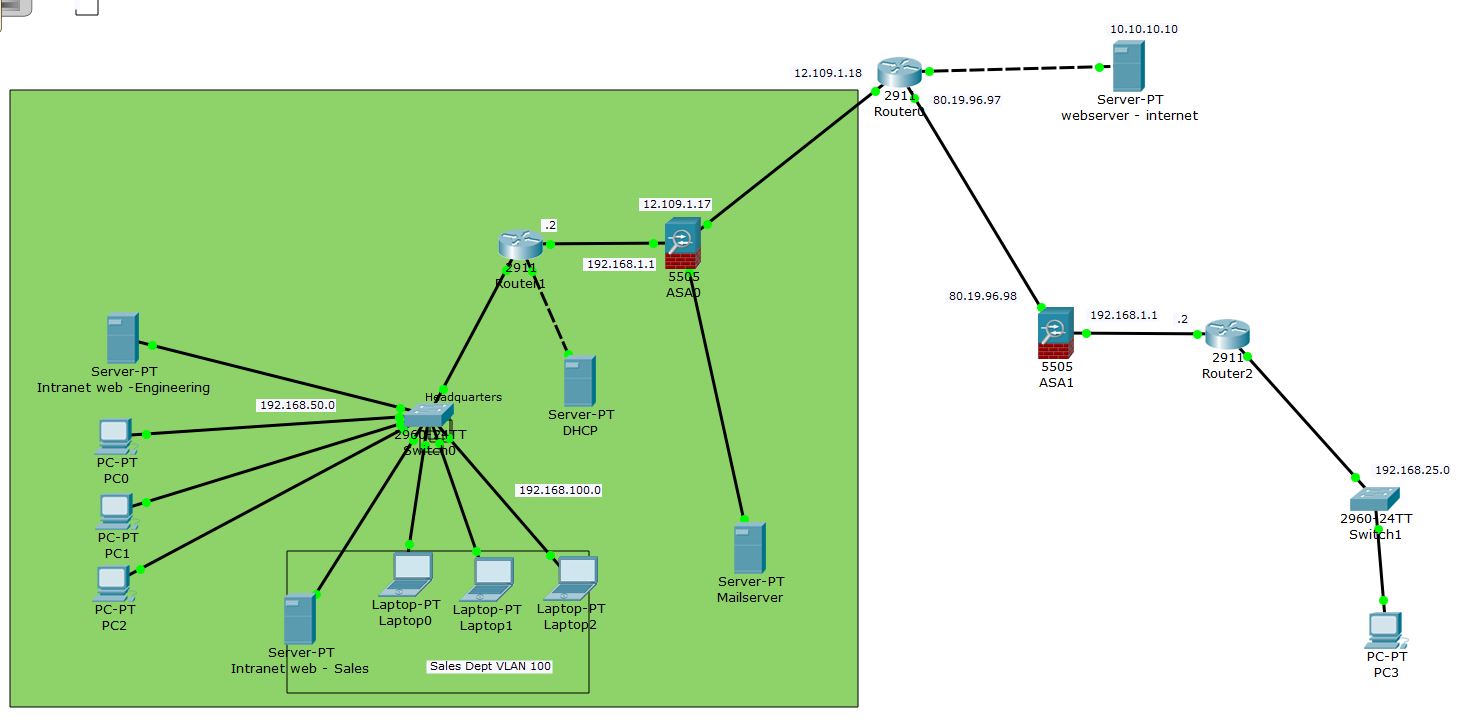
i have configured the VPN, but i cannot understand why the tunnel does not come up. Also i do not have most of the tools (like packet-tracer) from this cli version.
Can you help me ?
i am attaching the configuration of the 3 routers and the ASAs.
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 01:16 PM
Yes you need to add the following commands
On Router 1:-
ip access-list extented NAT
deny ip 192.168.50.0 0.0.0.255 192.168.25.0 0.0.0.255
permit ip 192.168.50.0 0.0.0.255 any
!
no ip nat inside source list 1 interface GigabitEthernet0/2 overload
ip nat inside source list NAT interface GigabitEthernet0/2 overload
!
On Router 2,
ip access-list extented NAT
deny ip 192.168.25.0 0.0.0.255 192.168.50.0 0.0.0.255
permit ip 192.168.25.0 0.0.0.255 any
!
no ip nat inside source list 1 interface GigabitEthernet0/2 overload
ip nat inside source list NAT interface GigabitEthernet0/2 overload
and check that VPN tunnel is working after changes or not.
Please rate this if it is helpful or marked as correct if you get you answer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 10:21 AM
Hi David,
Are you able to ping ASA1 outside interface from ASA0 ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 10:25 AM
Yes sir, i can. Both ways.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 10:45 AM
Try continuous ping from any device in 192.168.50.x to any device in 192.168.25.x subnet and on ASA0 enter the command "debug crypto ikev1 25" and check are you see any output in console.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 11:47 AM
I tried. The echo gets to destination, but the icmp reply gets dropped when entering ASA0:
1. The receiving port has an inbound traffic access-list with an ID of permit_icmp. The device checks the packet against the access-list.
2. The packet matches the criteria of the following statement: permit icmp any any. The packet is permitted.
3. The packet is coming from an outside network. The device looks up its NAT table for necessary translations.
4. The NAT table does not have a matched entry for this packet. It passes the packet through without translations.
5. The device looks up the destination IP address in the CEF table.
6. The CEF table has an entry for the device to receive this packet. The device dispatches the packet to the upper layer.
7. The packet is an ICMP packet. The ICMP process processes it.
8. The ICMP process received an Echo Reply message.
9. The ICMP process has not sent an ICMP message with this identification recently. It drops the message.
Im not really sure what this means. Also "debug crypto ikev1 25" is not available on Packet tracer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 12:28 PM
Can you please post the "show crypto ikev1 sa" and "show crypto ipsec sa" outputs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 12:33 PM
Ok so i understood the ping error i was getting. It was 2 to the router natting the packet before reaching the ASA.
Basically the ASA was not seeing meaningful traffic in order to create the tunnel.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 01:16 PM
Yes you need to add the following commands
On Router 1:-
ip access-list extented NAT
deny ip 192.168.50.0 0.0.0.255 192.168.25.0 0.0.0.255
permit ip 192.168.50.0 0.0.0.255 any
!
no ip nat inside source list 1 interface GigabitEthernet0/2 overload
ip nat inside source list NAT interface GigabitEthernet0/2 overload
!
On Router 2,
ip access-list extented NAT
deny ip 192.168.25.0 0.0.0.255 192.168.50.0 0.0.0.255
permit ip 192.168.25.0 0.0.0.255 any
!
no ip nat inside source list 1 interface GigabitEthernet0/2 overload
ip nat inside source list NAT interface GigabitEthernet0/2 overload
and check that VPN tunnel is working after changes or not.
Please rate this if it is helpful or marked as correct if you get you answer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 02:20 PM
First of all thanks, i forgot to remove certain destination from being NATted.
The tunnel still doest not come up.
I see the ISAKMP and IPsec packets between the ASAs, but when i try to ping i get:
1. The routing table finds a routing entry to the destination IP address.
2. The destination network can be reached via 192.168.50.50.
3. The device decrements the TTL on the packet.
4. The packet is going from an inside to an outside network. The device looks up its NAT table for necessary translations.
5. The NAT table does not have a matched entry for this packet. It passes the packet through without translations.
6. The traffic is interesting traffic and needs to be encrypted and encapsulated in IPSec PDUs.
7. The insteresting traffic can not be encrypted, IKE (ISAKMP) needs to negotatiate IPSec SAs.
on ASA 1 i show:
There are no IKEv1 SAs
There are no IKEv2 SAs
On ASA0 i show:
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 80.19.96.98
Type : L2L Role : responder
Rekey : no State : MM_SA_SETUP
There are no IKEv2 SAs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 03:40 PM
Working!
Thanks for your support!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2017 02:33 AM
Glad to hear :-). Thanks for rating
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2018 07:42 AM
Can you send me the .pkt file?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide