- Cisco Community
- Technology and Support
- Security
- VPN
- kindly check Router 20 log's
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
DMVPN Isakmp Security association is deleting every 60 Seconds
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-31-2016 12:34 AM - edited 02-21-2020 08:45 PM
Hello,
Platform : Cisco IOS Software, C880 Software (C880DATA-UNIVERSALK9-M), Version 15.2(4)M4, RELEASE SOFTWARE (fc2)
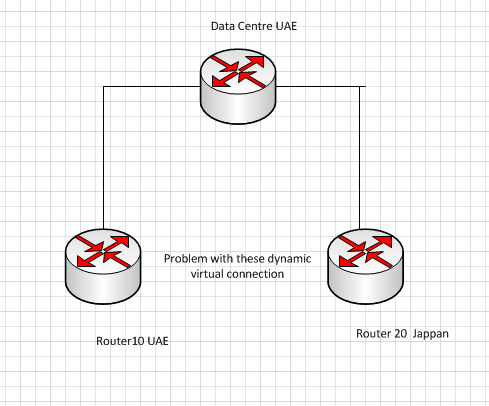
Facing one problem every 60 seconds dynamic VPN is Reconnecting with remote peer router20(jappan) spoke router from router10 uae spoke router
This is a production network. was working perfectly issue happens accidentally restarted router 10 issue got resolved after one day again it happens seeking a permanent solution
Router 10 tunnel interface
------------------------------------------------
interface Tunnel1
bandwidth 100000
ip address ***** 255.255.255.0
no ip redirects
ip mtu 1340
ip nhrp authentication vooler0
ip nhrp map **** *****
ip nhrp map multicast *****
ip nhrp network-id 5
ip nhrp nhs ******
ip nhrp registration no-unique
ip nhrp shortcut
ip nhrp redirect
no ip route-cache cef
no ip split-horizon
ip tcp adjust-mss 1300
ip ospf authentication message-digest
ip ospf message-digest-key 1 md5 *********
ip ospf network broadcast
ip ospf priority 0
ip ospf cost 10
logging event subif-link-status
keepalive 10 2
tunnel source Dialer1
tunnel mode gre multipoint
tunnel key 6
tunnel path-mtu-discovery
tunnel protection ipsec profile ********
already issued these commands on both router's
crypto isakmp policy 10
crypto isakmp invalid-spi-recovery
crypto isakmp keepalive 10 periodic
--------------------------------------------------------------------------------------
Sh run | s cry
same as both router
local-address Dialer1
pre-shared-key address 0.0.0.0 0.0.0.0 key ***********
crypto isakmp profile **************
keyring *************
match identity address 0.0.0.0
local-address Dialer1
crypto ipsec transform-set ************* esp-aes esp-sha-hmac
mode tunnel
crypto ipsec profile *******
set transform-set *********
set isakmp-profile **********
tunnel protection ipsec profile **********
Router 20 Tunnel interface
--------------------------------------------
interface Tunnel1
bandwidth 100000
ip address ********** 255.255.255.0
no ip redirects
ip mtu 1340
ip nhrp authentication vooler0
ip nhrp map ****** ********
ip nhrp map multicast *******
ip nhrp network-id 5
ip nhrp nhs **********
ip nhrp registration no-unique
ip nhrp shortcut
ip nhrp redirect
no ip route-cache cef
no ip split-horizon
ip tcp adjust-mss 1300
ip ospf authentication message-digest
ip ospf message-digest-key 1 md5 ******************
ip ospf network broadcast
ip ospf priority 0
ip ospf cost 10
keepalive 10 2
tunnel source Dialer1
tunnel mode gre multipoint
tunnel key 6
tunnel path-mtu-discovery
tunnel protection ipsec profile ******************
end
Router 10-UAE debugs and logs after issuing clear crypto isakmp sa peer *.*.*.*
*Mar 31 10:22:13: %CRYPTO-4-IKMP_NO_SA: IKE message from *.*.*.* has no SA and is not an initialization offer
*Mar 31 10:23:13: %CRYPTO-6-IKMP_MODE_FAILURE: Processing of Informational mode failed with peer at *.*.*.*
*Mar 31 10:23:31: %CRYPTO-6-ISAKMP_MANUAL_DELETE: IKE SA manually deleted. Do 'clear crypto sa peer *.*.*.*' to manually clear IPSec SA's covered by this IKE SA.
*Mar 31 10:24:13: %CRYPTO-4-RECVD_PKT_INV_SPI: decaps: rec'd IPSEC packet has invalid spi for destaddr=*.*.*.*, prot=50, spi=0xD1B94596(3518580118), srcaddr=*.*.*.*, input interface=Dialer1
*Mar 31 10:24:13: %CRYPTO-4-IKMP_NO_SA: IKE message from *.*.*.* has no SA and is not an initialization offer
*Mar 31 10:24:30 UTC: insert of map into mapdb AVL failed, map + ace pair already exists on the mapdb
*Mar 31 10:24:30 UTC: IPSEC(recalculate_mtu): reset sadb_root 88638574 mtu to 1500
*Mar 31 10:24:30 UTC: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= *.*.*.*:500, remote= *.*.*.*:500,
local_proxy= *.*.*.*/255.255.255.255/47/0,
remote_proxy= *.*.*.*/255.255.255.255/47/0,
protocol= ESP, transform= esp-aes esp-sha-hmac (Tunnel),
lifedur= 3600s and 4608000kb,
spi= 0x0(0), conn_id= 0, keysize= 128, flags= 0x0
*Mar 31 10:24:30 UTC: IPSEC: Expand action denied, notify RP
*Mar 31 10:24:30 UTC: IPSEC: Expand action denied, notify RP
*Mar 31 10:24:30 UTC: IPSEC: Expand action denied, discard or forward packet.
*Mar 31 10:24:30 UTC: IPSEC: Expand action denied, discard or forward packet.
*Mar 31 10:24:30 UTC: IPSEC(validate_proposal_request): proposal part #1
*Mar 31 10:24:30 UTC: IPSEC(validate_proposal_request): proposal part #1,
(key eng. msg.) INBOUND local= *.*.*.*:0, remote= *.*.*.*:0,
local_proxy= *.*.*.*/255.255.255.255/47/0,
remote_proxy= *.*.*.*/255.255.255.255/47/0,
protocol= ESP, transform= NONE (Tunnel),
lifedur= 0s and 0kb,
spi= 0x0(0), conn_id= 0, keysize= 128, flags= 0x0
*Mar 31 10:24:30 UTC: map_db_check_isakmp_profile profile did not match
*Mar 31 10:24:30 UTC: Crypto mapdb : proxy_match
src addr : *.*.*.*
dst addr : *.*.*.*
protocol : 47
src port : 0
dst port : 0
*Mar 31 10:24:30 UTC: map_db_check_isakmp_profile profile did not match
*Mar 31 10:24:30 UTC: Crypto mapdb : proxy_match
src addr : *.*.*.*
dst addr : *.*.*.*
protocol : 47
src port : 0
dst port : 0
*Mar 31 10:24:30 UTC: map_db_check_isakmp_profile profile did not match
*Mar 31 10:24:30 UTC: map_db_find_best did not find matching map
*Mar 31 10:24:30 UTC: Crypto mapdb : proxy_match
src addr : *.*.*.*
dst addr : *.*.*.*
protocol : 47
src port : 0
dst port : 0
*Mar 31 10:24:30 UTC: IPSEC(key_engine): got a queue event with 1 KMI message(s)
*Mar 31 10:24:30 UTC: map_db_check_isakmp_profile profile did not match
*Mar 31 10:24:30 UTC: Crypto mapdb : proxy_match
src addr : *.*.*.*
dst addr : *.*.*.*
protocol : 47
src port : 0
dst port : 0
*Mar 31 10:24:30 UTC: map_db_check_isakmp_profile profile did not match
*Mar 31 10:24:30 UTC: Crypto mapdb : proxy_match
src addr : *.*.*.*
dst addr : *.*.*.*
protocol : 47
src port : 0
dst port : 0
*Mar 31 10:24:30 UTC: map_db_check_isakmp_profile profile did not match
*Mar 31 10:24:30 UTC: map_db_find_best did not find matching map
*Mar 31 10:24:30 UTC: Crypto mapdb : proxy_match
src addr : *.*.*.*
dst addr : *.*.*.*
protocol : 47
src port : 0
dst port : 0
*Mar 31 10:24:30 UTC: IPSEC(crypto_ipsec_create_ipsec_sas): Map found Tunnel1-head-0
*Mar 31 10:24:30 UTC: IPSEC(crypto_ipsec_sa_find_ident_head): reconnecting with the same proxies and peer *.*.*.*
*Mar 31 10:24:30 UTC: IPSEC(crypto_ipsec_update_ident_tunnel_decap_oce): updating Tunnel1 ident 89895468 with tun_decap_oce 883783DC
*Mar 31 10:24:30 UTC: IPSEC(create_sa): sa created,
(sa) sa_dest= *.*.*.*, sa_proto= 50,
sa_spi= 0xED733DFD(3983752701),
sa_trans= esp-aes esp-sha-hmac , sa_conn_id= 1
sa_lifetime(k/sec)= (4608000/3600)
*Mar 31 10:24:30 UTC: IPSEC(create_sa): sa created,
(sa) sa_dest= *.*.*.*, sa_proto= 50,
sa_spi= 0xB57F207D(3045007485),
sa_trans= esp-aes esp-sha-hmac , sa_conn_id= 2
sa_lifetime(k/sec)= (4608000/3600)
*Mar 31 10:24:30 UTC: IPSEC: Expand action denied, notify RP
*Mar 31 10:24:33 UTC: IPSEC(key_engine): request timer fired: count = 1,
(identity) local= *.*.*.*:0, remote= *.*.*.*:0,
local_proxy= *.*.*.*/255.255.255.255/47/0,
remote_proxy= *.*.*.*/255.255.255.255/47/0
*Mar 31 10:24:33 UTC: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= *.*.*.*:500, remote= *.*.*.*:500,
local_proxy= *.*.*.*/255.255.255.255/47/0,
remote_proxy= *.*.*.*/255.255.255.255/47/0,
protocol= ESP, transform= esp-3des esp-md5-hmac (Transport),
lifedur= 3600s and 4608000kb,
spi= 0x0(0), conn_id= 0, keysize= 0, flags= 0x0
*Mar 31 10:24:38 UTC: IPSEC(update_current_outbound_sa): updated peer *.*.*.* current outbound sa to SPI B57F207D
*Mar 31 10:24:38 UTC: IPSEC(delete_sa): deleting SA,
(sa) sa_dest= *.*.*.*, sa_proto= 50,
sa_spi= 0xED733DFD(3983752701),
sa_trans= esp-aes esp-sha-hmac , sa_conn_id= 1
sa_lifetime(k/sec)= (4608000/3600),
(identity) local= *.*.*.*:0, remote= *.*.*.*:0,
local_proxy= *.*.*.*/255.255.255.255/47/0,
remote_proxy= *.*.*.*/255.255.255.255/47/0
*Mar 31 10:24:38 UTC: IPSEC(update_current_outbound_sa): updated peer *.*.*.* current outbound sa to SPI B57F207D
*Mar 31 10:24:38 UTC: IPSEC(delete_sa): deleting SA,
(sa) sa_dest= *.*.*.*, sa_proto= 50,
sa_spi= 0xB57F207D(3045007485),
sa_trans= esp-aes esp-sha-hmac , sa_conn_id= 2
sa_lifetime(k/sec)= (4608000/3600),
(identity) local= *.*.*.*:0, remote= *.*.*.*:0,
local_proxy= *.*.*.*/255.255.255.255/47/0,
remote_proxy= *.*.*.*/255.255.255.255/47/0
*Mar 31 10:24:38 UTC: IPSEC(cleanup_tun_decap_oce): unlock and null out Tunnel1 tun_decap_oce 883783DC from ident 89895468
*Mar 31 10:24:38 UTC: IPSEC(key_engine): got a queue event with 1 KMI message(s)
*Mar 31 10:24:38 UTC: IPSEC(key_engine): got a queue event with 1 KMI message(s)
*Mar 31 10:24:38 UTC: insert of map into mapdb AVL failed, map + ace pair already exists on the mapdb
*Mar 31 10:24:38 UTC: IPSEC(recalculate_mtu): reset sadb_root 88638574 mtu to 1500
*Mar 31 10:24:38 UTC: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= *.*.*.*:500, remote= *.*.*.*:500,
local_proxy= *.*.*.*/255.255.255.255/47/0,
remote_proxy= *.*.*.*/255.255.255.255/47/0,
protocol= ESP, transform= esp-aes esp-sha-hmac (Tunnel),
lifedur= 3600s and 4608000kb,
spi= 0x0(0), conn_id= 0, keysize= 128, flags= 0x0
*Mar 31 10:24:38 UTC: IPSEC: Expand action denied, notify RP
*Mar 31 10:24:38 UTC: IPSEC: Expand action denied, notify RP
*Mar 31 10:24:38 UTC: IPSEC: Expand action denied, discard or forward packet.
*Mar 31 10:24:38 UTC: IPSEC: Expand action denied, discard or forward packet.
- Labels:
-
DMVPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-31-2016 02:12 AM
kindly check Router 20 log's as well
*Mar 31 08:41:20.164: ISAKMP:(2178):deleting node -1636081989 error FALSE reason "Informational (in) state 1"
*Mar 31 08:41:20.164: IPSEC(key_engine): got a queue event with 1 KMI message(s)
*Mar 31 08:41:20.164: IPSEC(key_engine_delete_sas): rec'd delete notify from ISAKMP
*Mar 31 08:41:20.164: IPSEC(key_engine_delete_sas): delete SA with spi 0xF6427ECE proto 50 for *.*.*.*
*Mar 31 08:41:20.168: ISAKMP: Failed to find peer index node to update peer_info_list
*Mar 31 08:41:20.168: IPSEC(update_current_outbound_sa): updated peer *.*.*.* current outbound sa to SPI F6427ECE
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide