- Cisco Community
- Technology and Support
- Security
- VPN
- IPv6 Allowing it on Secure Client
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2023 11:59 AM
Currently, when a VPN client that is dual stacked connnects, the v6 is killed off by the VPN client.
We don't want that to happen. We do not have IPv6 on our Firepower, but nevertheless, we want to allow the traffic to continue but not let it in the tunnel.
How in the world is this possible? Tac said to "disabling ipv6 on the anyconnect profile file" should do it, but it does not.
Client bypass protocol works does anyone know?
Any ideas?
Solved! Go to Solution.
- Labels:
-
AnyConnect
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2023 11:32 PM
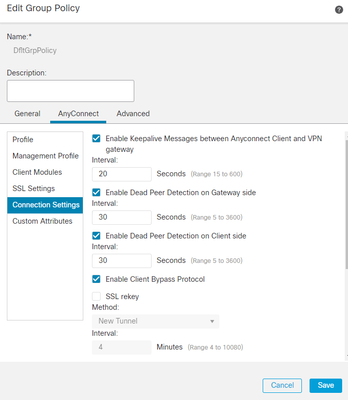
For FMC the option is available under AnyConnect > Connection Settings > Enable Client Bypass Protocol in the Group Policy editor page.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2023 11:27 PM
Client bypass protocol should work. If the option is not available from the GUI, you can use flexconfig to push it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2023 11:32 PM
For FMC the option is available under AnyConnect > Connection Settings > Enable Client Bypass Protocol in the Group Policy editor page.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide