- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Configuring GRE over IPsec
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2021 08:57 AM
Greetings!
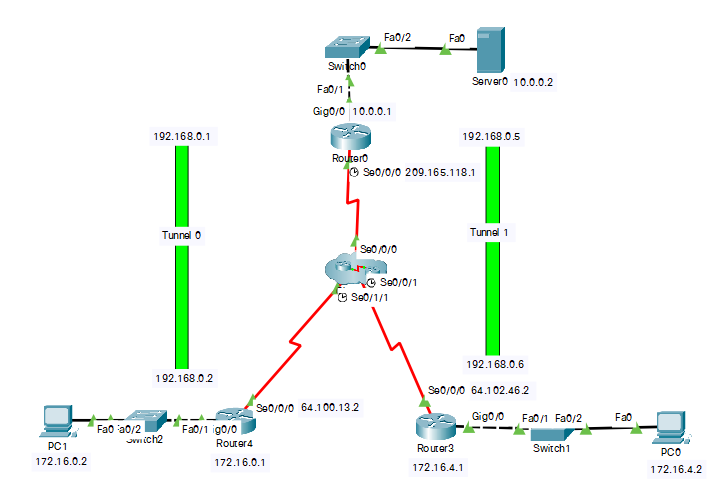
I´m trying to configure this lab and PC1 can ping Server, but for PC0 to ping server I had to configure a static route (
ip route 10.0.0.0 255.0.0.0 192.168.0.5), but not on PC1 (All routers have EIGRP configured.)
I can´t really understand why. I´ve checked configurations but I must be missing something.
I´de appreciate any help on understanding what´s happening and why.
I´ve attached the lab if someone wants to give it a try and help me solve this.
R0:
access-list 101 permit ip 10.0.0.0 0.255.255.255 172.16.0.0
0.0.3.255
crypto isakmp policy 10
encryption aes 256
authentication pre-share
group 5
crypto isakmp key vpn-key address 64.102.46.2
crypto isakmp key vpn-key address 64.100.13.2
crypto ipsec transform-set R0_SET esp-aes esp-sha-hmac
crypto map R0_MAP 101 ipsec-isakmp
set peer 64.102.46.2
set peer 64.100.13.2
set transform-set R0_SET
match address 101
interface serial 0/0/0
crypto map R0_MAP
interface tunnel 0
ip address 192.168.0.1 255.255.255.252
tunnel source serial 0/0/0
tunnel destination 64.100.13.2
tunnel mode gre ip
interface tunnel 1
ip address 192.168.0.5 255.255.255.252
tunnel source serial 0/0/0
tunnel destination 64.102.46.2
tunnel mode gre ip
ip route 172.16.0.0 255.255.252.0 192.168.0.2
ip route 172.16.4.0 255.255.252.0 192.168.0.6
R3:
access-list 101 permit ip 172.16.4.0 0.0.3.255 10.0.0.0 0.255.255.255
crypto isakmp policy 10
encryption aes 256
authentication pre-share
group 5
crypto isakmp key vpn-key address 209.165.118.1
crypto ipsec transform-set R4-SET esp-aes esp-sha-hmac
crypto map R4_MAP 101 ipsec-isakmp
set peer 209.165.118.1
set transform-set R4-SET
match address 101
interface serial 0/0/0
crypto map R4_MAP
interface tunnel 1
ip address 192.168.0.6 255.255.255.252
tunnel source serial 0/0/0
tunnel destination 209.165.118.1
tunnel mode gre ip
ip route 10.0.0.0 255.0.0.0 192.168.0.5
R4:
access-list 101 permit ip 172.16.0.0 0.0.3.255 10.0.0.0 0.255.255.255
crypto isakmp policy 10
encryption aes 256
authentication pre-share
group 5
crypto isakmp key vpn-key address 209.165.118.1
crypto ipsec transform-set R3-SET esp-aes esp-sha-hmac
crypto map R3_MAP 101 ipsec-isakmp
set peer 209.165.118.1
set transform-set R3-SET
match address 101
interface serial 0/0/0
crypto map R3_MAP
interface tunnel 0
ip address 192.168.0.2 255.255.255.252
tunnel source serial 0/0/0
tunnel destination 209.165.118.1
tunnel mode gre ip
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2021 09:18 AM
I don't have packet-tracer to check your full configuration, you say you've got EIGRP configured on all routers, is the traffic being routed unencrypted?
Check "show crypto ipsec sa" on R0 and confirm there are active SAs to R4 and the counters encaps|decpas increase when PC1 pings the server.
It could also potentially be that because your crypto ACL permits "ip" from the local networks, traffic is being encrypted over the crypto map without being sent over the tunnel interface. Again the "show crypto ipsec sa" would confirm the traffic selectors, provide the output for further review.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2021 09:18 AM
I don't have packet-tracer to check your full configuration, you say you've got EIGRP configured on all routers, is the traffic being routed unencrypted?
Check "show crypto ipsec sa" on R0 and confirm there are active SAs to R4 and the counters encaps|decpas increase when PC1 pings the server.
It could also potentially be that because your crypto ACL permits "ip" from the local networks, traffic is being encrypted over the crypto map without being sent over the tunnel interface. Again the "show crypto ipsec sa" would confirm the traffic selectors, provide the output for further review.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2021 11:39 AM
Hi Rob.
Thank´s mate!
I must have had a misconfigured netmask and crytpo map missplaced. I now can ping from PC0.
I also checked isakmp sa and an association wasn´t built successfuly between R3 and R0 even though it was using the tunnel (very odd).
R0#sh crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
64.100.13.2 209.165.118.1 QM_IDLE 1026 0 ACTIVE
R4#sh crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
209.165.118.1 64.100.13.2 QM_IDLE 1062 0 ACTIVE
R3#sh crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
209.165.118.1 64.102.46.2 QM_IDLE 1073 0 ACTIVE
(PC0)
C:\>tracert 10.0.0.2
Tracing route to 10.0.0.2 over a maximum of 30 hops:
1 0 ms 0 ms 0 ms 172.16.4.1
2 8 ms 3 ms 15 ms 192.168.0.5
3 3 ms 11 ms 19 ms 10.0.0.2
(PC1)
C:\>tracert 10.0.0.2
Tracing route to 10.0.0.2 over a maximum of 30 hops:
1 0 ms 0 ms 0 ms 172.16.0.1
2 3 ms 10 ms 11 ms 192.168.0.1
3 9 ms 8 ms 9 ms 10.0.0.2
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide