- Cisco Community
- Technology and Support
- Security
- VPN
- Re:isa-server to asa 5505 vpn
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
isa-server to asa 5505 vpn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2013 07:17 AM
hi
the vpn goes up, but the session ipsec turns out to be like the picture below
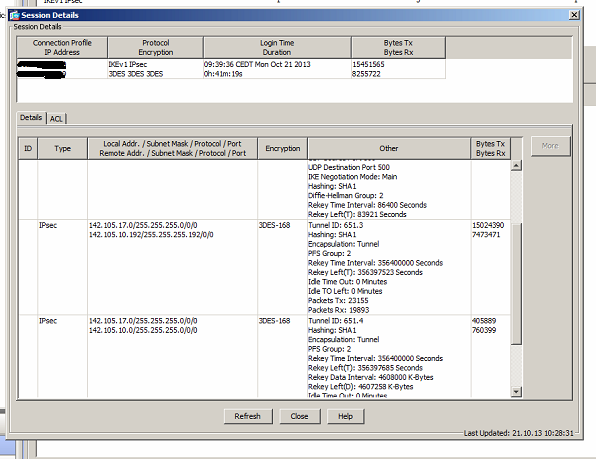
the vpn goes up only if the traffic starts from the side of isa server why?
under the ASA 5505 configuration
Result of the command: "show conf"
: Saved
: Written by enable_15 at 11:00:49.904 CEDT Tue Oct 22 2013
!
ASA Version 8.4(5)
!
hostname ciscoasa
!
names
!
interface Ethernet0/0
switchport access vlan 2
speed 100
duplex full
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan1
nameif inside
security-level 100
ip address 142.105.17.8 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address x.x.x.x 255.255.255.248
!
ftp mode passive
clock timezone CEST 1
clock summer-time CEDT recurring last Sun Mar 2:00 last Sun Oct 3:00
object network rete
subnet 142.105.17.0 255.255.255.0
object network ISA-SERVER
host w.w.w.w
object network dusseldorf
subnet 142.105.17.0 255.255.255.0
object network frosinone
subnet 142.105.10.0 255.255.255.0
object network AS400
host 142.105.10.228
object network routertelecom
host x.x.x.x
object network google
host 8.8.8.8
description dnsgoogle
object network fwout
host x.x.x.x
object-group protocol TCPUDP
protocol-object udp
protocol-object tcp
access-list inside_access_in extended permit ip any any
access-list outside_cryptomap extended permit ip object dusseldorf object frosinone
pager lines 24
logging enable
logging asdm informational
mtu inside 1500
mtu outside 1500
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
nat (inside,outside) source static dusseldorf dusseldorf destination static frosinone frosinone no-proxy-arp route-lookup
!
object network rete
nat (inside,outside) static interface
access-group inside_access_in in interface inside per-user-override
route outside 0.0.0.0 0.0.0.0 y.y.y.y 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
http server enable
http 142.105.17.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
sysopt connection preserve-vpn-flows
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS mode transport
crypto ipsec ikev2 ipsec-proposal DES
protocol esp encryption des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal 3DES
protocol esp encryption 3des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto ipsec security-association lifetime seconds 356400000
crypto map outside_map 1 match address outside_cryptomap
crypto map outside_map 1 set pfs
crypto map outside_map 1 set peer w.w.w.w
crypto map outside_map 1 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 1 set ikev2 pre-shared-key *****
crypto map outside_map interface outside
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 10
encryption aes-192
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption aes
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 30
encryption 3des
integrity sha
group 5 2
prf sha
lifetime seconds none
crypto ikev2 policy 40
encryption des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 enable inside
crypto ikev1 enable inside
crypto ikev1 enable outside
crypto ikev1 policy 10
authentication crack
encryption aes-256
hash sha
group 2
lifetime 86400
crypto ikev1 policy 20
authentication rsa-sig
encryption aes-256
hash sha
group 2
lifetime 86400
crypto ikev1 policy 30
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime 86400
crypto ikev1 policy 40
authentication crack
encryption aes-192
hash sha
group 2
lifetime 86400
crypto ikev1 policy 50
authentication rsa-sig
encryption aes-192
hash sha
group 2
lifetime 86400
crypto ikev1 policy 60
authentication pre-share
encryption aes-192
hash sha
group 2
lifetime 86400
crypto ikev1 policy 70
authentication crack
encryption aes
hash sha
group 2
lifetime 86400
crypto ikev1 policy 80
authentication rsa-sig
encryption aes
hash sha
group 2
lifetime 86400
crypto ikev1 policy 90
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
crypto ikev1 policy 100
authentication crack
encryption 3des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 110
authentication rsa-sig
encryption 3des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 120
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 130
authentication crack
encryption des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 140
authentication rsa-sig
encryption des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 150
authentication pre-share
encryption des
hash sha
group 2
lifetime 86400
telnet timeout 5
ssh timeout 5
ssh key-exchange group dh-group1-sha1
console timeout 0
dhcpd auto_config outside
!
dhcpd address 142.105.17.12-142.105.17.139 inside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
group-policy DfltGrpPolicy attributes
vpn-idle-timeout none
vpn-tunnel-protocol ikev2 l2tp-ipsec
group-policy GroupPolicy_ w.w.w.w internal
group-policy GroupPolicy_ w.w.w.w attributes
vpn-idle-timeout none
vpn-session-timeout none
vpn-tunnel-protocol ikev1 l2tp-ipsec
username CCS_Remote password acOiI5gz2VSd3mKO encrypted privilege 15
tunnel-group DefaultL2LGroup ipsec-attributes
ikev1 pre-shared-key *****
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
tunnel-group w.w.w.w type ipsec-l2l
tunnel-group w.w.w.w general-attributes
default-group-policy GroupPolicy_w.w.w.w
tunnel-group w.w.w.w ipsec-attributes
ikev1 pre-shared-key *****
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
tunnel-group-map default-group w.w.w.w
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect dns preset_dns_map
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:f39e26a278f484f3cc1fda988aedd863
question:
- why the vpn goes up only one way? isa-server -> asa 5505 and not bidirectional, even if it is bidirectional
- why ipsec creates multiple instances with different subnets?
many thanks!
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2013 08:13 AM
In the screenshout there is TX and RX bytes, so traffic should be flowing .. can you enable ASDM logging and check the logs?
Michael
Please rate all helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2013 08:29 AM
I checked the logs but there is no log of ipsec
can not understand why if I have the vpn subnet 255.255.255.0 for class C
ipsec creates subnet 255.255.255.192 or 255.255.255.224 or 255.255.255.64?
is very strange!
and then the only way to activate the vpn is use ping or any traffic from isa-server to asa and not vice versa
i'm going crazy!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2013 12:31 PM
When your in ASDM main page, no vpn active and you ping from a client behind the ASA. Dont you see something in the logs? Vpn should be triggered when theres interesting traffic.
Sent from Cisco Technical Support Android App
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2013 12:03 AM
attach the log.

my question is:
can not understand why if I have the vpn subnet 255.255.255.0 for class C
ipsec creates subnet 255.255.255.192 or 255.255.255.224 or 255.255.255.64?
is very strange!
and then the only way to activate the vpn is use ping or any traffic from isa-server to asa and not vice versa
many thanks!
Luca
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2013 12:17 AM
OK, studied your config again. The error (different subnets) must be on the ISA.
Because the defined networks on the ISA (192, 224, 64) are smaller and fit into the /24 on the ASA, the VPN get's up.
On the other side, when ASA wants to bring it up, the 24 is too big for 192, 224 and 64.
Check the objects in the VPN config at the ISA.
Michael
Please rate all helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2013 12:37 AM
hi Michael,
i have same idea! but isa server 2004 is very bastard
if i can attach the ip sec session on isa server
many thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2013 01:23 AM
you can see the ipsec policy on isa server
Local Tunnel Endpoint: local pubblic ip address
Remote Tunnel Endpoint: remote pubblic ip address (asa 5505)
To allow HTTP proxy or NAT traffic to the remote site,
the remote site configuration must contain the local
site tunnel end-point IP address.
IKE Phase I Parameters:
Mode: Main mode
Encryption: 3DES
Integrity: SHA1
Diffie-Hellman group: Group 2 (1024 bit)
Authentication method: Pre-shared secret (xxxxxxxxxx)
Security Association lifetime: 99000 seconds
IKE Phase II Parameters:
Mode: ESP tunnel mode
Encryption: 3DES
Integrity: SHA1
Perfect Forward Secrecy: ON
Diffie-Hellman group: Group 2 (1024 bit)
Time rekeying: ON
Security Association lifetime: 99000 seconds
Kbyte rekeying: ON
Rekey after sending: 4608000 Kbytes
Remote Network 'vpn dus' IP Subnets:
Subnet: 142.105.17.0/255.255.255.0
Local Network 'DMZ' IP Subnets:
Subnet: 10.20.30.0/255.255.255.0
Local Network 'Internal' IP Subnets:
Subnet: 10.0.0.0/255.255.255.0
Subnet: 10.255.255.255/255.255.255.255
Subnet: 142.105.10.116/255.255.255.255
Subnet: 142.105.10.112/255.255.255.252
Subnet: 142.105.10.96/255.255.255.240
Subnet: 142.105.10.64/255.255.255.224
Subnet: 142.105.10.0/255.255.255.192
Subnet: 142.105.10.122/255.255.255.255
Subnet: 142.105.10.118/255.255.255.254
Subnet: 142.105.10.120/255.255.255.254
Subnet: 142.105.10.124/255.255.255.255
Subnet: 142.105.10.127/255.255.255.255
Subnet: 142.105.10.130/255.255.255.254
Subnet: 142.105.10.132/255.255.255.252
Subnet: 142.105.10.136/255.255.255.248
Subnet: 142.105.10.144/255.255.255.240
Subnet: 142.105.10.160/255.255.255.224
Subnet: 142.105.10.192/255.255.255.192
Subnet: 142.105.15.0/255.255.255.0
Subnet: 142.105.16.0/255.255.255.0
Subnet: 142.105.20.0/255.255.255.0
Subnet: 142.105.18.0/255.255.254.0
Subnet: 142.105.255.255/255.255.255.255
Subnet: 255.255.255.254/255.255.255.255
Subnet: 255.255.255.252/255.255.255.254
Subnet: 255.255.255.248/255.255.255.252
Subnet: 255.255.255.240/255.255.255.248
Subnet: 255.255.255.224/255.255.255.240
Subnet: 255.255.255.192/255.255.255.224
Subnet: 255.255.255.128/255.255.255.192
Subnet: 255.255.255.0/255.255.255.128
Subnet: 255.255.254.0/255.255.255.0
Subnet: 255.255.252.0/255.255.254.0
Subnet: 255.255.248.0/255.255.252.0
Subnet: 255.255.240.0/255.255.248.0
Subnet: 255.255.224.0/255.255.240.0
Subnet: 255.255.192.0/255.255.224.0
Subnet: 255.255.128.0/255.255.192.0
Subnet: 255.255.0.0/255.255.128.0
Subnet: 255.254.0.0/255.255.0.0
Subnet: 255.252.0.0/255.254.0.0
Subnet: 255.248.0.0/255.252.0.0
Subnet: 255.240.0.0/255.248.0.0
Subnet: 255.224.0.0/255.240.0.0
Subnet: 255.192.0.0/255.224.0.0
Subnet: 255.128.0.0/255.192.0.0
Subnet: 255.0.0.0/255.128.0.0
Subnet: 254.0.0.0/255.0.0.0
Subnet: 252.0.0.0/254.0.0.0
Subnet: 248.0.0.0/252.0.0.0
Subnet: 240.0.0.0/248.0.0.0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-24-2013 01:54 AM
Sorry, I have no idea how to fix this on the ISA side, perhaps you should crawl the MS docs?
Michael
Please rate all helpful posts
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide