- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Cisco Secure Client CVE-2024-20337
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco Secure Client CVE-2024-20337
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2024 06:49 AM
Following upgrading to upgrading to 5.1.2.42 to fix the vulnerability CVE-2024-20337
Within Microsoft Defender this is still flagged as vulnerability for the CVE
It appears to refer to a component of the install:
C:\Program Files (x86)\Cisco\Cisco Secure Client\acsocktool.exe\acsocktool.exe
Cisco secure Client Socket Filter Tool v5.1.2.22
Question is if this version is covers the vulnerability why is a component still being flagged as a vulnerability?
Thanks
- Labels:
-
AnyConnect
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2024 04:21 AM
Also seeing this which is killing our secure score.
According to this Stack Overflow article it's for "DNS proxying. App/transparent proxying. Content filtering".
I've removed the EXE from my system and Secure Client still works in our setup as we do not use that functionality of AnyConnect/Secure Client.
Hopefully Cisco will release a new update and/or Microsoft will revaluate the vulnerability.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2024 04:48 AM
Hello ansto,
I think...Cisco has released software updates (free) that address this vulnerability. There are no workarounds that address this vulnerability.
For more details....Please go through the following link:
Best regards
******* If This Helps, Please Rate *******
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2024 06:14 AM
Hi Gopinath,
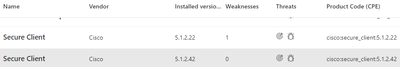
The fixed releases section in the link you provided refers to the software we have already installed: 5.1.2.42 (cisco-secure-client-win-5.1.2.42-predeploy-k9)
v5.1.2.42 bundles a component (Cisco secure Client Socket Filter Tool ) which has a version number of v5.1.2.22 - which is from the previous vulnerable release.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2024 07:07 AM
Is Windows Defender specifically flagging C:\Program Files (x86)\Cisco\Cisco Secure Client\acsocktool.exe\acsocktool.exe as vulnerable?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2024 07:40 AM
Yep, showing as weakness due to versioning.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-23-2024 01:17 PM
I don't think the acsocktool.exe would have nothing to do with SAML authentication which is the focus of CVE-2024-20337. It seems as though Windows Defender is simply looking at the version numbers and determining a vulnerability.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2024 01:31 AM
Thanks - reported in two tenants:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2024 01:10 AM
Hi stsargen,
We can report this is an inaccuracy to Microsoft, if you are sure that this component is not vulnerable.
Agreed based on description it shouldn't, but we don't have source code or vuln tests to confirm.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2024 01:15 AM
Yep that would be helpful as affecting the exposure score within defender.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2024 06:08 AM
I have confirmed that this has nothing to do with SAML authentication. Please report to Microsoft as a false positive.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2024 09:18 AM
There seems to be a newer version for the Secure client:
5.1.3.62
can anyone see if updating make the vulnerability go away from the ATP console?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2024 03:03 AM
The vulnerability is still there after updating to 5.1.3.62 so it's been reported as a false positive.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2024 10:11 AM
The version of the file has not changed in the AnyConnect package. It will not change unless a code change is needed in that specific file.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-07-2024 05:31 AM
Can confirm my reports didn't change anything. The inertia needed to get MS to change this, as @mcoombe said, might require Cisco's input?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide