- Cisco Community
- Technology and Support
- Security
- VPN
- As it turns out an upgrade to
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Remote Access SSL VPN Certificate Authentication Issues
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2015 03:31 AM - edited 02-21-2020 08:03 PM
Hello,
I have been tasked with upgrading an SSL VPN solution to add a VPN profile that utilizes certificate authentication (the other profiles currently use AAA).
Before I make a start on the live systems I want to get it working in a lab environment, but have come across the following issue:
When logging into the VPN using the Anyconnect client I get the following message:
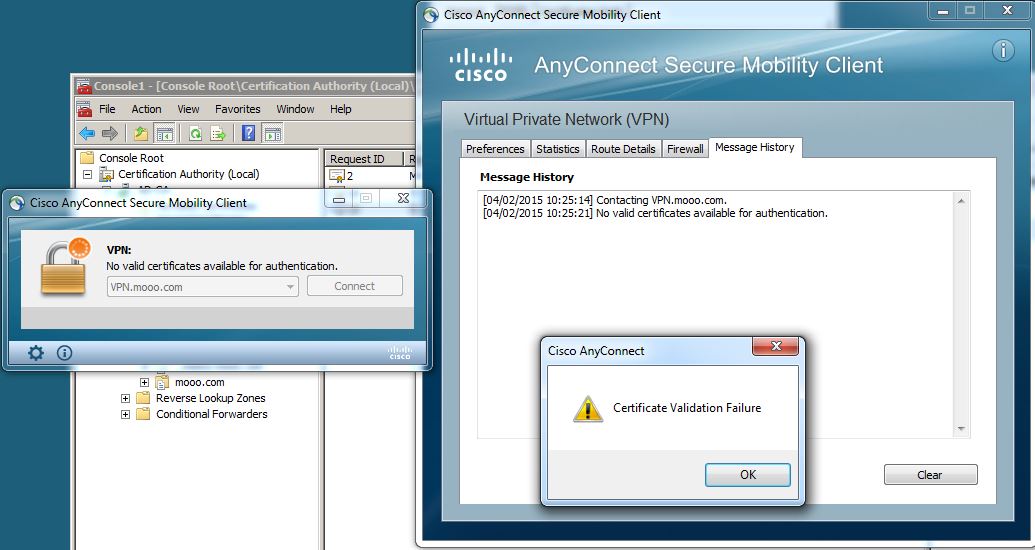
I am running Anyconnect version 3.1.06078 and ASA version 8.4(2)
I have a Windows 2008 server running as a certificate authority.
I have imported the CA root certificate onto the ASA and issued a certificate to the ASA using a "server authentication" certificate template.
I have imported the CA root certificate onto the client machine and issued a certificate to the client using a "user" certificate template.
From the ASA's point of view everything seems OK, it recognises the client certificate and the certificate is validated (CRL checking is disabled for now) For this reason I think that the Anyconnect client may have an issue with the cert on the ASA? see ASA logs below:

I have read Cisco's requirements for the certificates, which as I understand it is as follows:
ASA certificate:
Key usage: Digital Signature and Key Encipherment
EKU: Server Authentication
Client certificate:
Key usage: Digital Signature and Key Encipherment
EKU: Client Authentication
Here is my ASA certificate information:

Here is my client certificate information:

I have attached a copy of the ASA configuration file.
If anyone can help with this it would be greatly appreciated!
Kind Regards,
Rhys.
- Labels:
-
Remote Access
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2015 05:53 AM
As it turns out an upgrade to ASA 9.1.5 sorted all of my problems.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide