- Cisco Community
- Technology and Support
- Security
- VPN
- Configuring Site to Site VPN Connection via GRE Tunnels
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2014 03:02 AM
I am trying to establish site-to-site VPN connection over the internet using GRE tunnels. I am able to reach from one WAN interface to the other. But I am not able to get the ISAKMP and IPSec to work. Please find below the configuration and a simplified network diagram below. In the below scenario I am also running BGP between these routers. The BGP neighbor-ships are formed via the tunnels. But I want the traffic between the tunnels to be encrypted. Since the IPsec and ISAKMP is not working the BGP routes and other traffic are not encrypted.
Therefore I would like to know what might the reason for this.
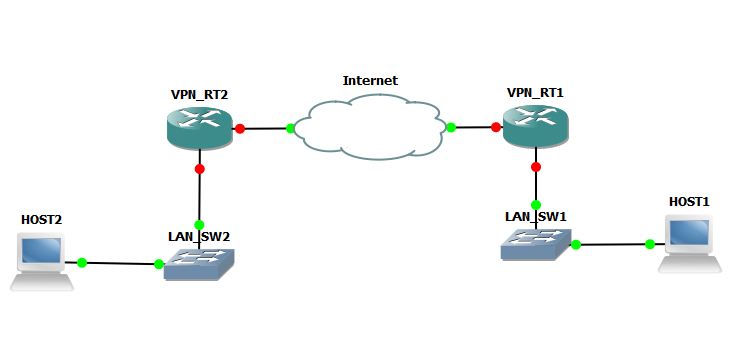
Config on VPN Router 1
crypto isakmp policy 1 encr 3des authentication pre-share group 2 lifetime 500 crypto isakmp key test_key1 address 192.168.30.1 crypto isakmp key test_key1 address 192.168.30.2 crypto isakmp keepalive 60 20 crypto isakmp aggressive-mode disable ! ! crypto ipsec transform-set high esp-3des esp-sha-hmac mode tunnel ! ! ! crypto map CRYP_MAP_IPSEC 10 ipsec-isakmp set peer 192.168.20.1 set security-association lifetime seconds 4000 set transform-set high set pfs group2 match address 110 crypto map CRYP_MAP_IPSEC 20 ipsec-isakmp set peer 192.168.20.2 set security-association lifetime seconds 4000 set transform-set high set pfs group2 match address 111 ! interface Loopback0 description IPsec_Tunnel0 ip address 192.168.30.1 255.255.255.255 ! interface Loopback1 description IPsec_Tunnel1 ip address 192.168.30.2 255.255.255.255 ! interface Loopback2 description BGP_Peer1 ip address 192.168.40.1 255.255.255.255 ! interface Loopback3 description BGP_Peer2 ip address 192.168.40.2 255.255.255.255 ! interface Tunnel0 ip unnumbered Loopback0 tunnel source Loopback0 tunnel destination 192.168.20.1 crypto map CRYP_MAP_IPSEC ! interface Tunnel1 ip unnumbered Loopback1 tunnel source Loopback1 tunnel destination 192.168.20.2 crypto map CRYP_MAP_IPSEC ! interface gi0 description #### CONNECTED TO Internet #### ip address 10.1.1.1 255.255.255.252 ip access-group 100 in duplex auto speed auto ! router bgp 64851 bgp log-neighbor-changes neighbor BGP_PEER_1 peer-group neighbor BGP_PEER_1 remote-as 64859 neighbor BGP_PEER_1 ebgp-multihop 255 neighbor BGP_PEER_1 update-source Loopback2 neighbor BGP_PEER_1 version 4 neighbor BGP_PEER_1 next-hop-self neighbor BGP_PEER_2 peer-group neighbor BGP_PEER_2 remote-as 64859 neighbor BGP_PEER_2 ebgp-multihop 255 neighbor BGP_PEER_2 update-source Loopback3 neighbor BGP_PEER_2 version 4 neighbor BGP_PEER_2 next-hop-self neighbor 192.168.10.1 peer-group BGP_PEER_1 neighbor 192.168.10.2 peer-group BGP_PEER_2 ! ip route 192.168.10.1 255.255.255.255 Tunnel0 ip route 192.168.10.2 255.255.255.255 Tunnel1 ip route 192.168.20.1 255.255.255.255 GigabitEthernet0 ip route 192.168.20.2 255.255.255.255 GigabitEthernet0 ! access-list 100 permit ip any any access-list 110 permit gre host 192.168.30.1 host 192.168.20.1 access-list 110 permit gre host 192.168.20.1 host 192.168.30.1 access-list 111 permit gre host 192.168.30.2 host 192.168.20.2 access-list 111 permit gre host 192.168.20.2 host 192.168.30.2 ======================================================================
Config on VPN Router 2
crypto isakmp policy 1 encr 3des authentication pre-share group 2 lifetime 500 crypto isakmp key test_key1 address 192.168.30.1 crypto isakmp key test_key1 address 192.168.30.2 crypto isakmp keepalive 60 20 crypto isakmp aggressive-mode disable ! ! crypto ipsec transform-set high esp-3des esp-sha-hmac mode tunnel ! ! ! crypto map CRYP_MAP_IPSEC 10 ipsec-isakmp set peer 192.168.30.1 set security-association lifetime seconds 4000 set transform-set high set pfs group2 match address 110 crypto map CRYP_MAP_IPSEC 20 ipsec-isakmp set peer 192.168.30.2 set security-association lifetime seconds 4000 set transform-set high set pfs group2 match address 111 ! interface Loopback0 description IPsec_Tunnel0 ip address 192.168.20.1 255.255.255.255 ! interface Loopback1 description IPsec_Tunnel1 ip address 192.168.20.2 255.255.255.255 ! interface Loopback2 description BGP_Peer1 ip address 192.168.10.1 255.255.255.255 ! interface Loopback3 description BGP_Peer2 ip address 192.168.10.2 255.255.255.255 ! interface Tunnel0 ip unnumbered Loopback0 tunnel source Loopback0 tunnel destination 192.168.30.1 crypto map CRYP_MAP_IPSEC ! interface Tunnel1 ip unnumbered Loopback1 tunnel source Loopback1 tunnel destination 192.168.30.2 crypto map CRYP_MAP_IPSEC ! interface gi0 description #### CONNECTED TO Internet #### ip address 10.1.1.2 255.255.255.252 ip access-group 100 in duplex auto speed auto ! router bgp 64859 bgp log-neighbor-changes neighbor BGP_PEER_1 peer-group neighbor BGP_PEER_1 remote-as 64851 neighbor BGP_PEER_1 ebgp-multihop 255 neighbor BGP_PEER_1 update-source Loopback2 neighbor BGP_PEER_1 version 4 neighbor BGP_PEER_1 next-hop-self neighbor BGP_PEER_2 peer-group neighbor BGP_PEER_2 remote-as 64851 neighbor BGP_PEER_2 ebgp-multihop 255 neighbor BGP_PEER_2 update-source Loopback3 neighbor BGP_PEER_2 version 4 neighbor BGP_PEER_2 next-hop-self neighbor 192.168.40.1 peer-group BGP_PEER_1 neighbor 192.168.40.2 peer-group BGP_PEER_2 ! ip route 192.168.40.1 255.255.255.255 Tunnel0 ip route 192.168.40.2 255.255.255.255 Tunnel1 ip route 192.168.30.1 255.255.255.255 gi0 ip route 192.168.30.2 255.255.255.255 gi0 ! access-list 100 permit ip any any access-list 110 permit gre host 192.168.20.1 host 192.168.30.1 access-list 110 permit gre host 192.168.30.1 host 192.168.20.1 access-list 111 permit gre host 192.168.20.2 host 192.168.30.2 access-list 111 permit gre host 192.168.30.2 host 192.168.20.2 ======================================================================
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2014 03:39 AM
Your Tunnel encryption configuration is incorrect...you need to do something the following at both ends.
| crypto isakmp policy 10 |
| encryption aes |
| hash sha |
| authentication pre-share |
| group 5 |
| crypto isakmp key cisco address <PEER ADDRESS> |
| crypto ipsec transform-set MYSET esp-aes 256 esp-sha-hmac |
| crypto ipsec profile MYPROFILE |
| set transform-set MYSET |
| interface tunnel 10 |
| ip unnumbered gig0/0 |
| tunnel source gig0/0 |
| tunnel destination <PEER ADDRESS> |
| tunnel mode ipsec ipv4 |
| tunnel protection ipsec profile MYPROFILE |
|
--
Please remember to select a correct answer and rate helpful posts
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2014 03:39 AM
Your Tunnel encryption configuration is incorrect...you need to do something the following at both ends.
| crypto isakmp policy 10 |
| encryption aes |
| hash sha |
| authentication pre-share |
| group 5 |
| crypto isakmp key cisco address <PEER ADDRESS> |
| crypto ipsec transform-set MYSET esp-aes 256 esp-sha-hmac |
| crypto ipsec profile MYPROFILE |
| set transform-set MYSET |
| interface tunnel 10 |
| ip unnumbered gig0/0 |
| tunnel source gig0/0 |
| tunnel destination <PEER ADDRESS> |
| tunnel mode ipsec ipv4 |
| tunnel protection ipsec profile MYPROFILE |
|
--
Please remember to select a correct answer and rate helpful posts
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-21-2014 04:34 AM
Dear MariusGunnerud,
Thanks for the advice. I will try out the new configuration and will let you know.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2014 01:35 AM
Dear MariusGunnerud,
I have managed to bring up the IPsec and ISAKMP to working status with same configuration.
Only I have included the following command that you recommended.
crypto ipsec profile MYPROFILE set transform-set MYSET
and the following in the tunnel interface.
tunnel mode ipsec ipv4 tunnel protection ipsec profile MYPROFILE
Also I have included "crypto isakmp invalid-spi-recovery" as well.
Thank you very much for you help.
BR,
IsmailSamah
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2014 05:40 AM
Glad you got it working! ![]()
Thank you for the rating
Please remember to select a correct answer and rate helpful posts
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide



