- Cisco Community
- Technology and Support
- Security
- VPN
- Re: IKEv2 ipsec split tunnel not work
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
IKEv2 ipsec split tunnel not work
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-23-2022 01:54 PM
Hi everyone.
I need help with Flex VPN configuration on ISR4331 (IOS 16.06.05) in remote access schema - different clients must connect to router and get access to different networks (split tunneling).
VPN clients are Android Strongswan, Linux Strongswan and native Windows 10/11 VPN clients.
I configured IKEv2 VPN with certificate authentication, clients connect correct but they send all traffic to tunnel, every client have acces to every network behind the router and use tunnel like default route even if I set "not use tunnel as default" in client.
My config look like this:
!
aaa new-model
!
aaa authorization network IKE2_AUTHOR_LOCAL local
!
crypto pki trustpoint router
enrollment pkcs12
revocation-check none
rsakeypair router
!
crypto pki certificate map CERT_MAP 10
subject-name co android
!
crypto ikev2 authorization policy IKE2_AUTHOR_POLICY
pool vpn_pool
route set access-list test
!
crypto ikev2 proposal ikev2-proposal
encryption aes-cbc-128
integrity sha1
group 14
!
crypto ikev2 policy ikev2-policy
proposal ikev2-proposal
!
crypto ikev2 profile PROF
match certificate CERT_MAP
identity local address 1.2.3.4
authentication remote rsa-sig
authentication local rsa-sig
pki trustpoint router
dpd 120 5 on-demand
nat keepalive 15
aaa authorization group cert list IKE2_AUTHOR_LOCAL IKE2_AUTHOR_POLICY
virtual-template 10
!
no crypto ikev2 http-url cert
!
crypto ipsec transform-set 3DES-MD5 esp-aes esp-sha-hmac
mode tunnel
!
crypto ipsec profile PROF
set transform-set 3DES-MD5
set ikev2-profile PROF
!
interface Loopback172
description Loopback for VPN
ip address 172.16.16.254 255.255.255.0
!
interface Virtual-Template10 type tunnel
ip unnumbered Loopback172
tunnel mode ipsec ipv4
tunnel protection ipsec profile PROF
!
ip local pool vpn_pool 172.16.16.1 172.16.16.128
!
ip access-list standard test
permit 192.168.99.0 0.0.0.255
!
Also I try use "route set interface" and "route set remote/local" and situation the same - split tunneling not work.
Where i have error in configuration?
Thank!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2022 01:23 AM
@AndriiD I believe that split-tunnelling is only supported if using AnyConnect VPN client, not 3rd party VPN clients.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2022 04:22 AM
Rob, thank you.
I will try use AnyConnect VPN client.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2022 05:23 AM
route set depend on ACL you use for IPSec,
what can you try is add
ACL with permit source <you split LAN> destination <any>
and then set route
here the VPN header will build static route from ACL and send it to VPN client.
try this way
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2022 05:46 AM
I try use extended ACL, but client still have access to all networks behind the router.
I use ACL like this:
Extended IP access list test
10 permit ip 192.168.99.0 0.0.0.255 any
20 deny ip any any
And i try with and without "deny" statement.
And one more thing - in some configuration examples I see info about use only standart ACL for split route...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2022 05:54 AM - edited 07-24-2022 08:22 AM
route set interface
route set access-list test
as @Rob Ingram mention only standard ACL not extended.
try the following
config under IKEv2 authz
route set interface <- add the next-hop of static route
route set access-list test <- the prefix of static route
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2022 06:18 AM - edited 07-24-2022 08:23 AM
when finish
in client PC
route print to see if the static route is add or not
debug aaa authz
check if the router send the route to VPN if it send then issue with client if not then the issue in router config.
if you can share it here
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2022 10:36 AM
After connection on clients (Android phone and Linux laptop) no routes.
Problem not in clients because when I use another VPN server (Mikrotik router and Linux Strongswan) everything works fine
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2022 10:40 AM
$ sudo route -n
this for linux
just see if the route is push from the Cisco Router to VPN client.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2022 11:47 AM
No routes pushed to client after connection
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2022 12:12 PM - edited 07-24-2022 12:26 PM
I will check my note and update you later
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2022 12:53 PM
I think I'm lost aaa authentication section in crypto ikev2 profile.
In logs I see this:
*Jul 24 19:43:03.912: AAA/AUTHOR: auth_need : user= 'adm' ruser= 'R1'rem_addr= '1.2.3.4' priv= 15 list= '' AUTHOR-TYPE= 'commands'
*Jul 24 19:43:10.498: AAA/BIND(000011BC): Bind i/f
*Jul 24 19:43:10.498: AAA/AUTHOR (0x11BC): Pick method list 'IKE2_AUTHOR_LOCAL'
*Jul 24 19:43:10.499: AAA/BIND(000011BD): Bind i/f
*Jul 24 19:43:10.499: AAA/AUTHOR (0x11BD): Invalid method list id=0x0
*Jul 24 19:43:36.785: AAA/AUTHOR: auth_need : user= 'adm' ruser= 'R1'rem_addr= '1.2.3.4' priv= 15 list= '' AUTHOR-TYPE= 'commands'
*Jul 24 19:43:39.316: AAA/AUTHOR: auth_need : user= 'adm' ruser= 'R1'rem_addr= '1.2.3.4' priv= 0 list= '' AUTHOR-TYPE= 'commands'
*Jul 24 19:43:39.316: %SYS-5-CONFIG_I: Configured from console by adm on vty0 (1.2.3.4)
*Jul 24 19:43:40.455: AAA/AUTHOR: auth_need : user= 'adm' ruser= 'R1'rem_addr= '1.2.3.4' priv= 15 list= '' AUTHOR-TYPE= 'commands'
*Jul 24 19:45:52.467: AAA/AUTHOR: auth_need : user= 'adm' ruser= 'R1'rem_addr= '1.2.3.4' priv= 15 list= '' AUTHOR-TYPE= 'commands'
*Jul 24 19:46:03.883: AAA/BIND(000011BE): Bind i/f
*Jul 24 19:46:03.883: AAA/AUTHOR (0x11BE): Pick method list 'IKE2_AUTHOR_LOCAL'
*Jul 24 19:46:03.886: %LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access1, changed state to down
*Jul 24 19:46:03.981: %LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access1, changed state to up
adm is username of single user who presen on router, maybe I need create user for everyone vpn users?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2022 01:14 PM
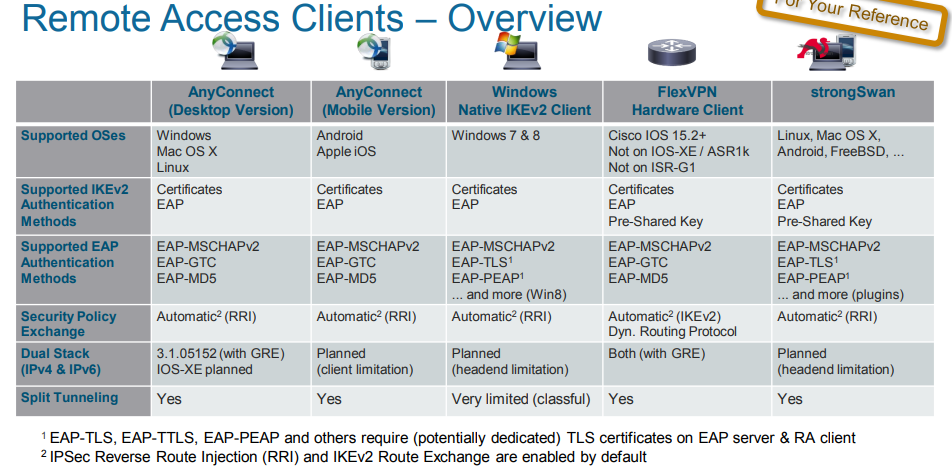
according to CiscoLive, 3th party RA is support.
split tunneling is support.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2022 01:20 PM - edited 07-24-2022 01:21 PM
aaa authorization network IKE2_AUTHOR_LOCAL local <- delete this
!
crypto ikev2 authorization policy IKE2_AUTHOR_POLICY
pool vpn_pool
route set access-list test
!
crypto ikev2 profile PROF
aaa authorization group cert list default IKE2_AUTHOR_POLICY
!
ip access-list standard test
permit 192.168.99.0 0.0.0.255 <-remember only classful for Win
Hope this work
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2022 01:37 PM
No this don't work.
In log I see this:
*Jul 24 20:32:59.631: AAA/AUTHOR: auth_need : user= 'copyrightbanneruser' ruser= 'R1'rem_addr= 'async' priv= 15 list= '' AUTHOR-TYPE= 'commands'
*Jul 24 20:34:15.191: AAA/BIND(000011CD): Bind i/f
*Jul 24 20:34:15.191: AAA/AUTHOR (0x11CD): Invalid method list id=0x0
i thin this because I delete network authorization list.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide