- Cisco Community
- Technology and Support
- Security
- VPN
- Re: How to restrict users of LDAP group to login to only particular VPN Group policy?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to restrict users of LDAP group to login to only particular VPN Group policy?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2017 04:15 AM - edited 02-21-2020 09:25 PM
I am using ASA with firepower service (9.6 version), And I want to restrict users of particular LDAP group to login only to particular VPN group policy not to other policy.
Right now I have configured tunnel-group with LDAP login , But contains all the users of domain.
How can achieve the desired configuration ?
PLease find below my current configuration for LDAP,
tunnel-group Anyconnect_LDAP type remote-access
tunnel-group Anyconnect_LDAP general-attributes
address-pool Anyconnect_LDAP_pool
authentication-server-group LDAP
default-group-policy Anyconnect_LDAP
tunnel-group Anyconnect_LDAP webvpn-attributes
group-alias Anyconnect_LDAP enable
aaa-server LDAP protocol ldap
aaa-server LDAP (inside) host x.x.x.x
ldap-base-dn dc=XX,dc=YY
ldap-scope subtree
ldap-naming-attribute sAMAccountName
ldap-login-password ****
ldap-login-dn CN=ASA admin,OU=users,DC=XX,DC=YY
server-type microsoft
- Labels:
-
Other VPN Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2017 06:11 AM
You can use ldap attribute-map.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2017 10:28 PM
HI Bogdan,
Thank you for the response, But can you please share configuration example because I am new to ASA and AD also.
If I have xx-user user from xx-ldap-grp LDAP group and it can only login to particuar group-policy xx-grp-policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2017 01:26 AM
It looks like you already defined the ldap server, so you will need to define the ldap-map.
ldap attribute-map LDAP-MAP
map-name memberOf IETF-Radius-Class
map-value memberOf CN=xx-ldap-grp LDAP,OU=users,DC=XX,DC=YY xx-grp-policy
When defining the AD group you need to use the Distinguished Name, dsquery can be used for that.
For instance 'dsquery group DC=XX,DC=YY' will show all groups in the domain DC=XX,DC=YY, and then display their distinguished names.
Then you need to apply the ldap-map to the AAA server group:
aaa-server LDAP (inside) host x.x.x.x
ldap-attribute-map LDAP-MAP
In order to prevent users to connect to the wrong group-policy and gain unauthorized access you can configure a noaccess group-policy and assign it as default in the tunnel-group.
group-policy NOACCESS internal
group-policy NOACCESS attributes
vpn-simultaneous-logins 0
vpn-tunnel-protocol IPSec webvpn
tunnel-group Anyconnect_LDAP general-attributes
default-group-policy NOACCESS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2017 03:10 AM
once again thanks for the reply,
So for AD i need to create dsquery group? simple LDAP group will not work? Is this dsquery is something i need to use? Wht is dsquery
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2017 03:17 AM
dsquery is a tool that can help you retrieve the group distinguished name you need to configure in the ldap attribute-map
https://technet.microsoft.com/en-us/library/cc732952(v=ws.11).aspx
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-21-2017 11:20 AM
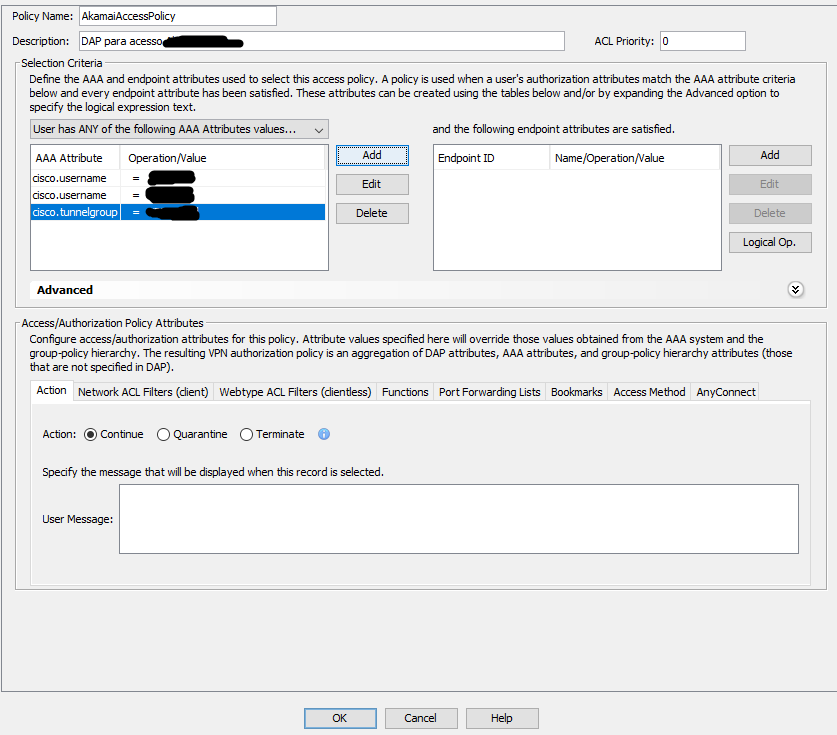
You have to configure a DAP (only possible through ASDM).
Basicaly you will need to create two conditions on DAP:
1) Member of group X
2) VPN Group y
Action = Permit
Have a look here:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2018 01:53 AM
Thanks for the response Andre!!
Can you give me an example of the same!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2018 03:09 AM
See the image:
But in your case you will use LDAP attribute (memberOf), and will have to set "User has ALL of the following AAA Attributes...".
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide