- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Lan-to-Lan tunnel between three ASA/PIX
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2013 07:29 AM
Hi guys,
I need some help to fix a issue i got.
Here is the topology, i hope you can see what is says.
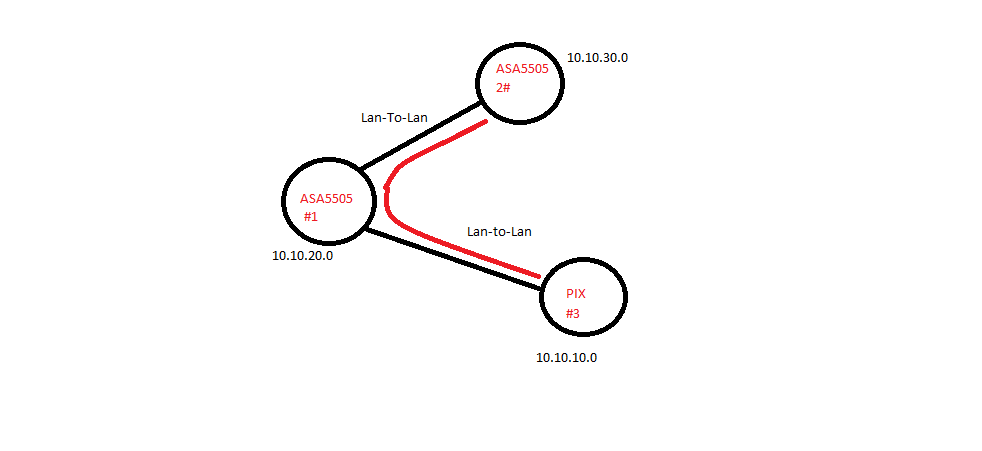
I got lan-to-lan VPN from ASA #1 to PIX #3 and ASA #2
Now we need to get access from ASA #2 to PIX #3 network.
How do i fix this in the easiest way.
We dont want a tunneln between ASA #2 and PIX #3. We already done that but the connection was horrible.
ASA #1 and ASA #2 are located in China, and PIX are in Sweden.
the ISP ASA #2 uses has trouble with their line to Sweden.
Thanks in advance!
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2013 07:41 AM
That's easy to achieve. You need to configure three things:
1) permit same-security-traffic intra-interface on ASA1
2) Extend the crypto-ACL on all devices:
ASA2 to ASA1:
10.10.30.0 to 10.10.20.0 (already there)
10.10.30.0 to 10.10.10.0
PIX3 to ASA1:
10.10.10.0 to 10.10.20.0 (already there)
10.10.10.0 to 10.10.30.0
ASA1 to ASA2:
10.10.20.0 to 10.10.30.0 (already there)
10.10.10.0 to 10.10.30.0
ASA1 to PIX3:
10.10.20.0 to 10.10.10.0 (already there)
10.10.30.0 to 10.10.10.0
3) Configure NAT-Excemption on ASA1 that this traffic won't be natted as you did for the existing VPN-traffic.
--
Don't stop after you've improved your network! Improve the world by lending money to the working poor:
http://www.kiva.org/invitedby/karsteni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2013 07:35 AM
Hi,
i think that you have problems with the routing. Can you post the routing table from all devices?
The tunnel between ASA-ASA-PIX are up? Also u can ping the next neighbor with the internal ip?
It is important that the internal traffic were forwarded over the outside / Wan interface without NAT.
Regards
Markus
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2013 07:41 AM
That's easy to achieve. You need to configure three things:
1) permit same-security-traffic intra-interface on ASA1
2) Extend the crypto-ACL on all devices:
ASA2 to ASA1:
10.10.30.0 to 10.10.20.0 (already there)
10.10.30.0 to 10.10.10.0
PIX3 to ASA1:
10.10.10.0 to 10.10.20.0 (already there)
10.10.10.0 to 10.10.30.0
ASA1 to ASA2:
10.10.20.0 to 10.10.30.0 (already there)
10.10.10.0 to 10.10.30.0
ASA1 to PIX3:
10.10.20.0 to 10.10.10.0 (already there)
10.10.30.0 to 10.10.10.0
3) Configure NAT-Excemption on ASA1 that this traffic won't be natted as you did for the existing VPN-traffic.
--
Don't stop after you've improved your network! Improve the world by lending money to the working poor:
http://www.kiva.org/invitedby/karsteni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2013 12:39 AM
Hi
Thanks again! But I'm still having touble to get this work. :-(
The site-to-site tunnels are up. I can ping between #1 and #3 and #1 and #2.
Here is a output on the configuration I've added to the devices with the real IP-networks.
Do you know what could be the issue?
ASA #1
same-security-traffic permit intra-interface
access-list vpn_to_pix3 extended permit ip 192.168.1.0 255.255.255.0 192.168.120.0 255.255.255.0
access-list vpn_to_pix3 extended permit ip 192.168.1.0 255.255.255.0 192.168.124.0 255.255.255.0
access-list vpn_to_pix3 extended permit ip 192.168.1.0 255.255.255.0 192.168.123.0 255.255.255.0
access-list vpn_to_asa2 extended permit ip 192.168.120.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list vpn_to_asa2 extended permit ip 192.168.124.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list vpn_to_asa2 extended permit ip 192.168.123.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list no_nat extended permit ip 192.168.1.0 255.255.255.0 192.168.120.0 255.255.255.0
access-list no_nat extended permit ip 192.168.1.0 255.255.255.0 192.168.124.0 255.255.255.0
access-list no_nat extended permit ip 192.168.1.0 255.255.255.0 192.168.123.0 255.255.255.0
access-list no_nat extended permit ip 192.168.124.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list no_nat extended permit ip 192.168.120.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list no_nat extended permit ip 192.168.123.0 255.255.255.0 192.168.1.0 255.255.255.0
------------------------------------------------------------------
ASA #2
name 192.168.1.0 sh
name 192.168.120.0 sweden3
name 192.168.124.0 sweden
name 192.168.123.0 sweden2
object-group network swedennet
network-object sweden2 255.255.255.0
network-object sweden 255.255.255.0
network-object sweden3 255.255.255.0
access-list vpn_to_asa1 extended permit ip sh 255.255.255.0 object-group swedennet
access-list no_nat extended permit ip sh 255.255.255.0 object-group swedennet
------------------------------------------------------------------
PIX #3
access-list vpn_to_asa1 permit ip 192.168.123.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list vpn_to_asa1 permit ip 192.168.120.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list vpn_to_asa1 permit ip 192.168.124.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list no_nat permit ip 192.168.123.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list no_nat permit ip 192.168.120.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list no_nat permit ip 192.168.124.0 255.255.255.0 192.168.1.0 255.255.255.0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2013 06:47 AM
the config looks good all in all. There are some things that could go wrong:
1) On ASA-1, the new NAT-exemption could be needed on the outside interface depending on your existing NAT-configuration.
2) There are different ways to control which traffic is allowed in the VPN. print sh output of "sh run all sysopt", if there is not something active like "permit-vpn" or "permit ipsec" (that depends on the version), then the VPN-traffic has to be allowed on the public interface.
--
Don't stop after you've improved your network! Improve the world by lending money to the working poor:
http://www.kiva.org/invitedby/karsteni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2013 05:47 AM
Hi and thanks again!
I've checked
sh run all sysopt
and permit-vpn is active.
I can se that the tunnel is active and have connection to PIX3 network when i try to ping. but I still cant access anything.
Here is the show crypto ipsec sa from ASA2
interface: outside
Crypto map tag: cry-map, seq num: 20, local addr: 116.x.x.x
access-list vpn_to_ufab_china extended permit ip 192.168.1.0 255.255.255.0 192.168.123.0 255.255.255.0
local ident (addr/mask/prot/port): (sh/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (sweden2/255.255.255.0/0/0)
current_peer: 222.x.x.x
#pkts encaps: 24, #pkts encrypt: 24, #pkts digest: 24
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 24, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 116.x.x.x, remote crypto endpt.: 222.x.x.x
path mtu 1500, ipsec overhead 58, media mtu 1500
current outbound spi: 4D3DF09E
current inbound spi : 0D887D4F
inbound esp sas:
spi: 0x0D887D4F (227048783)
transform: esp-3des esp-md5-hmac no compression
in use settings ={L2L, Tunnel, }
slot: 0, conn_id: 278528, crypto-map: cry-map
sa timing: remaining key lifetime (kB/sec): (3915000/28159)
IV size: 8 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
outbound esp sas:
spi: 0x4D3DF09E (1295904926)
transform: esp-3des esp-md5-hmac no compression
in use settings ={L2L, Tunnel, }
slot: 0, conn_id: 278528, crypto-map: cry-map
sa timing: remaining key lifetime (kB/sec): (3914998/28159)
IV size: 8 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Running cfg from ASA1
: Saved
:
ASA Version 7.2(4)
!
!
interface Vlan1
nameif inside
security-level 100
ip address 192.168.155.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address 222.x.x.x 255.255.255.240
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
ftp mode passive
same-security-traffic permit intra-interface
access-list vpn_to_pix3 extended permit ip 192.168.155.0 255.255.255.0 192.168.124.0 255.255.255.0
access-list vpn_to_pix3 extended permit ip 192.168.155.0 255.255.255.0 192.168.126.0 255.255.255.0
access-list vpn_to_pix3 extended permit ip 192.168.155.0 255.255.255.0 192.168.123.0 255.255.255.0
access-list vpn_to_pix3 extended permit ip 192.168.155.0 255.255.255.0 192.168.125.0 255.255.255.0
access-list vpn_to_pix3 extended permit ip 192.168.1.0 255.255.255.0 192.168.120.0 255.255.255.0
access-list vpn_to_pix3 extended permit ip 192.168.1.0 255.255.255.0 192.168.124.0 255.255.255.0
access-list vpn_to_pix3 extended permit ip 192.168.1.0 255.255.255.0 192.168.123.0 255.255.255.0
access-list no_nat extended permit ip 192.168.155.0 255.255.255.0 192.168.124.0 255.255.255.0
access-list no_nat extended permit ip 192.168.155.0 255.255.255.0 192.168.126.0 255.255.255.0
access-list no_nat extended permit ip 192.168.155.0 255.255.255.0 192.168.123.0 255.255.255.0
access-list no_nat extended permit ip 192.168.155.0 255.255.255.0 10.12.13.0 255.255.255.0
access-list no_nat extended permit ip 192.168.155.0 255.255.255.0 192.168.125.0 255.255.255.0
access-list no_nat extended permit ip 192.168.155.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list no_nat extended permit ip 192.168.1.0 255.255.255.0 192.168.120.0 255.255.255.0
access-list no_nat extended permit ip 192.168.1.0 255.255.255.0 192.168.124.0 255.255.255.0
access-list no_nat extended permit ip 192.168.1.0 255.255.255.0 192.168.123.0 255.255.255.0
access-list no_nat extended permit ip 192.168.124.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list no_nat extended permit ip 192.168.120.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list no_nat extended permit ip 192.168.123.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list split_acl extended permit ip 192.168.155.0 255.255.255.0 any
access-list outside_access_in extended permit icmp any any
access-list vpn_to_asa2 extended permit ip 192.168.155.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list vpn_to_asa2 extended permit ip 192.168.120.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list vpn_to_asa2 extended permit ip 192.168.124.0 255.255.255.0 192.168.1.0 255.255.255.0
access-list vpn_to_asa2 extended permit ip 192.168.123.0 255.255.255.0 192.168.1.0 255.255.255.0
pager lines 24
logging enable
logging asdm informational
mtu inside 1500
mtu outside 1500
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-524.bin
no asdm history enable
arp timeout 14400
global (outside) 1 interface
nat (inside) 0 access-list no_nat
nat (inside) 1 0.0.0.0 0.0.0.0
access-group outside_access_in in interface outside
route outside 0.0.0.0 0.0.0.0 default-gateway 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
http server enable
http 192.168.155.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
snmp-server community pubuanet
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set 3des-set esp-3des esp-md5-hmac
crypto dynamic-map dynmap 10 set transform-set 3des-set
crypto dynamic-map dynmap 10 set reverse-route
crypto map mymap 10 match address vpn_to_pix3
crypto map mymap 10 set peer 194.x.x.x
crypto map mymap 10 set transform-set 3des-set
crypto map mymap 20 match address vpn_to_asa2
crypto map mymap 20 set peer 116.x.x.x
crypto map mymap 20 set transform-set 3des-set
crypto map mymap 100 ipsec-isakmp dynamic dynmap
crypto map mymap interface outside
crypto isakmp identity address
crypto isakmp enable outside
crypto isakmp policy 40
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto isakmp nat-traversal 20
!
group-policy vpn-china internal
group-policy vpn-china attributes
dns-server value 202.96.209.133 202.96.209.5
split-tunnel-policy tunnelspecified
split-tunnel-network-list value split_acl
tunnel-group 194.x.x.x type ipsec-l2l
tunnel-group 194.x.x.x ipsec-attributes
pre-shared-key *
tunnel-group 116.x.x.x type ipsec-l2l
tunnel-group 116.x.x.x ipsec-attributes
pre-shared-key *
!
!
: end
-----------------------------------------------------------------------------
Running cfg from ASA2
: Saved
:
ASA Version 8.2(5)
!
names
name 192.168.1.0 sh
name 192.168.120.0 sweden3
name 192.168.124.0 sweden
name 192.168.123.0 sweden2
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan1
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address 116.x.x.x 255.255.255.252
!
interface Vlan5
no nameif
security-level 50
no ip address
!
ftp mode passive
clock timezone HKST 8
dns server-group DefaultDNS
domain-name dfmarine
object-group network swedennet
network-object sweden2 255.255.255.0
network-object sweden 255.255.255.0
network-object sweden3 255.255.255.0
access-list 102 extended permit icmp any any
access-list 102 extended permit tcp any host 116.x.x.x eq 3389
access-list 102 extended permit tcp any host 116.x.x.x eq ftp
access-list 102 extended permit tcp any host 116.x.x.x eq www
access-list vpn_to_asa1 extended permit ip sh 255.255.255.0 192.168.155.0 255.255.255.0
access-list vpn_to_asa1 extended permit ip sh 255.255.255.0 object-group swedennet
access-list no_nat extended permit ip sh 255.255.255.0 object-group swedennet
access-list no_nat extended permit ip sh 255.255.255.0 192.168.155.0 255.255.255.0
pager lines 24
logging enable
logging asdm informational
mtu inside 1500
mtu outside 1500
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
global (outside) 1 interface
nat (inside) 0 access-list no_nat
nat (inside) 1 0.0.0.0 0.0.0.0
static (inside,outside) tcp interface 3389 192.168.1.252 3389 netmask 255.255.255.255
static (inside,outside) tcp interface ftp 192.168.1.251 ftp netmask 255.255.255.255
static (inside,outside) tcp interface www 192.168.1.251 www netmask 255.255.255.255
access-group 102 in interface outside
route outside 0.0.0.0 0.0.0.0 default-gateway 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
aaa authentication ssh console LOCAL
http server enable
http sh 255.255.255.0 inside
no snmp-server location
no snmp-server contact
snmp-server community *****
snmp-server enable traps snmp authentication linkup linkdown coldstart
sysopt connection tcpmss 0
crypto ipsec transform-set trans esp-3des esp-md5-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto map cry-map 20 match address vpn_to_asa1
crypto map cry-map 20 set peer 222.x.x.x
crypto map cry-map 20 set transform-set trans
crypto map cry-map interface outside
crypto isakmp identity address
crypto isakmp enable outside
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash md5
group 2
lifetime 86400
crypto isakmp policy 20
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ssl encryption des-sha1
webvpn
group-policy DfltGrpPolicy attributes
vpn-tunnel-protocol IPSec
tunnel-group 222.x.x.x type ipsec-l2l
tunnel-group 222.x.x.x ipsec-attributes
pre-shared-key *****
!
!
prompt hostname context
no call-home reporting anonymous
: end
-----------------------------------------------------------------------------
No further changes on PIX3, and I don't think the problem is located there.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2013 11:20 AM
Hi Guys!
Thanks for your quick replies!
I will look into this tomorrow and get back to you!
Have a nice day
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2013 01:59 AM
Update!
Everything has been solved, the problem was that I missed to delete a old crypto map pointing to ASA#2 on the PIX.
After a relaod on the pix everything is up and running. Thanks you for taking you'r time, it helped me alot in my troubleshooting!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide



