- Cisco Community
- Technology and Support
- Security
- VPN
- Disaster Recovery Site - Redundant VPN Peers
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2011 09:40 AM
Hello all, thanks in advance for your expertise.
We are setting up a disaster recovery site which will host redundant copies of our servers and critical data in Kansas City. In the case of a disaster, our headquarters site would be totally gone.
Currently we have 7 branch offices that communicate to our HQ via VPN tunnels (either over an Internet circuit, or over a Cox Communications Ethernet WAN circuit). The branch sites each have a 2821 Cisco ISR Router. At the headquarters and at the DR site, we use a Cisco ASA 5510 to terminate the VPN tunnels and do all of our backbone routing. Routing on the ASA and on the branch routers is all static, using a routing protocol would be a nice upgrade in the future..any ideas? We use lan-2-lan IPSEC VPN tunnels, no GRE/VPN is in use because the ASA does not terminate it.
What is the best way to setup my branch routers to automatically or manually fail-over to connect to a different ASA at the DR site?
Also, if my Headquarters site is still up, but either my Internet circuit or the Cox ethernet circuit at the headquarters goes down. How can I re-route all traffic in a loop back to the headquarters over the one good remaining circuit?
Is there a better way to do what I want to accomplish? BGP is not an option at this point due to its complexity.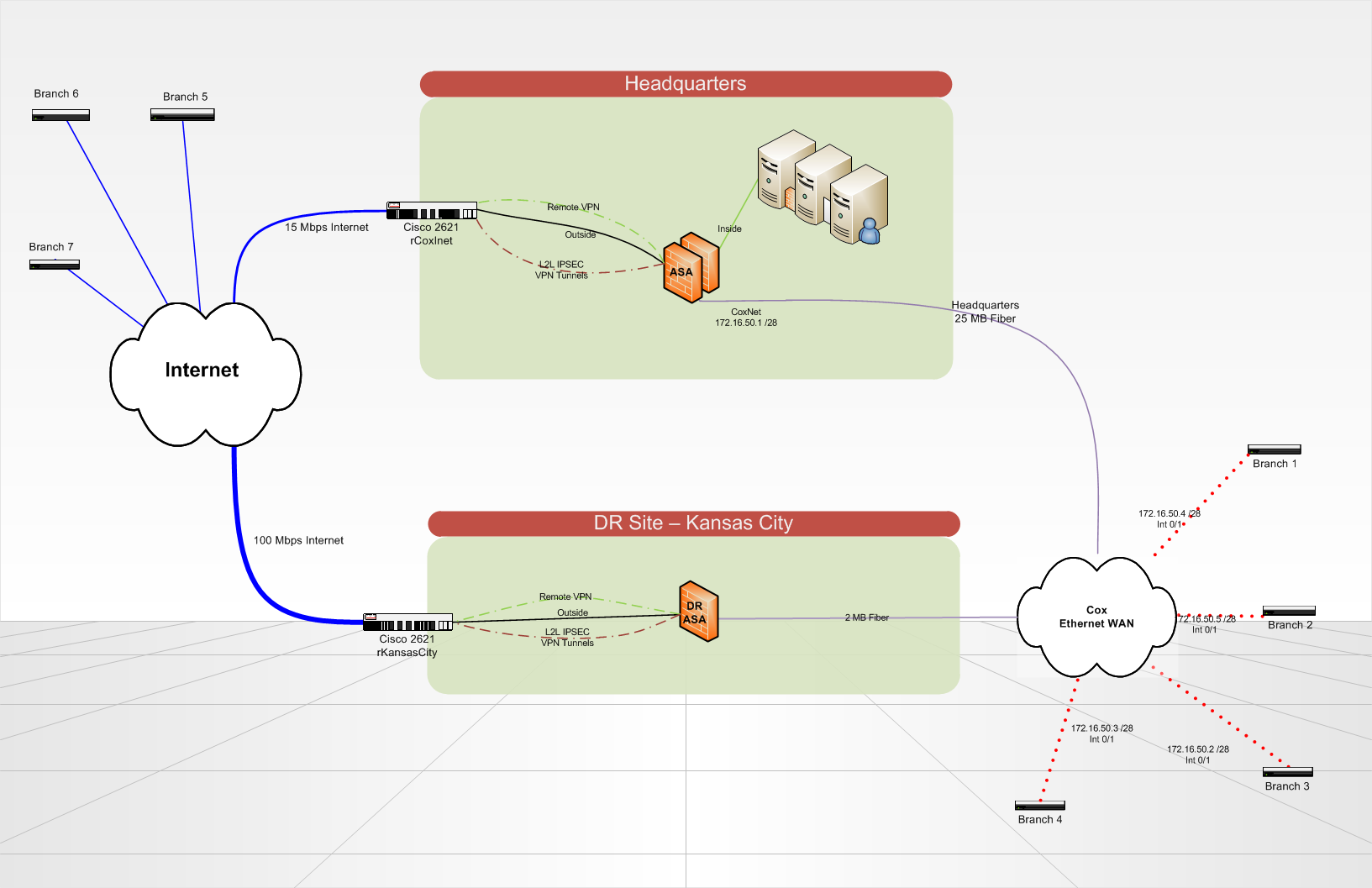
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2011 06:39 AM
Lucas,
To address the two point separately.
The easiest way to provide active/standby type of reundancy is preferred peer option in crypto maps (on ISR routers).
You can choose to establish VPN to HQ and only if HQ is not up you fallback to DR, when HQ is up you will EVENTUALLY fall back to it.
The answer to send part of your questions could also be the preferred peer option (and multiple peers in a crypto map entry).
That being said you can try to route OSPF traffic over IPsec tunnel (and using neighbor command to avoid handling of mcast in pure IPsec).
Docs:
HTH,
Marcin
P.S.
If you want my personal opion, chaning ASAs in HQ and DR sites and putting in routers you could do DMVPN or DVTI-SVTI scenario which would give you way more capabilities ;-)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2011 10:07 AM
If you want both tunnels up and active at the same then no, using multiple peer entries won't solve this issue.
If the subnets are different then i would just create separate IPSEC tunnels from your branch offices. You have 2821 routers at the branch so to change the default-route if the HQ site goes down you could use IP SLA on the routers. IP SLA allows you to setup a ping from the 2821 to HQ. If the ping fails then it will install an alternative default-route in your routing table on the 2821. If HQ comes back up and the ping is successful again then it will reinstall the default-route to HQ.
Just do a search within these forums for an IP SLA example.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2011 06:39 AM
Lucas,
To address the two point separately.
The easiest way to provide active/standby type of reundancy is preferred peer option in crypto maps (on ISR routers).
You can choose to establish VPN to HQ and only if HQ is not up you fallback to DR, when HQ is up you will EVENTUALLY fall back to it.
The answer to send part of your questions could also be the preferred peer option (and multiple peers in a crypto map entry).
That being said you can try to route OSPF traffic over IPsec tunnel (and using neighbor command to avoid handling of mcast in pure IPsec).
Docs:
HTH,
Marcin
P.S.
If you want my personal opion, chaning ASAs in HQ and DR sites and putting in routers you could do DMVPN or DVTI-SVTI scenario which would give you way more capabilities ;-)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2011 09:42 AM
Marcin, thanks for the reply. I actually need both sites to be active at the same time rather than an active/standby scenario. I have two CallManager servers that I plan to cluster across the WAN: 1 at Headquarters and 1 at DR site. The IP phones at the branch locations would need to be able to do heartbeats to both servers.
Would this multiple peers in a crypto map still meet this need? Or should I just create new a completely new crypto map for each brach office connecting to the DR site and have it active ALL the time?
Because my subnets are different at the headquarters and the DR, i don't think there would be any hard having two active tunnels. My only question then would be, how do I have my branch router change the default route if headquarters goes down?
Thanks!!
Anyone else?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2011 10:07 AM
If you want both tunnels up and active at the same then no, using multiple peer entries won't solve this issue.
If the subnets are different then i would just create separate IPSEC tunnels from your branch offices. You have 2821 routers at the branch so to change the default-route if the HQ site goes down you could use IP SLA on the routers. IP SLA allows you to setup a ping from the 2821 to HQ. If the ping fails then it will install an alternative default-route in your routing table on the 2821. If HQ comes back up and the ping is successful again then it will reinstall the default-route to HQ.
Just do a search within these forums for an IP SLA example.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2011 11:21 AM
Thanks Jon! Great info, I'm going to do my homework on the IP SLA.
Off hand, do you know if there is a timer to prevent route-flapping?
For example, I would only want my routes to go to DR if headquarters were down for X number of minutes. Then if Headquarters comes up steady for N number of minutes, the router will swap my default route back to HQ rather than DR site.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2011 11:23 AM
Lucas
Yes within IP SLA you can set the frequency of the ping test using the "frequency" command and you can also specify how long to wait after the ping has failed before removing the route with the "delay down" command.
Jon
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide