- Cisco Community
- Technology and Support
- Security
- VPN
- Re: commonly used Diffie-Hellman primes risk
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
commonly used Diffie-Hellman primes risk
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2021 01:45 AM - edited 09-10-2021 01:52 AM
Hi,
We have a FPR1010 device with FTD image and manage by FDM.
A risk was found in VPN service (outside interface and port 443) that it's using a commonly used Diffie-Hellman primes for SSL key exchange. How can I change that DH primes?
The server is using a common or default prime number as a parameter during the Diffie-Hellman key exchange. This makes the secure session vulnerable to a precomputation attack. An attacker can spend a significant amount of time to generate a lookup/rainbow table for a particular prime number. This lookup table can then be used to obtain the shared secret for the handshake and decrypt the session.
Thanks!
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2021 02:02 AM
您需要升级到 FDM 7.0 版,该版本现在支持更改远程访问 VPN 的 SSL 密码设置。
Which should translate to - "You will need to upgrade to FDM 7.0, which now supports changing SSL cipher settings for remote access VPN."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2021 02:07 AM
是的,我们使用的是7.0.0.1-15,ssl密码设置好像只是更改cipher和协议,dh素数不知道怎么搞
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2021 09:30 AM
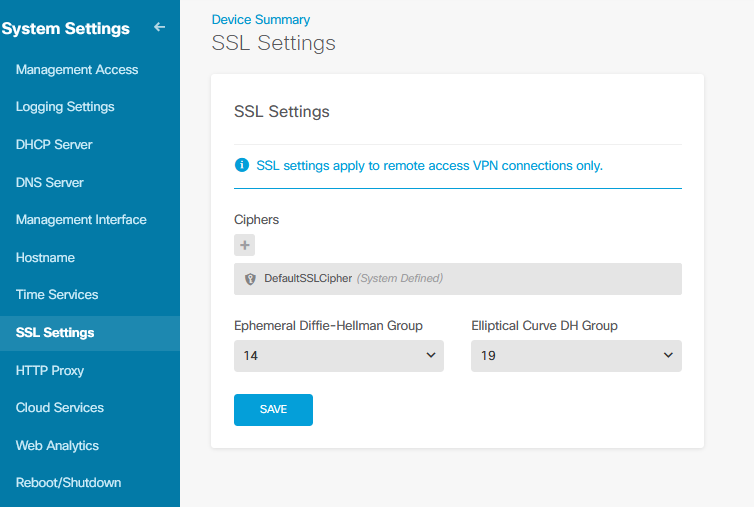
这会更改 DH(Diffie Hellman)设置
This changes the DH (Diffie Hellman) settings
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2021 11:55 AM
Yes, but this can not fix the risk of commonly DH primes. We already set to 15 and 21.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-15-2022 01:29 PM
Hello,
Were you able to resolve this issue. We are using FMC to manage FTD and getting the same issue while doing network security scan from outside.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-15-2022 11:53 PM
ECDHE will not use the dh primes, so we can avoid the risk
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide