- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Packet Tracer IPSec VPN Tunnel ACL Drops
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-26-2020 10:28 PM - edited 05-27-2020 04:18 AM
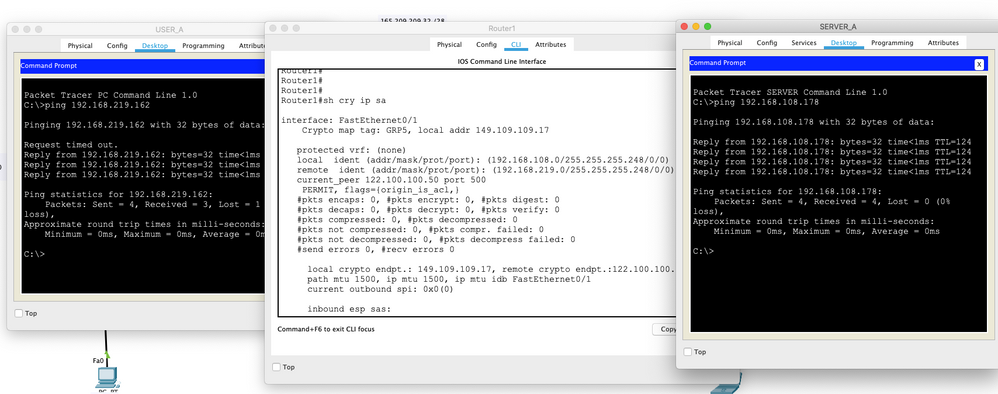
I have an IPSEC VPN Network that I have configured. The network uses EIGRP to connect to each other. My ACL is a Named Extended Network. The two nodes that I want to communicate with each other won't communicate with each other. To be more specific, USER_A and SERVER_A are not communicating. However they can ping to the rest of the network just fine. I am leaning towards either my ACL is configured wrong or that my interfaces are configured wrong and I cannot figure out how to correct it although I'm willing to bet it's simple. Image attachment displays the network.
Router 1
ip access-list extended VPN1
permit ip 192.168.108.176 0.0.0.255 192.168.219.160 0.0.0.255
exit
int f0/1
exit
!
crypto isakmp policy 666
encryption aes 128
hash sha
authentication pre-share
group 5
lifetime 40000
exit
!
crypto isakmp key Anon address 122.100.100.50
!
crypto ipsec transform-set PF_666 esp-aes 128 esp-sha-hmac
!
crypto map GRP5 666 ipsec-isakmp
set peer 122.100.100.50
set pfs group5
set transform-set PF_666
match address VPN1
!
int f0/1
crypto map GRP5
Router 2
ip access-list extended VPN1
permit ip 192.168.219.160 0.0.0.255 192.168.108.176 0.0.0.255
exit
int f1/0
exit
!
crypto isakmp policy 666
encryption aes 128
hash sha
authentication pre-share
group 5
lifetime 40000
exit
!
crypto isakmp key Anon address 149.109.109.18
!
crypto ipsec transform-set PF_666 esp-aes 128 esp-sha-hmac
!
crypto map GRP5 666 ipsec-isakmp
set peer 149.109.109.18
set pfs group5
set transform-set PF_666
match address VPN1
!
int f1/0
crypto map GRP5
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-27-2020 12:11 AM
See attached
changed peer on Router2 from .18 to .17
crypto map GRP5 666 ipsec-isakmp set peer 149.109.109.17
Changed ACLs from .255 to .7
ip access-list extended VPN1 permit ip 192.168.219.0 0.0.0.7 192.168.108.0 0.0.0.7
because the interesting traffic is generated from
interface FastEthernet0/1 ip address 192.168.219.161 255.255.255.248
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-26-2020 11:19 PM
Hi
zip and attach the packet tracer file here
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-26-2020 11:42 PM - edited 05-27-2020 04:19 AM
Attached and sent.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-27-2020 12:11 AM
See attached
changed peer on Router2 from .18 to .17
crypto map GRP5 666 ipsec-isakmp set peer 149.109.109.17
Changed ACLs from .255 to .7
ip access-list extended VPN1 permit ip 192.168.219.0 0.0.0.7 192.168.108.0 0.0.0.7
because the interesting traffic is generated from
interface FastEthernet0/1 ip address 192.168.219.161 255.255.255.248
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-27-2020 04:17 AM
Took your solution and tested it. Then applied my save and made the changes myself to verify it and it's working perfectly for me. I very much appreciate your patience in helping me with such simple mistakes.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide