- Cisco Community
- Technology and Support
- Security
- VPN
- Dynamic VTI Tunnel Issue - not coming up
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Dynamic VTI Tunnel Issue - not coming up
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2022 09:08 AM
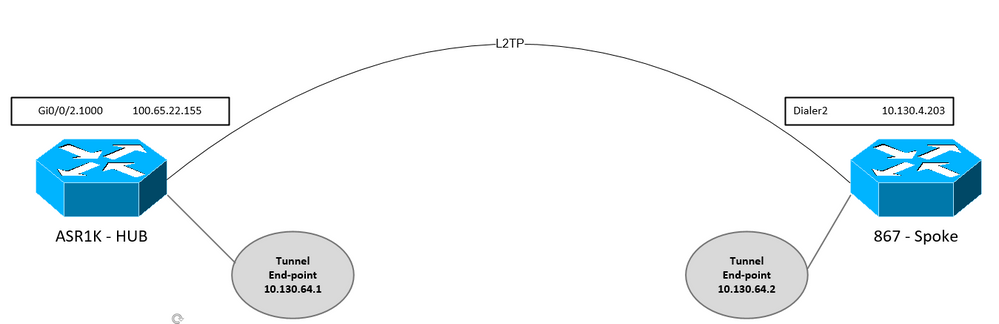
We have a requirement to encrypt traffic between 400+ branches, they are all using 867 routers so we cannot use DMVPN
To minimise config on hub, we are looking to use dynamic vti tunnels but having an issue
I would appreciate some advice on the design/config as that is probably the issue
From what I can see in logs phase 1 establishes and begins to update to QM_IDLE to be then torn down by hub, I cannot find any errors in the logs in relation to this
### HUB
crypto keyring 867keys vrf AP_WAN pre-shared-key address 10.130.4.203 255.255.255.0 key cisco123 no-xauth ! crypto isakmp policy 10 encr aes 256 hash sha256 authentication pre-share group 24 ! ! crypto isakmp profile 867 vrf AP_WAN keyring 867keys match identity address 10.130.4.203 255.255.255.255 AP_WAN match identity address 0.0.0.0 AP_WAN virtual-template 2 ! crypto ipsec transform-set 867 esp-aes 256 esp-sha256-hmac mode tunnel ! crypto ipsec profile 867 set transform-set 867 set isakmp-profile 867 ! interface Virtual-Template5 type tunnel ip vrf forwarding AP_WAN ip unnumbered Loopback105 tunnel source GigabitEthernet0/0/2.1000 tunnel mode ipsec ipv4 tunnel destination dynamic tunnel vrf AP_WAN tunnel protection ipsec profile 867 ! interface Loopback105 description END POINT FOR D-VTI TUNNELS TO 867 ROUTERS ip vrf forwarding AP_WAN ip address 10.130.64.1 255.255.255.255 ! interface GigabitEthernet0/0/2.1000 description ** Vodafone ANPOST-L2TP ** encapsulation dot1Q 1000 ip vrf forwarding AP_WAN ip address 100.65.22.155 255.255.255.254 no ip redirects no ip unreachables no ip proxy-arp
### SPOKE
crypto keyring mykeys pre-shared-key address 0.0.0.0 0.0.0.0 key cisco123 no-xauth ! crypto isakmp policy 10 encr aes 256 hash sha256 authentication pre-share group 24 crypto isakmp profile 867 keyring mykeys match identity address 10.130.64.1 255.255.255.255 match identity address 0.0.0.0 ! crypto ipsec transform-set 867 esp-aes 256 esp-sha256-hmac mode tunnel ! crypto ipsec profile 867 set transform-set 867 set isakmp-profile 867 ! interface Tunnel5 description COLO D-VTI TUNNEL ip address 10.130.64.2 255.255.255.248 ip mtu 1400 tunnel source Dialer2 tunnel mode ipsec ipv4 tunnel destination 10.130.64.1 tunnel protection ipsec profile 867 ! interface Dialer2 description #### Voda L2TP #### mtu 1492 ip address negotiated no ip redirects no ip unreachables no ip proxy-arp ip mtu 1452 ip flow ingress ip virtual-reassembly in encapsulation ppp dialer pool 2 dialer-group 2 no cdp enable ppp authentication chap callin ppp chap hostname Roebuck-867-1_anp@anpost.cl1 ppp chap password 7 055A205F334B4B1D58 !
### HUB DEBUGS
Log Buffer (32000 bytes):
Mar 14 15:36:38.745 GMT: ISAKMP-PAK: (0):received packet from 10.130.4.203 dport 500 sport 500 AP_WAN (N) NEW SA
Mar 14 15:36:38.745 GMT: ISAKMP: (0):Created a peer struct for 10.130.4.203, peer port 500
Mar 14 15:36:38.745 GMT: ISAKMP: (0):New peer created peer = 0x80007FCDE584A150 peer_handle = 0x8000000080002247
Mar 14 15:36:38.745 GMT: ISAKMP: (0):Locking peer struct 0x80007FCDE584A150, refcount 1 for crypto_isakmp_process_block
Mar 14 15:36:38.745 GMT: ISAKMP: (0):local port 500, remote port 500
Mar 14 15:36:38.745 GMT: ISAKMP: (0):insert sa successfully sa = 80007FCDE6E75AC8
Mar 14 15:36:38.745 GMT: ISAKMP: (0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
Mar 14 15:36:38.745 GMT: ISAKMP: (0):Old State = IKE_READY New State = IKE_R_MM1
Mar 14 15:36:38.746 GMT: ISAKMP: (0):processing SA payload. message ID = 0
Mar 14 15:36:38.746 GMT: ISAKMP: (0):processing vendor id payload
Mar 14 15:36:38.746 GMT: ISAKMP: (0):vendor ID seems Unity/DPD but major 69 mismatch
Mar 14 15:36:38.746 GMT: ISAKMP: (0):vendor ID is NAT-T RFC 3947
Mar 14 15:36:38.746 GMT: ISAKMP: (0):processing vendor id payload
Mar 14 15:36:38.746 GMT: ISAKMP: (0):vendor ID seems Unity/DPD but major 245 mismatch
Mar 14 15:36:38.746 GMT: ISAKMP: (0):vendor ID is NAT-T v7
Mar 14 15:36:38.746 GMT: ISAKMP: (0):processing vendor id payload
Mar 14 15:36:38.746 GMT: ISAKMP: (0):vendor ID seems Unity/DPD but major 157 mismatch
Mar 14 15:36:38.746 GMT: ISAKMP: (0):vendor ID is NAT-T v3
Mar 14 15:36:38.746 GMT: ISAKMP: (0):processing vendor id payload
Mar 14 15:36:38.746 GMT: ISAKMP: (0):vendor ID seems Unity/DPD but major 123 mismatch
Mar 14 15:36:38.746 GMT: ISAKMP: (0):vendor ID is NAT-T v2
Mar 14 15:36:38.746 GMT: ISAKMP: (0):found peer pre-shared key matching 10.130.4.203
Mar 14 15:36:38.746 GMT: ISAKMP: (0):local preshared key found
Mar 14 15:36:38.746 GMT: ISAKMP: (0):Scanning profiles for xauth ... ikeprof 867
Mar 14 15:36:38.746 GMT: ISAKMP: (0):Checking ISAKMP transform 1 against priority 10 policy
Mar 14 15:36:38.746 GMT: ISAKMP: (0): encryption AES-CBC
Mar 14 15:36:38.746 GMT: ISAKMP: (0): keylength of 256
Mar 14 15:36:38.746 GMT: ISAKMP: (0): hash SHA256
Mar 14 15:36:38.746 GMT: ISAKMP: (0): default group 24
Mar 14 15:36:38.746 GMT: ISAKMP: (0): auth pre-share
Mar 14 15:36:38.746 GMT: ISAKMP: (0): life type in seconds
Mar 14 15:36:38.746 GMT: ISAKMP: life duration (VPI) of 0x0 0x1 0x51 0x80
Mar 14 15:36:38.746 GMT: ISAKMP: (0):atts are acceptable. Next payload is 0
Mar 14 15:36:38.746 GMT: ISAKMP: (0):Acceptable atts:actual life: 86400
Mar 14 15:36:38.746 GMT: ISAKMP: (0):Acceptable atts:life: 0
Mar 14 15:36:38.746 GMT: ISAKMP: (0):Fill atts in sa vpi_length:4
Mar 14 15:36:38.746 GMT: ISAKMP: (0):Fill atts in sa life_in_seconds:86400
Mar 14 15:36:38.746 GMT: ISAKMP: (0):Returning Actual lifetime: 86400
Mar 14 15:36:38.746 GMT: ISAKMP: (0):Started lifetime timer: 86400.
Mar 14 15:36:38.750 GMT: ISAKMP: (0):processing vendor id payload
Mar 14 15:36:38.750 GMT: ISAKMP: (0):vendor ID seems Unity/DPD but major 69 mismatch
Mar 14 15:36:38.750 GMT: ISAKMP: (0):vendor ID is NAT-T RFC 3947
Mar 14 15:36:38.750 GMT: ISAKMP: (0):processing vendor id payload
Mar 14 15:36:38.750 GMT: ISAKMP: (0):vendor ID seems Unity/DPD but major 245 mismatch
Mar 14 15:36:38.750 GMT: ISAKMP: (0):vendor ID is NAT-T v7
Mar 14 15:36:38.750 GMT: ISAKMP: (0):processing vendor id payload
Mar 14 15:36:38.750 GMT: ISAKMP: (0):vendor ID seems Unity/DPD but major 157 mismatch
Mar 14 15:36:38.750 GMT: ISAKMP: (0):vendor ID is NAT-T v3
Mar 14 15:36:38.750 GMT: ISAKMP: (0):processing vendor id payload
Mar 14 15:36:38.750 GMT: ISAKMP: (0):vendor ID seems Unity/DPD but major 123 mismatch
Mar 14 15:36:38.750 GMT: ISAKMP: (0):vendor ID is NAT-T v2
Mar 14 15:36:38.750 GMT: ISAKMP: (0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
Mar 14 15:36:38.750 GMT: ISAKMP: (0):Old State = IKE_R_MM1 New State = IKE_R_MM1
Mar 14 15:36:38.750 GMT: ISAKMP: (0):constructed NAT-T vendor-rfc3947 ID
Mar 14 15:36:38.750 GMT: ISAKMP-PAK: (0):sending packet to 10.130.4.203 my_port 500 peer_port 500 (R) MM_SA_SETUP
Mar 14 15:36:38.750 GMT: ISAKMP: (0):Sending an IKE IPv4 Packet.
Mar 14 15:36:38.750 GMT: ISAKMP: (0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
Mar 14 15:36:38.751 GMT: ISAKMP: (0):Old State = IKE_R_MM1 New State = IKE_R_MM2
Mar 14 15:36:38.958 GMT: ISAKMP-PAK: (0):received packet from 10.130.4.203 dport 500 sport 500 AP_WAN (R) MM_SA_SETUP
Mar 14 15:36:38.958 GMT: ISAKMP: (0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
Mar 14 15:36:38.958 GMT: ISAKMP: (0):Old State = IKE_R_MM2 New State = IKE_R_MM3
Mar 14 15:36:38.958 GMT: ISAKMP: (0):processing KE payload. message ID = 0
Mar 14 15:36:38.965 GMT: ISAKMP: (0):processing NONCE payload. message ID = 0
Mar 14 15:36:38.965 GMT: ISAKMP: (0):found peer pre-shared key matching 10.130.4.203
Mar 14 15:36:38.965 GMT: ISAKMP: (60832):processing vendor id payload
Mar 14 15:36:38.965 GMT: ISAKMP: (60832):vendor ID is DPD
Mar 14 15:36:38.965 GMT: ISAKMP: (60832):processing vendor id payload
Mar 14 15:36:38.965 GMT: ISAKMP: (60832):speaking to another IOS box!
Mar 14 15:36:38.965 GMT: ISAKMP: (60832):processing vendor id payload
Mar 14 15:36:38.965 GMT: ISAKMP: (60832):vendor ID seems Unity/DPD but major 77 mismatch
Mar 14 15:36:38.965 GMT: ISAKMP: (60832):vendor ID is XAUTH
Mar 14 15:36:38.965 GMT: ISAKMP: (60832):received payload type 20
Mar 14 15:36:38.965 GMT: ISAKMP: (60832):His hash no match - this node outside NAT
Mar 14 15:36:38.965 GMT: ISAKMP: (60832):received payload type 20
Mar 14 15:36:38.965 GMT: ISAKMP: (60832):No NAT Found for self or peer
Mar 14 15:36:38.965 GMT: ISAKMP: (60832):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
Mar 14 15:36:38.965 GMT: ISAKMP: (60832):Old State = IKE_R_MM3 New State = IKE_R_MM3
Mar 14 15:36:38.965 GMT: ISAKMP-PAK: (60832):sending packet to 10.130.4.203 my_port 500 peer_port 500 (R) MM_KEY_EXCH
Mar 14 15:36:38.965 GMT: ISAKMP: (60832):Sending an IKE IPv4 Packet.
Mar 14 15:36:38.965 GMT: ISAKMP: (60832):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
Mar 14 15:36:38.965 GMT: ISAKMP: (60832):Old State = IKE_R_MM3 New State = IKE_R_MM4
Mar 14 15:36:39.369 GMT: ISAKMP-PAK: (60832):received packet from 10.130.4.203 dport 500 sport 500 AP_WAN (R) MM_KEY_EXCH
Mar 14 15:36:39.369 GMT: ISAKMP: (60832):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
Mar 14 15:36:39.369 GMT: ISAKMP: (60832):Old State = IKE_R_MM4 New State = IKE_R_MM5
Mar 14 15:36:39.369 GMT: ISAKMP: (60832):processing ID payload. message ID = 0
Mar 14 15:36:39.369 GMT: ISAKMP: (60832):ID payload
next-payload : 8
type : 1
Mar 14 15:36:39.369 GMT: ISAKMP: (60832): address : 10.130.4.203
Mar 14 15:36:39.369 GMT: ISAKMP: (60832): protocol : 17
port : 500
length : 12
Mar 14 15:36:39.369 GMT: ISAKMP: (0):peer matches 867 profile
Mar 14 15:36:39.369 GMT: ISAKMP: (60832):Found ADDRESS key in keyring 867keys
Mar 14 15:36:39.369 GMT: ISAKMP: (60832):processing HASH payload. message ID = 0
Mar 14 15:36:39.369 GMT: ISAKMP: (60832):processing NOTIFY INITIAL_CONTACT protocol 1
spi 0, message ID = 0, sa = 0x80007FCDE6E75AC8
Mar 14 15:36:39.369 GMT: ISAKMP: (60832):SA authentication status:
authenticated
Mar 14 15:36:39.369 GMT: ISAKMP: (60832):SA has been authenticated with 10.130.4.203
Mar 14 15:36:39.369 GMT: ISAKMP: (60832):SA authentication status:
authenticated
Mar 14 15:36:39.369 GMT: ISAKMP: (60832):Process initial contact,
bring down existing phase 1 and 2 SA's with local 10.130.64.1 remote 10.130.4.203 remote port 500
Mar 14 15:36:39.369 GMT: ISAKMP: (0):Trying to insert a peer 10.130.64.1/10.130.4.203/500/AP_WAN,
Mar 14 15:36:39.369 GMT: ISAKMP: (0): and inserted successfully 80007FCDE584A150.
Mar 14 15:36:39.369 GMT: ISAKMP: (60832):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
Mar 14 15:36:39.369 GMT: ISAKMP: (60832):Old State = IKE_R_MM5 New State = IKE_R_MM5
Mar 14 15:36:39.369 GMT: IPSEC(key_engine): got a queue event with 1 KMI message(s)
Mar 14 15:36:39.369 GMT: ISAKMP: (60832):SA is doing
Mar 14 15:36:39.369 GMT: ISAKMP: (60832):pre-shared key authentication using id type ID_IPV4_ADDR
Mar 14 15:36:39.369 GMT: ISAKMP: (60832):ID payload
next-payload : 8
type : 1
Mar 14 15:36:39.369 GMT: ISAKMP: (60832): address : 10.130.64.1
Mar 14 15:36:39.369 GMT: ISAKMP: (60832): protocol : 17
port : 500
length : 12
Mar 14 15:36:39.369 GMT: ISAKMP: (60832):Total payload length: 12
Mar 14 15:36:39.369 GMT: ISAKMP-PAK: (60832):sending packet to 10.130.4.203 my_port 500 peer_port 500 (R) MM_KEY_EXCH
Mar 14 15:36:39.370 GMT: ISAKMP: (60832):Sending an IKE IPv4 Packet.
Mar 14 15:36:39.370 GMT: ISAKMP: (60832):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
Mar 14 15:36:39.370 GMT: ISAKMP: (60832):Old State = IKE_R_MM5 New State = IKE_R_MM5
Mar 14 15:36:39.370 GMT: ISAKMP: (60832):Input = IKE_MESG_INTERNAL, IKE_FETCH_USER_ATTR
Mar 14 15:36:39.370 GMT: ISAKMP: (60832):Old State = IKE_R_MM5 New State = IKE_P1_COMPLETE
Mar 14 15:36:39.370 GMT: ISAKMP: (60832):Input = IKE_MESG_INTERNAL, IKE_PHASE1_COMPLETE
Mar 14 15:36:39.370 GMT: ISAKMP: (60832):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
Mar 14 15:36:39.370 GMT: IPSEC(key_engine): got a queue event with 1 KMI message(s)
Mar 14 15:36:39.370 GMT: Cannot find crypto swsb : in crypto_ipsec_notify_isakmp_delete (), 608
Mar 14 15:36:39.370 GMT: Cannot find crypto swsb : in crypto_ipsec_notify_isakmp_delete (), 608
Mar 14 15:36:39.370 GMT: ISAKMP: (60832):peer does not do paranoid keepalives.
Mar 14 15:36:39.370 GMT: ISAKMP: (60832):deleting SA reason "P1 delete notify (in)" state (R) QM_IDLE (peer 10.130.4.203)
Mar 14 15:36:39.370 GMT: ISAKMP: (60832):set new node 1070185223 to QM_IDLE
Mar 14 15:36:39.370 GMT: ISAKMP-PAK: (60832):sending packet to 10.130.4.203 my_port 500 peer_port 500 (R) QM_IDLE
Mar 14 15:36:39.370 GMT: ISAKMP: (60832):Sending an IKE IPv4 Packet.
Mar 14 15:36:39.370 GMT: ISAKMP: (60832):purging node 1070185223
Mar 14 15:36:39.371 GMT: ISAKMP: (60832):Input = IKE_MESG_INTERNAL, IKE_PHASE1_DEL
Mar 14 15:36:39.371 GMT: ISAKMP: (60832):Old State = IKE_P1_COMPLETE New State = IKE_DEST_SA
Mar 14 15:36:39.371 GMT: ISAKMP: (60832):deleting SA reason "P1 delete notify (in)" state (R) QM_IDLE (peer 10.130.4.203)
Mar 14 15:36:39.371 GMT: ISAKMP: (0):Unlocking peer struct 0x80007FCDE584A150 for isadb_mark_sa_deleted(), count 0
Mar 14 15:36:39.371 GMT: ISAKMP: (0):Deleting peer node by peer_reap for 10.130.4.203: 80007FCDE584A150
Mar 14 15:36:39.371 GMT: ISAKMP: (60832):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
Mar 14 15:36:39.371 GMT: ISAKMP: (60832):Old State = IKE_DEST_SA New State = IKE_DEST_SA
Mar 14 15:36:39.371 GMT: IPSEC(key_engine): got a queue event with 1 KMI message(s)
Mar 14 15:36:39.387 GMT: ISAKMP-PAK: (60832):received packet from 10.130.4.203 dport 500 sport 500 AP_WAN (R) MM_NO_STATE
Mar 14 15:37:08.741 GMT: ISAKMP-PAK: (0):received packet from 10.130.4.203 dport 500 sport 500 AP_WAN (N) NEW SA
Mar 14 15:37:08.741 GMT: ISAKMP: (0):Created a peer struct for 10.130.4.203, peer port 500
Mar 14 15:37:08.741 GMT: ISAKMP: (0):New peer created peer = 0x80007FCDE584A150 peer_handle = 0x8000000080002278
Mar 14 15:37:08.741 GMT: ISAKMP: (0):Locking peer struct 0x80007FCDE584A150, refcount 1 for crypto_isakmp_process_block
Mar 14 15:37:08.741 GMT: ISAKMP: (0):local port 500, remote port 500
Mar 14 15:37:08.741 GMT: ISAKMP: (0):Find a dup sa in the avl tree during calling isadb_insert sa = 80007FCDE6CECBC8
Mar 14 15:37:08.741 GMT: ISAKMP: (0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
Mar 14 15:37:08.741 GMT: ISAKMP: (0):Old State = IKE_READY New State = IKE_R_MM1
Mar 14 15:37:08.741 GMT: ISAKMP: (0):processing SA payload. message ID = 0
Mar 14 15:37:08.741 GMT: ISAKMP: (0):processing vendor id payload
Mar 14 15:37:08.741 GMT: ISAKMP: (0):vendor ID seems Unity/DPD but major 69 mismatch
Mar 14 15:37:08.741 GMT: ISAKMP: (0):vendor ID is NAT-T RFC 3947
Mar 14 15:37:08.741 GMT: ISAKMP: (0):processing vendor id payload
Mar 14 15:37:08.741 GMT: ISAKMP: (0):vendor ID seems Unity/DPD but major 245 mismatch
Mar 14 15:37:08.741 GMT: ISAKMP: (0):vendor ID is NAT-T v7
Mar 14 15:37:08.741 GMT: ISAKMP: (0):processing vendor id payload
Mar 14 15:37:08.741 GMT: ISAKMP: (0):vendor ID seems Unity/DPD but major 157 mismatch
Mar 14 15:37:08.741 GMT: ISAKMP: (0):vendor ID is NAT-T v3
Mar 14 15:37:08.741 GMT: ISAKMP: (0):processing vendor id payload
Mar 14 15:37:08.741 GMT: ISAKMP: (0):vendor ID seems Unity/DPD but major 123 mismatch
Mar 14 15:37:08.741 GMT: ISAKMP: (0):vendor ID is NAT-T v2
Mar 14 15:37:08.741 GMT: ISAKMP: (0):found peer pre-shared key matching 10.130.4.203
Mar 14 15:37:08.741 GMT: ISAKMP: (0):local preshared key found
Mar 14 15:37:08.741 GMT: ISAKMP: (0):Scanning profiles for xauth ... ikeprof 867
Mar 14 15:37:08.741 GMT: ISAKMP: (0):Checking ISAKMP transform 1 against priority 10 policy
Mar 14 15:37:08.741 GMT: ISAKMP: (0): encryption AES-CBC
Mar 14 15:37:08.741 GMT: ISAKMP: (0): keylength of 256
Mar 14 15:37:08.741 GMT: ISAKMP: (0): hash SHA256
Mar 14 15:37:08.741 GMT: ISAKMP: (0): default group 24
Mar 14 15:37:08.741 GMT: ISAKMP: (0): auth pre-share
Mar 14 15:37:08.741 GMT: ISAKMP: (0): life type in seconds
Mar 14 15:37:08.741 GMT: ISAKMP: life duration (VPI) of 0x0 0x1 0x51 0x80
Mar 14 15:37:08.741 GMT: ISAKMP: (0):atts are acceptable. Next payload is 0
Mar 14 15:37:08.742 GMT: ISAKMP: (0):Acceptable atts:actual life: 86400
Mar 14 15:37:08.742 GMT: ISAKMP: (0):Acceptable atts:life: 0
Mar 14 15:37:08.742 GMT: ISAKMP: (0):Fill atts in sa vpi_length:4
Mar 14 15:37:08.742 GMT: ISAKMP: (0):Fill atts in sa life_in_seconds:86400
Mar 14 15:37:08.742 GMT: ISAKMP: (0):Returning Actual lifetime: 86400
Mar 14 15:37:08.742 GMT: ISAKMP: (0):Started lifetime timer: 86400.
Mar 14 15:37:08.745 GMT: ISAKMP: (0):processing vendor id payload
Mar 14 15:37:08.745 GMT: ISAKMP: (0):vendor ID seems Unity/DPD but major 69 mismatch
Mar 14 15:37:08.745 GMT: ISAKMP: (0):vendor ID is NAT-T RFC 3947
Mar 14 15:37:08.745 GMT: ISAKMP: (0):processing vendor id payload
Mar 14 15:37:08.745 GMT: ISAKMP: (0):vendor ID seems Unity/DPD but major 245 mismatch
Mar 14 15:37:08.745 GMT: ISAKMP: (0):vendor ID is NAT-T v7
Mar 14 15:37:08.745 GMT: ISAKMP: (0):processing vendor id payload
Mar 14 15:37:08.745 GMT: ISAKMP: (0):vendor ID seems Unity/DPD but major 157 mismatch
Mar 14 15:37:08.746 GMT: ISAKMP: (0):vendor ID is NAT-T v3
Mar 14 15:37:08.746 GMT: ISAKMP: (0):processing vendor id payload
Mar 14 15:37:08.746 GMT: ISAKMP: (0):vendor ID seems Unity/DPD but major 123 mismatch
Mar 14 15:37:08.746 GMT: ISAKMP: (0):vendor ID is NAT-T v2
Mar 14 15:37:08.746 GMT: ISAKMP: (0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
Mar 14 15:37:08.746 GMT: ISAKMP: (0):Old State = IKE_R_MM1 New State = IKE_R_MM1
Mar 14 15:37:08.746 GMT: ISAKMP: (0):constructed NAT-T vendor-rfc3947 ID
Mar 14 15:37:08.746 GMT: ISAKMP-PAK: (0):sending packet to 10.130.4.203 my_port 500 peer_port 500 (R) MM_SA_SETUP
Mar 14 15:37:08.746 GMT: ISAKMP: (0):Sending an IKE IPv4 Packet.
Mar 14 15:37:08.746 GMT: ISAKMP: (0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
Mar 14 15:37:08.746 GMT: ISAKMP: (0):Old State = IKE_R_MM1 New State = IKE_R_MM2
Mar 14 15:37:08.947 GMT: ISAKMP-PAK: (0):received packet from 10.130.4.203 dport 500 sport 500 AP_WAN (R) MM_SA_SETUP
Mar 14 15:37:08.947 GMT: ISAKMP: (0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
Mar 14 15:37:08.947 GMT: ISAKMP: (0):Old State = IKE_R_MM2 New State = IKE_R_MM3
Mar 14 15:37:08.947 GMT: ISAKMP: (0):processing KE payload. message ID = 0
Mar 14 15:37:08.954 GMT: ISAKMP: (0):processing NONCE payload. message ID = 0
Mar 14 15:37:08.954 GMT: ISAKMP: (0):found peer pre-shared key matching 10.130.4.203
Mar 14 15:37:08.954 GMT: ISAKMP: (60833):processing vendor id payload
Mar 14 15:37:08.954 GMT: ISAKMP: (60833):vendor ID is DPD
Mar 14 15:37:08.955 GMT: ISAKMP: (60833):processing vendor id payload
Mar 14 15:37:08.955 GMT: ISAKMP: (60833):speaking to another IOS box!
Mar 14 15:37:08.955 GMT: ISAKMP: (60833):processing vendor id payload
Mar 14 15:37:08.955 GMT: ISAKMP: (60833):vendor ID seems Unity/DPD but major 22 mismatch
Mar 14 15:37:08.955 GMT: ISAKMP: (60833):vendor ID is XAUTH
Mar 14 15:37:08.955 GMT: ISAKMP: (60833):received payload type 20
Mar 14 15:37:08.955 GMT: ISAKMP: (60833):His hash no match - this node outside NAT
Mar 14 15:37:08.955 GMT: ISAKMP: (60833):received payload type 20
Mar 14 15:37:08.955 GMT: ISAKMP: (60833):No NAT Found for self or peer
Mar 14 15:37:08.955 GMT: ISAKMP: (60833):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
Mar 14 15:37:08.955 GMT: ISAKMP: (60833):Old State = IKE_R_MM3 New State = IKE_R_MM3
Mar 14 15:37:08.955 GMT: ISAKMP-PAK: (60833):sending packet to 10.130.4.203 my_port 500 peer_port 500 (R) MM_KEY_EXCH
Mar 14 15:37:08.955 GMT: ISAKMP: (60833):Sending an IKE IPv4 Packet.
Mar 14 15:37:08.955 GMT: ISAKMP: (60833):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
Mar 14 15:37:08.955 GMT: ISAKMP: (60833):Old State = IKE_R_MM3 New State = IKE_R_MM4
Mar 14 15:37:09.351 GMT: ISAKMP-PAK: (60833):received packet from 10.130.4.203 dport 500 sport 500 AP_WAN (R) MM_KEY_EXCH
Mar 14 15:37:09.351 GMT: ISAKMP: (60833):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
Mar 14 15:37:09.351 GMT: ISAKMP: (60833):Old State = IKE_R_MM4 New State = IKE_R_MM5
Mar 14 15:37:09.351 GMT: ISAKMP: (60833):processing ID payload. message ID = 0
Mar 14 15:37:09.351 GMT: ISAKMP: (60833):ID payload
next-payload : 8
type : 1
Mar 14 15:37:09.352 GMT: ISAKMP: (60833): address : 10.130.4.203
Mar 14 15:37:09.352 GMT: ISAKMP: (60833): protocol : 17
port : 500
length : 12
Mar 14 15:37:09.352 GMT: ISAKMP: (0):peer matches 867 profile
Mar 14 15:37:09.352 GMT: ISAKMP: (60833):Found ADDRESS key in keyring 867keys
Mar 14 15:37:09.352 GMT: ISAKMP: (60833):processing HASH payload. message ID = 0
Mar 14 15:37:09.352 GMT: ISAKMP: (60833):processing NOTIFY INITIAL_CONTACT protocol 1
spi 0, message ID = 0, sa = 0x80007FCDE6CECBC8
Mar 14 15:37:09.352 GMT: ISAKMP: (60833):SA authentication status:
authenticated
Mar 14 15:37:09.352 GMT: ISAKMP: (60833):SA has been authenticated with 10.130.4.203
Mar 14 15:37:09.352 GMT: ISAKMP: (60833):SA authentication status:
authenticated
Mar 14 15:37:09.352 GMT: ISAKMP: (60833):Process initial contact,
bring down existing phase 1 and 2 SA's with local 10.130.64.1 remote 10.130.4.203 remote port 500
Mar 14 15:37:09.352 GMT: ISAKMP: (0):Trying to insert a peer 10.130.64.1/10.130.4.203/500/AP_WAN,
Mar 14 15:37:09.352 GMT: ISAKMP: (0): and inserted successfully 80007FCDE584A150.
Mar 14 15:37:09.352 GMT: ISAKMP: (60833):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
Mar 14 15:37:09.352 GMT: ISAKMP: (60833):Old State = IKE_R_MM5 New State = IKE_R_MM5
Mar 14 15:37:09.352 GMT: IPSEC(key_engine): got a queue event with 1 KMI message(s)
Mar 14 15:37:09.352 GMT: ISAKMP: (60833):SA is doing
Mar 14 15:37:09.352 GMT: ISAKMP: (60833):pre-shared key authentication using id type ID_IPV4_ADDR
Mar 14 15:37:09.352 GMT: ISAKMP: (60833):ID payload
next-payload : 8
type : 1
Mar 14 15:37:09.352 GMT: ISAKMP: (60833): address : 10.130.64.1
Mar 14 15:37:09.352 GMT: ISAKMP: (60833): protocol : 17
port : 500
length : 12
Mar 14 15:37:09.352 GMT: ISAKMP: (60833):Total payload length: 12
Mar 14 15:37:09.352 GMT: ISAKMP-PAK: (60833):sending packet to 10.130.4.203 my_port 500 peer_port 500 (R) MM_KEY_EXCH
Mar 14 15:37:09.352 GMT: ISAKMP: (60833):Sending an IKE IPv4 Packet.
Mar 14 15:37:09.352 GMT: ISAKMP: (60833):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
Mar 14 15:37:09.352 GMT: ISAKMP: (60833):Old State = IKE_R_MM5 New State = IKE_R_MM5
Mar 14 15:37:09.352 GMT: ISAKMP: (60833):Input = IKE_MESG_INTERNAL, IKE_FETCH_USER_ATTR
Mar 14 15:37:09.352 GMT: ISAKMP: (60833):Old State = IKE_R_MM5 New State = IKE_P1_COMPLETE
Mar 14 15:37:09.353 GMT: ISAKMP: (60833):Input = IKE_MESG_INTERNAL, IKE_PHASE1_COMPLETE
Mar 14 15:37:09.353 GMT: ISAKMP: (60833):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
Mar 14 15:37:09.353 GMT: IPSEC(key_engine): got a queue event with 1 KMI message(s)
Mar 14 15:37:09.353 GMT: Cannot find crypto swsb : in crypto_ipsec_notify_isakmp_delete (), 608
Mar 14 15:37:09.353 GMT: Cannot find crypto swsb : in crypto_ipsec_notify_isakmp_delete (), 608
Mar 14 15:37:09.353 GMT: ISAKMP: (60833):peer does not do paranoid keepalives.
Mar 14 15:37:09.353 GMT: ISAKMP: (60833):deleting SA reason "P1 delete notify (in)" state (R) QM_IDLE (peer 10.130.4.203)
Mar 14 15:37:09.353 GMT: ISAKMP: (60832):peer does not do paranoid keepalives.
Mar 14 15:37:09.353 GMT: ISAKMP: (60833):set new node 2094578565 to QM_IDLE
Mar 14 15:37:09.353 GMT: ISAKMP-PAK: (60833):sending packet to 10.130.4.203 my_port 500 peer_port 500 (R) QM_IDLE
Mar 14 15:37:09.353 GMT: ISAKMP: (60833):Sending an IKE IPv4 Packet.
Mar 14 15:37:09.353 GMT: ISAKMP: (60833):purging node 2094578565
Mar 14 15:37:09.353 GMT: ISAKMP: (60833):Input = IKE_MESG_INTERNAL, IKE_PHASE1_DEL
Mar 14 15:37:09.353 GMT: ISAKMP: (60833):Old State = IKE_P1_COMPLETE New State = IKE_DEST_SA
Mar 14 15:37:09.353 GMT: ISAKMP: (60833):deleting SA reason "P1 delete notify (in)" state (R) QM_IDLE (peer 10.130.4.203)
Mar 14 15:37:09.353 GMT: ISAKMP: (0):Unlocking peer struct 0x80007FCDE584A150 for isadb_mark_sa_deleted(), count 0
Mar 14 15:37:09.353 GMT: ISAKMP: (0):Deleting peer node by peer_reap for 10.130.4.203: 80007FCDE584A150
Mar 14 15:37:09.354 GMT: ISAKMP: (60833):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
Mar 14 15:37:09.354 GMT: ISAKMP: (60833):Old State = IKE_DEST_SA New State = IKE_DEST_SA
Mar 14 15:37:09.354 GMT: IPSEC(key_engine): got a queue event with 1 KMI message(s)
Mar 14 15:37:09.363 GMT: ISAKMP-PAK: (60833):received packet from 10.130.4.203 dport 500 sport 500 AP_WAN (R) MM_NO_STATE
### SPOKE DEBUGS
Roebuck-VF867-1(config)#int tun 5
Roebuck-VF867-1(config-if)#
Roebuck-VF867-1(config-if)#
Roebuck-VF867-1(config-if)#
Roebuck-VF867-1(config-if)#no shut
Roebuck-VF867-1(config-if)#
*Mar 14 15:32:36.842: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is OFF
*Mar 14 15:32:36.846: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
*Mar 14 15:32:36.846: insert of map into mapdb AVL failed, map + ace pair already exists on the mapdb
*Mar 14 15:32:36.846: IPSEC: Expand action denied, discard or forward packet.
*Mar 14 15:32:36.846: IPSEC: Expand action denied, notify RP
*Mar 14 15:32:36.846: IPSEC: Expand action denied, discard or forward packet.
*Mar 14 15:32:36.846: IPSEC: Expand action denied, discard or forward packet.
*Mar 14 15:32:36.846: IPSEC:(SESSION ID = 1) (recalculate_mtu) reset sadb_root 8B184CDC mtu to 1452
*Mar 14 15:32:36.846: IPSEC:(SESSION ID = 1) (adjust_mtu) adjusting ident ip mtu from 1400 to 1452,
(identity) local= 10.130.4.203:0, remote= 10.130.64.1:0,
local_proxy= 0.0.0.0/0.0.0.0/256/0,
remote_proxy= 0.0.0.0/0.0.0.0/256/0
*Mar 14 15:32:36.846: IPSEC:(SESSION ID = 1) (adjust_mtu) adjusting path mtu from 1400 to 1452,
(identity) local= 10.130.4.203:0, remote= 10.130.64.1:0,
local_proxy= 0.0.0.0/0.0.0.0/256/0,
remote_proxy= 0.0.0.0/0.0.0.0/256/0
*Mar 14 15:32:36.846: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 10.130.4.203:500, remote= 10.130.64.1:500,
local_proxy= 0.0.0.0/0.0.0.0/256/0,
remote_proxy= 0.0.0.0/0.0.0.0/256/0,
protocol= ESP, transform= esp-aes 256 esp-sha256-hmac (Tunnel),
lifedur= 3600s and 4608000kb,
spi= 0x0(0), conn_id= 0, keysize= 256, flags= 0x0
*Mar 14 15:32:36.850: ISAKMP: (0):SA request profile is 867
*Mar 14 15:32:36.850: ISAKMP: (0):Created a peer struct for 10.130.64.1, peer port 500
*Mar 14 15:32:36.850: ISAKMP: (0):New peer created peer = 0x89878BC0 peer_handle = 0x8000026F
*Mar 14 15:32:36.850: ISAKMP: (0):Locking peer struct 0x89878BC0, refcount 1 for isakmp_initiator
*Mar 14 15:32:36.850: ISAKMP: (0):local port 500, remote port 500
*Mar 14 15:32:36.850: ISAKMP: (0):set new node 0 to QM_IDLE
*Mar 14 15:32:36.850: ISAKMP: (0):insert sa successfully sa = 8BB11CC0
*Mar 14 15:32:36.850: ISAKMP: (0):Can not start Aggressive mode, trying Main mode.
*Mar 14 15:32:36.850: ISAKMP: (0):Found ADDRESS key in keyring mykeys
*Mar 14 15:32:36.850: ISAKMP: (0):constructed NAT-T vendor-rfc3947 ID
*Mar 14 15:32:36.850: ISAKMP: (0):constructed NAT-T vendor-07 ID
*Mar 14 15:32:36.850: ISAKMP: (0):constructed NAT-T vendor-03 ID
*Mar 14 15:32:36.850: ISAKMP: (0):constructed NAT-T vendor-02 ID
*Mar 14 15:32:36.850: ISAKMP: (0):Input = IKE_MESG_FROM_IPSEC, IKE_SA_REQ_MM
*Mar 14 15:32:36.850: ISAKMP: (0):Old State = IKE_READY New State = IKE_I_MM1
*Mar 14 15:32:36.850: ISAKMP: (0):beginning Main Mode exchange
*Mar 14 15:32:36.850: ISAKMP-PAK: (0):sending packet to 10.130.64.1 my_port 500 peer_port 500 (I) MM_NO_STATE
*Mar 14 15:32:36.850: ISAKMP: (0):Sending an IKE IPv4 Packet.
*Mar 14 15:32:36.862: ISAKMP-PAK: (0):received packet from 10.130.64.1 dport 500 sport 500 Global (I) MM_NO_STATE
*Mar 14 15:32:36.862: ISAKMP: (0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Mar 14 15:32:36.866: ISAKMP: (0):Old State = IKE_I_MM1 New State = IKE_I_MM2
*Mar 14 15:32:36.866: ISAKMP: (0):processing SA payload. message ID = 0
*Mar 14 15:32:36.866: ISAKMP: (0):processing vendor id payload
*Mar 14 15:32:36.866: ISAKMP: (0):vendor ID seems Unity/DPD but major 69 mismatch
*Mar 14 15:32:36.866: ISAKMP: (0):vendor ID is NAT-T RFC 3947
*Mar 14 15:32:36.866: ISAKMP: (0):Found ADDRESS key in keyring mykeys
*Mar 14 15:32:36.866: ISAKMP: (0):local preshared key found
*Mar 14 15:32:36.866: ISAKMP: (0):Looking for xauth in profile 867
*Mar 14 15:32:36.866: ISAKMP: (0):Checking ISAKMP transform 1 against priority 10 policy
*Mar 14 15:32:36.866: ISAKMP: (0): encryption AES-CBC
*Mar 14 15:32:36.866: ISAKMP: (0): keylength of 256
*Mar 14 15:32:36.866: ISAKMP: (0): hash SHA256
*Mar 14 15:32:36.866: ISAKMP: (0): default group 24
*Mar 14 15:32:36.866: ISAKMP: (0): auth pre-share
*Mar 14 15:32:36.866: ISAKMP: (0): life type in seconds
*Mar 14 15:32:36.866: ISAKMP: life duration (VPI) of 0x0 0x1 0x51 0x80
*Mar 14 15:32:36.866: ISAKMP: (0):atts are acceptable. Next payload is 0
*Mar 14 15:32:36.866: ISAKMP: (0):Acceptable atts:actual life: 0
*Mar 14 15:32:36.866: ISAKMP: (0):Acceptable atts:life: 0
*Mar 14 15:32:36.866: ISAKMP: (0):Fill atts in sa vpi_length:4
*Mar 14 15:32:36.866: ISAKMP: (0):Fill atts in sa life_in_seconds:86400
*Mar 14 15:32:36.866: ISAKMP: (0):Returning Actual lifetime: 86400
*Mar 14 15:32:36.866: ISAKMP: (0):Started lifetime timer: 86400.
*Mar 14 15:32:37.062: ISAKMP: (0):processing vendor id payload
*Mar 14 15:32:37.062: ISAKMP: (0):vendor ID seems Unity/DPD but major 69 mismatch
*Mar 14 15:32:37.062: ISAKMP: (0):vendor ID is NAT-T RFC 3947
*Mar 14 15:32:37.062: ISAKMP: (0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Mar 14 15:32:37.062: ISAKMP: (0):Old State = IKE_I_MM2 New State = IKE_I_MM2
*Mar 14 15:32:37.062: ISAKMP-PAK: (0):sending packet to 10.130.64.1 my_port 500 peer_port 500 (I) MM_SA_SETUP
*Mar 14 15:32:37.062: ISAKMP: (0):Sending an IKE IPv4 Packet.
*Mar 14 15:32:37.062: ISAKMP: (0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Mar 14 15:32:37.062: ISAKMP: (0):Old State = IKE_I_MM2 New State = IKE_I_MM3
*Mar 14 15:32:37.078: ISAKMP-PAK: (0):received packet from 10.130.64.1 dport 500 sport 500 Global (I) MM_SA_SETUP
*Mar 14 15:32:37.078: ISAKMP: (0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Mar 14 15:32:37.078: ISAKMP: (0):Old State = IKE_I_MM3 New State = IKE_I_MM4
*Mar 14 15:32:37.078: ISAKMP: (0):processing KE payload. message ID = 0
*Mar 14 15:32:37.470: ISAKMP: (0):processing NONCE payload. message ID = 0
*Mar 14 15:32:37.470: ISAKMP: (0):Found ADDRESS key in keyring mykeys
*Mar 14 15:32:37.470: ISAKMP: (1003):processing vendor id payload
*Mar 14 15:32:37.470: ISAKMP: (1003):vendor ID is Unity
*Mar 14 15:32:37.470: ISAKMP: (1003):processing vendor id payload
*Mar 14 15:32:37.470: ISAKMP: (1003):vendor ID is DPD
*Mar 14 15:32:37.470: ISAKMP: (1003):processing vendor id payload
*Mar 14 15:32:37.470: ISAKMP: (1003):speaking to another IOS box!
*Mar 14 15:32:37.470: ISAKMP: (1003):received payload type 20
*Mar 14 15:32:37.470: ISAKMP: (1003):His hash no match - this node outside NAT
*Mar 14 15:32:37.470: ISAKMP: (1003):received payload type 20
*Mar 14 15:32:37.470: ISAKMP: (1003):No NAT Found for self or peer
*Mar 14 15:32:37.470: ISAKMP: (1003):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Mar 14 15:32:37.470: ISAKMP: (1003):Old State = IKE_I_MM4 New State = IKE_I_MM4
*Mar 14 15:32:37.474: ISAKMP: (1003):Send initial contact
*Mar 14 15:32:37.474: ISAKMP: (1003):SA is doing
*Mar 14 15:32:37.474: ISAKMP: (1003):pre-shared key authentication using id type ID_IPV4_ADDR
*Mar 14 15:32:37.474: ISAKMP: (1003):ID payload
next-payload : 8
type : 1
*Mar 14 15:32:37.474: ISAKMP: (1003): address : 10.130.4.203
*Mar 14 15:32:37.474: ISAKMP: (1003): protocol : 17
port : 500
length : 12
*Mar 14 15:32:37.474: ISAKMP: (1003):Total payload length: 12
*Mar 14 15:32:37.474: ISAKMP-PAK: (1003):sending packet to 10.130.64.1 my_port 500 peer_port 500 (I) MM_KEY_EXCH
*Mar 14 15:32:37.474: ISAKMP: (1003):Sending an IKE IPv4 Packet.
*Mar 14 15:32:37.474: ISAKMP: (1003):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Mar 14 15:32:37.474: ISAKMP: (1003):Old State = IKE_I_MM4 New State = IKE_I_MM5
*Mar 14 15:32:37.482: ISAKMP-PAK: (1003):received packet from 10.130.64.1 dport 500 sport 500 Global (I) MM_KEY_EXCH
*Mar 14 15:32:37.482: ISAKMP: (1003):processing ID payload. message ID = 0
*Mar 14 15:32:37.482: ISAKMP: (1003):ID payload
next-payload : 8
type : 1
*Mar 14 15:32:37.482: ISAKMP: (1003): address : 10.130.64.1
*Mar 14 15:32:37.482: ISAKMP: (1003): protocol : 17
port : 500
length : 12
*Mar 14 15:32:37.482: ISAKMP: (1003):processing HASH payload. message ID = 0
*Mar 14 15:32:37.482: ISAKMP: (1003):SA authentication status:
authenticated
*Mar 14 15:32:37.482: ISAKMP: (1003):SA has been authenticated with 10.130.64.1
*Mar 14 15:32:37.482: ISAKMP: (0):Trying to insert a peer 10.130.4.203/10.130.64.1/500/,
*Mar 14 15:32:37.482: ISAKMP: (0): and inserted successfully 89878BC0.
*Mar 14 15:32:37.482: ISAKMP: (1003):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Mar 14 15:32:37.486: ISAKMP: (1003):Old State = IKE_I_MM5 New State = IKE_I_MM6
*Mar 14 15:32:37.486: ISAKMP: (1003):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Mar 14 15:32:37.486: ISAKMP: (1003):Old State = IKE_I_MM6 New State = IKE_I_MM6
*Mar 14 15:32:37.486: ISAKMP-PAK: (1003):received packet from 10.130.64.1 dport 500 sport 500 Global (I) MM_KEY_EXCH
*Mar 14 15:32:37.486: ISAKMP: (1003):set new node 1070185223 to QM_IDLE
*Mar 14 15:32:37.486: ISAKMP: (1003):processing HASH payload. message ID = 1070185223
*Mar 14 15:32:37.486: ISAKMP: (1003):received payload type 18
*Mar 14 15:32:37.486: ISAKMP: (1003):Processing delete with reason payload
*Mar 14 15:32:37.486: ISAKMP: (1003):delete doi = 1
*Mar 14 15:32:37.486: ISAKMP: (1003):delete protocol id = 1
*Mar 14 15:32:37.486: ISAKMP: (1003):delete spi_size = 16
*Mar 14 15:32:37.486: ISAKMP: (1003):delete num spis = 1
*Mar 14 15:32:37.486: ISAKMP: (1003):delete_reason = 6
*Mar 14 15:32:37.490: ISAKMP: (1003):processing DELETE_WITH_REASON payload, message ID = 1070185223, reason: Unknown delete reason!
*Mar 14 15:32:37.490: ISAKMP: (1003):peer does not do paranoid keepalives.
*Mar 14 15:32:37.490: ISAKMP: (1003):deleting SA reason "P1 delete notify (in)" state (I) MM_KEY_EXCH (peer 10.130.64.1)
*Mar 14 15:32:37.490: ISAKMP: (1003):deleting node 1070185223 error FALSE reason "Informational (in) state 1"
*Mar 14 15:32:37.490: ISAKMP: (1003):Ignoring as SA is marked dead!
*Mar 14 15:32:37.490: ISAKMP: (1003):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Mar 14 15:32:37.490: ISAKMP: (1003):Old State = IKE_I_MM6 New State = IKE_P1_COMPLETE
*Mar 14 15:32:37.490: ISAKMP: (1003):set new node -614784848 to QM_IDLE
*Mar 14 15:32:37.490: ISAKMP-PAK: (1003):sending packet to 10.130.64.1 my_port 500 peer_port 500 (I) MM_KEY_EXCH
*Mar 14 15:32:37.490: ISAKMP: (1003):Sending an IKE IPv4 Packet.
*Mar 14 15:32:37.490: ISAKMP: (1003):purging node -614784848
*Mar 14 15:32:37.490: ISAKMP: (1003):Input = IKE_MESG_INTERNAL, IKE_PHASE1_DEL
*Mar 14 15:32:37.490: ISAKMP: (1003):Old State = IKE_P1_COMPLETE New State = IKE_DEST_SA
*Mar 14 15:32:37.490: ISAKMP: (1003):deleting SA reason "P1 delete notify (in)" state (I) MM_KEY_EXCH (peer 10.130.64.1)
*Mar 14 15:32:37.494: ISAKMP: (0):Unlocking peer struct 0x89878BC0 for isadb_mark_sa_deleted(), count 0
*Mar 14 15:32:37.494: ISAKMP: (0):Deleting peer node by peer_reap for 10.130.64.1: 89878BC0
*Mar 14 15:32:37.494: ISAKMP: (1003):deleting node 99910444 error FALSE reason "IKE deleted"
*Mar 14 15:32:37.494: ISAKMP: (1003):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Mar 14 15:32:37.494: ISAKMP: (1003):Old State = IKE_DEST_SA New State = IKE_DEST_SA
*Mar 14 15:32:37.494: IPSEC(key_engine): got a queue event with 1 KMI message(s)
*Mar 14 15:32:38.842: %LINK-3-UPDOWN: Interface Tunnel5, changed state to up
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide