- Cisco Community
- Technology and Support
- Security
- VPN
- What is the IP address of the
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
L2TP Passthrough ASA 5510
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-20-2016 03:05 AM
Hi there,
I was hoping someone could help? I am trying to set up an L2TP VPN the actual VPN server is running on a windows server on my internal LAN I simply want to pass connections from clients outside the network through an ASA 5510 on the perimeter.
I can confirm the server side config on the windows box is correct as I have tested by connecting to it via L2TP from a client on the inside with no problems. With connections from Windows PCs on the outside I get the following error:
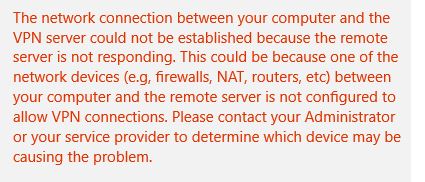
A sanitized version of my ASA Config is below:
hostname CustomerASA
domain-name Customercomputing.com
enable password mzQdMUfMe3JpS6Jz encrypted
passwd cfdtRgP86KiRsmfE encrypted
names
name 10.100.100.30 PonchoSBS
dns-guard
!
interface Ethernet0/0
description ######## Customer Internal LAN ##########
nameif LAN-Customer
security-level 80
ip address 10.100.100.201 255.255.255.0
!
interface Ethernet0/1
description ######## CustLan2 Internal LAN ########
nameif LAN-CustLan2
security-level 80
ip address 10.100.110.201 255.255.255.0
!
interface Ethernet0/2
description ######## LAN CustLan3 ########
nameif LAN-CustLan3
security-level 80
ip address 10.100.120.201 255.255.255.0
!
interface Ethernet0/3
description ######## Outside ISP Interface ########
nameif Outside
security-level 0
ip address 69.69.69.238 255.255.255.248
!
interface Management0/0
description ######## Management Access Only ########
nameif Management
security-level 100
ip address 192.168.1.1 255.255.255.0
!
boot system disk0:/asa831-k8.bin
ftp mode passive
clock timezone GMT 0
dns server-group DefaultDNS
domain-name Customercomputing.com
same-security-traffic permit inter-interface
object network PonchoSBS
host 10.100.100.30
object network LAN-Customer
subnet 10.100.100.0 255.255.255.0
object network LAN-CustLan2
subnet 10.100.110.0 255.255.255.0
object network LAN-CustLan3
subnet 10.100.120.0 255.255.255.0
object service RDP
service tcp destination eq 3389
object network MgmtNAT
subnet 192.168.1.0 255.255.255.0
description MgmtNAT
object network PonchoSBS_EXTERNAL
host 69.69.69.237
object network Outside_Int_IP
host 69.69.69.238
object network Science_Server_25
host 10.100.100.126
object network Science_Server_443
host 10.100.100.126
object network Science_Server_80
host 10.100.100.126
object network VS-Proxy
host 10.100.100.215
object network VS-DC
host 10.100.100.2
object network VS-Exchange2013
host 10.100.100.3
object network spamfilter1
subnet 195.130.217.0 255.255.255.0
object network spamfilter10
subnet 41.74.204.0 255.255.252.0
object network spamfilter11
subnet 213.167.75.0 255.255.255.0
object network spamfilter12
subnet 213.167.81.0 255.255.255.0
object network spamfilter13
subnet 208.66.139.0 255.255.255.0
object network spamfilter14
subnet 216.229.156.0 255.255.255.0
object network spamfilter2
subnet 91.220.42.0 255.255.255.0
object network spamfilter3
subnet 207.211.31.0 255.255.255.128
object network spamfilter4
subnet 207.211.30.0 255.255.255.0
object network spamfilter5
subnet 205.139.110.0 255.255.255.0
object network spamfilter6
subnet 205.139.111.0 255.255.255.0
object network spamfilter7
subnet 41.74.192.0 255.255.252.0
object network spamfilter8
subnet 41.74.200.0 255.255.252.0
object network spamfilter9
subnet 41.74.196.0 255.255.252.0
object network company
host 88.98.40.1
object service LDAP
service tcp destination eq ldap
object network VS-DC-LDAP
host 10.100.100.2
description LDAP for DC - spamfilter Communication.
object service IKE
service udp source range 1 65535 destination eq isakmp
description IKE
object service IPSecESP
service esp
description IPSec ESP
object service IPsecNAT-T
service udp source range 1 65535 destination eq 4500
description IPSec NAT-T
object network VS_EXCHANGE2013_Int
host 10.100.100.3
object-group service DM_INLINE_SERVICE_1
service-object gre
service-object tcp destination eq https
service-object tcp destination eq pptp
service-object esp
service-object ah
object-group service DM_INLINE_TCP_2 tcp
port-object eq 85
port-object eq www
object-group service DM_INLINE_TCP_1 tcp
port-object eq www
port-object eq https
port-object eq smtp
object-group service DM_INLINE_SERVICE_2
service-object object LDAP
object-group service L2TP
service-object object IKE
service-object object IPSecESP
service-object object IPsecNAT-T
service-object tcp-udp destination eq 1701
object-group protocol TCPUDP
protocol-object udp
protocol-object tcp
object-group network spamfilter
network-object object spamfilter1
network-object object spamfilter2
network-object object spamfilter4
network-object object spamfilter5
network-object object spamfilter6
network-object object spamfilter10
network-object object spamfilter11
network-object object spamfilter12
network-object object spamfilter13
network-object object spamfilter14
network-object object spamfilter3
network-object object spamfilter7
network-object object spamfilter8
network-object object spamfilter9
network-object object company
object-group network DM_INLINE_NETWORK_3
network-object object Outside_Int_IP
network-object object PonchoSBS_EXTERNAL
access-list Outside_access extended permit object-group DM_INLINE_SERVICE_1 any object VS-Exchange2013
access-list Outside_access extended permit tcp any host 10.100.100.126 object-gr oup DM_INLINE_TCP_1 inactive
access-list Outside_access extended permit tcp object-group spamfilter object VS-E xchange2013 eq smtp
access-list Outside_access extended permit object-group L2TP any object VS-Excha nge2013
access-list Outside_access extended permit object-group DM_INLINE_SERVICE_2 obje ct-group spamfilter object VS-DC-LDAP
access-list Outside_access extended permit tcp any host 10.100.100.215 object-gr oup DM_INLINE_TCP_2
access-list Outside_access extended permit ip object LAN-Customer 69.69.69.2 32 255.255.255.248 inactive
access-list LAN-Customer_access_in extended permit ip any any
pager lines 24
logging enable
logging asdm informational
mtu LAN-Customer 1500
mtu LAN-CustLan2 1500
mtu LAN-CustLan3 1500
mtu Outside 1500
mtu Management 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
icmp permit any LAN-CustLan3
asdm image disk0:/asdm-631.bin
no asdm history enable
arp timeout 14400
!
object network LAN-Customer
nat (LAN-Customer,Outside) dynamic interface
object network LAN-CustLan2
nat (LAN-CustLan2,Outside) dynamic interface
object network LAN-CustLan3
nat (LAN-CustLan3,Outside) dynamic interface
object network MgmtNAT
nat (Management,Outside) dynamic interface
object network Science_Server_25
nat (LAN-Customer,Outside) static interface service tcp smtp smtp
object network Science_Server_443
nat (LAN-Customer,Outside) static interface service tcp https https
object network Science_Server_80
nat (LAN-Customer,Outside) static interface service tcp www www
object network VS-Proxy
nat (LAN-Customer,Outside) static interface service tcp www 81
object network VS-Exchange2013
nat (any,any) static 69.69.69.237
object network VS-DC-LDAP
nat (any,Outside) static interface service tcp ldap ldap
access-group LAN-Customer_access_in in interface LAN-Customer
access-group Outside_access in interface Outside
route Outside 0.0.0.0 0.0.0.0 69.69.69.233 5
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-record DfltAccessPolicy
aaa authentication ssh console LOCAL
http server enable 4443
http 192.168.1.0 255.255.255.0 Management
http 0.0.0.0 0.0.0.0 LAN-Customer
http 88.98.40.1 255.255.255.255 Outside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto isakmp nat-traversal 3600
telnet timeout 5
ssh 0.0.0.0 0.0.0.0 LAN-Customer
ssh 88.98.40.1 255.255.255.255 Outside
ssh 0.0.0.0 0.0.0.0 Management
ssh timeout 5
console timeout 0
dhcpd address 10.100.110.10-10.100.110.50 LAN-CustLan2
dhcpd dns 8.8.8.8 4.4.4.4 interface LAN-CustLan2
dhcpd enable LAN-CustLan2
!
dhcpd address 10.100.120.10-10.100.120.50 LAN-CustLan3
dhcpd dns 8.8.8.8 4.4.4.4 interface LAN-CustLan3
dhcpd enable LAN-CustLan3
!
dhcpd address 192.168.1.10-192.168.1.50 Management
dhcpd enable Management
!
threat-detection basic-threat
threat-detection statistics host
threat-detection statistics port
threat-detection statistics protocol
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
username company password /dOQN1XOcOofMIyT encrypted privilege 15
username admin password x4VzqNDubhe0TkYT encrypted privilege 15
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map global_policy
class inspection_default
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect pptp
inspect icmp
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:a820c5efa789fa1c1ad95fb23bcf7879
: end
Any assistance with what is wrong would be greatly appreciated. The packet tracer both in the ASDM GUI and from ther terminal would suggest that the ACLs and NAT are working fine it is just that the connections therough the ASA do not complete.
Thanks very much,
Dan
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2016 01:31 AM
What is the IP address of the device you want to pass L2TP through to?
You need to NAT:
UDP/500
UDP/4500
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide