I'm having some problems with a certain DAP that included a radius attribute. I can't get it to match a certain
Here's how it's setup right now.
User log in on VPN (ipsec, anyconnect and portal) and their access is determined by AD groups that is specified in the NPS on a 2008 server.
The DAP looks like this.
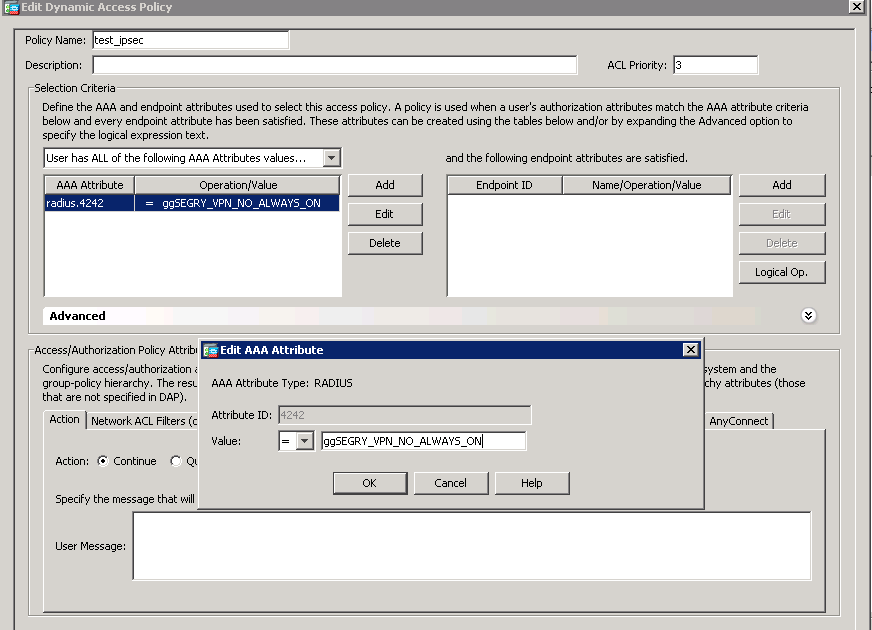
I got 4242 from this (i also found that "memberOf" could also be 145, and therefor 4241, but that didn't help)
"For RADIUS attributes, DAP defines the Attribute ID = 4096 + RADIUS ID.
For example:
The RADIUS attribute "Access Hours" has a Radius ID = 1, therefore DAP attribute value = 4096 + 1 = 4097.
The RADIUS attribute "Member Of" has a Radius ID = 146, therefore DAP attribute value = 4096 + 146 = 4242."
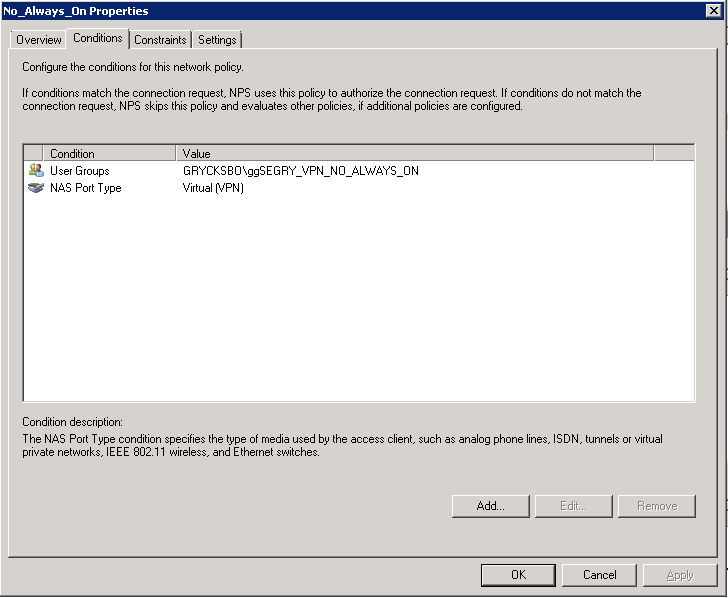
The NPS Network policy looks like this.
In the log you can see that it's using DfltAccessPolicy and therefore denying access.
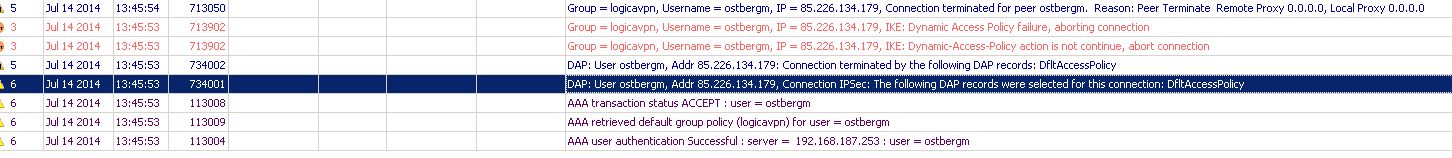
The authentication server is set on RADIUS and if I try my account there it works.
My account is in the right group (ggSEGRY_VPN_NO_ALWAYS_ON)
As soon I a remove the radius attribute it's working, but I need it to force some other polices on certain users.
I'm really out of ideas here, anyone?
Any ideas?