- Cisco Community
- Technology and Support
- Security
- VPN
- IPSEC IKEv2 not establishing between ASA 1150 and Opengear
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
IPSEC IKEv2 not establishing between ASA 1150 and Opengear
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-29-2024 07:12 AM
Hej
I am trying to setup a IPSEC IKEv2 tunnel between an ASA1150 and an Opengear OM1208 device.
I am wondering what am I missing. I use a similar config between ASAv-ASAv and it works ok.
Host-1----172.16.68.0/24------ASA----------Opengear----172.16.69.0/24----Host-2
ASA Config
interface GigabitEthernet0/0
nameif MGMT
security-level 100
ip address 10.250.3.25 255.255.252.0
!
interface GigabitEthernet0/3
nameif UBUNTU-1-OPENGEAR-IPSEC
security-level 100
ip address 172.16.68.1 255.255.255.0
!
access-list MGMT extended permit ip any any
access-list UBUNTU-1-OPENGEAR-IPSEC extended permit ip any any
access-group MGMT in interface MGMT
access-group UBUNTU-1-OPENGEAR-IPSEC in interface UBUNTU-1-OPENGEAR-IPSEC
route MGMT 10.0.0.0 255.255.255.0 10.250.0.1
route MGMT 172.16.69.0 255.255.255.0 10.250.0.1 1
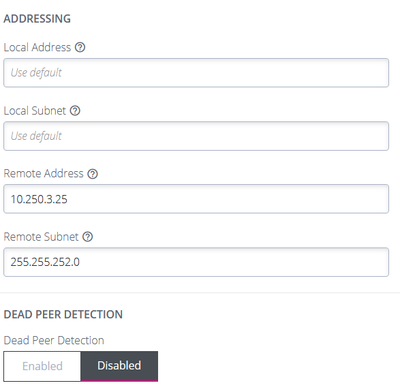
object network OPENGEAR-IPSEC-LOCAL
subnet 172.16.68.0 255.255.255.0
object network OPENGEAR-IPSEC-REMOTE
subnet 172.16.69.0 255.255.255.0
access-list OPENGEAR-IPSEC extended permit ip object OPENGEAR-IPSEC-LOCAL object OPENGEAR-IPSEC-REMOTE
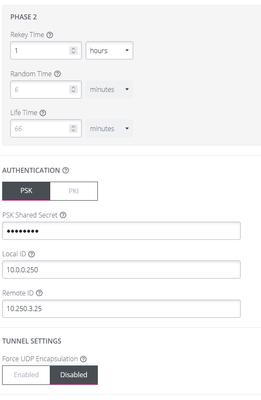
crypto ipsec ikev2 ipsec-proposal OPENGEAR-IPSEC-PROPOSAL
protocol esp encryption aes-256
protocol esp integrity sha-512
crypto ipsec security-association pmtu-aging infinite
crypto map OPENGEAR-1 1 match address OPENGEAR-IPSEC
crypto map OPENGEAR-1 1 set peer 10.0.0.250
crypto map OPENGEAR-1 1 set ikev2 ipsec-proposal OPENGEAR-IPSEC-PROPOSAL
crypto map OPENGEAR-1 interface MGMT
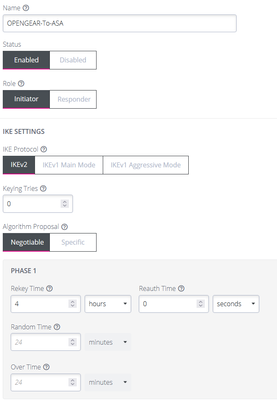
crypto ikev2 policy 10
encryption aes-256
integrity sha512
group 19
prf sha256
lifetime seconds 86400
crypto ikev2 enable MGMT
group-policy OPENGEAR-IPSEC internal
tunnel-group 10.0.0.250 type ipsec-l2l
tunnel-group 10.0.0.250 general-attributes
default-group-policy OPENGEAR-IPSEC
tunnel-group 10.0.0.250 ipsec-attributes
ikev2 remote-authentication pre-shared-key XXXXX
ikev2 local-authentication pre-shared-key XXXXXASA Packet trace Outside-to-Inside
FW-3(config)# packet-tracer input MGMT tcp 172.16.69.2 bgp 172.16.68.2 bgp det$
Phase: 1
Type: ROUTE-LOOKUP
Subtype: No ECMP load balancing
Result: ALLOW
Elapsed time: 26424 ns
Config:
Additional Information:
Destination is locally connected. No ECMP load balancing.
Found next-hop 172.16.68.2 using egress ifc UBUNTU-1-OPENGEAR-IPSEC
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Elapsed time: 8930 ns
Config:
access-group MGMT in interface MGMT
access-list MGMT extended permit ip any any
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7fb0654b7f50, priority=13, domain=permit, deny=false
hits=7, user_data=0x7fb04b7b1d00, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=MGMT, output_ifc=any
Phase: 3
Type: NAT
Subtype: per-session
Result: ALLOW
Elapsed time: 8930 ns
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7fb06505d300, priority=0, domain=nat-per-session, deny=false
hits=3733, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 4
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Elapsed time: 8930 ns
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7fb065466130, priority=0, domain=inspect-ip-options, deny=true
hits=6721, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=MGMT, output_ifc=any
Phase: 5
Type: QOS
Subtype:
Result: ALLOW
Elapsed time: 160379 ns
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7fb065415f20, priority=70, domain=qos-per-class, deny=false
hits=3936, user_data=0x7fb0653b3960, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 6
Type: VPN
Subtype: ipsec-tunnel-flow
Result: DROP
Elapsed time: 2202 ns
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7fb065e85320, priority=70, domain=ipsec-tunnel-flow, deny=false
hits=3, user_data=0x0, cs_id=0x7fb065c51610, reverse, flags=0x0, protocol=0
src ip/id=172.16.69.0, mask=255.255.255.0, port=0, tag=any
dst ip/id=172.16.68.0, mask=255.255.255.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=MGMT, output_ifc=any
Result:
input-interface: MGMT
input-status: up
input-line-status: up
output-interface: UBUNTU-1-OPENGEAR-IPSEC
output-status: up
output-line-status: up
Action: drop
Time Taken: 215795 ns
Drop-reason: (acl-drop) Flow is denied by configured rule, Drop-location: frame 0x0000561c24a5e4c0 flow (NA)/NAASA Packet trace Inside-to-Outside
FW-3(config)# packet-tracer input UBUNTU-1-OPENGEAR-IPSEC tcp 172.16.68.2 bgp $
Phase: 1
Type: INPUT-ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Elapsed time: 19818 ns
Config:
Additional Information:
Found next-hop 10.0.0.1 using egress ifc MGMT
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Elapsed time: 6116 ns
Config:
access-group UBUNTU-1-OPENGEAR-IPSEC in interface UBUNTU-1-OPENGEAR-IPSEC
access-list UBUNTU-1-OPENGEAR-IPSEC extended permit ip any any
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7fb066d6cf80, priority=13, domain=permit, deny=false
hits=96, user_data=0x7fb04b7b1400, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=UBUNTU-1-OPENGEAR-IPSEC, output_ifc=any
Phase: 3
Type: NAT
Subtype: per-session
Result: ALLOW
Elapsed time: 6116 ns
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7fb06505d300, priority=0, domain=nat-per-session, deny=false
hits=3734, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 4
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Elapsed time: 6116 ns
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7fb065e659e0, priority=0, domain=inspect-ip-options, deny=true
hits=111, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=UBUNTU-1-OPENGEAR-IPSEC, output_ifc=any
Phase: 5
Type: QOS
Subtype:
Result: ALLOW
Elapsed time: 19451 ns
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7fb065415f20, priority=70, domain=qos-per-class, deny=false
hits=3937, user_data=0x7fb0653b3960, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 6
Type: VPN
Subtype: encrypt
Result: DROP
Elapsed time: 4037 ns
Config:
Additional Information:
Forward Flow based lookup yields rule:
out id=0x7fb065e84b80, priority=70, domain=encrypt, deny=false
hits=102, user_data=0x0, cs_id=0x7fb065c51610, reverse, flags=0x0, protocol=0
src ip/id=172.16.68.0, mask=255.255.255.0, port=0, tag=any
dst ip/id=172.16.69.0, mask=255.255.255.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=MGMT
Result:
input-interface: UBUNTU-1-OPENGEAR-IPSEC
input-status: up
input-line-status: up
output-interface: MGMT
output-status: up
output-line-status: up
Action: drop
Time Taken: 61654 ns
Drop-reason: (acl-drop) Flow is denied by configured rule, Drop-location: frame 0x0000561c24a5e4c0 flow (NA)/NAASA Debug
IKEv2-PLAT-4: Received PFKEY Acquire SA for SPI 0x0, error FALSE
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-4: attempting to find tunnel group for IP: 10.0.0.250
IKEv2-PLAT-4: mapped to tunnel group 10.0.0.250 using peer IP
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-4: my_auth_method = 2
IKEv2-PLAT-4: supported_peers_auth_method = 2
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-4: ISAKMP P1 ID = 0
IKEv2-PLAT-4: Translating IKE_ID_AUTO to = 254
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-4: Received PFKEY SPI callback for SPI 0xC62F2BE2, error FALSE
IKEv2-PLAT-4:
IKEv2 received all requested SPIs from CTM to initiate tunnel.
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-4: tp_name set to:
IKEv2-PLAT-4: tg_name set to: 10.0.0.250
IKEv2-PLAT-4: tunn grp type set to: L2L
IKEv2-PLAT-7: New ikev2 sa request admitted
IKEv2-PLAT-7: Incrementing outgoing negotiating sa count by one
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: IDLE Event: EV_INIT_SA
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_GET_IKE_POLICY
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_SET_POLICY
IKEv2-PROTO-7: (32): Setting configured policies
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_CHK_AUTH4PKI
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_GEN_DH_KEY
IKEv2-PROTO-4: (32): [IKEv2 -> Crypto Engine] Computing DH public key, DH Group 19
IKEv2-PROTO-4: (32): Request queued for computation of DH key
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_NO_EVENT
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_OK_RECD_DH_PUBKEY_RESP
IKEv2-PROTO-7: (32): Action: Action_Null
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_GET_CONFIG_MODE
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_BLD_MSG
IKEv2-PROTO-4: (32): Generating IKE_SA_INIT message
IKEv2-PROTO-4: (32): IKE Proposal: 1, SPI size: 0 (initial negotiation),
Num. transforms: 4
(32): AES-CBC(32): SHA512(32): SHA512(32): DH_GROUP_256_ECP/Group 19IKEv2-PROTO-7: Construct Vendor Specific Payload: DELETE-REASONIKEv2-PROTO-7: Construct Vendor Specific Payload: (CUSTOM)IKEv2-PROTO-7: Construct Notify Payload: NAT_DETECTION_SOURCE_IPIKEv2-PROTO-7: Construct Notify Payload: NAT_DETECTION_DESTINATION_IPIKEv2-PROTO-7: Construct Notify Payload: IKEV2_FRAGMENTATION_SUPPORTEDIKEv2-PROTO-7: Construct Vendor Specific Payload: FRAGMENTATION(32):
IKEv2-PROTO-4: (32): Sending Packet [To 10.0.0.250:500/From 10.250.3.25:500/VRF i0:f0]
(32): Initiator SPI : 98F8243DC22B2F9B - Responder SPI : 0000000000000000 Message id: 0
(32): IKEv2 IKE_SA_INIT Exchange REQUESTIKEv2-PROTO-5: (32): Next payload: SA, version: 2.0 (32): Exchange type: IKE_SA_INIT, flags: INITIATOR (32): Message id: 0, length: 382(32):
Payload contents:
(32): SA(32): Next payload: KE, reserved: 0x0, length: 48
(32): last proposal: 0x0, reserved: 0x0, length: 44
Proposal: 1, Protocol id: IKE, SPI size: 0, #trans: 4(32): last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
(32): last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: SHA512
(32): last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA512
(32): last transform: 0x0, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_256_ECP/Group 19
(32): KE(32): Next payload: N, reserved: 0x0, length: 72
(32): DH group: 19, Reserved: 0x0
(32):
(32): 58 40 08 bf e6 ab b1 15 84 81 5d a3 08 bd 73 90
(32): 7f 4f ca af c2 4a c9 ea 8d 39 64 95 49 62 d2 7b
(32): e9 b9 31 ad 25 d8 8e 07 de 65 ff 19 ae da fc 81
(32): d1 82 9c a3 7c 90 5e 2f e1 8e d2 25 cc b2 54 ff
(32): N(32): Next payload: VID, reserved: 0x0, length: 68
(32):
(32): 3b 94 ee 53 06 1e 3c 01 01 5f 43 a7 2f 1b d0 e1
(32): f5 af 71 c0 ec 26 c1 47 49 17 e5 63 7d cb 32 02
(32): 2a 92 0f 9e a0 53 28 91 0b 4d 81 89 24 b4 7a 28
(32): 1b 2b 6b 21 c5 64 44 a3 b7 3b 8e e4 1f 8a a8 3d
(32): VID(32): Next payload: VID, reserved: 0x0, length: 23
(32):
(32): 43 49 53 43 4f 2d 44 45 4c 45 54 45 2d 52 45 41
(32): 53 4f 4e
(32): VID(32): Next payload: NOTIFY, reserved: 0x0, length: 59
(32):
(32): 43 49 53 43 4f 28 43 4f 50 59 52 49 47 48 54 29
(32): 26 43 6f 70 79 72 69 67 68 74 20 28 63 29 20 32
(32): 30 30 39 20 43 69 73 63 6f 20 53 79 73 74 65 6d
(32): 73 2c 20 49 6e 63 2e
(32): NOTIFY(NAT_DETECTION_SOURCE_IP)(32): Next payload: NOTIFY, reserved: 0x0, length: 28
(32): Security protocol id: IKE, spi size: 0, type: NAT_DETECTION_SOURCE_IP
(32):
(32): 08 6f 6f 2e 6c 69 67 b0 66 44 d2 a8 87 1b f9 8c
(32): fd 40 e7 31
(32): NOTIFY(NAT_DETECTION_DESTINATION_IP)(32): Next payload: NOTIFY, reserved: 0x0, length: 28
(32): Security protocol id: IKE, spi size: 0, type: NAT_DETECTION_DESTINATION_IP
(32):
(32): c7 a4 08 4b 3a 17 2d fb 4c d5 3e d5 e8 30 d2 47
(32): 3a 3b 54 fb
(32): NOTIFY(IKEV2_FRAGMENTATION_SUPPORTED)(32): Next payload: VID, reserved: 0x0, length: 8
(32): Security protocol id: Unknown - 0, spi size: 0, type: IKEV2_FRAGMENTATION_SUPPORTED
(32): VID(32): Next payload: NONE, reserved: 0x0, length: 20
(32):
(32): 40 48 b7 d5 6e bc e8 85 25 e7 de 7f 00 d6 c2 d3
(32):
IKEv2-PLAT-5: (32): SENT PKT [IKE_SA_INIT] [10.250.3.25]:500->[10.0.0.250]:500 InitSPI=0x98f8243dc22b2f9b RespSPI=0x0000000000000000 MID=00000000
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_INSERT_SA
IKEv2-PROTO-4: (32): Insert SA
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_WAIT_INIT Event: EV_NO_EVENT
IKEv2 Recv RAW packet dump
98 f8 24 3d c2 2b 2f 9b bf 26 0d 3b 50 2c 6e 80 | ..$=.+/..&.;P,n.
21 20 22 20 00 00 00 00 00 00 01 08 22 00 00 30 | ! " ........"..0
00 00 00 2c 01 01 00 04 03 00 00 0c 01 00 00 0c | ...,............
80 0e 01 00 03 00 00 08 03 00 00 0e 03 00 00 08 | ................
02 00 00 07 00 00 00 08 04 00 00 13 28 00 00 48 | ............(..H
00 13 00 00 69 4a a7 0c 8c c4 c8 11 f6 8c 6f 96 | ....iJ........o.
3e 64 5c 34 e0 48 24 6c 8c 20 19 8b 62 28 bd 02 | >d\4.H$l. ..b(..
26 c8 36 ce 38 bb 4e c1 9a dd 56 92 62 f1 38 3f | &.6.8.N...V.b.8?
83 b0 76 c2 bf 07 02 d4 1c d5 9a 1f 0b 70 cb d6 | ..v..........p..
40 66 0a df 29 00 00 24 18 bb 93 a3 85 68 70 d4 | @f..)..$.....hp.
92 48 c0 38 dc 08 12 83 65 b0 75 0b 09 47 cf db | .H.8....e.u..G..
b3 3a 9e bf a2 c1 cc 12 29 00 00 1c 00 00 40 04 | .:......).....@.
2c 79 8d 9b 0b 3a 1d fd 18 36 2e bc d5 61 0b 34 | ,y...:...6...a.4
84 66 8c 14 29 00 00 1c 00 00 40 05 fc 2e a8 3c | .f..).....@....<
e1 b2 fb 04 52 cc 6e 38 7f af 4d 95 1e 72 69 80 | ....R.n8.M..ri.
29 00 00 08 00 00 40 2e 29 00 00 08 00 00 40 22 | ).....@.).....@"
00 00 00 08 00 00 40 14 | ......@.
IKEv2-PLAT-5: RECV PKT [IKE_SA_INIT] [10.0.0.250]:500->[10.250.3.25]:500 InitSPI=0x98f8243dc22b2f9b RespSPI=0xbf260d3b502c6e80 MID=00000000
(32):
IKEv2-PROTO-4: (32): Received Packet [From 10.0.0.250:500/To 10.250.3.25:500/VRF i0:f0]
(32): Initiator SPI : 98F8243DC22B2F9B - Responder SPI : BF260D3B502C6E80 Message id: 0
(32): IKEv2 IKE_SA_INIT Exchange RESPONSEIKEv2-PROTO-5: (32): Next payload: SA, version: 2.0 (32): Exchange type: IKE_SA_INIT, flags: RESPONDER MSG-RESPONSE (32): Message id: 0, length: 264(32):
Payload contents:
(32): SA(32): Next payload: KE, reserved: 0x0, length: 48
(32): last proposal: 0x0, reserved: 0x0, length: 44
Proposal: 1, Protocol id: IKE, SPI size: 0, #trans: 4(32): last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
(32): last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA512
(32): last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: SHA512
(32): last transform: 0x0, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_256_ECP/Group 19
(32): KE(32): Next payload: N, reserved: 0x0, length: 72
(32): DH group: 19, Reserved: 0x0
(32):
(32): 69 4a a7 0c 8c c4 c8 11 f6 8c 6f 96 3e 64 5c 34
(32): e0 48 24 6c 8c 20 19 8b 62 28 bd 02 26 c8 36 ce
(32): 38 bb 4e c1 9a dd 56 92 62 f1 38 3f 83 b0 76 c2
(32): bf 07 02 d4 1c d5 9a 1f 0b 70 cb d6 40 66 0a df
(32): N(32): Next payload: NOTIFY, reserved: 0x0, length: 36
(32):
(32): 18 bb 93 a3 85 68 70 d4 92 48 c0 38 dc 08 12 83
(32): 65 b0 75 0b 09 47 cf db b3 3a 9e bf a2 c1 cc 12
IKEv2-PROTO-7: Parse Notify Payload: NAT_DETECTION_SOURCE_IP(32): NOTIFY(NAT_DETECTION_SOURCE_IP)(32): Next payload: NOTIFY, reserved: 0x0, length: 28
(32): Security protocol id: Unknown - 0, spi size: 0, type: NAT_DETECTION_SOURCE_IP
(32):
(32): 2c 79 8d 9b 0b 3a 1d fd 18 36 2e bc d5 61 0b 34
(32): 84 66 8c 14
IKEv2-PROTO-7: Parse Notify Payload: NAT_DETECTION_DESTINATION_IP(32): NOTIFY(NAT_DETECTION_DESTINATION_IP)(32): Next payload: NOTIFY, reserved: 0x0, length: 28
(32): Security protocol id: Unknown - 0, spi size: 0, type: NAT_DETECTION_DESTINATION_IP
(32):
(32): fc 2e a8 3c e1 b2 fb 04 52 cc 6e 38 7f af 4d 95
(32): 1e 72 69 80
IKEv2-PROTO-7: Parse Notify Payload: IKEV2_FRAGMENTATION_SUPPORTED(32): NOTIFY(IKEV2_FRAGMENTATION_SUPPORTED)(32): Next payload: NOTIFY, reserved: 0x0, length: 8
(32): Security protocol id: Unknown - 0, spi size: 0, type: IKEV2_FRAGMENTATION_SUPPORTED
IKEv2-PROTO-7: Parse Notify Payload: Unknown - 16418(32): NOTIFY(Unknown - 16418)(32): Next payload: NOTIFY, reserved: 0x0, length: 8
(32): Security protocol id: Unknown - 0, spi size: 0, type: Unknown - 0
IKEv2-PROTO-7: Parse Notify Payload: Unknown - 16404(32): NOTIFY(Unknown - 16404)(32): Next payload: NONE, reserved: 0x0, length: 8
(32): Security protocol id: Unknown - 0, spi size: 0, type: Unknown - 0
(32):
(32): Decrypted packet:(32): Data: 264 bytes
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000000 CurState: I_WAIT_INIT Event: EV_RECV_INIT
IKEv2-PROTO-7: (32): Processing IKE_SA_INIT message
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000000 CurState: I_PROC_INIT Event: EV_CHK4_NOTIFY
IKEv2-PROTO-4: (32): Processing IKE_SA_INIT message
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000000 CurState: I_PROC_INIT Event: EV_VERIFY_MSG
IKEv2-PROTO-4: (32): Verify SA init message
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000000 CurState: I_PROC_INIT Event: EV_PROC_MSG
IKEv2-PROTO-4: (32): Processing IKE_SA_INIT message
IKEv2-PLAT-4: (32): my auth method set to: 2
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000000 CurState: I_PROC_INIT Event: EV_DETECT_NAT
IKEv2-PROTO-7: (32): Process NAT discovery notify
IKEv2-PROTO-7: (32): Processing nat detect src notify
IKEv2-PROTO-7: (32): Remote address matched
IKEv2-PROTO-7: (32): Processing nat detect dst notify
IKEv2-PROTO-7: (32): Local address matched
IKEv2-PROTO-7: (32): No NAT found
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000000 CurState: I_PROC_INIT Event: EV_CHK_NAT_T
IKEv2-PROTO-4: (32): Checking NAT discovery
IKEv2-PROTO-4: (32): NAT not found
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000000 CurState: I_PROC_INIT Event: EV_CHK_CONFIG_MODE
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000000 CurState: INIT_DONE Event: EV_GEN_DH_SECRET
IKEv2-PROTO-4: (32): [IKEv2 -> Crypto Engine] Computing DH secret key, DH Group 19
IKEv2-PROTO-4: (32): Request queued for computation of DH secret
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000000 CurState: INIT_DONE Event: EV_NO_EVENT
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000000 CurState: INIT_DONE Event: EV_OK_RECD_DH_SECRET_RESP
IKEv2-PROTO-7: (32): Action: Action_Null
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000000 CurState: INIT_DONE Event: EV_GEN_SKEYID
IKEv2-PROTO-7: (32): Generate skeyid
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000000 CurState: INIT_DONE Event: EV_DONE
IKEv2-PROTO-4: (32): IETF Fragmentation is enabled
IKEv2-PROTO-4: (32): Completed SA init exchange
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000000 CurState: INIT_DONE Event: EV_CHK4_ROLE
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_GET_CONFIG_MODE
IKEv2-PLAT-4: Build config mode reply: no request stored
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_CHK_FOR_PPK
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_CHK_PPK_MAND
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_CHK_EAP
IKEv2-PROTO-4: (32): Check for EAP exchange
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_GEN_AUTH
IKEv2-PROTO-4: (32): Generate my authentication data
IKEv2-PROTO-4: (32): Use preshared key for id 10.250.3.25, key len 8
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_GEN_FALLBACK_AUTH
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_CHK_AUTH_TYPE
IKEv2-PROTO-4: (32): Get my authentication method
IKEv2-PROTO-4: (32): My authentication method is 'PSK'
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_OK_AUTH_GEN
IKEv2-PROTO-4: (32): Check for EAP exchange
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_SEND_AUTH
IKEv2-PROTO-4: (32): Generating IKE_AUTH message
IKEv2-PROTO-7: Construct Vendor Specific Payload: CISCO-GRANITEIKEv2-PROTO-4: (32): Constructing IDi payload: '10.250.3.25' of type 'IPv4 address'
IKEv2-PROTO-4: (32): ESP Proposal: 1, SPI size: 4 (IPSec negotiation),
Num. transforms: 3
(32): AES-CBC(32): SHA512(32): Don't use ESNIKEv2-PROTO-7: Construct Notify Payload: INITIAL_CONTACTIKEv2-PROTO-7: Construct Notify Payload: ESP_TFC_NO_SUPPORTIKEv2-PROTO-7: Construct Notify Payload: NON_FIRST_FRAGSIKEv2-PROTO-4: (32): Building packet for encryption.
(32):
Payload contents:
(32): VID(32): Next payload: IDi, reserved: 0x0, length: 20
(32):
(32): 9a f8 25 3d d1 1c dc dc 8a 19 49 0b ad b4 b3 cb
(32): IDi(32): Next payload: AUTH, reserved: 0x0, length: 12
(32): Id type: IPv4 address, Reserved: 0x0 0x0
(32):
(32): 0a fa 03 19
(32): AUTH(32): Next payload: SA, reserved: 0x0, length: 72
(32): Auth method PSK, reserved: 0x0, reserved 0x0
(32): Auth data: 64 bytes
(32): SA(32): Next payload: TSi, reserved: 0x0, length: 44
(32): last proposal: 0x0, reserved: 0x0, length: 40
Proposal: 1, Protocol id: ESP, SPI size: 4, #trans: 3(32): last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
(32): last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA512
(32): last transform: 0x0, reserved: 0x0: length: 8
type: 5, reserved: 0x0, id: Don't use ESN
(32): TSi(32): Next payload: TSr, reserved: 0x0, length: 40
(32): Num of TSs: 2, reserved 0x0, reserved 0x0
(32): TS type: TS_IPV4_ADDR_RANGE, proto id: 0, length: 16
(32): start port: 0, end port: 65535
(32): start addr: 172.16.68.2, end addr: 172.16.68.2
(32): TS type: TS_IPV4_ADDR_RANGE, proto id: 0, length: 16
(32): start port: 0, end port: 65535
(32): start addr: 172.16.68.0, end addr: 172.16.68.255
(32): TSr(32): Next payload: NOTIFY, reserved: 0x0, length: 40
(32): Num of TSs: 2, reserved 0x0, reserved 0x0
(32): TS type: TS_IPV4_ADDR_RANGE, proto id: 0, length: 16
(32): start port: 0, end port: 65535
(32): start addr: 172.16.69.2, end addr: 172.16.69.2
(32): TS type: TS_IPV4_ADDR_RANGE, proto id: 0, length: 16
(32): start port: 0, end port: 65535
(32): start addr: 172.16.69.0, end addr: 172.16.69.255
(32): NOTIFY(INITIAL_CONTACT)(32): Next payload: NOTIFY, reserved: 0x0, length: 8
(32): Security protocol id: IKE, spi size: 0, type: INITIAL_CONTACT
(32): NOTIFY(ESP_TFC_NO_SUPPORT)(32): Next payload: NOTIFY, reserved: 0x0, length: 8
(32): Security protocol id: IKE, spi size: 0, type: ESP_TFC_NO_SUPPORT
(32): NOTIFY(NON_FIRST_FRAGS)(32): Next payload: NONE, reserved: 0x0, length: 8
(32): Security protocol id: IKE, spi size: 0, type: NON_FIRST_FRAGS
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: I_BLD_AUTH Event: EV_ENCRYPT_MSG
IKEv2-PLAT-4: (32): Encrypt success status returned via ipc 1
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: I_BLD_AUTH Event: EV_NO_EVENT
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: I_BLD_AUTH Event: EV_OK_ENCRYPT_RESP
IKEv2-PROTO-7: (32): Action: Action_Null
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: I_BLD_AUTH Event: EV_TRYSEND
(32):
IKEv2-PROTO-4: (32): Sending Packet [To 10.0.0.250:500/From 10.250.3.25:500/VRF i0:f0]
(32): Initiator SPI : 98F8243DC22B2F9B - Responder SPI : BF260D3B502C6E80 Message id: 1
(32): IKEv2 IKE_AUTH Exchange REQUESTIKEv2-PROTO-5: (32): Next payload: ENCR, version: 2.0 (32): Exchange type: IKE_AUTH, flags: INITIATOR (32): Message id: 1, length: 336(32):
Payload contents:
(32): ENCR(32): Next payload: VID, reserved: 0x0, length: 308
(32): Encrypted data: 304 bytes
(32):
IKEv2-PLAT-5: (32): SENT PKT [IKE_AUTH] [10.250.3.25]:500->[10.0.0.250]:500 InitSPI=0x98f8243dc22b2f9b RespSPI=0xbf260d3b502c6e80 MID=00000001
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: I_BLD_AUTH Event: EV_CHK_EAP_POST_ASYNC
IKEv2-PROTO-4: (32): Check for EAP exchange
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: I_WAIT_AUTH Event: EV_NO_EVENT
IKEv2 Recv RAW packet dump
98 f8 24 3d c2 2b 2f 9b bf 26 0d 3b 50 2c 6e 80 | ..$=.+/..&.;P,n.
2e 20 23 20 00 00 00 01 00 00 00 b0 24 00 00 94 | . # ........$...
76 90 50 70 9e 04 b7 54 b4 7b 0f a8 f5 06 05 9b | v.Pp...T.{......
a4 cd 1b ce d0 fd 76 66 43 e9 1d b5 c9 d4 3e 08 | ......vfC.....>.
5b c6 51 2b e5 69 36 2b fd ac 72 c6 d8 95 43 96 | [.Q+.i6+..r...C.
34 cc e6 f2 7c d5 a6 87 e8 20 88 fc 05 63 6f ca | 4...|.... ...co.
1e 87 5e 67 df 06 6a 75 f1 ac 30 7b cb ba df 6a | ..^g..ju..0{...j
d0 03 d5 25 f2 bc 0e 40 1b d1 5d 46 82 72 17 79 | ...%...@..]F.r.y
3f 27 5d 3a f1 f0 ab 13 17 c6 23 78 6a 80 52 39 | ?']:......#xj.R9
c7 25 db b9 0b 87 80 51 59 6b 60 a3 20 f8 3a 52 | .%.....QYk`. .:R
c0 85 3b 8b 08 9f 88 f3 ee 50 3d a8 c4 9d ba 7b | ..;......P=....{
IKEv2-PLAT-5: RECV PKT [IKE_AUTH] [10.0.0.250]:500->[10.250.3.25]:500 InitSPI=0x98f8243dc22b2f9b RespSPI=0xbf260d3b502c6e80 MID=00000001
(32):
IKEv2-PROTO-4: (32): Received Packet [From 10.0.0.250:500/To 10.250.3.25:500/VRF i0:f0]
(32): Initiator SPI : 98F8243DC22B2F9B - Responder SPI : BF260D3B502C6E80 Message id: 1
(32): IKEv2 IKE_AUTH Exchange RESPONSEIKEv2-PROTO-5: (32): Next payload: ENCR, version: 2.0 (32): Exchange type: IKE_AUTH, flags: RESPONDER MSG-RESPONSE (32): Message id: 1, length: 176(32):
Payload contents:
IKEv2-PLAT-4: (32): Decrypt success status returned via ipc 1
IKEv2-PROTO-4: decrypt queued(32):
(32): Decrypted packet:(32): Data: 176 bytes
(32): REAL Decrypted packet:(32): Data: 92 bytes
IDr Next payload: AUTH, reserved: 0x0, length: 12
Id type: IPv4 address, Reserved: 0x0 0x0
0a 00 00 fa
AUTH Next payload: NOTIFY, reserved: 0x0, length: 72
Auth method PSK, reserved: 0x0, reserved 0x0
Auth data: 64 bytes
IKEv2-PROTO-7: Parse Notify Payload: TS_UNACCEPTABLE NOTIFY(TS_UNACCEPTABLE) Next payload: NONE, reserved: 0x0, length: 8
Security protocol id: Unknown - 0, spi size: 0, type: TS_UNACCEPTABLE
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: I_WAIT_AUTH Event: EV_RECV_AUTH
IKEv2-PROTO-7: (32): Action: Action_Null
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_CHK4_NOTIFY
IKEv2-PROTO-4: (32): Process auth response notify
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_PROC_MSG
IKEv2-PLAT-4: (32): peer auth method set to: 2
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_CHK_IF_PEER_CERT_NEEDS_TO_BE_FETCHED_FOR_PROF_SEL
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_GET_POLICY_BY_PEERID
IKEv2-PROTO-4: (32): Searching policy based on peer's identity '10.0.0.250' of type 'IPv4 address'
IKEv2-PLAT-4: (32): Site to Site connection detected
IKEv2-PLAT-4: connection initiated with tunnel group 10.0.0.250
IKEv2-PLAT-2: (32): Template number 0
IKEv2-PLAT-4: my_auth_method = 2
IKEv2-PLAT-4: supported_peers_auth_method = 2
IKEv2-PLAT-4: (32): PSH P1 ID = 1
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_VERIFY_POLICY_BY_PEERID
IKEv2-PROTO-4: (32): Verify peer's policy
IKEv2-PROTO-4: (32): Peer's policy verified
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: unknown event
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_CHK_AUTH_TYPE
IKEv2-PROTO-4: (32): Get peer's authentication method
IKEv2-PROTO-4: (32): Peer's authentication method is 'PSK'
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_GET_PRESHR_KEY
IKEv2-PROTO-4: (32): Get peer's preshared key for 10.0.0.250
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_VERIFY_AUTH
IKEv2-PROTO-4: (32): Verify peer's authentication data
IKEv2-PROTO-4: (32): Use preshared key for id 10.0.0.250, key len 8
IKEv2-PROTO-7: (32): Computing AUTH data to authenticate Peer, return code = 1
IKEv2-PROTO-4: (32): Verification of peer's authenctication data PASSED
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_CHK_EAP
IKEv2-PROTO-4: (32): Check for EAP exchange
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_NOTIFY_AUTH_DONE
IKEv2-PLAT-4: (32): Completed authentication for connection
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_CHK_CONFIG_MODE
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_CHK4_IC
IKEv2-PROTO-4: (32): Processing INITIAL_CONTACT
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_CHK_IKE_ONLY
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: AUTH_DONE Event: EV_OK
IKEv2-PROTO-7: (32): Action: Action_Null
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: AUTH_DONE Event: EV_UPDATE_CAC_STATS
IKEv2-PLAT-7: New ikev2 sa request activated
IKEv2-PLAT-7: Decrement count for outgoing negotiating
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: AUTH_DONE Event: EV_INSERT_IKE
IKEv2-PROTO-4: (32): IKEV2 SA created; inserting SA into database. SA lifetime timer (86400 sec) started
IKEv2-PLAT-4:
CONNECTION STATUS: UP... peer: 10.0.0.250:500, phase1_id: 10.0.0.250
IKEv2-PROTO-4: (32): Session with IKE ID PAIR (10.0.0.250, 10.250.3.25) is UP
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: AUTH_DONE Event: EV_REGISTER_SESSION
IKEv2-PLAT-4: (32): connection auth hdl set to 287
IKEv2-PLAT-4: (32): AAA conn attribute retrieval successfully queued for register session request.
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: AUTH_DONE Event: EV_NO_EVENT
IKEv2-PLAT-4: (32): idle timeout set to: 30
IKEv2-PLAT-4: (32): session timeout set to: 0
IKEv2-PLAT-4: (32): group policy set to OPENGEAR-IPSEC
IKEv2-PLAT-4: (32): class attr set
IKEv2-PLAT-4: (32): tunnel protocol set to: 0x4c
IKEv2-PLAT-4: (32): IPv4 filter ID not configured for connection
IKEv2-PLAT-4: (32): group lock set to: none
IKEv2-PLAT-4: (32): IPv6 filter ID not configured for connection
IKEv2-PLAT-4: (32): connection attributes set valid to TRUE
IKEv2-PLAT-4: (32): Successfully retrieved conn attrs
IKEv2-PLAT-4: (32): Session registration after conn attr retrieval PASSED, No error
IKEv2-PLAT-4: (32): connection auth hdl set to -1
IKEv2-PLAT-4:
CONNECTION STATUS: REGISTERED... peer: 10.0.0.250:500, phase1_id: 10.0.0.250
IKEv2-PROTO-4: (32): Initializing DPD, configured for 10 seconds
IKEv2-PLAT-4: mib_index set to: 501
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: AUTH_DONE Event: EV_RECD_REGISTER_SESSION_RESP
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: AUTH_DONE Event: EV_CHECK_DUPE
IKEv2-PROTO-4: (32): Checking for duplicate IKEv2 SA
IKEv2-PROTO-4: (32): No duplicate IKEv2 SA found
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: AUTH_DONE Event: EV_CHK4_ROLE
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: READY Event: EV_CHK_IKE_ONLY
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: READY Event: EV_DEL_SA
IKEv2-PROTO-4: (32): Queuing IKE SA delete request reason: unknown
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: READY Event: EV_FREE_NEG
IKEv2-PROTO-7: (32): Deleting negotiation context for my message ID: 0x1
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: READY Event: EV_DELETE
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: DELETE Event: EV_DELETE
IKEv2-PROTO-7: (32): Action: Action_Null
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: INFO_I_BLD_INFO Event: EV_SND_SA_DEL
IKEv2-PROTO-4: (32): Sending DELETE INFO message for IKEv2 SA [ISPI: 0x98F8243DC22B2F9B RSPI: 0xBF260D3B502C6E80]
IKEv2-PROTO-4: (32): Building packet for encryption.
(32):
Payload contents:
(32): DELETE(32): Next payload: NONE, reserved: 0x0, length: 8
(32): Security protocol id: IKE, spi size: 0, num of spi: 0
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: INFO_I_BLD_INFO Event: EV_ENCRYPT_MSG
IKEv2-PLAT-4: (32): Encrypt success status returned via ipc 1
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: INFO_I_BLD_INFO Event: EV_NO_EVENT
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: INFO_I_BLD_INFO Event: EV_OK_ENCRYPT_RESP
IKEv2-PROTO-7: (32): Action: Action_Null
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000001 CurState: INFO_I_BLD_INFO Event: EV_TRYSEND
IKEv2-PROTO-4: (32): Checking if request will fit in peer window
(32):
IKEv2-PROTO-4: (32): Sending Packet [To 10.0.0.250:500/From 10.250.3.25:500/VRF i0:f0]
(32): Initiator SPI : 98F8243DC22B2F9B - Responder SPI : BF260D3B502C6E80 Message id: 2
(32): IKEv2 INFORMATIONAL Exchange REQUESTIKEv2-PROTO-5: (32): Next payload: ENCR, version: 2.0 (32): Exchange type: INFORMATIONAL, flags: INITIATOR (32): Message id: 2, length: 96(32):
Payload contents:
(32): ENCR(32): Next payload: DELETE, reserved: 0x0, length: 68
(32): Encrypted data: 64 bytes
(32):
IKEv2-PLAT-5: (32): SENT PKT [INFORMATIONAL] [10.250.3.25]:500->[10.0.0.250]:500 InitSPI=0x98f8243dc22b2f9b RespSPI=0xbf260d3b502c6e80 MID=00000002
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000002 CurState: INFO_I_BLD_INFO Event: EV_CHK_INFO_TYPE
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000002 CurState: INFO_I_BLD_INFO Event: EV_CHK4_ACTIVE_SA
IKEv2-PROTO-4: (32): Check for existing active SA
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000002 CurState: INFO_I_BLD_INFO Event: EV_STOP_ACCT
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000002 CurState: INFO_I_BLD_INFO Event: EV_TERM_CONN
IKEv2-PROTO-4: (32): Delete all IKE SAs
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000002 CurState: INFO_I_WAIT Event: EV_NO_EVENT
IKEv2-PLAT-4: Received PFKEY delete SA for SPI 0xC62F2BE2 error FALSE
IKEv2-PLAT-4: PFKEY Delete Ack from IPSec
IKEv2 Recv RAW packet dump
98 f8 24 3d c2 2b 2f 9b bf 26 0d 3b 50 2c 6e 80 | ..$=.+/..&.;P,n.
2e 20 25 20 00 00 00 02 00 00 00 60 00 00 00 44 | . % .......`...D
55 84 68 a4 4a c2 4c d9 33 11 c3 51 8d 92 bf db | U.h.J.L.3..Q....
c3 4c 3b fd cf ea 07 55 de 5a a8 48 78 c0 ca b6 | .L;....U.Z.Hx...
6d a2 e3 c3 90 1d 1c a7 1d 43 8f eb ed 55 4d b4 | m........C...UM.
7e 4d f7 29 44 8e c1 2f 09 9c c7 c8 bf 23 02 cf | ~M.)D../.....#..
IKEv2-PLAT-5: RECV PKT [INFORMATIONAL] [10.0.0.250]:500->[10.250.3.25]:500 InitSPI=0x98f8243dc22b2f9b RespSPI=0xbf260d3b502c6e80 MID=00000002
(32):
IKEv2-PROTO-4: (32): Received Packet [From 10.0.0.250:500/To 10.250.3.25:500/VRF i0:f0]
(32): Initiator SPI : 98F8243DC22B2F9B - Responder SPI : BF260D3B502C6E80 Message id: 2
(32): IKEv2 INFORMATIONAL Exchange RESPONSEIKEv2-PROTO-5: (32): Next payload: ENCR, version: 2.0 (32): Exchange type: INFORMATIONAL, flags: RESPONDER MSG-RESPONSE (32): Message id: 2, length: 96(32):
Payload contents:
IKEv2-PLAT-4: (32): Decrypt success status returned via ipc 1
IKEv2-PROTO-4: decrypt queued(32):
(32): Decrypted packet:(32): Data: 96 bytes
(32): REAL Decrypted packet:(32): Data: 0 bytes
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000002 CurState: INFO_I_WAIT Event: EV_RECV_INFO_ACK
IKEv2-PROTO-4: (32): Processing ACK to informational exchange
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000002 CurState: INFO_I_WAIT Event: EV_CHK_INFO_TYPE
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000002 CurState: DELETE Event: EV_RECV_DEL_ACK
IKEv2-PROTO-7: (32): Action: Action_Null
IKEv2-PROTO-7: (32): SM Trace-> SA: I_SPI=98F8243DC22B2F9B R_SPI=BF260D3B502C6E80 (I) MsgID = 00000002 CurState: DELETE Event: EV_FREE_SA
IKEv2-PROTO-4: (32): Deleting SA
IKEv2-PLAT-4:
CONNECTION STATUS: DOWN... peer: 10.0.0.250:500, phase1_id: 10.0.0.250
IKEv2-PLAT-4: (32): IKEv2 session deregistered from session manager. Reason: 8
IKEv2-PLAT-4: (32): session manager killed ikev2 tunnel. Reason: Internal Error
IKEv2-PLAT-4: (32): Deleted associated IKE flow: MGMT, 10.250.3.25:62465 <-> 10.0.0.250:62465
IKEv2-PLAT-4: (32): PSH cleanup
IKEv2-PLAT-7: Active ike sa request deleted
IKEv2-PLAT-7: Decrement count for outgoing active
IKEv2-PLAT-4: Received PFKEY Acquire SA for SPI 0x0, error FALSE
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-4: attempting to find tunnel group for IP: 10.0.0.250
IKEv2-PLAT-4: mapped to tunnel group 10.0.0.250 using peer IP
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-4: my_auth_method = 2
IKEv2-PLAT-4: supported_peers_auth_method = 2
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-4: ISAKMP P1 ID = 0
IKEv2-PLAT-4: Translating IKE_ID_AUTO to = 254
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-4: Received PFKEY SPI callback for SPI 0xF702A0FB, error FALSE
IKEv2-PLAT-4:
IKEv2 received all requested SPIs from CTM to initiate tunnel.
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-4: tp_name set to:
IKEv2-PLAT-4: tg_name set to: 10.0.0.250
IKEv2-PLAT-4: tunn grp type set to: L2L
IKEv2-PLAT-7: New ikev2 sa request admitted
IKEv2-PLAT-7: Incrementing outgoing negotiating sa count by one
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: IDLE Event: EV_INIT_SA
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_GET_IKE_POLICY
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_SET_POLICY
IKEv2-PROTO-7: (33): Setting configured policies
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_CHK_AUTH4PKI
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_GEN_DH_KEY
IKEv2-PROTO-4: (33): [IKEv2 -> Crypto Engine] Computing DH public key, DH Group 19
IKEv2-PROTO-4: (33): Request queued for computation of DH key
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_NO_EVENT
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_OK_RECD_DH_PUBKEY_RESP
IKEv2-PROTO-7: (33): Action: Action_Null
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_GET_CONFIG_MODE
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_BLD_MSG
IKEv2-PROTO-4: (33): Generating IKE_SA_INIT message
IKEv2-PROTO-4: (33): IKE Proposal: 1, SPI size: 0 (initial negotiation),
Num. transforms: 4
(33): AES-CBC(33): SHA512(33): SHA512(33): DH_GROUP_256_ECP/Group 19IKEv2-PROTO-7: Construct Vendor Specific Payload: DELETE-REASONIKEv2-PROTO-7: Construct Vendor Specific Payload: (CUSTOM)IKEv2-PROTO-7: Construct Notify Payload: NAT_DETECTION_SOURCE_IPIKEv2-PROTO-7: Construct Notify Payload: NAT_DETECTION_DESTINATION_IPIKEv2-PROTO-7: Construct Notify Payload: IKEV2_FRAGMENTATION_SUPPORTEDIKEv2-PROTO-7: Construct Vendor Specific Payload: FRAGMENTATION(33):
IKEv2-PROTO-4: (33): Sending Packet [To 10.0.0.250:500/From 10.250.3.25:500/VRF i0:f0]
(33): Initiator SPI : 50797D141ED3E71E - Responder SPI : 0000000000000000 Message id: 0
(33): IKEv2 IKE_SA_INIT Exchange REQUESTIKEv2-PROTO-5: (33): Next payload: SA, version: 2.0 (33): Exchange type: IKE_SA_INIT, flags: INITIATOR (33): Message id: 0, length: 382(33):
Payload contents:
(33): SA(33): Next payload: KE, reserved: 0x0, length: 48
(33): last proposal: 0x0, reserved: 0x0, length: 44
Proposal: 1, Protocol id: IKE, SPI size: 0, #trans: 4(33): last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
(33): last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: SHA512
(33): last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA512
(33): last transform: 0x0, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_256_ECP/Group 19
(33): KE(33): Next payload: N, reserved: 0x0, length: 72
(33): DH group: 19, Reserved: 0x0
(33):
(33): b5 b5 76 39 de 13 0c d9 91 23 d7 0d 33 d9 ba 57
(33): a7 9c cf 45 67 f7 3d 25 f4 cd df ba 2c cf d9 38
(33): 79 cd 63 a5 ca 78 f0 8f 7f 6f 80 25 f7 e0 28 d0
(33): cf 66 76 4f 8a 7a e8 67 87 13 45 d3 42 19 ff 7c
(33): N(33): Next payload: VID, reserved: 0x0, length: 68
(33):
(33): af 9a c8 12 49 18 28 11 07 4b 00 47 cd f8 78 6c
(33): 1e d7 85 27 ff 2e dc 3e 8e 92 1d 8b b8 07 28 b1
(33): 47 3c 68 eb e1 0a d5 6f 68 aa c5 35 d4 2f 39 7c
(33): 24 f9 a8 2e eb 92 4d be 8c 29 a4 59 33 41 c4 31
(33): VID(33): Next payload: VID, reserved: 0x0, length: 23
(33):
(33): 43 49 53 43 4f 2d 44 45 4c 45 54 45 2d 52 45 41
(33): 53 4f 4e
(33): VID(33): Next payload: NOTIFY, reserved: 0x0, length: 59
(33):
(33): 43 49 53 43 4f 28 43 4f 50 59 52 49 47 48 54 29
(33): 26 43 6f 70 79 72 69 67 68 74 20 28 63 29 20 32
(33): 30 30 39 20 43 69 73 63 6f 20 53 79 73 74 65 6d
(33): 73 2c 20 49 6e 63 2e
(33): NOTIFY(NAT_DETECTION_SOURCE_IP)(33): Next payload: NOTIFY, reserved: 0x0, length: 28
(33): Security protocol id: IKE, spi size: 0, type: NAT_DETECTION_SOURCE_IP
(33):
(33): a4 24 41 3c c6 c9 a8 d0 39 d6 b3 31 36 82 d2 d7
(33): 0d b0 6b 54
(33): NOTIFY(NAT_DETECTION_DESTINATION_IP)(33): Next payload: NOTIFY, reserved: 0x0, length: 28
(33): Security protocol id: IKE, spi size: 0, type: NAT_DETECTION_DESTINATION_IP
(33):
(33): 6f 02 2e 31 c3 da 61 fa 1f eb b7 6f 60 d4 93 1b
(33): 34 e3 d4 8b
(33): NOTIFY(IKEV2_FRAGMENTATION_SUPPORTED)(33): Next payload: VID, reserved: 0x0, length: 8
(33): Security protocol id: Unknown - 0, spi size: 0, type: IKEV2_FRAGMENTATION_SUPPORTED
(33): VID(33): Next payload: NONE, reserved: 0x0, length: 20
(33):
(33): 40 48 b7 d5 6e bc e8 85 25 e7 de 7f 00 d6 c2 d3
(33):
IKEv2-PLAT-5: (33): SENT PKT [IKE_SA_INIT] [10.250.3.25]:500->[10.0.0.250]:500 InitSPI=0x50797d141ed3e71e RespSPI=0x0000000000000000 MID=00000000
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_INSERT_SA
IKEv2-PROTO-4: (33): Insert SA
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_WAIT_INIT Event: EV_NO_EVENT
IKEv2 Recv RAW packet dump
50 79 7d 14 1e d3 e7 1e 67 b5 22 4e 93 25 b5 1f | Py}.....g."N.%..
21 20 22 20 00 00 00 00 00 00 01 08 22 00 00 30 | ! " ........"..0
00 00 00 2c 01 01 00 04 03 00 00 0c 01 00 00 0c | ...,............
80 0e 01 00 03 00 00 08 03 00 00 0e 03 00 00 08 | ................
02 00 00 07 00 00 00 08 04 00 00 13 28 00 00 48 | ............(..H
00 13 00 00 a7 70 53 a2 14 7c 59 45 da db ff f1 | .....pS..|YE....
24 06 a8 5c 35 27 69 63 f8 96 24 c0 8d 40 4f 0d | $..\5'ic..$..@O.
71 1c 3f d1 9a 93 aa b5 64 1c fe 0e 5b c1 a0 41 | q.?.....d...[..A
98 d5 3f 2d 42 8a df 48 3e cf 4c 45 f1 ef 6a 8e | ..?-B..H>.LE..j.
61 02 2b 04 29 00 00 24 fc 15 ad b1 23 2d 02 37 | a.+.)..$....#-.7
1d a2 43 3d b8 09 f5 ee 69 06 2c 3a 30 ce 6d 05 | ..C=....i.,:0.m.
3f a9 1f 78 7f 44 a6 c6 29 00 00 1c 00 00 40 04 | ?..xD..).....@.
98 d5 53 5a 65 82 87 e4 75 e1 73 6c 90 8d 17 6e | ..SZe...u.sl...n
a3 9f 12 56 29 00 00 1c 00 00 40 05 e2 c8 16 3a | ...V).....@....:
80 50 81 14 0a 81 82 b6 cd 56 97 ab 19 e2 0e bd | .P.......V......
29 00 00 08 00 00 40 2e 29 00 00 08 00 00 40 22 | ).....@.).....@"
00 00 00 08 00 00 40 14 | ......@.
IKEv2-PLAT-5: RECV PKT [IKE_SA_INIT] [10.0.0.250]:500->[10.250.3.25]:500 InitSPI=0x50797d141ed3e71e RespSPI=0x67b5224e9325b51f MID=00000000
(33):
IKEv2-PROTO-4: (33): Received Packet [From 10.0.0.250:500/To 10.250.3.25:500/VRF i0:f0]
(33): Initiator SPI : 50797D141ED3E71E - Responder SPI : 67B5224E9325B51F Message id: 0
(33): IKEv2 IKE_SA_INIT Exchange RESPONSEIKEv2-PROTO-5: (33): Next payload: SA, version: 2.0 (33): Exchange type: IKE_SA_INIT, flags: RESPONDER MSG-RESPONSE (33): Message id: 0, length: 264(33):
Payload contents:
(33): SA(33): Next payload: KE, reserved: 0x0, length: 48
(33): last proposal: 0x0, reserved: 0x0, length: 44
Proposal: 1, Protocol id: IKE, SPI size: 0, #trans: 4(33): last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
(33): last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA512
(33): last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: SHA512
(33): last transform: 0x0, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_256_ECP/Group 19
(33): KE(33): Next payload: N, reserved: 0x0, length: 72
(33): DH group: 19, Reserved: 0x0
(33):
(33): a7 70 53 a2 14 7c 59 45 da db ff f1 24 06 a8 5c
(33): 35 27 69 63 f8 96 24 c0 8d 40 4f 0d 71 1c 3f d1
(33): 9a 93 aa b5 64 1c fe 0e 5b c1 a0 41 98 d5 3f 2d
(33): 42 8a df 48 3e cf 4c 45 f1 ef 6a 8e 61 02 2b 04
(33): N(33): Next payload: NOTIFY, reserved: 0x0, length: 36
(33):
(33): fc 15 ad b1 23 2d 02 37 1d a2 43 3d b8 09 f5 ee
(33): 69 06 2c 3a 30 ce 6d 05 3f a9 1f 78 7f 44 a6 c6
IKEv2-PROTO-7: Parse Notify Payload: NAT_DETECTION_SOURCE_IP(33): NOTIFY(NAT_DETECTION_SOURCE_IP)(33): Next payload: NOTIFY, reserved: 0x0, length: 28
(33): Security protocol id: Unknown - 0, spi size: 0, type: NAT_DETECTION_SOURCE_IP
(33):
(33): 98 d5 53 5a 65 82 87 e4 75 e1 73 6c 90 8d 17 6e
(33): a3 9f 12 56
IKEv2-PROTO-7: Parse Notify Payload: NAT_DETECTION_DESTINATION_IP(33): NOTIFY(NAT_DETECTION_DESTINATION_IP)(33): Next payload: NOTIFY, reserved: 0x0, length: 28
(33): Security protocol id: Unknown - 0, spi size: 0, type: NAT_DETECTION_DESTINATION_IP
(33):
(33): e2 c8 16 3a 80 50 81 14 0a 81 82 b6 cd 56 97 ab
(33): 19 e2 0e bd
IKEv2-PROTO-7: Parse Notify Payload: IKEV2_FRAGMENTATION_SUPPORTED(33): NOTIFY(IKEV2_FRAGMENTATION_SUPPORTED)(33): Next payload: NOTIFY, reserved: 0x0, length: 8
(33): Security protocol id: Unknown - 0, spi size: 0, type: IKEV2_FRAGMENTATION_SUPPORTED
IKEv2-PROTO-7: Parse Notify Payload: Unknown - 16418(33): NOTIFY(Unknown - 16418)(33): Next payload: NOTIFY, reserved: 0x0, length: 8
(33): Security protocol id: Unknown - 0, spi size: 0, type: Unknown - 0
IKEv2-PROTO-7: Parse Notify Payload: Unknown - 16404(33): NOTIFY(Unknown - 16404)(33): Next payload: NONE, reserved: 0x0, length: 8
(33): Security protocol id: Unknown - 0, spi size: 0, type: Unknown - 0
(33):
(33): Decrypted packet:(33): Data: 264 bytes
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000000 CurState: I_WAIT_INIT Event: EV_RECV_INIT
IKEv2-PROTO-7: (33): Processing IKE_SA_INIT message
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000000 CurState: I_PROC_INIT Event: EV_CHK4_NOTIFY
IKEv2-PROTO-4: (33): Processing IKE_SA_INIT message
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000000 CurState: I_PROC_INIT Event: EV_VERIFY_MSG
IKEv2-PROTO-4: (33): Verify SA init message
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000000 CurState: I_PROC_INIT Event: EV_PROC_MSG
IKEv2-PROTO-4: (33): Processing IKE_SA_INIT message
IKEv2-PLAT-4: (33): my auth method set to: 2
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000000 CurState: I_PROC_INIT Event: EV_DETECT_NAT
IKEv2-PROTO-7: (33): Process NAT discovery notify
IKEv2-PROTO-7: (33): Processing nat detect src notify
IKEv2-PROTO-7: (33): Remote address matched
IKEv2-PROTO-7: (33): Processing nat detect dst notify
IKEv2-PROTO-7: (33): Local address matched
IKEv2-PROTO-7: (33): No NAT found
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000000 CurState: I_PROC_INIT Event: EV_CHK_NAT_T
IKEv2-PROTO-4: (33): Checking NAT discovery
IKEv2-PROTO-4: (33): NAT not found
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000000 CurState: I_PROC_INIT Event: EV_CHK_CONFIG_MODE
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000000 CurState: INIT_DONE Event: EV_GEN_DH_SECRET
IKEv2-PROTO-4: (33): [IKEv2 -> Crypto Engine] Computing DH secret key, DH Group 19
IKEv2-PROTO-4: (33): Request queued for computation of DH secret
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000000 CurState: INIT_DONE Event: EV_NO_EVENT
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000000 CurState: INIT_DONE Event: EV_OK_RECD_DH_SECRET_RESP
IKEv2-PROTO-7: (33): Action: Action_Null
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000000 CurState: INIT_DONE Event: EV_GEN_SKEYID
IKEv2-PROTO-7: (33): Generate skeyid
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000000 CurState: INIT_DONE Event: EV_DONE
IKEv2-PROTO-4: (33): IETF Fragmentation is enabled
IKEv2-PROTO-4: (33): Completed SA init exchange
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000000 CurState: INIT_DONE Event: EV_CHK4_ROLE
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_GET_CONFIG_MODE
IKEv2-PLAT-4: Build config mode reply: no request stored
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_CHK_FOR_PPK
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_CHK_PPK_MAND
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_CHK_EAP
IKEv2-PROTO-4: (33): Check for EAP exchange
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_GEN_AUTH
IKEv2-PROTO-4: (33): Generate my authentication data
IKEv2-PROTO-4: (33): Use preshared key for id 10.250.3.25, key len 8
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_GEN_FALLBACK_AUTH
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_CHK_AUTH_TYPE
IKEv2-PROTO-4: (33): Get my authentication method
IKEv2-PROTO-4: (33): My authentication method is 'PSK'
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_OK_AUTH_GEN
IKEv2-PROTO-4: (33): Check for EAP exchange
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_SEND_AUTH
IKEv2-PROTO-4: (33): Generating IKE_AUTH message
IKEv2-PROTO-7: Construct Vendor Specific Payload: CISCO-GRANITEIKEv2-PROTO-4: (33): Constructing IDi payload: '10.250.3.25' of type 'IPv4 address'
IKEv2-PROTO-4: (33): ESP Proposal: 1, SPI size: 4 (IPSec negotiation),
Num. transforms: 3
(33): AES-CBC(33): SHA512(33): Don't use ESNIKEv2-PROTO-7: Construct Notify Payload: INITIAL_CONTACTIKEv2-PROTO-7: Construct Notify Payload: ESP_TFC_NO_SUPPORTIKEv2-PROTO-7: Construct Notify Payload: NON_FIRST_FRAGSIKEv2-PROTO-4: (33): Building packet for encryption.
(33):
Payload contents:
(33): VID(33): Next payload: IDi, reserved: 0x0, length: 20
(33):
(33): 52 79 7c 14 0d e4 14 59 14 ed 81 c9 38 71 2a 65
(33): IDi(33): Next payload: AUTH, reserved: 0x0, length: 12
(33): Id type: IPv4 address, Reserved: 0x0 0x0
(33):
(33): 0a fa 03 19
(33): AUTH(33): Next payload: SA, reserved: 0x0, length: 72
(33): Auth method PSK, reserved: 0x0, reserved 0x0
(33): Auth data: 64 bytes
(33): SA(33): Next payload: TSi, reserved: 0x0, length: 44
(33): last proposal: 0x0, reserved: 0x0, length: 40
Proposal: 1, Protocol id: ESP, SPI size: 4, #trans: 3(33): last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
(33): last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA512
(33): last transform: 0x0, reserved: 0x0: length: 8
type: 5, reserved: 0x0, id: Don't use ESN
(33): TSi(33): Next payload: TSr, reserved: 0x0, length: 40
(33): Num of TSs: 2, reserved 0x0, reserved 0x0
(33): TS type: TS_IPV4_ADDR_RANGE, proto id: 0, length: 16
(33): start port: 0, end port: 65535
(33): start addr: 172.16.68.2, end addr: 172.16.68.2
(33): TS type: TS_IPV4_ADDR_RANGE, proto id: 0, length: 16
(33): start port: 0, end port: 65535
(33): start addr: 172.16.68.0, end addr: 172.16.68.255
(33): TSr(33): Next payload: NOTIFY, reserved: 0x0, length: 40
(33): Num of TSs: 2, reserved 0x0, reserved 0x0
(33): TS type: TS_IPV4_ADDR_RANGE, proto id: 0, length: 16
(33): start port: 0, end port: 65535
(33): start addr: 172.16.69.2, end addr: 172.16.69.2
(33): TS type: TS_IPV4_ADDR_RANGE, proto id: 0, length: 16
(33): start port: 0, end port: 65535
(33): start addr: 172.16.69.0, end addr: 172.16.69.255
(33): NOTIFY(INITIAL_CONTACT)(33): Next payload: NOTIFY, reserved: 0x0, length: 8
(33): Security protocol id: IKE, spi size: 0, type: INITIAL_CONTACT
(33): NOTIFY(ESP_TFC_NO_SUPPORT)(33): Next payload: NOTIFY, reserved: 0x0, length: 8
(33): Security protocol id: IKE, spi size: 0, type: ESP_TFC_NO_SUPPORT
(33): NOTIFY(NON_FIRST_FRAGS)(33): Next payload: NONE, reserved: 0x0, length: 8
(33): Security protocol id: IKE, spi size: 0, type: NON_FIRST_FRAGS
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: I_BLD_AUTH Event: EV_ENCRYPT_MSG
IKEv2-PLAT-4: (33): Encrypt success status returned via ipc 1
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: I_BLD_AUTH Event: EV_NO_EVENT
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: I_BLD_AUTH Event: EV_OK_ENCRYPT_RESP
IKEv2-PROTO-7: (33): Action: Action_Null
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: I_BLD_AUTH Event: EV_TRYSEND
(33):
IKEv2-PROTO-4: (33): Sending Packet [To 10.0.0.250:500/From 10.250.3.25:500/VRF i0:f0]
(33): Initiator SPI : 50797D141ED3E71E - Responder SPI : 67B5224E9325B51F Message id: 1
(33): IKEv2 IKE_AUTH Exchange REQUESTIKEv2-PROTO-5: (33): Next payload: ENCR, version: 2.0 (33): Exchange type: IKE_AUTH, flags: INITIATOR (33): Message id: 1, length: 336(33):
Payload contents:
(33): ENCR(33): Next payload: VID, reserved: 0x0, length: 308
(33): Encrypted data: 304 bytes
(33):
IKEv2-PLAT-5: (33): SENT PKT [IKE_AUTH] [10.250.3.25]:500->[10.0.0.250]:500 InitSPI=0x50797d141ed3e71e RespSPI=0x67b5224e9325b51f MID=00000001
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: I_BLD_AUTH Event: EV_CHK_EAP_POST_ASYNC
IKEv2-PROTO-4: (33): Check for EAP exchange
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: I_WAIT_AUTH Event: EV_NO_EVENT
IKEv2 Recv RAW packet dump
50 79 7d 14 1e d3 e7 1e 67 b5 22 4e 93 25 b5 1f | Py}.....g."N.%..
2e 20 23 20 00 00 00 01 00 00 00 b0 24 00 00 94 | . # ........$...
f2 2d 05 4f d7 fd d3 bb f8 47 a5 22 f0 15 bb 59 | .-.O.....G."...Y
1a a0 fa 20 12 d2 67 b4 1f d9 31 5f f8 6b ff 1f | ... ..g...1_.k..
ad 0e 3f 4a 1c 5c d9 dc 26 23 54 14 3a 6e 03 ea | ..?J.\..&#T.:n..
da 38 76 91 40 72 ec 9a 77 dc 3d 92 ee 83 28 cd | .8v.@r..w.=...(.
8b e5 c7 79 f3 13 b4 f2 77 6c 3e 01 23 c9 27 63 | ...y....wl>.#.'c
cb c6 2c d8 2b 1c a7 5f f3 4f 74 5b 96 4b e3 4a | ..,.+.._.Ot[.K.J
8d 56 dd d7 22 ed 2f 03 6c 18 8a fe 25 27 41 b2 | .V.."./.l...%'A.
48 09 ed 71 c0 83 33 59 ba 9e 90 30 81 d6 2e bd | H..q..3Y...0....
5e 45 e3 67 0a da 86 04 30 8f 84 16 65 27 cc 9f | ^E.g....0...e'..
IKEv2-PLAT-5: RECV PKT [IKE_AUTH] [10.0.0.250]:500->[10.250.3.25]:500 InitSPI=0x50797d141ed3e71e RespSPI=0x67b5224e9325b51f MID=00000001
(33):
IKEv2-PROTO-4: (33): Received Packet [From 10.0.0.250:500/To 10.250.3.25:500/VRF i0:f0]
(33): Initiator SPI : 50797D141ED3E71E - Responder SPI : 67B5224E9325B51F Message id: 1
(33): IKEv2 IKE_AUTH Exchange RESPONSEIKEv2-PROTO-5: (33): Next payload: ENCR, version: 2.0 (33): Exchange type: IKE_AUTH, flags: RESPONDER MSG-RESPONSE (33): Message id: 1, length: 176(33):
Payload contents:
IKEv2-PLAT-4: (33): Decrypt success status returned via ipc 1
IKEv2-PROTO-4: decrypt queued(33):
(33): Decrypted packet:(33): Data: 176 bytes
(33): REAL Decrypted packet:(33): Data: 92 bytes
IDr Next payload: AUTH, reserved: 0x0, length: 12
Id type: IPv4 address, Reserved: 0x0 0x0
0a 00 00 fa
AUTH Next payload: NOTIFY, reserved: 0x0, length: 72
Auth method PSK, reserved: 0x0, reserved 0x0
Auth data: 64 bytes
IKEv2-PROTO-7: Parse Notify Payload: TS_UNACCEPTABLE NOTIFY(TS_UNACCEPTABLE) Next payload: NONE, reserved: 0x0, length: 8
Security protocol id: Unknown - 0, spi size: 0, type: TS_UNACCEPTABLE
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: I_WAIT_AUTH Event: EV_RECV_AUTH
IKEv2-PROTO-7: (33): Action: Action_Null
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_CHK4_NOTIFY
IKEv2-PROTO-4: (33): Process auth response notify
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_PROC_MSG
IKEv2-PLAT-4: (33): peer auth method set to: 2
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_CHK_IF_PEER_CERT_NEEDS_TO_BE_FETCHED_FOR_PROF_SEL
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_GET_POLICY_BY_PEERID
IKEv2-PROTO-4: (33): Searching policy based on peer's identity '10.0.0.250' of type 'IPv4 address'
IKEv2-PLAT-4: (33): Site to Site connection detected
IKEv2-PLAT-4: connection initiated with tunnel group 10.0.0.250
IKEv2-PLAT-2: (33): Template number 0
IKEv2-PLAT-4: my_auth_method = 2
IKEv2-PLAT-4: supported_peers_auth_method = 2
IKEv2-PLAT-4: (33): PSH P1 ID = 1
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_VERIFY_POLICY_BY_PEERID
IKEv2-PROTO-4: (33): Verify peer's policy
IKEv2-PROTO-4: (33): Peer's policy verified
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: unknown event
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_CHK_AUTH_TYPE
IKEv2-PROTO-4: (33): Get peer's authentication method
IKEv2-PROTO-4: (33): Peer's authentication method is 'PSK'
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_GET_PRESHR_KEY
IKEv2-PROTO-4: (33): Get peer's preshared key for 10.0.0.250
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_VERIFY_AUTH
IKEv2-PROTO-4: (33): Verify peer's authentication data
IKEv2-PROTO-4: (33): Use preshared key for id 10.0.0.250, key len 8
IKEv2-PROTO-7: (33): Computing AUTH data to authenticate Peer, return code = 1
IKEv2-PROTO-4: (33): Verification of peer's authenctication data PASSED
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_CHK_EAP
IKEv2-PROTO-4: (33): Check for EAP exchange
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_NOTIFY_AUTH_DONE
IKEv2-PLAT-4: (33): Completed authentication for connection
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_CHK_CONFIG_MODE
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_CHK4_IC
IKEv2-PROTO-4: (33): Processing INITIAL_CONTACT
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_CHK_IKE_ONLY
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: AUTH_DONE Event: EV_OK
IKEv2-PROTO-7: (33): Action: Action_Null
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: AUTH_DONE Event: EV_UPDATE_CAC_STATS
IKEv2-PLAT-7: New ikev2 sa request activated
IKEv2-PLAT-7: Decrement count for outgoing negotiating
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: AUTH_DONE Event: EV_INSERT_IKE
IKEv2-PROTO-4: (33): IKEV2 SA created; inserting SA into database. SA lifetime timer (86400 sec) started
IKEv2-PLAT-4:
CONNECTION STATUS: UP... peer: 10.0.0.250:500, phase1_id: 10.0.0.250
IKEv2-PROTO-4: (33): Session with IKE ID PAIR (10.0.0.250, 10.250.3.25) is UP
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: AUTH_DONE Event: EV_REGISTER_SESSION
IKEv2-PLAT-4: (33): connection auth hdl set to 288
IKEv2-PLAT-4: (33): AAA conn attribute retrieval successfully queued for register session request.
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: AUTH_DONE Event: EV_NO_EVENT
IKEv2-PLAT-4: (33): idle timeout set to: 30
IKEv2-PLAT-4: (33): session timeout set to: 0
IKEv2-PLAT-4: (33): group policy set to OPENGEAR-IPSEC
IKEv2-PLAT-4: (33): class attr set
IKEv2-PLAT-4: (33): tunnel protocol set to: 0x4c
IKEv2-PLAT-4: (33): IPv4 filter ID not configured for connection
IKEv2-PLAT-4: (33): group lock set to: none
IKEv2-PLAT-4: (33): IPv6 filter ID not configured for connection
IKEv2-PLAT-4: (33): connection attributes set valid to TRUE
IKEv2-PLAT-4: (33): Successfully retrieved conn attrs
IKEv2-PLAT-4: (33): Session registration after conn attr retrieval PASSED, No error
IKEv2-PLAT-4: (33): connection auth hdl set to -1
IKEv2-PLAT-4:
CONNECTION STATUS: REGISTERED... peer: 10.0.0.250:500, phase1_id: 10.0.0.250
IKEv2-PROTO-4: (33): Initializing DPD, configured for 10 seconds
IKEv2-PLAT-4: mib_index set to: 501
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: AUTH_DONE Event: EV_RECD_REGISTER_SESSION_RESP
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: AUTH_DONE Event: EV_CHECK_DUPE
IKEv2-PROTO-4: (33): Checking for duplicate IKEv2 SA
IKEv2-PROTO-4: (33): No duplicate IKEv2 SA found
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: AUTH_DONE Event: EV_CHK4_ROLE
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: READY Event: EV_CHK_IKE_ONLY
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: READY Event: EV_DEL_SA
IKEv2-PROTO-4: (33): Queuing IKE SA delete request reason: unknown
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: READY Event: EV_FREE_NEG
IKEv2-PROTO-7: (33): Deleting negotiation context for my message ID: 0x1
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: READY Event: EV_DELETE
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: DELETE Event: EV_DELETE
IKEv2-PROTO-7: (33): Action: Action_Null
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: INFO_I_BLD_INFO Event: EV_SND_SA_DEL
IKEv2-PROTO-4: (33): Sending DELETE INFO message for IKEv2 SA [ISPI: 0x50797D141ED3E71E RSPI: 0x67B5224E9325B51F]
IKEv2-PROTO-4: (33): Building packet for encryption.
(33):
Payload contents:
(33): DELETE(33): Next payload: NONE, reserved: 0x0, length: 8
(33): Security protocol id: IKE, spi size: 0, num of spi: 0
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: INFO_I_BLD_INFO Event: EV_ENCRYPT_MSG
IKEv2-PLAT-4: (33): Encrypt success status returned via ipc 1
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: INFO_I_BLD_INFO Event: EV_NO_EVENT
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: INFO_I_BLD_INFO Event: EV_OK_ENCRYPT_RESP
IKEv2-PROTO-7: (33): Action: Action_Null
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000001 CurState: INFO_I_BLD_INFO Event: EV_TRYSEND
IKEv2-PROTO-4: (33): Checking if request will fit in peer window
(33):
IKEv2-PROTO-4: (33): Sending Packet [To 10.0.0.250:500/From 10.250.3.25:500/VRF i0:f0]
(33): Initiator SPI : 50797D141ED3E71E - Responder SPI : 67B5224E9325B51F Message id: 2
(33): IKEv2 INFORMATIONAL Exchange REQUESTIKEv2-PROTO-5: (33): Next payload: ENCR, version: 2.0 (33): Exchange type: INFORMATIONAL, flags: INITIATOR (33): Message id: 2, length: 96(33):
Payload contents:
(33): ENCR(33): Next payload: DELETE, reserved: 0x0, length: 68
(33): Encrypted data: 64 bytes
(33):
IKEv2-PLAT-5: (33): SENT PKT [INFORMATIONAL] [10.250.3.25]:500->[10.0.0.250]:500 InitSPI=0x50797d141ed3e71e RespSPI=0x67b5224e9325b51f MID=00000002
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000002 CurState: INFO_I_BLD_INFO Event: EV_CHK_INFO_TYPE
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000002 CurState: INFO_I_BLD_INFO Event: EV_CHK4_ACTIVE_SA
IKEv2-PROTO-4: (33): Check for existing active SA
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000002 CurState: INFO_I_BLD_INFO Event: EV_STOP_ACCT
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000002 CurState: INFO_I_BLD_INFO Event: EV_TERM_CONN
IKEv2-PROTO-4: (33): Delete all IKE SAs
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000002 CurState: INFO_I_WAIT Event: EV_NO_EVENT
IKEv2-PLAT-4: Received PFKEY delete SA for SPI 0xF702A0FB error FALSE
IKEv2-PLAT-4: PFKEY Delete Ack from IPSec
IKEv2 Recv RAW packet dump
50 79 7d 14 1e d3 e7 1e 67 b5 22 4e 93 25 b5 1f | Py}.....g."N.%..
2e 20 25 20 00 00 00 02 00 00 00 60 00 00 00 44 | . % .......`...D
e1 44 15 b0 62 e2 5d 72 0f 04 2c ae fe 55 8b 80 | .D..b.]r..,..U..
e8 d6 4c b8 eb ce bd 59 1d ae 6f 0b 7a 06 c4 67 | ..L....Y..o.z..g
c0 f2 97 97 78 fa a6 67 a1 cd a7 9a cd eb bb 08 | ....x..g........
48 1e 22 d0 5a 59 48 20 f4 a7 03 7c af a6 0f 58 | H.".ZYH ...|...X
IKEv2-PLAT-5: RECV PKT [INFORMATIONAL] [10.0.0.250]:500->[10.250.3.25]:500 InitSPI=0x50797d141ed3e71e RespSPI=0x67b5224e9325b51f MID=00000002
(33):
IKEv2-PROTO-4: (33): Received Packet [From 10.0.0.250:500/To 10.250.3.25:500/VRF i0:f0]
(33): Initiator SPI : 50797D141ED3E71E - Responder SPI : 67B5224E9325B51F Message id: 2
(33): IKEv2 INFORMATIONAL Exchange RESPONSEIKEv2-PROTO-5: (33): Next payload: ENCR, version: 2.0 (33): Exchange type: INFORMATIONAL, flags: RESPONDER MSG-RESPONSE (33): Message id: 2, length: 96(33):
Payload contents:
IKEv2-PLAT-4: (33): Decrypt success status returned via ipc 1
IKEv2-PROTO-4: decrypt queued(33):
(33): Decrypted packet:(33): Data: 96 bytes
(33): REAL Decrypted packet:(33): Data: 0 bytes
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000002 CurState: INFO_I_WAIT Event: EV_RECV_INFO_ACK
IKEv2-PROTO-4: (33): Processing ACK to informational exchange
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000002 CurState: INFO_I_WAIT Event: EV_CHK_INFO_TYPE
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000002 CurState: DELETE Event: EV_RECV_DEL_ACK
IKEv2-PROTO-7: (33): Action: Action_Null
IKEv2-PROTO-7: (33): SM Trace-> SA: I_SPI=50797D141ED3E71E R_SPI=67B5224E9325B51F (I) MsgID = 00000002 CurState: DELETE Event: EV_FREE_SA
IKEv2-PROTO-4: (33): Deleting SA
IKEv2-PLAT-4:
CONNECTION STATUS: DOWN... peer: 10.0.0.250:500, phase1_id: 10.0.0.250
IKEv2-PLAT-4: (33): IKEv2 session deregistered from session manager. Reason: 8
IKEv2-PLAT-4: (33): session manager killed ikev2 tunnel. Reason: Internal Error
IKEv2-PLAT-4: (33): Deleted associated IKE flow: MGMT, 10.250.3.25:62465 <-> 10.0.0.250:62465
IKEv2-PLAT-4: (33): PSH cleanup
IKEv2-PLAT-7: Active ike sa request deleted
IKEv2-PLAT-7: Decrement count for outgoing activeOpengear Config
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2024 05:58 AM
show crypto ikev2 sa <<- check if ASA already have phaseI, if Yes then clear it
then try ping OM LAN (from any host connect to OM LAN not from interface of OM)
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2024 06:57 AM
NoPhase 1 SA establishes.
I have a session with OM engineer tomo, hoping it is not a compatibility issue between vendors
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2024 05:48 AM
We have made some progress with OM team, but now we have problem with Authentication, and I can not figure out why it is causing an issue because I literally copy paste the Pre-shared-key to both devices.
When I ping from OM LAN. This one just keeps repeating.
IKEv2-PLAT-4: Received PFKEY Invalid SPI for SPI 0xE1E827E5, error FALSE
IKEv2-PROTO-7: Process delete IPSec API
IKEv2-PROTO-7: ipsec delete failed, error Failed to locate an item in the databaseWhen I ping from Local Side
IPSEC(crypto_map_check)-3: Looking for crypto map matching 5-tuple: Prot=1, saddr=172.16.70.2, sport=10496, daddr=172.16.69.2, dport=10496
IPSEC(crypto_map_check)-3: Checking crypto map MGMT_map 1: matched.
IKEv2-PLAT-4: Received PFKEY Acquire SA for SPI 0x0, error FALSE
IPSEC(crypto_map_check)-3: Looking for crypto map matching 5-tuple: Prot=1, saddr=172.16.70.2, sport=10496, daddr=172.16.69.2, dport=10496
IPSEC(crypto_map_check)-3: Checking crypto map MGMT_map 1: matched.
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-4: my_auth_method = 2
IKEv2-PLAT-4: no tunnel group specified: skipping peer auth settings
IKEv2-PLAT-4: supported_peers_auth_method = 43
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-4: ISAKMP P1 ID = 254
IKEv2-PLAT-7: INVALID PSH HANDLE
IPSEC INFO: Setting an IPSec timer of type SA Purge Timer for 30 seconds with a jitter value of 0
IPSEC INFO: IPSec SA PURGE timer started SPI 0x0A4D8FD5
IPSEC: New embryonic SA created @ 0x00007ffa09ab3e00,
SCB : 0x09CCF4B0,
Direction : inbound
SPI : 0x19573B1F
Session ID : 0x0024B000
VPIF num : 0x00000002
Tunnel type: l2l
Protocol : esp
Lifetime : 240 seconds
SA handle : 0x0A4D8FD5
IPSEC INFO: Setting an IPSec timer of type SA Purge Timer for 30 seconds with a jitter value of 0
IPSEC INFO: IPSec SA PURGE timer started SPI 0x0A4E53EB
IPSEC: New embryonic SA created @ 0x00007ffa09a34680,
SCB : 0x09AB4940,
Direction : inbound
SPI : 0xB2AA52F6
Session ID : 0x0024B000
VPIF num : 0x00000002
Tunnel type: l2l
Protocol : esp
Lifetime : 240 seconds
SA handle : 0x0A4E53EB
IPSEC INFO: Setting an IPSec timer of type SA Purge Timer for 30 seconds with a jitter value of 0
IPSEC INFO: IPSec SA PURGE timer started SPI 0x0A4EB6DB
IPSEC: New embryonic SA created @ 0x00007ffa09808850,
SCB : 0x09909750,
Direction : inbound
SPI : 0xA4AC3880
Session ID : 0x0024B000
VPIF num : 0x00000002
Tunnel type: l2l
Protocol : esp
Lifetime : 240 seconds
SA handle : 0x0A4EB6DB
IPSEC INFO: Setting an IPSec timer of type SA Purge Timer for 30 seconds with a jitter value of 0
IPSEC INFO: IPSec SA PURGE timer started SPI 0x0A4F4579
IPSEC: New embryonic SA created @ 0x00007ffa098ee990,
SCB : 0x09B8E0E0,
Direction : inbound
SPI : 0x0E1E020A
Session ID : 0x0024B000
VPIF num : 0x00000002
Tunnel type: l2l
Protocol : esp
Lifetime : 240 seconds
SA handle : 0x0A4F4579
IPSEC INFO: Setting an IPSec timer of type SA Purge Timer for 30 seconds with a jitter value of 0
IPSEC INFO: IPSec SA PURGE timer started SPI 0x0A4FD451
IPSEC: New embryonic SA created @ 0x00007ffa09b93e70,
SCB : 0x09AB7CA0,
Direction : inbound
SPI : 0xE96B194D
Session ID : 0x0024B000
VPIF num : 0x00000002
Tunnel type: l2l
Protocol : esp
Lifetime : 240 seconds
SA handle : 0x0A4FD451
IPSEC INFO: Setting an IPSec timer of type SA Purge Timer for 30 seconds with a jitter value of 0
IPSEC INFO: IPSec SA PURGE timer started SPI 0x0A5044B7
IPSEC: New embryonic SA created @ 0x00007ffa098e9590,
SCB : 0x098E9300,
Direction : inbound
SPI : 0xE3D3201E
Session ID : 0x0024B000
VPIF num : 0x00000002
Tunnel type: l2l
Protocol : esp
Lifetime : 240 seconds
SA handle : 0x0A5044B7
IPSEC INFO: Setting an IPSec timer of type SA Purge Timer for 30 seconds with a jitter value of 0
IPSEC INFO: IPSec SA PURGE timer started SPI 0x0A50E5B7
IPSEC: New embryonic SA created @ 0x00007ffa098e9ce0,
SCB : 0x098EFB50,
Direction : inbound
SPI : 0x86008F76
Session ID : 0x0024B000
VPIF num : 0x00000002
Tunnel type: l2l
Protocol : esp
Lifetime : 240 seconds
SA handle : 0x0A50E5B7
IPSEC INFO: Setting an IPSec timer of type SA Purge Timer for 30 seconds with a jitter value of 0
IPSEC INFO: IPSec SA PURGE timer started SPI 0x0A514125
IPSEC: New embryonic SA created @ 0x00007ffa09ab1e50,
SCB : 0x098F0090,
Direction : inbound
SPI : 0x6B88ECEF
Session ID : 0x0024B000
VPIF num : 0x00000002
Tunnel type: l2l
Protocol : esp
Lifetime : 240 seconds
SA handle : 0x0A514125
IPSEC INFO: Setting an IPSec timer of type SA Purge Timer for 30 seconds with a jitter value of 0
IPSEC INFO: IPSec SA PURGE timer started SPI 0x0A51E48D
IPSEC: New embryonic SA created @ 0x00007ffa09ab25a0,
SCB : 0x09A954A0,
Direction : inbound
SPI : 0x627A241F
Session ID : 0x0024B000
VPIF num : 0x00000002
Tunnel type: l2l
Protocol : esp
Lifetime : 240 seconds
SA handle : 0x0A51E48D
IKEv2-PLAT-4: Received PFKEY SPI callback for SPI 0x19573B1F, error FALSE
IKEv2-PLAT-4:
IKEv2 received a requested SPI from CTM and waiting for 8 more SPIs
IKEv2-PLAT-4: Received PFKEY SPI callback for SPI 0xB2AA52F6, error FALSE
IKEv2-PLAT-4:
IKEv2 received a requested SPI from CTM and waiting for 7 more SPIs
IKEv2-PLAT-4: Received PFKEY SPI callback for SPI 0xA4AC3880, error FALSE
IKEv2-PLAT-4:
IKEv2 received a requested SPI from CTM and waiting for 6 more SPIs
IKEv2-PLAT-4: Received PFKEY SPI callback for SPI 0xE1E020A, error FALSE
IKEv2-PLAT-4:
IKEv2 received a requested SPI from CTM and waiting for 5 more SPIs
IKEv2-PLAT-4: Received PFKEY SPI callback for SPI 0xE96B194D, error FALSE
IKEv2-PLAT-4:
IKEv2 received a requested SPI from CTM and waiting for 4 more SPIs
IKEv2-PLAT-4: Received PFKEY SPI callback for SPI 0xE3D3201E, error FALSE
IKEv2-PLAT-4:
IKEv2 received a requested SPI from CTM and waiting for 3 more SPIs
IKEv2-PLAT-4: Received PFKEY SPI callback for SPI 0x86008F76, error FALSE
IKEv2-PLAT-4:
IKEv2 received a requested SPI from CTM and waiting for 2 more SPIs
IKEv2-PLAT-4: Received PFKEY SPI callback for SPI 0x6B88ECEF, error FALSE
IKEv2-PLAT-4:
IKEv2 received a requested SPI from CTM and waiting for 1 more SPIs
IKEv2-PLAT-4: Received PFKEY SPI callback for SPI 0x627A241F, error FALSE
IKEv2-PLAT-4:
IKEv2 received all requested SPIs from CTM to initiate tunnel.
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-7: INVALID PSH HANDLE
IKEv2-PLAT-4: tp_name set to:
IKEv2-PLAT-4: tg_name set to:
IKEv2-PLAT-4: tunn grp type set to: L2L
IKEv2-PLAT-7: New ikev2 sa request admitted
IKEv2-PLAT-7: Incrementing outgoing negotiating sa count by one
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: IDLE Event: EV_INIT_SA
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_GET_IKE_POLICY
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_SET_POLICY
IKEv2-PROTO-7: (592): Setting configured policies
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_CHK_AUTH4PKI
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_PKI_SESH_OPEN
IKEv2-PROTO-7: (592): Opening a PKI session
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_GEN_DH_KEY
IKEv2-PROTO-4: (592): [IKEv2 -> Crypto Engine] Computing DH public key, DH Group 14
IKEv2-PROTO-4: (592): Request queued for computation of DH key
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_NO_EVENT
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_OK_RECD_DH_PUBKEY_RESP
IKEv2-PROTO-7: (592): Action: Action_Null
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_GET_CONFIG_MODE
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_BLD_MSG
IKEv2-PROTO-4: (592): Generating IKE_SA_INIT message
IKEv2-PROTO-4: (592): IKE Proposal: 1, SPI size: 0 (initial negotiation),
Num. transforms: 4
(592): AES-CBC(592): SHA256(592): SHA256(592): DH_GROUP_2048_MODP/Group 14IKEv2-PROTO-7: Construct Vendor Specific Payload: DELETE-REASONIKEv2-PROTO-7: Construct Vendor Specific Payload: (CUSTOM)IKEv2-PROTO-7: Construct Notify Payload: NAT_DETECTION_SOURCE_IPIKEv2-PROTO-7: Construct Notify Payload: NAT_DETECTION_DESTINATION_IPIKEv2-PROTO-7: Construct Notify Payload: IKEV2_FRAGMENTATION_SUPPORTEDIKEv2-PROTO-7: Construct Vendor Specific Payload: FRAGMENTATION(592):
IKEv2-PROTO-4: (592): Sending Packet [To 10.250.1.50:500/From 10.250.3.25:500/VRF i0:f0]
(592): Initiator SPI : A1905F9A70A65A46 - Responder SPI : 0000000000000000 Message id: 0
(592): IKEv2 IKE_SA_INIT Exchange REQUESTIKEv2-PROTO-5: (592): Next payload: SA, version: 2.0 (592): Exchange type: IKE_SA_INIT, flags: INITIATOR (592): Message id: 0, length: 574(592):
Payload contents:
(592): SA(592): Next payload: KE, reserved: 0x0, length: 48
(592): last proposal: 0x0, reserved: 0x0, length: 44
Proposal: 1, Protocol id: IKE, SPI size: 0, #trans: 4(592): last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
(592): last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: SHA256
(592): last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA256
(592): last transform: 0x0, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_2048_MODP/Group 14
(592): KE(592): Next payload: N, reserved: 0x0, length: 264
(592): DH group: 14, Reserved: 0x0
(592):
(592): 81 f9 e9 35 90 21 01 ad 5c c5 84 05 3c ce 8b dd
(592): 05 f1 b4 f4 3e 34 b4 95 88 c8 32 1b 77 e9 de ca
(592): d8 83 ce e5 5e cf c6 54 05 be 46 84 f6 e3 35 fb
(592): 65 1f b7 ef e8 e4 b9 c7 b2 bd 33 56 d8 0f c6 3b
(592): 33 68 a4 b3 90 49 39 e6 8a c9 ed 14 2a d6 15 e8
(592): 31 f7 5c dc 83 14 dc a0 d8 d2 43 24 73 3f 99 d6
(592): 98 64 61 57 b7 e9 c0 46 55 52 2d 73 3d a5 1f 8d
(592): 64 be a5 87 7a 6c de 0c ac 76 92 c2 91 34 eb 0d
(592): 10 29 a6 22 14 49 fb b5 38 55 20 76 47 14 8a bd
(592): 1c a5 55 3b 36 22 45 10 c0 80 59 d1 46 13 21 b1
(592): 6e 19 26 9d 6a 1f b7 86 f6 4e fb d8 ae 06 77 9d
(592): 5f dd 08 78 b3 15 ff 20 20 d1 1a 74 48 4a e4 7c
(592): 69 4d 1f 5d fc ab aa 9b 4a 73 33 a7 86 c1 ed 34
(592): 23 c9 03 06 e5 b0 6a 35 40 c8 9a a4 bb d5 15 89
(592): da d5 cc b8 ef c4 f7 a1 a0 a6 b9 37 03 c2 b1 dd
(592): f4 63 e1 55 f6 2a 4b ba 85 b1 47 3b 15 91 f9 81
(592): N(592): Next payload: VID, reserved: 0x0, length: 68
(592):
(592): 4f c4 30 1e c9 df 25 c3 de 4c 53 1d ad c5 b3 36
(592): 44 4a 8c 55 df 5e 73 22 1d 73 96 3f e6 76 7c 3a
(592): 95 1f e2 fc 98 44 43 02 31 41 87 4f 82 75 49 6b
(592): 77 7e 1c 14 1f ec 6a aa c2 ee 99 be bc 44 f6 b8
(592): VID(592): Next payload: VID, reserved: 0x0, length: 23
(592):
(592): 43 49 53 43 4f 2d 44 45 4c 45 54 45 2d 52 45 41
(592): 53 4f 4e
(592): VID(592): Next payload: NOTIFY, reserved: 0x0, length: 59
(592):
(592): 43 49 53 43 4f 28 43 4f 50 59 52 49 47 48 54 29
(592): 26 43 6f 70 79 72 69 67 68 74 20 28 63 29 20 32
(592): 30 30 39 20 43 69 73 63 6f 20 53 79 73 74 65 6d
(592): 73 2c 20 49 6e 63 2e
(592): NOTIFY(NAT_DETECTION_SOURCE_IP)(592): Next payload: NOTIFY, reserved: 0x0, length: 28
(592): Security protocol id: IKE, spi size: 0, type: NAT_DETECTION_SOURCE_IP
(592):
(592): dc 7c d9 0a 5c ce 48 52 81 9e b7 24 ae 0c 2d c7
(592): 8d ac f1 6c
(592): NOTIFY(NAT_DETECTION_DESTINATION_IP)(592): Next payload: NOTIFY, reserved: 0x0, length: 28
(592): Security protocol id: IKE, spi size: 0, type: NAT_DETECTION_DESTINATION_IP
(592):
(592): 69 85 26 4e 62 24 f9 2a 87 d8 2e b1 3c 67 0c 86
(592): 29 77 9e 2f
(592): NOTIFY(IKEV2_FRAGMENTATION_SUPPORTED)(592): Next payload: VID, reserved: 0x0, length: 8
(592): Security protocol id: Unknown - 0, spi size: 0, type: IKEV2_FRAGMENTATION_SUPPORTED
(592): VID(592): Next payload: NONE, reserved: 0x0, length: 20
(592):
(592): 40 48 b7 d5 6e bc e8 85 25 e7 de 7f 00 d6 c2 d3
(592):
IKEv2-PLAT-5: (592): SENT PKT [IKE_SA_INIT] [10.250.3.25]:500->[10.250.1.50]:500 InitSPI=0xa1905f9a70a65a46 RespSPI=0x0000000000000000 MID=00000000
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_BLD_INIT Event: EV_INSERT_SA
IKEv2-PROTO-4: (592): Insert SA
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=0000000000000000 (I) MsgID = 00000000 CurState: I_WAIT_INIT Event: EV_NO_EVENT
IKEv2-PLAT-5: RECV PKT [IKE_SA_INIT] [10.250.1.50]:500->[10.250.3.25]:500 InitSPI=0xa1905f9a70a65a46 RespSPI=0xa2dc42e9bf6d67ff MID=00000000
(592):
IKEv2-PROTO-4: (592): Received Packet [From 10.250.1.50:500/To 10.250.3.25:500/VRF i0:f0]
(592): Initiator SPI : A1905F9A70A65A46 - Responder SPI : A2DC42E9BF6D67FF Message id: 0
(592): IKEv2 IKE_SA_INIT Exchange RESPONSEIKEv2-PROTO-5: (592): Next payload: SA, version: 2.0 (592): Exchange type: IKE_SA_INIT, flags: RESPONDER MSG-RESPONSE (592): Message id: 0, length: 456(592):
Payload contents:
(592): SA(592): Next payload: KE, reserved: 0x0, length: 48
(592): last proposal: 0x0, reserved: 0x0, length: 44
Proposal: 1, Protocol id: IKE, SPI size: 0, #trans: 4(592): last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
(592): last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA256
(592): last transform: 0x3, reserved: 0x0: length: 8
type: 2, reserved: 0x0, id: SHA256
(592): last transform: 0x0, reserved: 0x0: length: 8
type: 4, reserved: 0x0, id: DH_GROUP_2048_MODP/Group 14
(592): KE(592): Next payload: N, reserved: 0x0, length: 264
(592): DH group: 14, Reserved: 0x0
(592):
(592): 99 43 4e a3 ca 16 68 61 b0 0a 36 c2 fe dd 2f 7c
(592): b6 43 ce 80 d4 5f 5d 30 7a 1d 6a 1f a0 b0 10 e3
(592): 07 22 c0 b2 f6 80 17 64 b0 bc 92 3d 37 12 3b f7
(592): a3 5c e6 a7 dd 6d 32 89 63 2c 77 29 af 2c b7 da
(592): a4 85 ba 59 8e 8a 9d dd 7b a7 3a a1 f8 47 71 83
(592): 7d 08 a5 07 1e fa e6 86 cf b7 5a d3 24 28 92 02
(592): f8 42 30 70 7d 43 45 f4 44 dd c0 d8 8d a1 06 c3
(592): 96 41 ec 75 49 03 8b dd 67 9d 0a 5a 85 aa b4 cf
(592): 2b 80 a8 a0 87 7e 8b bb ea 08 31 46 c6 f1 d0 83
(592): 45 1e 1c 1f 83 40 67 cc f0 bf f0 2d 53 7f e8 07
(592): 14 8a 3b 9f ab c0 6e fd fc f3 6f 62 b8 fb 31 28
(592): 9a ba 36 45 76 c1 be c9 94 98 ee c8 ff 46 aa d2
(592): 3c e5 4e 2e e6 a1 52 4d d0 3a 5b 6c 08 41 8d 27
(592): 0b 64 88 03 b7 14 46 da 49 0c 46 0c c9 44 22 fa
(592): f7 a8 63 0a 6f 48 8e 22 f3 63 03 ba 33 56 84 ea
(592): a5 9c b1 99 4d e5 c3 1a 65 d7 9b cb eb 61 b9 51
(592): N(592): Next payload: NOTIFY, reserved: 0x0, length: 36
(592):
(592): 35 53 66 66 21 92 75 44 11 70 29 d9 f3 da f6 0c
(592): d7 bd 60 0b b3 a6 32 2c a1 94 83 df fe 8d 87 d7
IKEv2-PROTO-7: Parse Notify Payload: NAT_DETECTION_SOURCE_IP(592): NOTIFY(NAT_DETECTION_SOURCE_IP)(592): Next payload: NOTIFY, reserved: 0x0, length: 28
(592): Security protocol id: Unknown - 0, spi size: 0, type: NAT_DETECTION_SOURCE_IP
(592):
(592): 50 6c 4e d6 99 a6 5e da b1 6d ad 1e 71 11 c8 2f
(592): 30 c4 80 39
IKEv2-PROTO-7: Parse Notify Payload: NAT_DETECTION_DESTINATION_IP(592): NOTIFY(NAT_DETECTION_DESTINATION_IP)(592): Next payload: NOTIFY, reserved: 0x0, length: 28
(592): Security protocol id: Unknown - 0, spi size: 0, type: NAT_DETECTION_DESTINATION_IP
(592):
(592): c0 bd a6 06 96 e1 6b 11 a4 cd 84 12 ad fd 74 b8
(592): 2c 3f 2c 45
IKEv2-PROTO-7: Parse Notify Payload: IKEV2_FRAGMENTATION_SUPPORTED(592): NOTIFY(IKEV2_FRAGMENTATION_SUPPORTED)(592): Next payload: NOTIFY, reserved: 0x0, length: 8
(592): Security protocol id: Unknown - 0, spi size: 0, type: IKEV2_FRAGMENTATION_SUPPORTED
IKEv2-PROTO-7: Parse Notify Payload: Unknown - 16418(592): NOTIFY(Unknown - 16418)(592): Next payload: NOTIFY, reserved: 0x0, length: 8
(592): Security protocol id: Unknown - 0, spi size: 0, type: Unknown - 0
IKEv2-PROTO-7: Parse Notify Payload: Unknown - 16404(592): NOTIFY(Unknown - 16404)(592): Next payload: NONE, reserved: 0x0, length: 8
(592): Security protocol id: Unknown - 0, spi size: 0, type: Unknown - 0
(592):
(592): Decrypted packet:(592): Data: 456 bytes
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000000 CurState: I_WAIT_INIT Event: EV_RECV_INIT
IKEv2-PROTO-7: (592): Processing IKE_SA_INIT message
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000000 CurState: I_PROC_INIT Event: EV_CHK4_NOTIFY
IKEv2-PROTO-4: (592): Processing IKE_SA_INIT message
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000000 CurState: I_PROC_INIT Event: EV_VERIFY_MSG
IKEv2-PROTO-4: (592): Verify SA init message
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000000 CurState: I_PROC_INIT Event: EV_PROC_MSG
IKEv2-PROTO-4: (592): Processing IKE_SA_INIT message
IKEv2-PLAT-4: (592): my auth method set to: 2
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000000 CurState: I_PROC_INIT Event: EV_DETECT_NAT
IKEv2-PROTO-7: (592): Process NAT discovery notify
IKEv2-PROTO-7: (592): Processing nat detect src notify
IKEv2-PROTO-7: (592): Remote address matched
IKEv2-PROTO-7: (592): Processing nat detect dst notify
IKEv2-PROTO-7: (592): Local address matched
IKEv2-PROTO-7: (592): No NAT found
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000000 CurState: I_PROC_INIT Event: EV_CHK_NAT_T
IKEv2-PROTO-4: (592): Checking NAT discovery
IKEv2-PROTO-4: (592): NAT not found
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000000 CurState: I_PROC_INIT Event: EV_CHK_CONFIG_MODE
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000000 CurState: INIT_DONE Event: EV_GEN_DH_SECRET
IKEv2-PROTO-4: (592): [IKEv2 -> Crypto Engine] Computing DH secret key, DH Group 14
IKEv2-PROTO-4: (592): Request queued for computation of DH secret
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000000 CurState: INIT_DONE Event: EV_NO_EVENT
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000000 CurState: INIT_DONE Event: EV_OK_RECD_DH_SECRET_RESP
IKEv2-PROTO-7: (592): Action: Action_Null
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000000 CurState: INIT_DONE Event: EV_GEN_SKEYID
IKEv2-PROTO-7: (592): Generate skeyid
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000000 CurState: INIT_DONE Event: EV_DONE
IKEv2-PROTO-4: (592): IETF Fragmentation is enabled
IKEv2-PROTO-4: (592): Completed SA init exchange
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000000 CurState: INIT_DONE Event: EV_CHK4_ROLE
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_GET_CONFIG_MODE
IKEv2-PLAT-4: Build config mode reply: no request stored
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_CHK_FOR_PPK
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_CHK_PPK_MAND
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_CHK_EAP
IKEv2-PROTO-4: (592): Check for EAP exchange
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_GEN_AUTH
IKEv2-PROTO-4: (592): Generate my authentication data
IKEv2-PROTO-4: (592): Use preshared key for id 10.250.3.25, key len 16
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_GEN_FALLBACK_AUTH
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_CHK_AUTH_TYPE
IKEv2-PROTO-4: (592): Get my authentication method
IKEv2-PROTO-4: (592): My authentication method is 'PSK'
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_OK_AUTH_GEN
IKEv2-PROTO-4: (592): Check for EAP exchange
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000000 CurState: I_BLD_AUTH Event: EV_SEND_AUTH
IKEv2-PROTO-4: (592): Generating IKE_AUTH message
IKEv2-PROTO-7: Construct Vendor Specific Payload: CISCO-GRANITEIKEv2-PROTO-4: (592): Constructing IDi payload: '10.250.3.25' of type 'IPv4 address'
Adding trusted issuer hash to send. Hash:
87 e3 bf 32 24 27 c1 40 5d 27 36 c3 81 e0 1d 1a
71 d4 a0 39
Adding trusted issuer hash to send. Hash:
73 97 82 ea b4 04 16 6e 25 d4 82 3c 37 db f8 a8
12 fb cf 26
IKEv2-PROTO-4: (592): ESP Proposal: 1, SPI size: 4 (IPSec negotiation),
Num. transforms: 3
(592): AES-CBC(592): SHA96(592): Don't use ESNIKEv2-PROTO-4: (592): ESP Proposal: 2, SPI size: 4 (IPSec negotiation),
Num. transforms: 3
(592): AES-CBC(592): SHA256(592): Don't use ESNIKEv2-PROTO-4: (592): ESP Proposal: 3, SPI size: 4 (IPSec negotiation),
Num. transforms: 3
(592): AES-CBC(592): SHA384(592): Don't use ESNIKEv2-PROTO-4: (592): ESP Proposal: 4, SPI size: 4 (IPSec negotiation),
Num. transforms: 3
(592): AES-CBC(592): SHA512(592): Don't use ESNIKEv2-PROTO-4: (592): ESP Proposal: 5, SPI size: 4 (IPSec negotiation),
Num. transforms: 3
(592): AES-CBC(592): SHA96(592): Don't use ESNIKEv2-PROTO-4: (592): ESP Proposal: 6, SPI size: 4 (IPSec negotiation),
Num. transforms: 3
(592): AES-CBC(592): SHA96(592): Don't use ESNIKEv2-PROTO-4: (592): ESP Proposal: 7, SPI size: 4 (IPSec negotiation),
Num. transforms: 3
(592): AES-CBC(592): SHA96(592): Don't use ESNIKEv2-PROTO-4: (592): ESP Proposal: 8, SPI size: 4 (IPSec negotiation),
Num. transforms: 3
(592): AES-CBC(592): SHA96(592): Don't use ESNIKEv2-PROTO-4: (592): ESP Proposal: 9, SPI size: 4 (IPSec negotiation),
Num. transforms: 3
(592): AES-CBC(592): SHA96(592): Don't use ESNIKEv2-PROTO-7: Construct Notify Payload: INITIAL_CONTACTIKEv2-PROTO-7: Construct Notify Payload: ESP_TFC_NO_SUPPORTIKEv2-PROTO-7: Construct Notify Payload: NON_FIRST_FRAGSIKEv2-PROTO-4: (592): Building packet for encryption.
(592):
Payload contents:
(592): VID(592): Next payload: IDi, reserved: 0x0, length: 20
(592):
(592): a3 90 5e 9a 63 91 a9 01 f2 68 1b c0 61 1d ed ce
(592): IDi(592): Next payload: CERTREQ, reserved: 0x0, length: 12
(592): Id type: IPv4 address, Reserved: 0x0 0x0
(592):
(592): 0a fa 03 19
(592): CERTREQ(592): Next payload: AUTH, reserved: 0x0, length: 45
(592): Cert encoding X.509 Certificate - signature
(592): CertReq data: 40 bytes
(592): AUTH(592): Next payload: SA, reserved: 0x0, length: 40
(592): Auth method PSK, reserved: 0x0, reserved 0x0
(592): Auth data: 32 bytes
(592): SA(592): Next payload: TSi, reserved: 0x0, length: 364
(592): last proposal: 0x2, reserved: 0x0, length: 40
Proposal: 1, Protocol id: ESP, SPI size: 4, #trans: 3(592): last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
(592): last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA96
(592): last transform: 0x0, reserved: 0x0: length: 8
type: 5, reserved: 0x0, id: Don't use ESN
(592): last proposal: 0x2, reserved: 0x0, length: 40
Proposal: 2, Protocol id: ESP, SPI size: 4, #trans: 3(592): last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
(592): last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA256
(592): last transform: 0x0, reserved: 0x0: length: 8
type: 5, reserved: 0x0, id: Don't use ESN
(592): last proposal: 0x2, reserved: 0x0, length: 40
Proposal: 3, Protocol id: ESP, SPI size: 4, #trans: 3(592): last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
(592): last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA384
(592): last transform: 0x0, reserved: 0x0: length: 8
type: 5, reserved: 0x0, id: Don't use ESN
(592): last proposal: 0x2, reserved: 0x0, length: 40
Proposal: 4, Protocol id: ESP, SPI size: 4, #trans: 3(592): last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
(592): last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA512
(592): last transform: 0x0, reserved: 0x0: length: 8
type: 5, reserved: 0x0, id: Don't use ESN
(592): last proposal: 0x2, reserved: 0x0, length: 40
Proposal: 5, Protocol id: ESP, SPI size: 4, #trans: 3(592): last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
(592): last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA96
(592): last transform: 0x0, reserved: 0x0: length: 8
type: 5, reserved: 0x0, id: Don't use ESN
(592): last proposal: 0x2, reserved: 0x0, length: 40
Proposal: 6, Protocol id: ESP, SPI size: 4, #trans: 3(592): last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
(592): last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA96
(592): last transform: 0x0, reserved: 0x0: length: 8
type: 5, reserved: 0x0, id: Don't use ESN
(592): last proposal: 0x2, reserved: 0x0, length: 40
Proposal: 7, Protocol id: ESP, SPI size: 4, #trans: 3(592): last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
(592): last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA96
(592): last transform: 0x0, reserved: 0x0: length: 8
type: 5, reserved: 0x0, id: Don't use ESN
(592): last proposal: 0x2, reserved: 0x0, length: 40
Proposal: 8, Protocol id: ESP, SPI size: 4, #trans: 3(592): last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
(592): last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA96
(592): last transform: 0x0, reserved: 0x0: length: 8
type: 5, reserved: 0x0, id: Don't use ESN
(592): last proposal: 0x0, reserved: 0x0, length: 40
Proposal: 9, Protocol id: ESP, SPI size: 4, #trans: 3(592): last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
(592): last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA96
(592): last transform: 0x0, reserved: 0x0: length: 8
type: 5, reserved: 0x0, id: Don't use ESN
(592): TSi(592): Next payload: TSr, reserved: 0x0, length: 40
(592): Num of TSs: 2, reserved 0x0, reserved 0x0
(592): TS type: TS_IPV4_ADDR_RANGE, proto id: 0, length: 16
(592): start port: 0, end port: 65535
(592): start addr: 172.16.70.2, end addr: 172.16.70.2
(592): TS type: TS_IPV4_ADDR_RANGE, proto id: 0, length: 16
(592): start port: 0, end port: 65535
(592): start addr: 172.16.70.0, end addr: 172.16.70.255
(592): TSr(592): Next payload: NOTIFY, reserved: 0x0, length: 40
(592): Num of TSs: 2, reserved 0x0, reserved 0x0
(592): TS type: TS_IPV4_ADDR_RANGE, proto id: 0, length: 16
(592): start port: 0, end port: 65535
(592): start addr: 172.16.69.2, end addr: 172.16.69.2
(592): TS type: TS_IPV4_ADDR_RANGE, proto id: 0, length: 16
(592): start port: 0, end port: 65535
(592): start addr: 172.16.69.0, end addr: 172.16.69.255
(592): NOTIFY(INITIAL_CONTACT)(592): Next payload: NOTIFY, reserved: 0x0, length: 8
(592): Security protocol id: IKE, spi size: 0, type: INITIAL_CONTACT
(592): NOTIFY(ESP_TFC_NO_SUPPORT)(592): Next payload: NOTIFY, reserved: 0x0, length: 8
(592): Security protocol id: IKE, spi size: 0, type: ESP_TFC_NO_SUPPORT
(592): NOTIFY(NON_FIRST_FRAGS)(592): Next payload: NONE, reserved: 0x0, length: 8
(592): Security protocol id: IKE, spi size: 0, type: NON_FIRST_FRAGS
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000001 CurState: I_BLD_AUTH Event: EV_ENCRYPT_MSG
IKEv2-PLAT-4: (592): Encrypt success status returned via ipc 1
IKEv2-PLAT-4: (592): Encrypt success status returned via ipc 1
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000001 CurState: I_BLD_AUTH Event: EV_NO_EVENT
(592):
IKEv2-PROTO-4: (592): Sending Packet [To 10.250.1.50:500/From 10.250.3.25:500/VRF i0:f0]
(592): Initiator SPI : A1905F9A70A65A46 - Responder SPI : A2DC42E9BF6D67FF Message id: 1
(592): IKEv2 IKE_AUTH Exchange REQUESTIKEv2-PROTO-5: (592): Next payload: SKF, version: 2.0 (592): Exchange type: IKE_AUTH, flags: INITIATOR (592): Message id: 1, length: 532(592):
Payload contents:
(592): SKF(592): Next payload: VID, reserved: 0x0, length: 504
(592): SKF Fragment number: 1 OF Total Fragments: 2(592):
(592): 0c e6 b1 f2 94 cb a0 82 fd 17 9c 78 41 a8 a5 e9
(592): f9 78 d2 06 9c 7f 39 4f a9 00 27 41 73 78 1d 41
(592): 3f 8e 92 42 83 10 db 58 37 eb 57 f7 da b9 70 e3
(592): e5 e3 f2 93 bd 6a d7 52 0a e3 9b b9 9d 28 ab 9f
(592): 8b ca ba f1 78 5b 64 2e 3c 12 0b c0 25 a0 f5 a6
(592): 7d 74 5f 78 15 39 63 84 de 82 ee 4d b6 32 6f 1c
(592): b1 8b 45 e5 48 18 c4 d8 94 00 23 e5 bd 52 94 a2
(592): ba f0 4f 5e bf 7c 1a fc dd 26 a7 5a b8 83 6f 3f
(592): 07 a5 fb 7d c2 45 14 af 38 d3 32 8a 64 85 f1 0c
(592): 90 dd 80 63 d2 3c 74 20 fb c2 3a c6 0e 4d 15 9d
(592): bf 38 a6 5c 8a b9 ad 43 f9 bc cb 09 a6 69 67 7c
(592): 7f 7e 40 fe b8 53 cd 02 f8 98 84 7b bf c2 5f c2
(592): 1e 00 4a 3c d3 26 d6 bb 27 f6 c0 28 c9 c7 19 2f
(592): 89 cd 31 28 45 c4 75 68 6b 84 24 d6 dc 28 80 bb
(592): 2b f1 94 27 bd 2c 6f cf 1e e7 64 94 d0 1e ad 99
(592): d6 ad c0 13 73 ba 72 45 aa af 16 ae 53 5e 71 9a
(592): 41 07 d9 25 0a fe 5b d1 94 98 cd cd fc 2b 9c 24
(592): b5 be 1c bd 4c e0 e9 31 d9 f2 78 ed 2b fb c5 02
(592): d8 1a 19 4f 7a 45 11 3a 6d 91 f0 71 f1 42 a9 19
(592): d1 52 3d 78 f3 ff b8 d7 25 b2 78 1b a9 62 1f 6a
(592): f3 06 21 51 0a ae 13 72 c6 3a 1e 4e 9a 63 78 b7
(592): 86 a9 0e f1 12 b3 73 6e bb 5f 62 81 9e c0 03 8e
(592): 6d 98 7d 8d 93 4e ec 60 9a 84 72 b5 ba bc 92 6a
(592): 97 b3 17 a9 23 7f a7 47 6e a1 c1 a4 12 44 d5 e1
(592): 22 ad a3 28 bc a9 52 da 25 dd c6 9d af 94 b4 f3
(592): a2 87 c7 50 bc fc 20 9f 59 fc 24 2f 74 12 17 12
(592): 05 12 1c 20 a4 17 87 71 eb c1 59 7b 87 54 79 7c
(592): 74 60 d7 6f 02 b7 69 e1 9e 18 4a f8 1b f2 3e 43
(592): 2e f6 cd c2 79 17 97 5b 83 ff d8 4e 76 91 37 1c
(592): 05 45 6f 64 af 24 b5 4a a5 57 0d 47 26 aa 7e 82
(592): 2d 83 89 74 bb 00 3a 6a 00 73 ee 3b 62 a9 42 ce
(592):
IKEv2-PROTO-7: Added encrypted fragment 1 of (2) to the list
(592):
IKEv2-PROTO-4: (592): Sending Packet [To 10.250.1.50:500/From 10.250.3.25:500/VRF i0:f0]
(592): Initiator SPI : A1905F9A70A65A46 - Responder SPI : A2DC42E9BF6D67FF Message id: 1
(592): IKEv2 IKE_AUTH Exchange REQUESTIKEv2-PROTO-5: (592): Next payload: SKF, version: 2.0 (592): Exchange type: IKE_AUTH, flags: INITIATOR (592): Message id: 1, length: 212(592):
Payload contents:
(592): SKF(592): Next payload: NONE, reserved: 0x0, length: 184
(592): SKF Fragment number: 2 OF Total Fragments: 2(592):
(592): 05 45 6f 64 af 24 b5 4a a5 57 0d 47 26 aa 7e 82
(592): eb 2e b2 b7 b7 51 63 a6 6f 30 e7 f9 84 48 ed 37
(592): 7f 2d 48 b1 39 8b cf a8 ca 93 7c 3e 6b 5b 8d b7
(592): 61 66 a2 3f 53 47 2b ce 00 90 b8 dd 34 69 6e 8b
(592): 59 38 5e 98 ed 68 42 f2 09 0b 84 9b 20 16 77 64
(592): e5 f9 b1 46 b5 40 bb 0e c2 10 cc 7c 8d 8e 38 c5
(592): 39 08 98 be 9e 25 67 95 1e 8c 07 22 ae 33 8d 3d
(592): b4 77 8b 6e 70 69 b6 42 5d 9f 76 6c 20 7a 06 67
(592): 1f 3f c7 8e 85 6c 76 3b ac a4 b3 25 ff a6 c0 eb
(592): e1 86 9d dc 54 c0 72 dc 2f 9d 59 64 4c 8f 94 db
(592): 05 d0 7a 77 75 7d 2b 22 5c 17 b5 2e 76 ff 54 37
(592):
IKEv2-PROTO-7: Added encrypted fragment 2 of (2) to the list
IKEv2-PROTO-7: (592): All fragments encrypted ready to be sent
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000001 CurState: I_BLD_AUTH Event: EV_OK_ENCRYPT_RESP
IKEv2-PROTO-7: (592): Action: Action_Null
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000001 CurState: I_BLD_AUTH Event: EV_TRYSEND
IKEv2-PLAT-5: (592): SENT PKT [IKE_AUTH] [10.250.3.25]:500->[10.250.1.50]:500 InitSPI=0xa1905f9a70a65a46 RespSPI=0xa2dc42e9bf6d67ff MID=00000001
IKEv2-PLAT-5: (592): SENT PKT [IKE_AUTH] [10.250.3.25]:500->[10.250.1.50]:500 InitSPI=0xa1905f9a70a65a46 RespSPI=0xa2dc42e9bf6d67ff MID=00000001
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000001 CurState: I_BLD_AUTH Event: EV_CHK_EAP_POST_ASYNC
IKEv2-PROTO-4: (592): Check for EAP exchange
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000001 CurState: I_WAIT_AUTH Event: EV_NO_EVENT
IKEv2-PLAT-5: RECV PKT [IKE_AUTH] [10.250.1.50]:500->[10.250.3.25]:500 InitSPI=0xa1905f9a70a65a46 RespSPI=0xa2dc42e9bf6d67ff MID=00000001
IKEv2-PROTO-7: Freeing all fragments in OUTBOUND fragment list
(592):
IKEv2-PROTO-4: (592): Received Packet [From 10.250.1.50:500/To 10.250.3.25:500/VRF i0:f0]
(592): Initiator SPI : A1905F9A70A65A46 - Responder SPI : A2DC42E9BF6D67FF Message id: 1
(592): IKEv2 IKE_AUTH Exchange RESPONSEIKEv2-PROTO-5: (592): Next payload: ENCR, version: 2.0 (592): Exchange type: IKE_AUTH, flags: RESPONDER MSG-RESPONSE (592): Message id: 1, length: 224(592):
Payload contents:
IKEv2-PLAT-4: (592): Decrypt success status returned via ipc 1
IKEv2-PROTO-4: decrypt queued(592):
(592): Decrypted packet:(592): Data: 224 bytes
(592): REAL Decrypted packet:(592): Data: 144 bytes
IDr Next payload: AUTH, reserved: 0x0, length: 12
Id type: IPv4 address, Reserved: 0x0 0x0
0a fa 01 32
AUTH Next payload: SA, reserved: 0x0, length: 40
Auth method PSK, reserved: 0x0, reserved 0x0
Auth data: 32 bytes
SA Next payload: TSi, reserved: 0x0, length: 44
last proposal: 0x0, reserved: 0x0, length: 40
Proposal: 1, Protocol id: ESP, SPI size: 4, #trans: 3 last transform: 0x3, reserved: 0x0: length: 12
type: 1, reserved: 0x0, id: AES-CBC
last transform: 0x3, reserved: 0x0: length: 8
type: 3, reserved: 0x0, id: SHA96
last transform: 0x0, reserved: 0x0: length: 8
type: 5, reserved: 0x0, id: Don't use ESN
TSi Next payload: TSr, reserved: 0x0, length: 24
Num of TSs: 1, reserved 0x0, reserved 0x0
TS type: TS_IPV4_ADDR_RANGE, proto id: 0, length: 16
start port: 0, end port: 65535
start addr: 172.16.70.0, end addr: 172.16.70.255
TSr Next payload: NONE, reserved: 0x0, length: 24
Num of TSs: 1, reserved 0x0, reserved 0x0
TS type: TS_IPV4_ADDR_RANGE, proto id: 0, length: 16
start port: 0, end port: 65535
start addr: 172.16.69.0, end addr: 172.16.69.255
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000001 CurState: I_WAIT_AUTH Event: EV_RECV_AUTH
IKEv2-PROTO-7: (592): Action: Action_Null
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_CHK4_NOTIFY
IKEv2-PROTO-4: (592): Process auth response notify
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_PROC_MSG
IKEv2-PLAT-4: (592): peer auth method set to: 2
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_CHK_IF_PEER_CERT_NEEDS_TO_BE_FETCHED_FOR_PROF_SEL
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_GET_POLICY_BY_PEERID
IKEv2-PROTO-4: (592): Searching policy based on peer's identity '10.250.1.50' of type 'IPv4 address'
IKEv2-PLAT-4: (592): Site to Site connection detected
IKEv2-PLAT-4: attempting to find tunnel group for ID: 10.250.1.50
IKEv2-PLAT-4: mapped to tunnel group 10.250.1.50 using phase 1 ID
IKEv2-PLAT-4: tg_name set to: 10.250.1.50
IKEv2-PLAT-4: tunn grp type set to: L2L
IKEv2-PLAT-2: (592): Template number 0
IKEv2-PLAT-4: my_auth_method = 2
IKEv2-PLAT-4: supported_peers_auth_method = 2
IKEv2-PLAT-4: (592): PSH P1 ID = 1
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_VERIFY_POLICY_BY_PEERID
IKEv2-PROTO-4: (592): Verify peer's policy
IKEv2-PROTO-4: (592): Peer's policy verified
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: unknown event
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_CHK_AUTH_TYPE
IKEv2-PROTO-4: (592): Get peer's authentication method
IKEv2-PROTO-4: (592): Peer's authentication method is 'PSK'
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_GET_PRESHR_KEY
IKEv2-PROTO-4: (592): Get peer's preshared key for 10.250.1.50
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_VERIFY_AUTH
IKEv2-PROTO-4: (592): Verify peer's authentication data
IKEv2-PROTO-4: (592): Use preshared key for id 10.250.1.50, key len 16
IKEv2-PROTO-7: (592): Computing AUTH data to authenticate Peer, return code = 1
IKEv2-PROTO-7: (592): Computed authentication value for peer differs from what peer sent
IKEv2-PROTO-2: (592): Failed to authenticate the IKE SA
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_AUTH_FAIL
IKEv2-PROTO-4: (592): Verification of peer's authentication data FAILED
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000001 CurState: AUTH_DONE Event: EV_FAIL
IKEv2-PROTO-4: (592): Auth exchange failed
IKEv2-PROTO-2: (592): Auth exchange failed
IKEv2-PROTO-2: (592): Auth exchange failed
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000001 CurState: EXIT Event: EV_ABORT
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000001 CurState: EXIT Event: EV_CHK_PENDING_ABORT
IKEv2-PLAT-7: Negotiating SA request deleted
IKEv2-PLAT-7: Decrement count for outgoing negotiating
IKEv2-PROTO-7: (592): SM Trace-> SA: I_SPI=A1905F9A70A65A46 R_SPI=A2DC42E9BF6D67FF (I) MsgID = 00000001 CurState: EXIT Event: EV_UPDATE_CAC_STATS
IKEv2-PROTO-4: (592): Abort exchange
IKEv2-PROTO-4: (592): Deleting SA
IKEv2-PLAT-4: (592): PSH cleanup
IPSEC DEBUG: Received a DELETE PFKey message from IKE for an inbound SA (SPI 0x19573B1F)
IPSEC DEBUG: Inbound SA (SPI 0x19573B1F) destroy started, state embryonic
IPSEC DEBUG: Inbound SA (SPI 0x19573B1F) free started, state embryonic
IPSEC INFO: Destroying an IPSec timer of type SA Purge Timer
IPSEC INFO: Setting an IPSec timer of type SA Purge Timer for 30 seconds with a jitter value of 0
IPSEC INFO: IPSec SA PURGE timer started SPI 0x0A4D8FD5
IPSEC INFO: Destroying an IPSec timer of type SA Purge Timer
IPSEC DEBUG: Inbound SA (SPI 0x19573B1F) free completed
IPSEC DEBUG: Inbound SA (SPI 0x19573B1F) destroy completed
IPSEC DEBUG: Received a DELETE PFKey message from IKE for an inbound SA (SPI 0xB2AA52F6)
IPSEC DEBUG: Inbound SA (SPI 0xB2AA52F6) destroy started, state embryonic
IPSEC DEBUG: Inbound SA (SPI 0xB2AA52F6) free started, state embryonic
IPSEC INFO: Destroying an IPSec timer of type SA Purge Timer
IPSEC INFO: Setting an IPSec timer of type SA Purge Timer for 30 seconds with a jitter value of 0
IPSEC INFO: IPSec SA PURGE timer started SPI 0x0A4E53EB
IPSEC INFO: Destroying an IPSec timer of type SA Purge Timer
IPSEC DEBUG: Inbound SA (SPI 0xB2AA52F6) free completed
IPSEC DEBUG: Inbound SA (SPI 0xB2AA52F6) destroy completed
IPSEC DEBUG: Received a DELETE PFKey message from IKE for an inbound SA (SPI 0xA4AC3880)
IPSEC DEBUG: Inbound SA (SPI 0xA4AC3880) destroy started, state embryonic
IPSEC DEBUG: Inbound SA (SPI 0xA4AC3880) free started, state embryonic
IPSEC INFO: Destroying an IPSec timer of type SA Purge Timer
IPSEC INFO: Setting an IPSec timer of type SA Purge Timer for 30 seconds with a jitter value of 0
IPSEC INFO: IPSec SA PURGE timer started SPI 0x0A4EB6DB
IPSEC INFO: Destroying an IPSec timer of type SA Purge Timer
IPSEC DEBUG: Inbound SA (SPI 0xA4AC3880) free completed
IPSEC DEBUG: Inbound SA (SPI 0xA4AC3880) destroy completed
IPSEC DEBUG: Received a DELETE PFKey message from IKE for an inbound SA (SPI 0x0E1E020A)
IPSEC DEBUG: Inbound SA (SPI 0x0E1E020A) destroy started, state embryonic
IPSEC DEBUG: Inbound SA (SPI 0x0E1E020A) free started, state embryonic
IPSEC INFO: Destroying an IPSec timer of type SA Purge Timer
IPSEC INFO: Setting an IPSec timer of type SA Purge Timer for 30 seconds with a jitter value of 0
IPSEC INFO: IPSec SA PURGE timer started SPI 0x0A4F4579
IPSEC INFO: Destroying an IPSec timer of type SA Purge Timer
IPSEC DEBUG: Inbound SA (SPI 0x0E1E020A) free completed
IPSEC DEBUG: Inbound SA (SPI 0x0E1E020A) destroy completed
IPSEC DEBUG: Received a DELETE PFKey message from IKE for an inbound SA (SPI 0xE96B194D)
IPSEC DEBUG: Inbound SA (SPI 0xE96B194D) destroy started, state embryonic
IPSEC DEBUG: Inbound SA (SPI 0xE96B194D) free started, state embryonic
IPSEC INFO: Destroying an IPSec timer of type SA Purge Timer
IPSEC INFO: Setting an IPSec timer of type SA Purge Timer for 30 seconds with a jitter value of 0
IPSEC INFO: IPSec SA PURGE timer started SPI 0x0A4FD451
IPSEC INFO: Destroying an IPSec timer of type SA Purge Timer
IPSEC DEBUG: Inbound SA (SPI 0xE96B194D) free completed
IPSEC DEBUG: Inbound SA (SPI 0xE96B194D) destroy completed
IPSEC DEBUG: Received a DELETE PFKey message from IKE for an inbound SA (SPI 0xE3D3201E)
IPSEC DEBUG: Inbound SA (SPI 0xE3D3201E) destroy started, state embryonic
IPSEC DEBUG: Inbound SA (SPI 0xE3D3201E) free started, state embryonic
IPSEC INFO: Destroying an IPSec timer of type SA Purge Timer
IPSEC INFO: Setting an IPSec timer of type SA Purge Timer for 30 seconds with a jitter value of 0
IPSEC INFO: IPSec SA PURGE timer started SPI 0x0A5044B7
IPSEC INFO: Destroying an IPSec timer of type SA Purge Timer
IPSEC DEBUG: Inbound SA (SPI 0xE3D3201E) free completed
IPSEC DEBUG: Inbound SA (SPI 0xE3D3201E) destroy completed
IPSEC DEBUG: Received a DELETE PFKey message from IKE for an inbound SA (SPI 0x86008F76)
IPSEC DEBUG: Inbound SA (SPI 0x86008F76) destroy started, state embryonic
IPSEC DEBUG: Inbound SA (SPI 0x86008F76) free started, state embryonic
IPSEC INFO: Destroying an IPSec timer of type SA Purge Timer
IPSEC INFO: Setting an IPSec timer of type SA Purge Timer for 30 seconds with a jitter value of 0
IPSEC INFO: IPSec SA PURGE timer started SPI 0x0A50E5B7
IPSEC INFO: Destroying an IPSec timer of type SA Purge Timer
IPSEC DEBUG: Inbound SA (SPI 0x86008F76) free completed
IPSEC DEBUG: Inbound SA (SPI 0x86008F76) destroy completed
IPSEC DEBUG: Received a DELETE PFKey message from IKE for an inbound SA (SPI 0x6B88ECEF)
IPSEC DEBUG: Inbound SA (SPI 0x6B88ECEF) destroy started, state embryonic
IPSEC DEBUG: Inbound SA (SPI 0x6B88ECEF) free started, state embryonic
IPSEC INFO: Destroying an IPSec timer of type SA Purge Timer
IPSEC INFO: Setting an IPSec timer of type SA Purge Timer for 30 seconds with a jitter value of 0
IPSEC INFO: IPSec SA PURGE timer started SPI 0x0A514125
IPSEC INFO: Destroying an IPSec timer of type SA Purge Timer
IPSEC DEBUG: Inbound SA (SPI 0x6B88ECEF) free completed
IPSEC DEBUG: Inbound SA (SPI 0x6B88ECEF) destroy completed
IPSEC DEBUG: Received a DELETE PFKey message from IKE for an inbound SA (SPI 0x627A241F)
IPSEC DEBUG: Inbound SA (SPI 0x627A241F) destroy started, state embryonic
IPSEC DEBUG: Inbound SA (SPI 0x627A241F) free started, state embryonic
IPSEC INFO: Destroying an IPSec timer of type SA Purge Timer
IPSEC INFO: Setting an IPSec timer of type SA Purge Timer for 30 seconds with a jitter value of 0
IPSEC INFO: IPSec SA PURGE timer started SPI 0x0A51E48D
IPSEC INFO: Destroying an IPSec timer of type SA Purge Timer
IPSEC DEBUG: Inbound SA (SPI 0x627A241F) free completed
IPSEC DEBUG: Inbound SA (SPI 0x627A241F) destroy completed
IKEv2-PLAT-4: Received PFKEY delete SA for SPI 0x19573B1F error FALSE
IKEv2-PLAT-4: PFKEY Delete Ack from IPSec
IKEv2-PLAT-4: Received PFKEY delete SA for SPI 0xB2AA52F6 error FALSE
IKEv2-PLAT-4: PFKEY Delete Ack from IPSec
IKEv2-PLAT-4: Received PFKEY delete SA for SPI 0xA4AC3880 error FALSE
IKEv2-PLAT-4: PFKEY Delete Ack from IPSec
IKEv2-PLAT-4: Received PFKEY delete SA for SPI 0xE1E020A error FALSE
IKEv2-PLAT-4: PFKEY Delete Ack from IPSec
IKEv2-PLAT-4: Received PFKEY delete SA for SPI 0xE96B194D error FALSE
IKEv2-PLAT-4: PFKEY Delete Ack from IPSec
IKEv2-PLAT-4: Received PFKEY delete SA for SPI 0xE3D3201E error FALSE
IKEv2-PLAT-4: PFKEY Delete Ack from IPSec
IKEv2-PLAT-4: Received PFKEY delete SA for SPI 0x86008F76 error FALSE
IKEv2-PLAT-4: PFKEY Delete Ack from IPSec
IKEv2-PLAT-4: Received PFKEY delete SA for SPI 0x6B88ECEF error FALSE
IKEv2-PLAT-4: PFKEY Delete Ack from IPSec
IKEv2-PLAT-4: Received PFKEY delete SA for SPI 0x627A241F error FALSE
IKEv2-PLAT-4: PFKEY Delete Ack from IPSec- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2024 02:36 AM
Hi friend
sorry late reply
the Auth is PSK but the key is encrypt not send as plain text, so the PhaseII SA is not match that make the PSK key seeing different.
crypto ipsec ikev2 ipsec-proposal OPENGEAR-IPSEC-PROPOSAL
protocol esp encryption aes-256
protocol esp integrity sha-512these from debug you share
(592): AES-CBC(592): SHA96(592): Don't use ESNIKEv2-PROTO-4: (592): ESP Proposal: 2, SPI size: 4 (IPSec negotiation),
Num. transforms: 3
(592): AES-CBC(592): SHA256(592): Don't use ESNIKEv2-PROTO-4: (592): ESP Proposal: 3, SPI size: 4 (IPSec negotiation),
Num. transforms: 3
(592): AES-CBC(592): SHA384(592): Don't use ESNIKEv2-PROTO-4: (592): ESP Proposal: 4, SPI size: 4 (IPSec negotiation),
Num. transforms: 3
(592): AES-CBC(592): SHA512(592): Don't use ESNIKEv2-PROTO-4: (592): ESP Proposal: 5, SPI size: 4 (IPSec negotiation),
Num. transforms: 3
(592): AES-CBC(592): SHA96(592): Don't use ESNIKEv2-PROTO-4: (592): ESP Proposal: 6, SPI size: 4 (IPSec negotiation),
Num. transforms: 3
(592): AES-CBC(592): SHA96(592): Don't use ESNIKEv2-PROTO-4: (592): ESP Proposal: 7, SPI size: 4 (IPSec negotiation),
Num. transforms: 3
(592): AES-CBC(592): SHA96(592): Don't use ESNIKEv2-PROTO-4: (592): ESP Proposal: 8, SPI size: 4 (IPSec negotiation),
Num. transforms: 3
(592): AES-CBC(592): SHA96(592): Don't use ESNIKEv2-PROTO-4: (592): ESP Proposal: 9, SPI size: 4 (IPSec negotiation), NOTE:- cisco not use standard SA named like other vendor so try check the SA name with standard.
MHM
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide